DDoS attacks shifting to VPS infrastructure for increased power

Hyper-volumetric DDoS (distributed denial of service) attacks in the first quarter of 2023 have shifted from relying on compromised IoT devices to leveraging breached Virtual Private Servers (VPS).
According to internet security company Cloudflare, the newer generation of botnets gradually abandoned the tactic of building large swarms of individually weak IoT devices and are now shifting towards enslaving vulnerable and misconfigured VPS servers using leaked API credentials or known exploits.
This approach helps the threat actors build high-performance botnets easier and often quicker, which can be up to 5,000 times stronger than IoT-based botnets.
“The new generation of botnets uses a fraction of the amount of devices, but each device is substantially stronger,” explains Cloudflare in the report.
“Cloud computing providers offer virtual private servers to allow start ups and businesses to create performant applications. The downside is that it also allows attackers to create high-performance botnets that can be as much as 5,000x stronger.”
Cloudflare has been working with key cloud computing providers and partners to crack down on these emerging VPS-based threats and says it has succeeded in taking down substantial portions of these novel botnets.
Q1 ’23 DDoS landscape
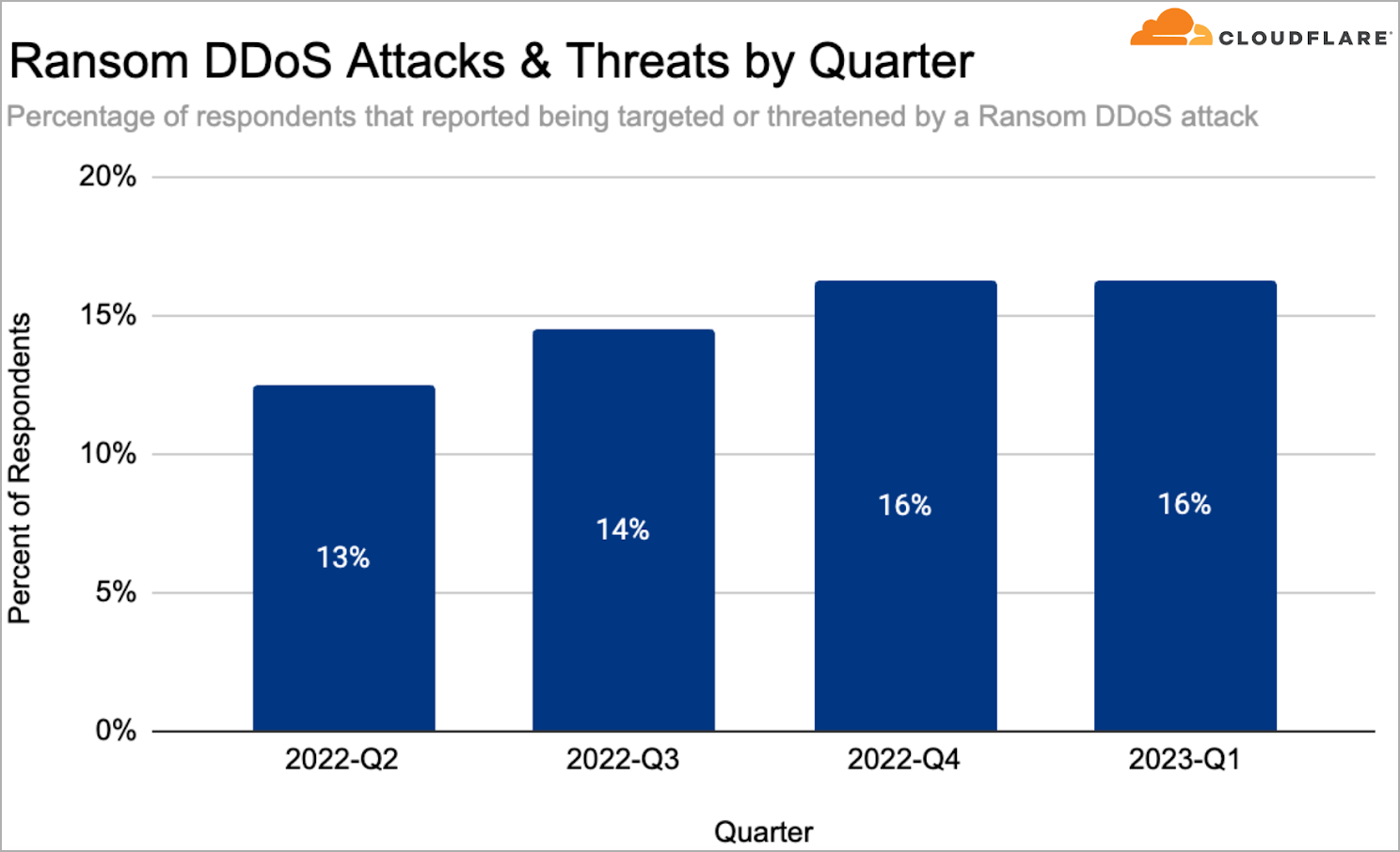
In general, Cloudflare reports steady DDoS activity in the first quarter of the year, with a notable 60% YoY increase in the ransom DDoS attacks, representing 16% of all recorded/reported DDoS attacks.
These extortion-based DDoS attacks cause service outages to the target by bombarding them with garbage traffic and continue indefinitely until the victim meets the attacker’s demands.
The most targeted country by DDoS attacks in general during Q1 ’23 was Israel, followed by the United States, Canada, and Turkey. Internet services, marketing, software, and gaming/gambling were the most targeted sectors.
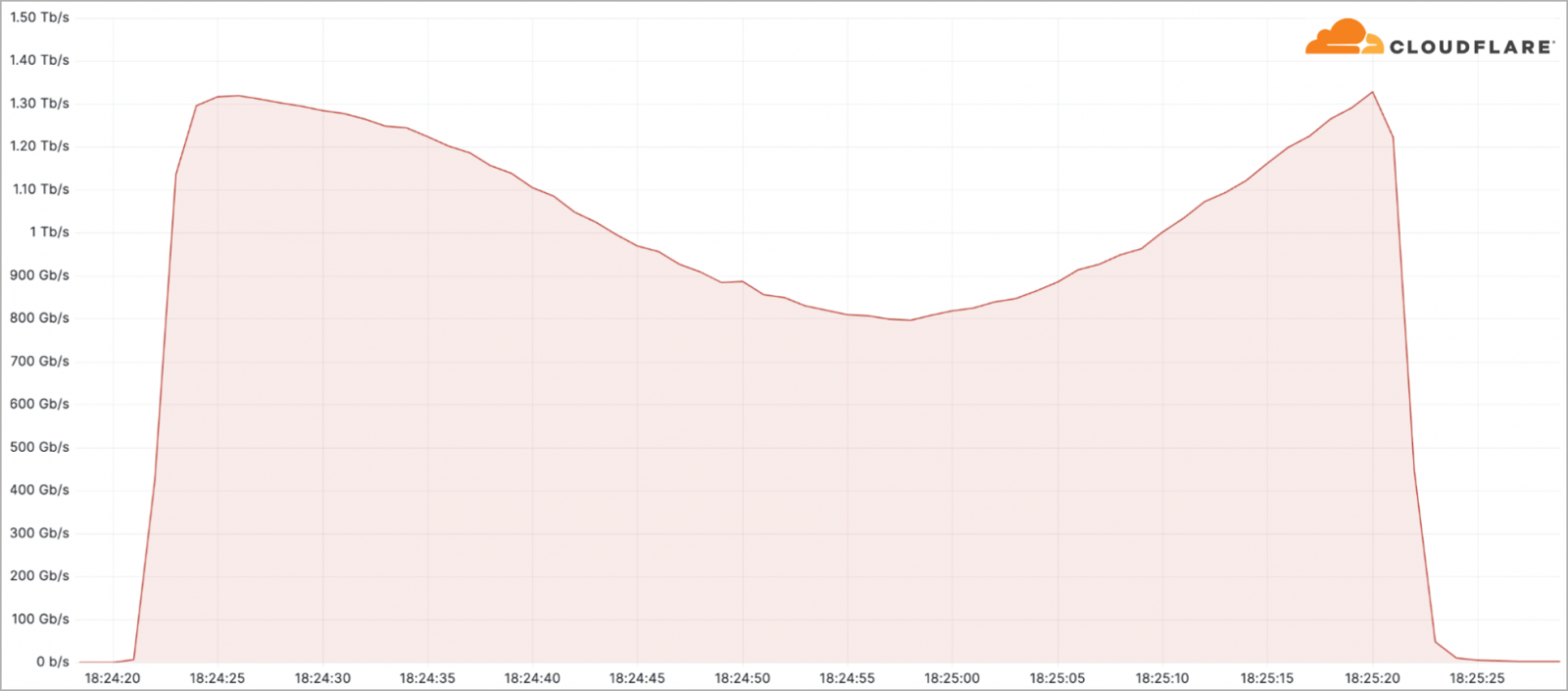
The most significant attack seen by Cloudflare this quarter peaked above 71 million requests per second. Another notable incident was a 1.3 terabits per second DDoS attack targeting a telecommunications service provider in South America.
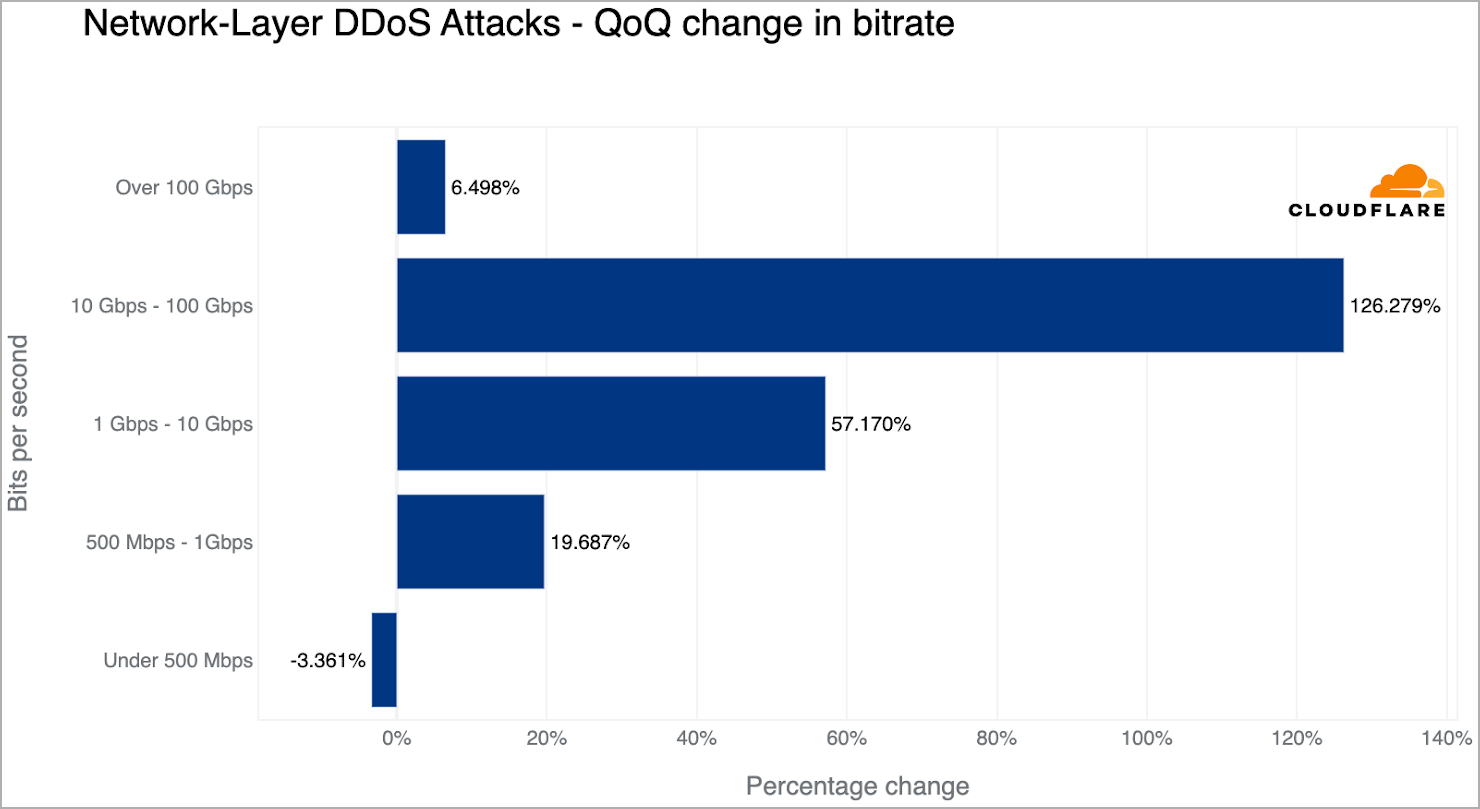
In terms of the size and duration of the attacks, most of them (86.6%) lasted for under 10 minutes, while 91% did not exceed 500 Mbps.
However, the number of larger attacks is still growing, with attacks surpassing 100 Gbps, recording a rise of about 6.5% compared to the previous quarter.
Emerging trends
DDoS attacks can manifest in many ways, and as defenses evolve to address them, attackers may devise new methods or return to old tactics that newer protection systems may not prioritize anymore.
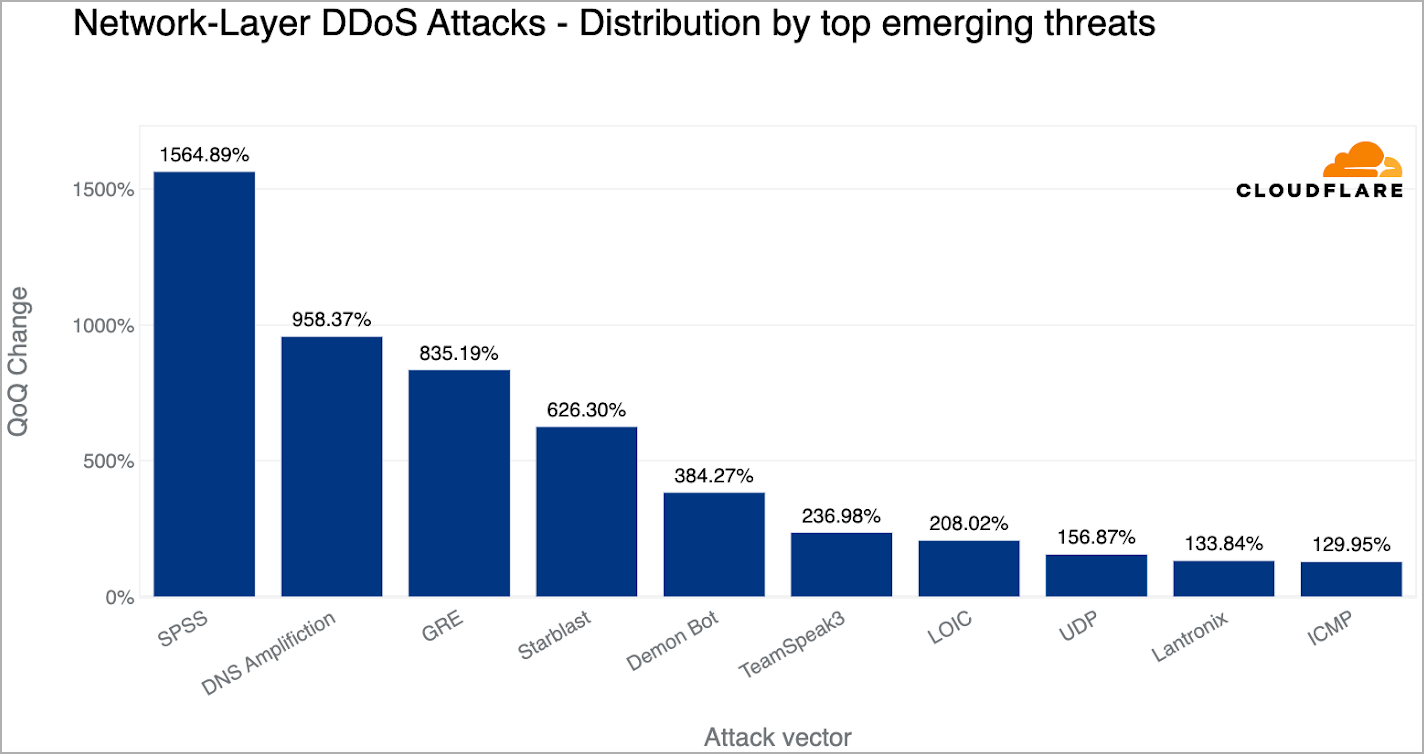
In this quarter, Cloudflare recorded the following emerging trends:
- 1,565% QoQ increase in SPSS (statistical product and service solutions) based DDoS attacks. This is fueled by the exploitation of two flaws (CVE-2021-22731 and CVE-2021-38153) in the Sentinel RMS License Manager service, leveraged for launching reflection DDoS attacks.
- 958% QoQ rise in DNS amplification DDoS attacks, where the attackers exploit DNS infrastructure flaws to generate large amounts of traffic.
- 835% QoQ increase in GRE (generic routing encapsulation) based DDoS attacks, where attackers abuse the GRE protocol to flood the victim’s network with garbage requests.
DDoS attacks in Q1 2023 show a trend of increasing in size and duration, targeting a broad range of industries. Therefore, effective defense strategies require automated detection and mitigation solutions.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





![[SILENTRANSOMGROUP] - Ransomware Victim: Hall Estill 13 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

