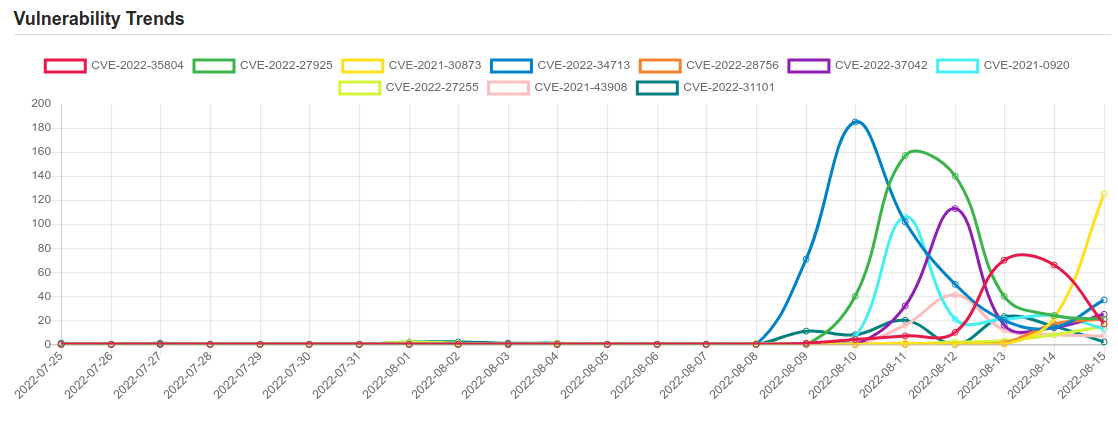
Daily Vulnerability Trends: Tue Aug 16 2022
| CVE NAME | CVE Description |
| CVE-2022-30216 | Windows Server Service Tampering Vulnerability. |
| CVE-2022-26923 | Active Directory Domain Services Elevation of Privilege Vulnerability. |
| CVE-2022-27254 | The remote keyless system on Honda Civic 2018 vehicles sends the same RF signal for each door-open request, which allows for a replay attack, a related issue to CVE-2019-20626. |
| CVE-2021-40444 | Microsoft MSHTML Remote Code Execution Vulnerability |
| CVE-2022-30190 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability. |
| CVE-2022-30333 | RARLAB UnRAR before 6.12 on Linux and UNIX allows directory traversal to write to files during an extract (aka unpack) operation, as demonstrated by creating a ~/.ssh/authorized_keys file. NOTE: WinRAR and Android RAR are unaffected. |
| CVE-2022-20233 | In param_find_digests_internal and related functions of the Titan-M source, there is a possible out of bounds write due to an incorrect bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-222472803References: N/A |
| CVE-2022-27925 | Zimbra Collaboration (aka ZCS) 8.8.15 and 9.0 has mboximport functionality that receives a ZIP archive and extracts files from it. An authenticated user with administrator rights has the ability to upload arbitrary files to the system, leading to directory traversal. |
| CVE-2021-30873 | A logic issue was addressed with improved state management. This issue is fixed in macOS Monterey 12.0.1. A malicious application may be able to elevate privileges. |
| CVE-2022-34713 | Microsoft Windows Support Diagnostic Tool (MSDT) Remote Code Execution Vulnerability. This CVE ID is unique from CVE-2022-35743. |
| CVE-2022-28756 | The Zoom Client for Meetings for macOS (Standard and for IT Admin) starting with version 5.7.3 and before 5.11.5 contains a vulnerability in the auto update process. A local low-privileged user could exploit this vulnerability to escalate their privileges to root. |
| CVE-2022-37042 | Zimbra Collaboration Suite (ZCS) 8.8.15 and 9.0 has mboximport functionality that receives a ZIP archive and extracts files from it. By bypassing authentication (i.e., not having an authtoken), an attacker can upload arbitrary files to the system, leading to directory traversal and remote code execution. NOTE: this issue exists because of an incomplete fix for CVE-2022-27925. |
| CVE-2021-0920 | In unix_scm_to_skb of af_unix.c, there is a possible use after free bug due to a race condition. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation.Product: AndroidVersions: Android kernelAndroid ID: A-196926917References: Upstream kernel |
| CVE-2022-27255 | In Realtek eCos RSDK 1.5.7p1 and MSDK 4.9.4p1, the SIP ALG function that rewrites SDP data has a stack-based buffer overflow. This allows an attacker to remotely execute code without authentication via a crafted SIP packet that contains malicious SDP data. |
| CVE-2021-43908 | Visual Studio Code Spoofing Vulnerability |
| CVE-2022-31101 | prestashop/blockwishlist is a prestashop extension which adds a block containing the customer’s wishlists. In affected versions an authenticated customer can perform SQL injection. This issue is fixed in version 2.1.1. Users are advised to upgrade. There are no known workarounds for this issue. |
| CVE-2021-09 | No description provided |
| CVE-2021-30659 | A validation issue was addressed with improved logic. This issue is fixed in iOS 14.5 and iPadOS 14.5, watchOS 7.4, macOS Big Sur 11.3. A malicious application may be able to leak sensitive user information. |
| CVE-2022-2590 | No description provided |
| CVE-2022-35804 | Microsoft Windows SMB code execution | CVE-2022-35804 |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.




