Daily Vulnerability Trends: Fri Nov 11 2022
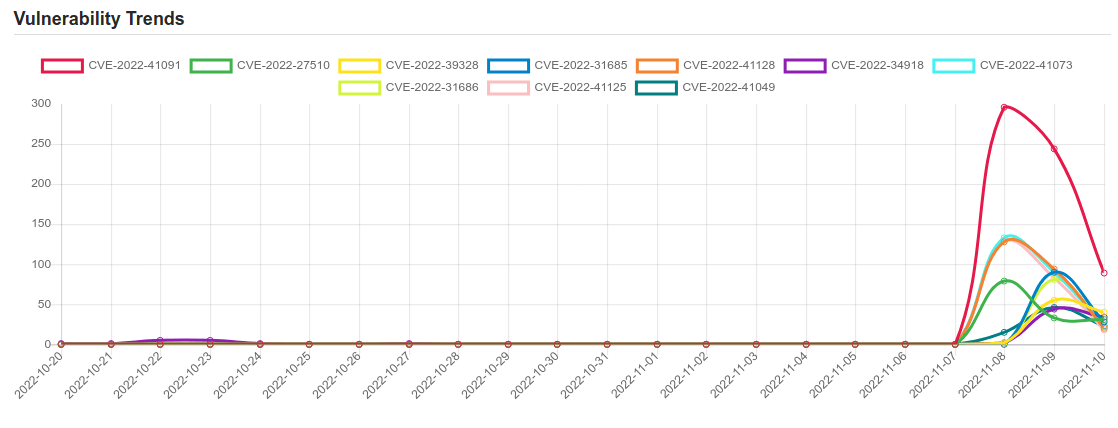
| CVE NAME | CVE Description |
| CVE-2022-41049 | Windows Mark of the Web Security Feature Bypass Vulnerability. This CVE ID is unique from CVE-2022-41091. |
| CVE-2022-31687 | VMware Workspace ONE Assist prior to 22.10 contains a Broken Access Control vulnerability. A malicious actor with network access to Workspace ONE Assist may be able to obtain administrative access without the need to authenticate to the application. |
| CVE-2022-27513 | Remote desktop takeover via phishing |
| CVE-2022-27516 | User login brute force protection functionality bypass |
| CVE-2020-1206 | An information disclosure vulnerability exists in the way that the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests, aka ‘Windows SMBv3 Client/Server Information Disclosure Vulnerability’. |
| CVE-2022-41120 | Microsoft Windows Sysmon Elevation of Privilege Vulnerability. |
| CVE-2022-41040 | Microsoft Exchange Server Elevation of Privilege Vulnerability. |
| CVE-2022-40684 | An authentication bypass using an alternate path or channel [CWE-288] in Fortinet FortiOS version 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy version 7.2.0 and version 7.0.0 through 7.0.6 and FortiSwitchManager version 7.2.0 and 7.0.0 allows an unauthenticated atttacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests. |
| CVE-2022-41082 | Microsoft Exchange Server Remote Code Execution Vulnerability. |
| CVE-2022-40619 | No description provided |
| CVE-2022-3699 | No description provided |
| CVE-2022-41091 | Windows Mark of the Web Security Feature Bypass Vulnerability. This CVE ID is unique from CVE-2022-41049. |
| CVE-2022-27510 | Unauthorized access to Gateway user capabilities |
| CVE-2022-39328 | Grafana is an open-source platform for monitoring and observability. Versions starting with 9.2.0 and less than 9.2.4 contain a race condition in the authentication middlewares logic which may allow an unauthenticated user to query an administration endpoint under heavy load. This issue is patched in 9.2.4. There are no known workarounds. |
| CVE-2022-31685 | VMware Workspace ONE Assist prior to 22.10 contains an Authentication Bypass vulnerability. A malicious actor with network access to Workspace ONE Assist may be able to obtain administrative access without the need to authenticate to the application. |
| CVE-2022-41128 | Windows Scripting Languages Remote Code Execution Vulnerability. This CVE ID is unique from CVE-2022-41118. |
| CVE-2022-34918 | An issue was discovered in the Linux kernel through 5.18.9. A type confusion bug in nft_set_elem_init (leading to a buffer overflow) could be used by a local attacker to escalate privileges, a different vulnerability than CVE-2022-32250. (The attacker can obtain root access, but must start with an unprivileged user namespace to obtain CAP_NET_ADMIN access.) This can be fixed in nft_setelem_parse_data in net/netfilter/nf_tables_api.c. |
| CVE-2022-41073 | Windows Print Spooler Elevation of Privilege Vulnerability. |
| CVE-2022-31686 | VMware Workspace ONE Assist prior to 22.10 contains a Broken Authentication Method vulnerability. A malicious actor with network access to Workspace ONE Assist may be able to obtain administrative access without the need to authenticate to the application. |
| CVE-2022-41125 | Windows CNG Key Isolation Service Elevation of Privilege Vulnerability. |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.




