Daily Vulnerability Trends: Thu Sep 15 2022
| CVE NAME | CVE Description |
| CVE-2022-27593 | An externally controlled reference to a resource vulnerability has been reported to affect QNAP NAS running Photo Station. If exploited, This could allow an attacker to modify system files. We have already fixed the vulnerability in the following versions: QTS 5.0.1: Photo Station 6.1.2 and later QTS 5.0.0/4.5.x: Photo Station 6.0.22 and later QTS 4.3.6: Photo Station 5.7.18 and later QTS 4.3.3: Photo Station 5.4.15 and later QTS 4.2.6: Photo Station 5.2.14 and later |
| CVE-2022-2964 | A flaw was found in the Linux kernel’s driver for the ASIX AX88179_178A-based USB 2.0/3.0 Gigabit Ethernet Devices. The vulnerability contains multiple out-of-bounds reads and possible out-of-bounds writes. |
| CVE-2022-32250 | net/netfilter/nf_tables_api.c in the Linux kernel through 5.18.1 allows a local user (able to create user/net namespaces) to escalate privileges to root because an incorrect NFT_STATEFUL_EXPR check leads to a use-after-free. |
| CVE-2022-23960 | Certain Arm Cortex and Neoverse processors through 2022-03-08 do not properly restrict cache speculation, aka Spectre-BHB. An attacker can leverage the shared branch history in the Branch History Buffer (BHB) to influence mispredicted branches. Then, cache allocation can allow the attacker to obtain sensitive information. |
| CVE-2022-35805 | Microsoft Dynamics CRM (on-premises) Remote Code Execution Vulnerability. This CVE ID is unique from CVE-2022-34700. |
| CVE-2022-34700 | Microsoft Dynamics CRM (on-premises) Remote Code Execution Vulnerability. This CVE ID is unique from CVE-2022-35805. |
| CVE-2021-1675 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2013-3220 | bitcoind and Bitcoin-Qt before 0.4.9rc2, 0.5.x before 0.5.8rc2, 0.6.x before 0.6.5rc2, and 0.7.x before 0.7.3rc2, and wxBitcoin, do not properly consider whether a block’s size could require an excessive number of database locks, which allows remote attackers to cause a denial of service (split) and enable certain double-spending capabilities via a large block that triggers incorrect Berkeley DB locking. |
| CVE-2022-39135 | In Apache Calcite prior to version 1.32.0 the SQL operators EXISTS_NODE, EXTRACT_XML, XML_TRANSFORM and EXTRACT_VALUE do not restrict XML External Entity references in their configuration, which makes them vulnerable to a potential XML External Entity (XXE) attack. Therefore any client exposing these operators, typically by using Oracle dialect (the first three) or MySQL dialect (the last one), is affected by this vulnerability (the extent of it will depend on the user under which the application is running). From Apache Calcite 1.32.0 onwards, Document Type Declarations and XML External Entity resolution are disabled on the impacted operators. |
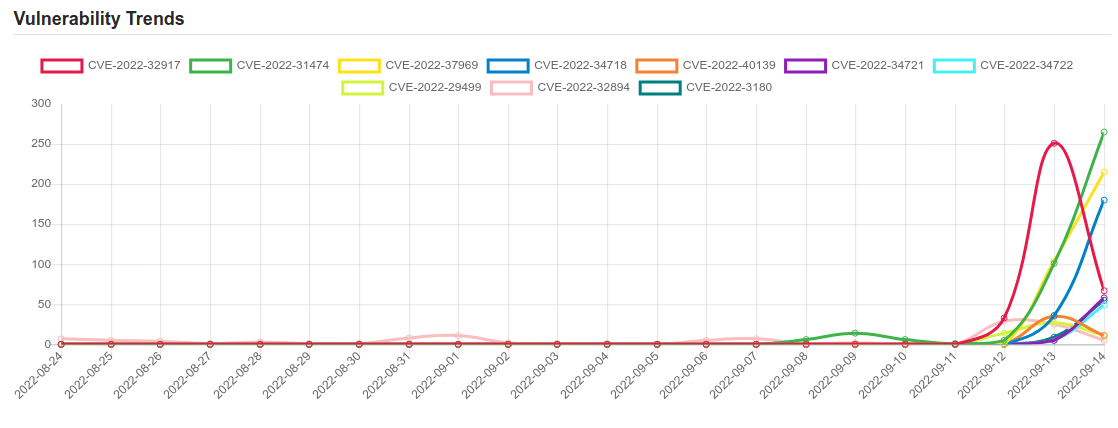
| CVE-2022-31474 | No description provided |
| CVE-2022-37969 | Windows Common Log File System Driver Elevation of Privilege Vulnerability. This CVE ID is unique from CVE-2022-35803. |
| CVE-2022-40139 | No description provided |
| CVE-2022-29499 | The Service Appliance component in Mitel MiVoice Connect through 19.2 SP3 allows remote code execution because of incorrect data validation. The Service Appliances are SA 100, SA 400, and Virtual SA. |
| CVE-2022-32894 | An out-of-bounds write issue was addressed with improved bounds checking. This issue is fixed in iOS 15.6.1 and iPadOS 15.6.1, macOS Monterey 12.5.1. An application may be able to execute arbitrary code with kernel privileges. Apple is aware of a report that this issue may have been actively exploited. |
| CVE-2022-37706 | No description provided |
| CVE-2022-32917 | Apple macOS Monterey, iOS and iPadOS privilege escalation | CVE-2022-32917 |
| CVE-2022-34718 | Microsoft Windows TCP/IP code execution | CVE-2022-34718 |
| CVE-2022-34721 | Microsoft Windows Internet Key Exchange (IKE) Protocol Extensions code execution | CVE-2022-34721 |
| CVE-2022-34722 | Microsoft Windows Internet Key Exchange (IKE) Protocol Extensions code execution | CVE-2022-34722 |
| CVE-2022-3180 | CODESYS Gateway Server V2 denial of service | CVE-2022-31802 |
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.





![[NIGHTSPIRE] - Ransomware Victim: Wilmington Personal Injury Lawyer - DPLAW 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
