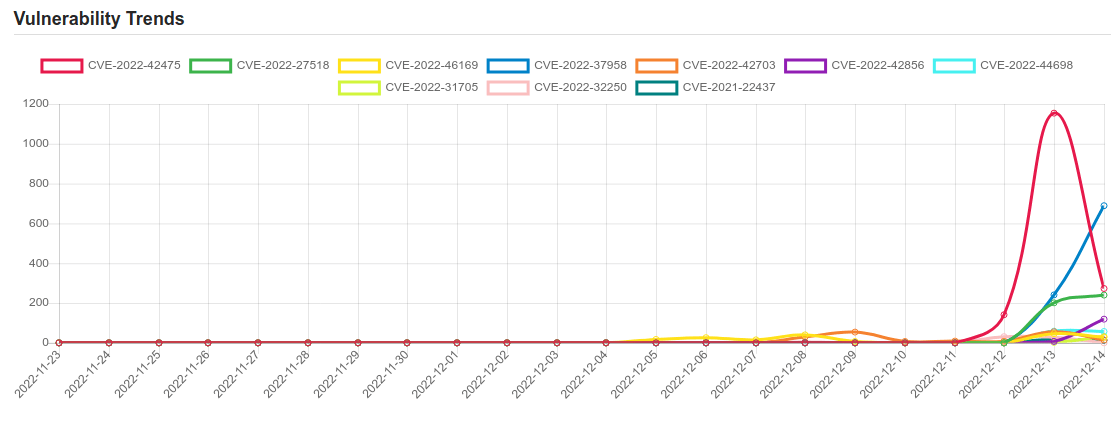
Daily Vulnerability Trends: Thu Dec 15 2022
| CVE NAME | CVE Description |
| CVE-2022-32250 | net/netfilter/nf_tables_api.c in the Linux kernel through 5.18.1 allows a local user (able to create user/net namespaces) to escalate privileges to root because an incorrect NFT_STATEFUL_EXPR check leads to a use-after-free. |
| CVE-2021-22437 | There is a software integer overflow leading to a TOCTOU condition in smartphones. Successful exploitation of this vulnerability may cause random address access. |
| CVE-2021-39993 | There is an Integer overflow vulnerability with ACPU in smartphones. Successful exploitation of this vulnerability may cause out-of-bounds access. |
| CVE-2021-39994 | There is an arbitrary address access vulnerability with the product line test code.Successful exploitation of this vulnerability may affect service confidentiality, integrity, and availability. |
| CVE-2022-40684 | An authentication bypass using an alternate path or channel [CWE-288] in Fortinet FortiOS version 7.2.0 through 7.2.1 and 7.0.0 through 7.0.6, FortiProxy version 7.2.0 and version 7.0.0 through 7.0.6 and FortiSwitchManager version 7.2.0 and 7.0.0 allows an unauthenticated atttacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests. |
| CVE-2022-4247 | A vulnerability classified as critical was found in Movie Ticket Booking System. This vulnerability affects unknown code of the file booking.php. The manipulation of the argument id leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-214624. |
| CVE-2022-424755 | No description provided |
| CVE-2017-11882 | Microsoft Office 2007 Service Pack 3, Microsoft Office 2010 Service Pack 2, Microsoft Office 2013 Service Pack 1, and Microsoft Office 2016 allow an attacker to run arbitrary code in the context of the current user by failing to properly handle objects in memory, aka “Microsoft Office Memory Corruption Vulnerability”. This CVE ID is unique from CVE-2017-11884. |
| CVE-2022-31702 | vRealize Network Insight (vRNI) contains a command injection vulnerability present in the vRNI REST API. A malicious actor with network access to the vRNI REST API can execute commands without authentication. |
| CVE-2022-45771 | An issue in the /api/audits component of Pwndoc v0.5.3 allows attackers to escalate privileges and execute arbitrary code via uploading a crafted audit file. |
| CVE-2022-275184677 | No description provided |
| CVE-2022-45025 | Markdown Preview Enhanced v0.6.5 and v0.19.6 for VSCode and Atom was discovered to contain a command injection vulnerability via the PDF file import function. |
| CVE-2022-42475 | No description provided |
| CVE-2022-27518 | Unauthenticated remote arbitrary code execution |
| CVE-2022-46169 | Cacti is an open source platform which provides a robust and extensible operational monitoring and fault management framework for users. In affected versions a command injection vulnerability allows an unauthenticated user to execute arbitrary code on a server running Cacti, if a specific data source was selected for any monitored device. The vulnerability resides in the `remote_agent.php` file. This file can be accessed without authentication. This function retrieves the IP address of the client via `get_client_addr` and resolves this IP address to the corresponding hostname via `gethostbyaddr`. After this, it is verified that an entry within the `poller` table exists, where the hostname corresponds to the resolved hostname. If such an entry was found, the function returns `true` and the client is authorized. This authorization can be bypassed due to the implementation of the `get_client_addr` function. The function is defined in the file `lib/functions.php` and checks serval `$_SERVER` variables to determine the IP address of the client. The variables beginning with `HTTP_` can be arbitrarily set by an attacker. Since there is a default entry in the `poller` table with the hostname of the server running Cacti, an attacker can bypass the authentication e.g. by providing the header `Forwarded-For: |
| CVE-2022-37958 | SPNEGO Extended Negotiation (NEGOEX) Security Mechanism Information Disclosure Vulnerability. |
| CVE-2022-42703 | mm/rmap.c in the Linux kernel before 5.19.7 has a use-after-free related to leaf anon_vma double reuse. |
| CVE-2022-42856 | No description provided |
| CVE-2022-44698 | Windows SmartScreen Security Feature Bypass Vulnerability. |
| CVE-2022-31705 | VMware ESXi, Workstation, and Fusion contain a heap out-of-bounds write vulnerability in the USB 2.0 controller (EHCI). A malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine’s VMX process running on the host. On ESXi, the exploitation is contained within the VMX sandbox whereas, on Workstation and Fusion, this may lead to code execution on the machine where Workstation or Fusion is installed. |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.




![[DRAGONFORCE] - Ransomware Victim: Pratt Homes 6 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)