Daily Vulnerability Trends: Thu Jul 28 2022
| CVE NAME | CVE Description |
| CVE-2022-32502 | No description provided |
| CVE-2022-32510 | No description provided |
| CVE-2022-26134 | In affected versions of Confluence Server and Data Center, an OGNL injection vulnerability exists that would allow an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance. The affected versions are from 1.3.0 before 7.4.17, from 7.13.0 before 7.13.7, from 7.14.0 before 7.14.3, from 7.15.0 before 7.15.2, from 7.16.0 before 7.16.4, from 7.17.0 before 7.17.4, and from 7.18.0 before 7.18.1. |
| CVE-2022-2143 | The affected product is vulnerable to two instances of command injection, which may allow an attacker to remotely execute arbitrary code. |
| CVE-2022-22047 | Windows CSRSS Elevation of Privilege Vulnerability. This CVE ID is unique from CVE-2022-22026, CVE-2022-22049. |
| CVE-2022-26138 | The Atlassian Questions For Confluence app for Confluence Server and Data Center creates a Confluence user account in the confluence-users group with the username disabledsystemuser and a hardcoded password. A remote, unauthenticated attacker with knowledge of the hardcoded password could exploit this to log into Confluence and access all content accessible to users in the confluence-users group. This user account is created when installing versions 2.7.34, 2.7.35, and 3.0.2 of the app. |
| CVE-2022-21571 | Vulnerability in the Oracle VM VirtualBox product of Oracle Virtualization (component: Core). The supported version that is affected is Prior to 6.1.36. Easily exploitable vulnerability allows high privileged attacker with logon to the infrastructure where Oracle VM VirtualBox executes to compromise Oracle VM VirtualBox. While the vulnerability is in Oracle VM VirtualBox, attacks may significantly impact additional products (scope change). Successful attacks of this vulnerability can result in takeover of Oracle VM VirtualBox. CVSS 3.1 Base Score 8.2 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.1/AV:L/AC:L/PR:H/UI:N/S:C/C:H/I:H/A:H). |
| CVE-2022-32509 | No description provided |
| CVE-2022-244622 | No description provided |
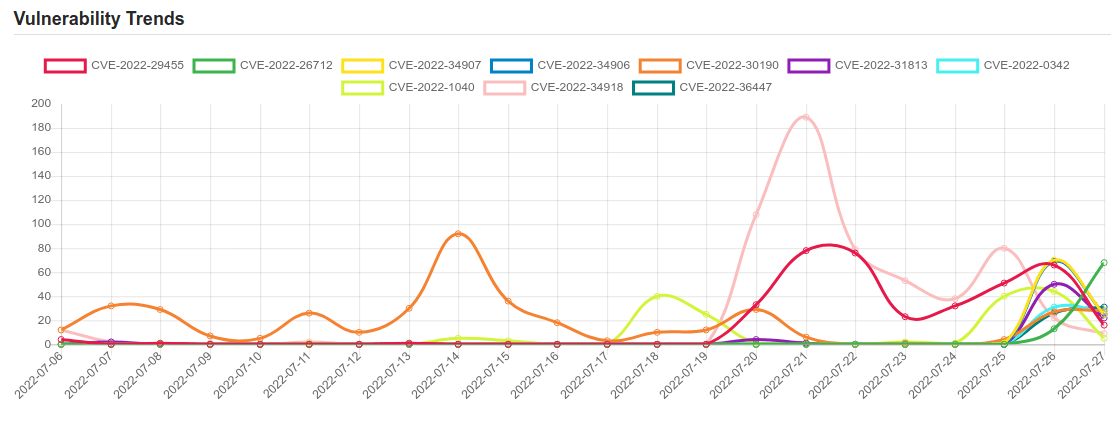
| CVE-2022-29455 | DOM-based Reflected Cross-Site Scripting (XSS) vulnerability in Elementor’s Elementor Website Builder plugin <= 3.5.5 versions. |
| CVE-2022-26712 | This issue was addressed by removing the vulnerable code. This issue is fixed in macOS Monterey 12.4, macOS Big Sur 11.6.6. A malicious application may be able to modify protected parts of the file system. |
| CVE-2022-34906 | A hard-coded cryptographic key is used in FileWave before 14.6.3 and 14.7.x before 14.7.2. Exploitation could allow an unauthenticated actor to decrypt sensitive information saved in FileWave, and even send crafted requests. |
| CVE-2022-30190 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability. |
| CVE-2022-31813 | Apache HTTP Server 2.4.53 and earlier may not send the X-Forwarded-* headers to the origin server based on client side Connection header hop-by-hop mechanism. This may be used to bypass IP based authentication on the origin server/application. |
| CVE-2022-0342 | An authentication bypass vulnerability in the CGI program of Zyxel USG/ZyWALL series firmware versions 4.20 through 4.70, USG FLEX series firmware versions 4.50 through 5.20, ATP series firmware versions 4.32 through 5.20, VPN series firmware versions 4.30 through 5.20, and NSG series firmware versions V1.20 through V1.33 Patch 4, which could allow an attacker to bypass the web authentication and obtain administrative access of the device. |
| CVE-2022-1040 | An authentication bypass vulnerability in the User Portal and Webadmin allows a remote attacker to execute code in Sophos Firewall version v18.5 MR3 and older. |
| CVE-2022-34918 | An issue was discovered in the Linux kernel through 5.18.9. A type confusion bug in nft_set_elem_init (leading to a buffer overflow) could be used by a local attacker to escalate privileges, a different vulnerability than CVE-2022-32250. (The attacker can obtain root access, but must start with an unprivileged user namespace to obtain CAP_NET_ADMIN access.) This can be fixed in nft_setelem_parse_data in net/netfilter/nf_tables_api.c. |
| CVE-2022-36447 | No description provided |
| CVE-2022-36408 | PrestaShop 1.6.0.10 through 1.7.x before 1.7.8.7 allows remote attackers to execute arbitrary code, aka a “previously unknown vulnerability chain” related to SQL injection and MySQL Smarty cache storage injection, as exploited in the wild in July 2022. |
| CVE-2022-34907 | FileWave security bypass | CVE-2022-34907 |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.





![[NIGHTSPIRE] - Ransomware Victim: Wilmington Personal Injury Lawyer - DPLAW 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
