Daily Vulnerability Trends: Sun Dec 25 2022
| CVE NAME | CVE Description |
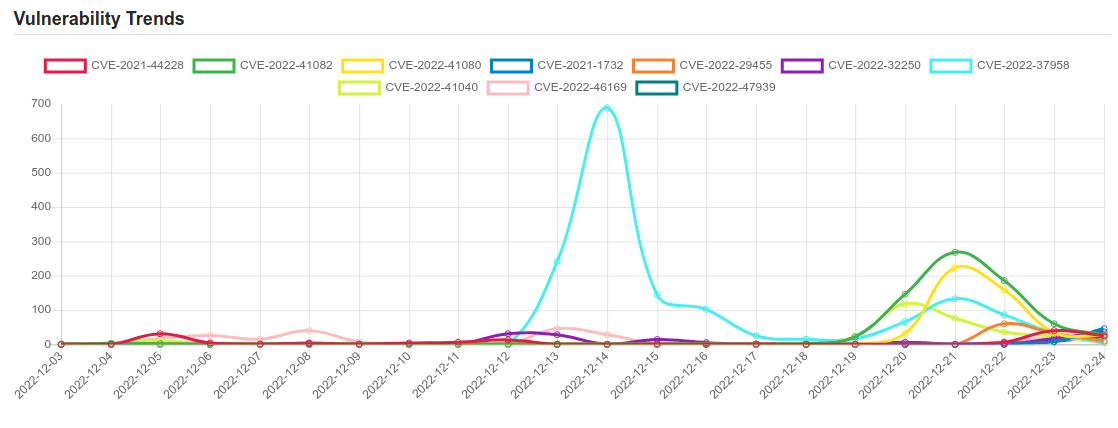
| CVE-2022-41040 | Microsoft Exchange Server Elevation of Privilege Vulnerability. |
| CVE-2022-46169 | Cacti is an open source platform which provides a robust and extensible operational monitoring and fault management framework for users. In affected versions a command injection vulnerability allows an unauthenticated user to execute arbitrary code on a server running Cacti, if a specific data source was selected for any monitored device. The vulnerability resides in the `remote_agent.php` file. This file can be accessed without authentication. This function retrieves the IP address of the client via `get_client_addr` and resolves this IP address to the corresponding hostname via `gethostbyaddr`. After this, it is verified that an entry within the `poller` table exists, where the hostname corresponds to the resolved hostname. If such an entry was found, the function returns `true` and the client is authorized. This authorization can be bypassed due to the implementation of the `get_client_addr` function. The function is defined in the file `lib/functions.php` and checks serval `$_SERVER` variables to determine the IP address of the client. The variables beginning with `HTTP_` can be arbitrarily set by an attacker. Since there is a default entry in the `poller` table with the hostname of the server running Cacti, an attacker can bypass the authentication e.g. by providing the header `Forwarded-For: |
| CVE-2022-47939 | An issue was discovered in ksmbd in the Linux kernel before 5.19.2. fs/ksmbd/smb2pdu.c has a use-after-free and OOPS for SMB2_TREE_DISCONNECT. |
| CVE-2022-42046 | WFS, Inc HeavenBurnsRed 2020.3.15.7141260 is vulnerable to Local Privilege Escalation. |
| CVE-2022-47942 | An issue was discovered in ksmbd in the Linux kernel before 5.19.2. There is a heap-based buffer overflow in set_ntacl_dacl, related to use of SMB2_QUERY_INFO_HE after a malformed SMB2_SET_INFO_HE command. |
| CVE-2020-7958 | An issue was discovered on OnePlus 7 Pro devices before 10.0.3.GM21BA. The firmware was found to contain functionality that allows a privileged user (root) in the Rich Execution Environment (REE) to obtain bitmap images from the fingerprint sensor because of Leftover Debug Code. The issue is that the Trusted Application (TA) supports an extended number of commands beyond what is needed to implement a fingerprint authentication system compatible with Android. An attacker who is in the position to send commands to the TA (for example, the root user) is able to send a sequence of these commands that will result in the TA sending a raw fingerprint image to the REE. This means that the Trusted Execution Environment (TEE) no longer protects identifiable fingerprint data from the REE. |
| CVE-2022-2602 | No description provided |
| CVE-2022-47941 | An issue was discovered in ksmbd in the Linux kernel before 5.19.2. fs/ksmbd/smb2pdu.c omits a kfree call in certain smb2_handle_negotiate error conditions, aka a memory leak. |
| CVE-2022-42821 | A logic issue was addressed with improved checks. This issue is fixed in macOS Monterey 12.6.2, macOS Big Sur 11.7.2, macOS Ventura 13. An app may bypass Gatekeeper checks. |
| CVE-2022-47938 | An issue was discovered in ksmbd in the Linux kernel before 5.19.2. fs/ksmbd/smb2misc.c has an out-of-bounds read and OOPS for SMB2_TREE_CONNECT. |
| CVE-2022-47940 | An issue was discovered in ksmbd in the Linux kernel before 5.18.18. fs/ksmbd/smb2pdu.c lacks length validation in the non-padding case in smb2_write. |
| CVE-2022-45359 | Unauth. Arbitrary File Upload vulnerability in YITH WooCommerce Gift Cards premium plugin <= 3.19.0 on WordPress. |
| CVE-2022-4543 | No description provided |
| CVE-2021-44228 | Apache Log4j2 2.0-beta9 through 2.15.0 (excluding security releases 2.12.2, 2.12.3, and 2.3.1) JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. From log4j 2.15.0, this behavior has been disabled by default. From version 2.16.0 (along with 2.12.2, 2.12.3, and 2.3.1), this functionality has been completely removed. Note that this vulnerability is specific to log4j-core and does not affect log4net, log4cxx, or other Apache Logging Services projects. |
| CVE-2022-41082 | Microsoft Exchange Server Remote Code Execution Vulnerability. |
|
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.  To keep up to date follow us on the below channels.     |


![Cobalt Strike Beacon Detected - 139[.]9[.]135[.]76:443 8 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
