Dark Pink hackers continue to target govt and military organizations
The Dark Pink APT hacking group continues to be very active in 2023, observed targeting government, military, and education organizations in Indonesia, Brunei, and Vietnam.
The threat group has been active since at least mid-2021, primarily targeting entities in the Asia-Pacific region, but it was first exposed in January 2023 by a Group-IB report.
The researchers report that after analyzing signs of previous activity by the threat actor, they now discovered additional breaches against an educational institute in Belgium and a military body in Thailand.
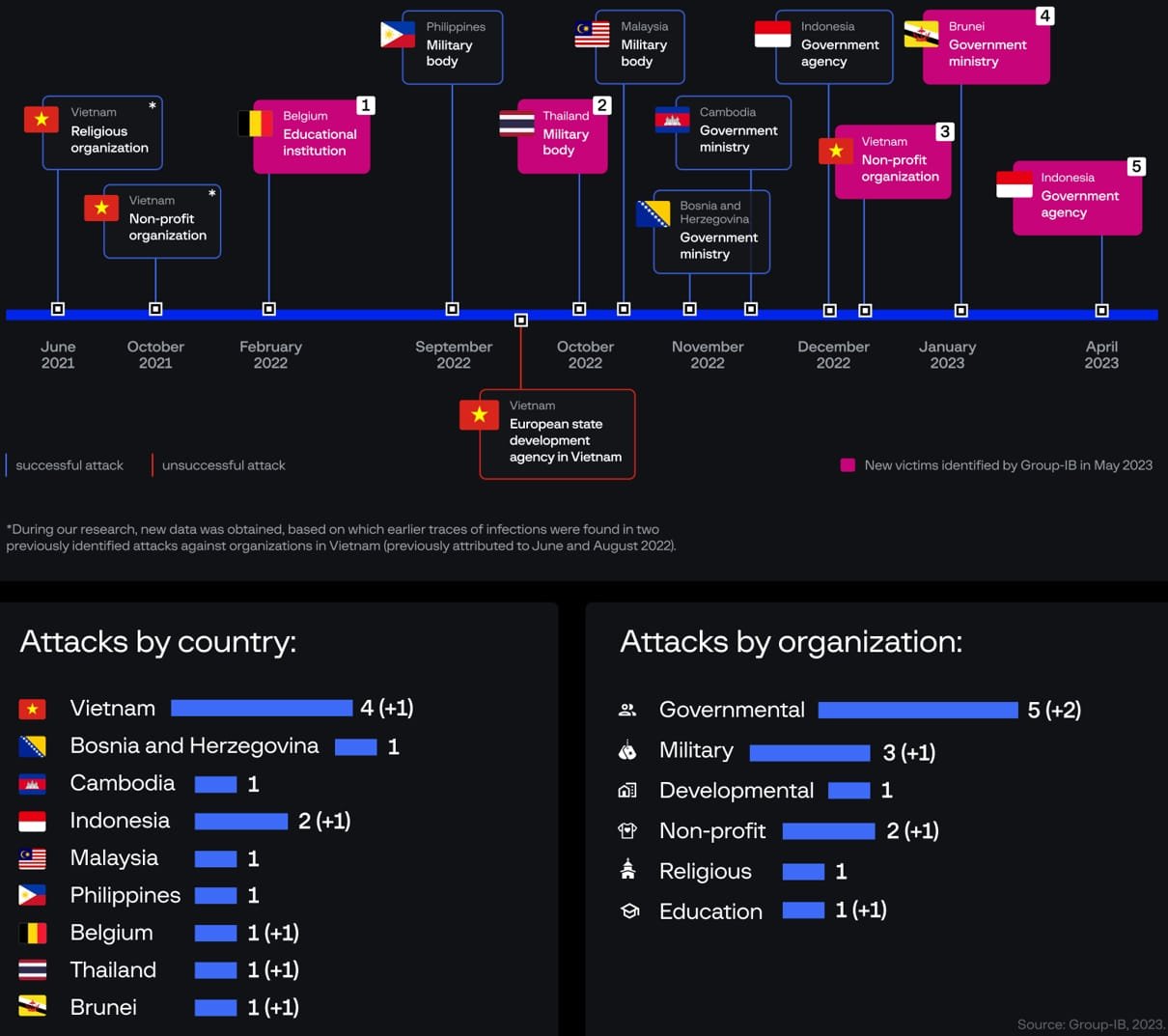
Despite the previous exposure by Group-IB, Dark Pink has not shown any signs of slowing down, and the company says it identified at least five attacks perpetrated by the group following the publication of the previous report.
In the recent attacks, Dark Pink showcased a revamped attack chain, implemented different persistence mechanisms, and deployed new data exfiltration tools, likely attempting to dodge detection by distancing their operations from publicly available IoCs (indicators of compromise).
Infiltration and lateral movement
Dark Pink attacks continue to rely on ISO archives sent via spear-phishing for initial infection, which employs DLL side-loading to launch its signature backdoors, ‘TelePowerBot’ and ‘KamiKakaBot.’
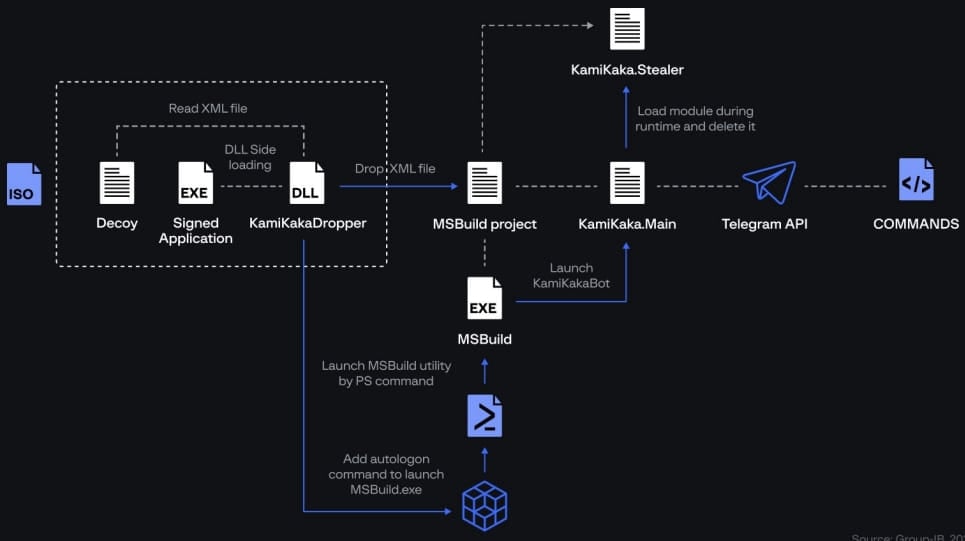
A new element is that the attackers have now split KamiKakaBot’s functionalities into two parts, namely device control and data theft.
Also, the implant is now loaded from memory, never touching the disk. This helps evade detection as antivirus tools do not monitor processes that initiate in memory.
KamiKakaBot continues to target data stored in web browsers and sends it to the attackers via Telegram. Moreover, the backdoor can download and execute arbitrary scripts on the breached device.
Group-IB discovered that Dark Pink uses a private GitHub repository to host additional modules downloaded by its malware to compromised systems.
The threat actors performed only 12 commits on that repository throughout 2023, mainly to add or update malware droppers, PowerShell scripts, the ZMsg info-stealer, and the Netlua privilege escalation tool.
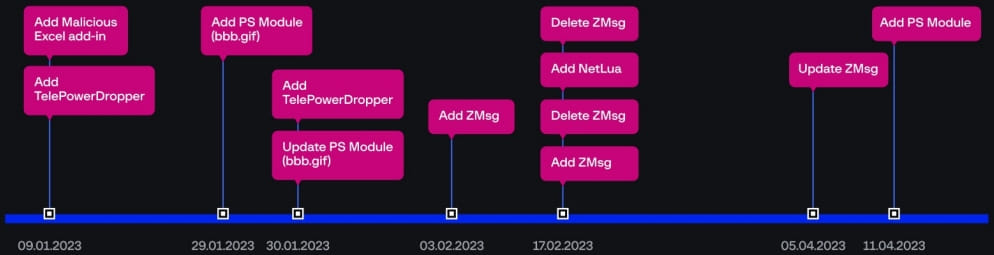
One of these PowerShell scripts is critical to Dark Pink’s lateral movement strategy, helping identify and interact with SMB shares within the network.
The script fetches a ZIP archive from GitHub, saves it to a local directory, and then creates LNK files on each SMB share linked to the malicious executable in the archive.
When these LNK files are opened, they launch the malicious executable, furthering Dark Pink’s propagation across the network and extending their reach to additional systems.
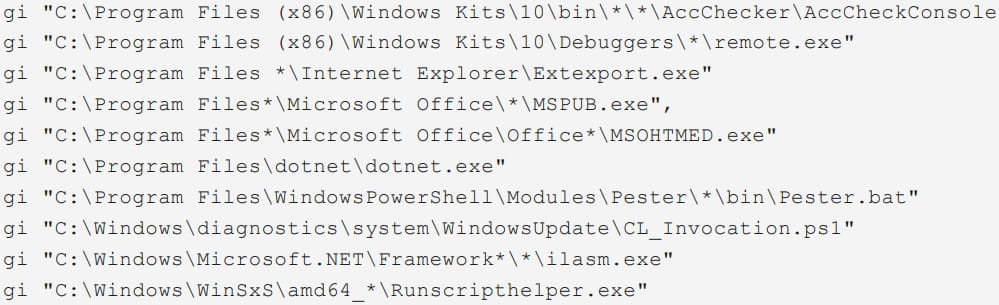
Dark Pink also uses PowerShell commands to perform checks for the presence of legitimate software and development tools on the compromised device that they can abuse for their operations.
These tools include ‘AccCheckConsole.exe,’ ‘remote.exe,’ ‘Extexport.exe,’ ‘MSPUB.exe,’ and ‘MSOHTMED.exe,’ which can be exploited for proxy execution, downloading additional payloads, and more.
However, Group-IB notes that it has not seen examples of abuse of these tools in the observed attacks.
New data theft tactics
Group-IB reports that Dark Pink now demonstrates variety in its data exfiltration method, going beyond sending ZIP archives to Telegram channels.
In some cases seen by the analysts, the attackers used DropBox uploads, while in others, they used HTTP exfiltration using a temporary endpoint created with the “Webhook.site” service or Windows servers.
The scripts mentioned earlier also feature the ability to exfiltrate data by creating new WebClient objects to upload files to an external address using the PUT method after defining the location of the target files on the breached computer.
Group-IB concludes that the Dark Pink threat actors are not discouraged by their previous exposure and are unlikely to stop now.
Most likely, the attackers will continue to update their tools and diversify their methods as much as possible.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





