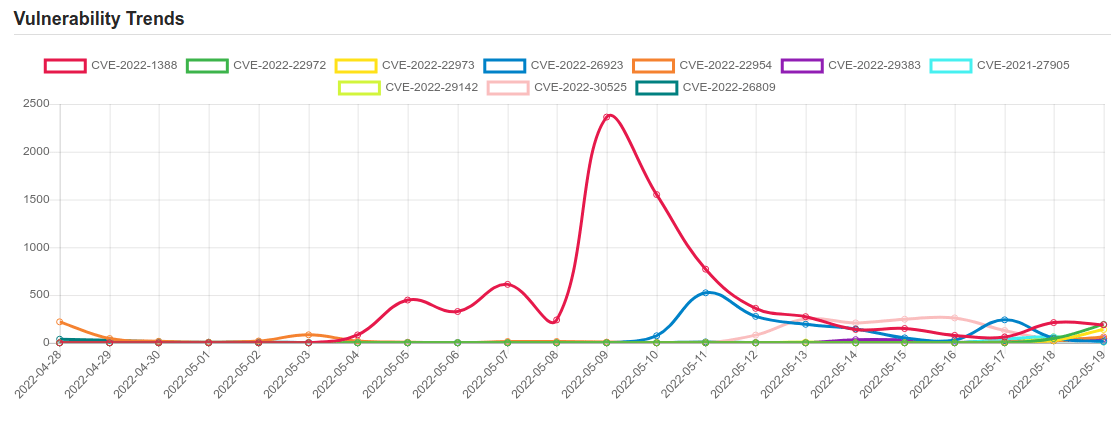
Daily Vulnerability Trends: Fri May 20 2022
| CVE NAME | CVE Description |
| CVE-2022-1771 | Stack-based Buffer Overflow in GitHub repository vim/vim prior to 8.2.4975. |
| CVE-2022-1774 | Exposure of Sensitive Information to an Unauthorized Actor in GitHub repository jgraph/drawio prior to 18.0.7. |
| CVE-2022-22646 | No description provided |
| CVE-2022-22960 | VMware Workspace ONE Access, Identity Manager and vRealize Automation contain a privilege escalation vulnerability due to improper permissions in support scripts. A malicious actor with local access can escalate privileges to ‘root’. |
| CVE-2022-26925 | Windows LSA Spoofing Vulnerability. |
| CVE-2022-22583 | A permissions issue was addressed with improved validation. This issue is fixed in Security Update 2022-001 Catalina, macOS Monterey 12.2, macOS Big Sur 11.6.3. An application may be able to access restricted files. |
| CVE-2022-26727 | No description provided |
| CVE-2022-22676 | No description provided |
| CVE-2022-1388 | On F5 BIG-IP 16.1.x versions prior to 16.1.2.2, 15.1.x versions prior to 15.1.5.1, 14.1.x versions prior to 14.1.4.6, 13.1.x versions prior to 13.1.5, and all 12.1.x and 11.6.x versions, undisclosed requests may bypass iControl REST authentication. Note: Software versions which have reached End of Technical Support (EoTS) are not evaluated |
| CVE-2022-22973 | No description provided |
| CVE-2022-26923 | Active Directory Domain Services Elevation of Privilege Vulnerability. |
| CVE-2022-22954 | VMware Workspace ONE Access and Identity Manager contain a remote code execution vulnerability due to server-side template injection. A malicious actor with network access can trigger a server-side template injection that may result in remote code execution. |
| CVE-2022-29383 | NETGEAR ProSafe SSL VPN firmware FVS336Gv2 and FVS336Gv3 was discovered to contain a SQL injection vulnerability via USERDBDomains.Domainname at cgi-bin/platform.cgi. |
| CVE-2021-27905 | The ReplicationHandler (normally registered at “/replication” under a Solr core) in Apache Solr has a “masterUrl” (also “leaderUrl” alias) parameter that is used to designate another ReplicationHandler on another Solr core to replicate index data into the local core. To prevent a SSRF vulnerability, Solr ought to check these parameters against a similar configuration it uses for the “shards” parameter. Prior to this bug getting fixed, it did not. This problem affects essentially all Solr versions prior to it getting fixed in 8.8.2. |
| CVE-2022-29142 | Windows Kernel Elevation of Privilege Vulnerability. This CVE ID is unique from CVE-2022-29133. |
| CVE-2022-30525 | A OS command injection vulnerability in the CGI program of Zyxel USG FLEX 100(W) firmware versions 5.00 through 5.21 Patch 1, USG FLEX 200 firmware versions 5.00 through 5.21 Patch 1, USG FLEX 500 firmware versions 5.00 through 5.21 Patch 1, USG FLEX 700 firmware versions 5.00 through 5.21 Patch 1, USG FLEX 50(W) firmware versions 5.10 through 5.21 Patch 1, USG20(W)-VPN firmware versions 5.10 through 5.21 Patch 1, ATP series firmware versions 5.10 through 5.21 Patch 1, VPN series firmware versions 4.60 through 5.21 Patch 1, which could allow an attacker to modify specific files and then execute some OS commands on a vulnerable device. |
| CVE-2022-26809 | Remote Procedure Call Runtime Remote Code Execution Vulnerability. This CVE ID is unique from CVE-2022-24492, CVE-2022-24528. |
| CVE-2021-40444 | Microsoft MSHTML Remote Code Execution Vulnerability |
| CVE-2022-1183 | On vulnerable configurations, the named daemon may, in some circumstances, terminate with an assertion failure. Vulnerable configurations are those that include a reference to http within the listen-on statements in their named.conf. TLS is used by both DNS over TLS (DoT) and DNS over HTTPS (DoH), but configurations using DoT alone are unaffected. Affects BIND 9.18.0 -> 9.18.2 and version 9.19.0 of the BIND 9.19 development branch. |
| CVE-2022-22972 | VMware Workspace ONE Access, VMware Identity Manager, and VMware vRealize Automation security bypass | CVE-2022-22972 |
If you like the site, please consider joining the telegram channel and supporting us on Patreon using the button below.


![Brute Ratel C4 Detected - 18[.]177[.]187[.]233:80 3 brute_ratel_c4](https://www.redpacketsecurity.com/wp-content/uploads/2022/07/brute_ratel_c4-300x300.jpg)
![Cobalt Strike Beacon Detected - 118[.]89[.]73[.]78:4433 4 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)