DFIR via XDR: How to expedite your investigations with a DFIRent approach
Rapid technological evolution requires security that is resilient, up to date and adaptable.
In this article, we will cover the transformation in the field of DFIR (digital forensics and incident response) in the last couple years, focusing on the digital forensics’ aspect and how XDR fits into the picture.
Before we dive into the details, let’s first break down the main components of DFIR and define the differences between them.
Digital Forensics vs Incident Response#
- Digital forensics: the practice of using scientific techniques and tools to identify, preserve, and analyze digital evidence from various sources, such as computers, smartphones, and other electronic devices, in a way that is admissible in a court of law.
- Incident response: the process of responding to and managing the aftermath of a security breach or cyberattack. This involves identifying the nature and scope of the incident, containing the damage, eradicating the threat, and restoring the affected systems.
In summary, digital forensics focuses on the longer-term investigation and the detailed analysis of digital evidence, while incident response involves the immediate and short-term response to a security incident.
Traditional Digital Forensics#
Regular crime forensics and digital forensics are closely related disciplines, as both are used to investigate crimes and uncover evidence.
Regular crime forensics is used to analyze physical evidence collected from crime scenes and can include fingerprinting, blood analyses, and other forms of physical evidence.
Digital forensics is used to analyze digital evidence collected from computers, phones, and other digital devices. This evidence includes log files, deleted files, and other digital artifacts.
The two disciplines are related in that they both rely on a thorough analysis of evidence to uncover clues and identify potential suspects. Physical evidence can provide key information about a crime scene, such as the location of the crime, the time of the crime, and the identity of the perpetrator.
Digital evidence can provide even more detailed information, such as emails, chat messages, and other documents that can reveal the identity of the perpetrator, as well as their intentions and plans.
Regular crime forensics and digital forensics also work together in many cases. For example, physical evidence can be used to identify a suspect, and then digital evidence can be used to further investigate the suspect’s actions and intentions.
The use of digital forensics has a long history that dates to the early days of computing and has continued to evolve and expand as technology has advanced.
Invented by law enforcement, the original motivation was to investigate crimes involving computers or digital devices.
The traditional process includes the following steps:
- First response: as soon as a security incident is reported, the DFIR team needs to reach the customer onsite to contain the attack and collect evidence.
- Identification: while the DFIR team is onsite they need to identify the involved devices in the incident.
- Preservation: collecting and storing the data using different forensic methods and tools.
- Analysis: an examination of the evidence collected.
- Documentation and reporting: after the investigation is done, the DFIR team creates a report that summarizes the incident.
Using digital forensics tools & techniques we can:
- Identify the root cause of the incident
- Create a timeline of events on the attack chain
- Recover deleted data
- Prove certain activity occurred such as data theft or system breach
Each phase of the process can be divided into many sub-phases but, for now, I want to focus on the Preservation phase.
In this phase the DFIR team collects the data they will work on during the investigation. The most comprehensive acquisition you can collect from a machine is a combination of:
- Disk image – a copy of the entire contents of a storage device. Its size will correspond to the size of the hard drive of the machine we acquire the data from
- Memory image – a snapshot of the memory of the machine. It will contain data on any running processes, network connections, etc., from the boot until the capture. The size of the image will correspond to the amount of RAM (random access memory) the machine has.
Traditionally, DFIR teams would acquire a forensic image by going to the customer site, physically approaching the machines, and creating a bit-by-bit duplicate of their hard drives while using a write blocker.
A write blocker is a device that prevents any changes to the hard drive to facilitate the legal defensibility of the forensic image.
After the team acquired the forensic images, they return to their DFIR lab where they have powerful machines that can process terabytes of images.
Today’s Struggle with Traditional DFIR Approach #
In this section, I’ll explain why, nowadays, it is harder and inefficient (sometimes) to follow the traditional approach to DFIR.
Time = Money#
The bottom line is: the longer the investigation will take, the more resources (people, time, money) will be spent.
- Most DFIR services charge hourly rates.
- The organization is losing money if the company assets/services are not available to customers/employees.
Organizations Become Enterprises and the Technology Keeps Evolving#
Digital forensics is based on evidence collected from the machines involved in the incident. Two main variables changed significantly during recent years:
- The average number of endpoints per organization.
- Hard drive capacity per endpoint.
The number of endpoints per organization continues to grow. Recent research found that the average U.S enterprise is running 135,000 endpoints, thus directly influencing the number of endpoints impacted in each incident. More compromised endpoints means the DFIR team must collect evidence from more devices.
The fact that the technology today is evolving, and the average hard drive capacity expanded significantly, influenced the process as well.
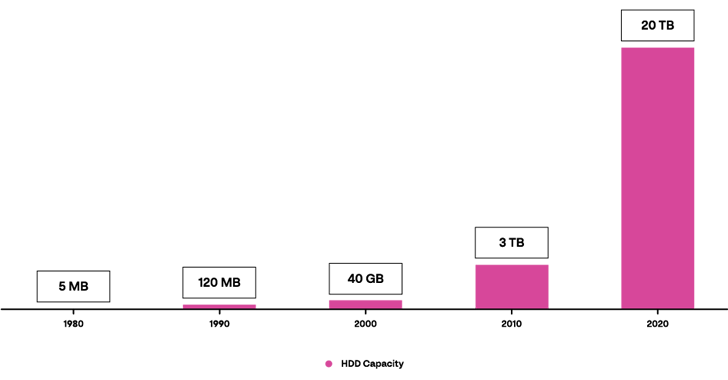 |
| HDD Capacity by Year |
Cloning a 20 terabytes disk can take many hours. Then processing it takes a long time too. After that, imagine you find indicators of connection from another machine and you need to go over this process, again and again. It doesn’t sound so efficient, and the time consumed is costly. Below are a few stats about money lost during incident response.
Money lost is due to a few factors:
- Operational downtime
- Reputational damage
- Legal costs
According to Gartner, a technological research and consulting firm based in Stamford, Connecticut, that conducts research on technology and shares this research both through private consulting as well as executive programs and conferences, the average cost of an downtime for an IT company is $5,600 per minute. This average can vary between organizations.
COVID-19 – no flights#
DFIR is among the many fields enormously influenced by COVID-19. During the pandemic’s peak, the skies were practically closed for civilian transportation, and DFIR teams couldn’t reach their customers’ sites when an incident occurred.
The need for remote working created new challenges for incident responders, such as how to securely access and investigate systems without physical access.
Modern Acquisition Approach#
As the volume and cost of cyber-related incidents has spiked in the recent years, so too has demand for incident investigations.
To adjust, the DFIR community had to reduce investigation time in a way that doesn’t harm the quality of delivered services and materials.
Investigation time is mainly comprised of:
- Acquisition Time: the time it takes to gather the evidence on the compromised machines.
- Transferring Time: the time it takes to deliver the evidence from the compromised machines to the DFIR team labs.
- Processing Time: the time it takes to parse the evidence using various DFIR tools.
- Analysis Time: the time it takes to investigate the parsed evidence and reach conclusions.
Full Disk Image is the Last Resort#
The original idea behind acquiring a full disk image is the fact it has the entire contents of a storage device so you’ll have every piece of data that could be affected during the incident, in addition to the various data sources and artifacts that need to be collected for forensic analysis.
When the investigation is conducted for law enforcement cases, for example, and in cases where there are no time constraints, collecting a full disk image may be the correct approach. However, I can safely say that a full disk image is not a necessity in 100% of the cases investigated by DFIR teams.
The amount of evidence collected influences every step in the investigative process, increasing how long it take to acquire, transfer, process, and analyze the data before, ultimately, reaching a conclusion.
Surgical Approach#
Thanks to the amazing DFIR community, various effective forensic tools can be used to automate and customize the acquisition process. You can create your own artifacts list that you want to collect according to the attack scenario.
The goal is to reduce overall investigation time by minimizing the amount of evidence to collect.
The most-known and dominant tool in the market for artifact collection is KAPE (Kroll artifact parser and extractor). Using it, you can collect and/or parse artifacts from a machine you want to investigate. According to your experience, you can use predefined lists of artifacts that need to be collected or make your own.
The idea behind these tools is, again, to reduce the size of the artifacts that need to be collected.
To achieve this goal, instead of collecting the entire hard disk, these tools collect specific files/folders which contain crucial digital evidence such as:
- Process Execution
- File Creation
- File/Folder Opening
- Deleted Files
- Browser Usage
To emphasize the differences, from my experience, when using KAPE to acquire evidence from a machine with 512 GB HDD, the output is 2-4 GB, which should be a great starting point for your investigation (producing enough visibility and allowing initial analysis and response). But, at the end of the day, it depends on the evidence collected.
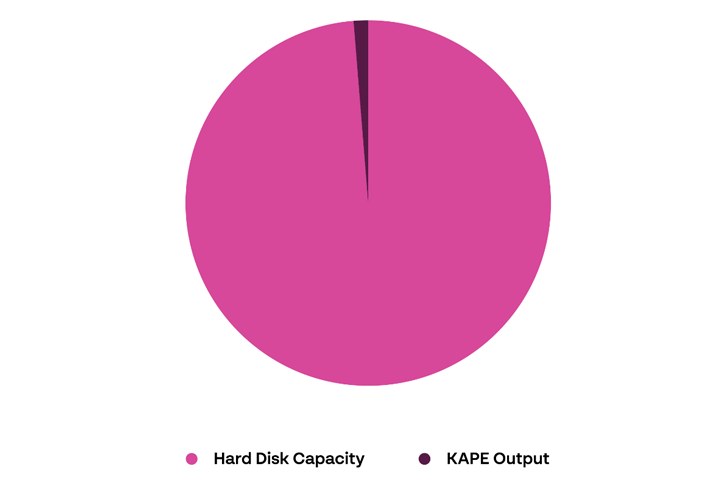 |
| Relevant Artifacts for Initial Acquisition |
Memory Image is the New Black#
If you’ll ask a DFIR analyst what the saddest response / phrase he can receive from a client, the answer will be: “we have shut down all the involved machines”.
RAM (Random Access Memory) is a volatile data source that is ruined in a shutdown event.
Memory forensics is one of the most efficient methods to perform forensic analysis, it contains information from the boot until the capture, such as:
- Executed process:
- Process id
- Parent process
- Execution time
- Command line
- Termination time
- Many additional valuable properties
- Network connections:
- IP addresses + ports
- Processes that established connection
- Files:
- NTFS timeline
- Files extraction from memory
- Threads and handles
- Memory access between processes
- Process injection
And that list is far from complete. Memory forensics is its own topic that should be covered in a separate article.
It depends on the logging policies of the machine, but there are many cases where the data you can extract, and the conclusions you can make from a memory image analysis, can’t be achieved from disk image forensics.
The message is that a memory image is one of the best data sources you can acquire from a compromised machine and its size is significantly small in comparison to a full disk image.
Investigation Time Comparison#
Disclaimer – In the following calculation, I focus on differences in the investigation time when relying on different data sources and I didn’t even compare the differences between physical acquisition (yes, still happening) to remote acquisition, which dramatically decreases the overall investigation time and allows DFIR professionals to handle and respond to incidents on a completely different scale.
To better emphasize the differences between investigation time when relying on different data sources, I created the following visualization. It’s important to mention that the time factor presented is an average calculation; many components can influence the calculation and, in turn, affect the investigation and response efforts.
For this comparison, I used a machine with the specifications of an average employee computer; 512 GB HDD and 16 GB RAM.
Naturally, servers that store more data or serve many clients can be heavier in terms of HDD and RAM.
The transferring time is calculated by a 20 Mbps upload speed
As you can see, the size of the evidence collected from a machine influences the overall investigation time.
When using memory images or specific digital evidence instead of the entire hard disk, we can reduce overall investigation time by more than 90%.
In summary, digital forensic investigation is a long process, and we need to make it as efficient as possible.
Next time, before acquiring anything, think carefully about what you need to collect from a machine at the beginning of the investigation.
DFIR via XDR#
XDR solutions provide to DFIR professionals the ability to automate different steps for many DFIR scenarios and processes, such as collecting evidence, analyzing data, and responding to threats. This, in turn, allows DFIR professionals to save time and resources while focusing on high-priority tasks.
In an ideal scenario, your security solution provides you with enough visibility, through its telemetry and logging capabilities, that you won’t need to collect and analyze additional artifacts from a compromised machine.
With the right product, all the data needed for your investigation should be there, waiting for your analysis. Needless to say, that reduces investigation time significantly.
Today, there is no doubt that XDR is a necessary feature of your security arsenal.
In this section, I won’t focus on XDR detection and prevention, but on why Cynet 360 AutoXDR is crucial to managing DFIR investigations:
- Data lake creation
- Efficient acquisition
- Taking actions at scale
Data lake creation#
It’s important to understand that there isn’t a bulletproof security product; there is always the possibility that a previously undiscovered attack vector could penetrate a network.
That said, we must ensure we have a security solution to view endpoint events in order to understand how a breach occurred — and how security posture can be improved moving forward.
The equation is simple: the more data and logs the DFIR team has when they approach an investigation, the less time and money it will take to reach a conclusion.
Cynet 360 AutoXDR generates data telemetry on endpoints, with visibility of events such as:
- Process execution
- File creation
- Writing files
- Reading files
- Network connections
These types of data should be enough to understand what occurred on a machine and the steps required to eradicate the threat, even without acquiring additional artifacts from it.
Efficient Acquisition#
In case additional artifacts are needed to reach conclusions (usually if a Cynet agent wasn’t installed or best practices weren’t followed), you can use Cynet 360 AutoXDR’s custom remediations to deploy, execute, and collect the output of any desired DFIR tool in a few simple clicks.
You can create your own time-saving arsenal of DFIR tools that will be ready to use in case of an incident. For example, custom remediation for memory image collection or for an artifact collector such as KAPE.
Even if a certain machine wasn’t protected by a security solution before infection, you can deploy Cynet 360 AutoXDR to ensure protection moving forward and launch your investigation by acquiring artifacts and executing DFIR tools in a matter of minutes.
Taking actions at scale#
The fact that you can take actions on many machines in parallel reduces the investigation time significantly, from acquisition to conclusion to remediation.
Conclusion#
Overall, the DFIR field generally and digital forensics specifically have changed much in recent years. By following these guidelines, you can ensure a more efficient investigation of the next incident response you face:
- Proactively plan your acquisition and cut down unnecessary extraction and investigation time with a predefined list of artifacts to acquire and investigate for each attack scenario.
- Remote DFIR is no longer a “nice-to-have” capability. Nowadays, on the heels of Covid-19 pandemic and the restrictions it introduced, remote acquisition, investigation, and response capabilities are mandatory.
- Data lake: the goal is to reduce investigation time. By having rich telemetry, generated by a security solution and available to support the DFIR team at the very beginning of the investigation, we can reduce the investigation time significantly.
- XDR as a “go to” for your DFIR needs. Use a single security solution that provides relevant telemetry to support your investigation and incorporates capabilities that allow you to take actions at scale, such as acquisition, DFIR tools execution and usage, as well as carrying out remediation actions.
Ready to see this approach in action? Watch as Asaf Perlman, Cynet’s battle-tested IR Leader, walks through real-life scenarios, sharing conclusions and pro tips to help you master the art of DFIR with XDR.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.