Daily Vulnerability Trends: Wed Nov 16 2022
| CVE NAME | CVE Description |
| CVE-2022-1802 | No description provided |
| CVE-2022-41352 | An issue was discovered in Zimbra Collaboration (ZCS) 8.8.15 and 9.0. An attacker can upload arbitrary files through amavisd via a cpio loophole (extraction to /opt/zimbra/jetty/webapps/zimbra/public) that can lead to incorrect access to any other user accounts. Zimbra recommends pax over cpio. Also, pax is in the prerequisites of Zimbra on Ubuntu; however, pax is no longer part of a default Red Hat installation after RHEL 6 (or CentOS 6). Once pax is installed, amavisd automatically prefers it over cpio. |
| CVE-2022-35803 | Windows Common Log File System Driver Elevation of Privilege Vulnerability. This CVE ID is unique from CVE-2022-37969. |
| CVE-2021-38827 | Xiongmai Camera XM-JPR2-LX V4.02.R12.A6420987.10002.147502.00000 is vulnerable to account takeover. |
| CVE-2022-2200 | No description provided |
| CVE-2022-1529 | No description provided |
| CVE-2022-37966 | Windows Kerberos RC4-HMAC Elevation of Privilege Vulnerability. |
| CVE-2022-37967 | Windows Kerberos Elevation of Privilege Vulnerability. |
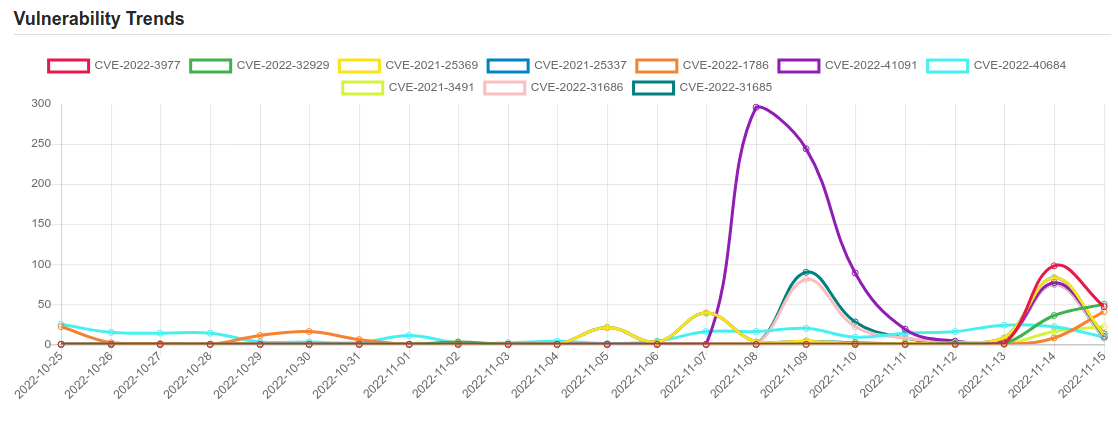
| CVE-2022-3977 | No description provided |
| CVE-2022-32929 | A permissions issue was addressed with additional restrictions. This issue is fixed in iOS 15.7.1 and iPadOS 15.7.1, iOS 15.7 and iPadOS 15.7, iOS 16.1 and iPadOS 16. An app may be able to access iOS backups. |
| CVE-2021-25369 | An improper access control vulnerability in sec_log file prior to SMR MAR-2021 Release 1 exposes sensitive kernel information to userspace. |
| CVE-2021-25337 | Improper access control in clipboard service in Samsung mobile devices prior to SMR Mar-2021 Release 1 allows untrusted applications to read or write certain local files. |
| CVE-2022-1786 | A use-after-free flaw was found in the Linux kernel’s io_uring subsystem in the way a user sets up a ring with IORING_SETUP_IOPOLL with more than one task completing submissions on this ring. This flaw allows a local user to crash or escalate their privileges on the system. |
| CVE-2022-41091 | Windows Mark of the Web Security Feature Bypass Vulnerability. This CVE ID is unique from CVE-2022-41049. |
| CVE-2022-40684 | An authentication bypass using an alternate path or channel [CWE-288] in Fortinet FortiOS version 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy version 7.2.0 and version 7.0.0 through 7.0.6 and FortiSwitchManager version 7.2.0 and 7.0.0 allows an unauthenticated atttacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests. |
| CVE-2021-3491 | The io_uring subsystem in the Linux kernel allowed the MAX_RW_COUNT limit to be bypassed in the PROVIDE_BUFFERS operation, which led to negative values being usedin mem_rw when reading /proc/ |
| CVE-2022-31686 | VMware Workspace ONE Assist prior to 22.10 contains a Broken Authentication Method vulnerability. A malicious actor with network access to Workspace ONE Assist may be able to obtain administrative access without the need to authenticate to the application. |
| CVE-2022-31685 | VMware Workspace ONE Assist prior to 22.10 contains an Authentication Bypass vulnerability. A malicious actor with network access to Workspace ONE Assist may be able to obtain administrative access without the need to authenticate to the application. |
| CVE-2021-25370 | An incorrect implementation handling file descriptor in dpu driver prior to SMR Mar-2021 Release 1 results in memory corruption leading to kernel panic. |
| CVE-2022-41082 | Microsoft Exchange Server Remote Code Execution Vulnerability. |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.




![Cobalt Strike Beacon Detected - 43[.]143[.]114[.]43:8099 6 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
![Brute Ratel C4 Detected - 54[.]178[.]158[.]125:80 10 brute_ratel_c4](https://www.redpacketsecurity.com/wp-content/uploads/2022/07/brute_ratel_c4-300x300.jpg)