Duo of Android dropper and payload target certain countries and app users
After making its first in-the-wild appearance in March 2021, Vultur—an information-stealing RAT that runs on Android—is back. And its dropper is equally nasty.
Vultur (Romanian for “vulture”) is known to target banks, cryptocurrency wallets, social media (Facebook, TikTok), and messaging services (WhatsApp, Viber) to harvest credentials using keylogging and screen recording.
According to ThreatFabric, the mobile security company that first spotted Vultur in 2021, the cybercriminals behind the malware have steered away from the common HTML overlay strategy usually seen in other Android banking Trojans. This approach usually requires time and effort for the attackers in order to steal what they want from the user. In steering away from this, the attackers made less effort but yielded the same results.
One of the Android dropper malware that drops Vultur (among others) is Brunhilda, a privately operated dropper. Initial variants of Vultur have been dropped by an Android app called “Protection Guard”, which have had 5,000 installs on the Google Play Store upon its discovery. Note, however, that there are many Brunhilda dropper apps on the Store, which suggests that infection count could be a lot higher.
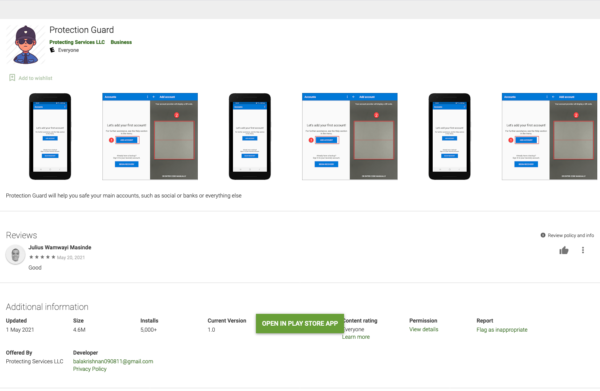
ThreatFabric believes that the group behind this dropper and Vultur are one and the same. The company has linked the two for the following reasons:
- The command and control server (C2) of “Project Brunhilda” supports Vultur-specific bot commands
- Vultur is seen using the same C2 that Brunhilda used in the past
- Vultur is seen using the same icon and package name of a Brunhilda dropper
- Vultur uses JSON-RPC to communicate with its C2, a tactic that Brunhilda used to do
Moreover, the group behind Vultur can see every interaction the user does to their device, thanks to the real-time implementation of VNC (Virtual Network Computing) screen sharing. This a legitimate tool that allows one to remotely control a device, so whatever the user sees on his phone screen, the actors can see it, too. However, for VNC to work properly, Vutur uses ngrok, another legitimate tool that uses an encrypted tunnel to expose local systems behind firewalls and NATs (network address translation) to the public Internet.
Nasty new malware dropper spreads Vultur
Recently, researchers from Pradeo, another mobile security solutions provider, found a fresh variant of Vultur after they spotted a fake two-factor authenticator (2FA) app on the Google Play Store. The dropper app, aptly named “2FA Authenticator” is responsible for dropping Vultur onto Android devices. Pradeo didn’t specify in its report if this dropper app is Brunhilda.
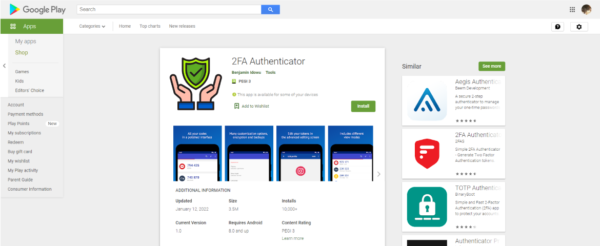
“2FA Authenticator”, as Pradeo noted, used the open source code of the Aegis Authenticator app, a legitimate 2FA authenticator with a presence in the Play Store, but that had been modified to include malicious code. Users are likely to be less suspicious of apps that appear to be working as they should.
Creating a dropper malware that also works is a tactic not unheard of as this is also used by another Android malware called BRATA.
The automated Vultur attack comes in two stages: first is profiling. The dropper prompts the user for consent to access critical permissions which were never disclosed in its Play Store profile. These are:
- Take pictures and videos. This allows the dropper to collect information, such as application list and localization, about the user which the attackers can use to target other users in specific countries using certain applications.
- Disable your screen lock. This disables any form of phone security (passwords, unlock pattern) set up by the user.
- Full network access. This allows the dropper to download other third-party apps under the guise of updates.
- Run at startup. This allows the dropper to freely perform tasks even when the app is shut down.
- Draw over other apps. This allows the dropper to change the interface of other mobile apps—a permission that “very few apps should use”, according to Google.
- Prevent device from sleeping. This allows the dropper to continue running in the background.
The second stage is the installation of Vultur. Pradeo has noted that the dropper doesn’t just drop Vultur once it is executed. Instead, the attack escalates to this stage if the information the dropper has collected meets certain conditions.
If you have downloaded an app that you suspect could be malicious, go to Settings > Apps. Look for “2FA Authenticator” in the list and delete it.
Stay safe!
The post Duo of Android dropper and payload target certain countries and app users appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[INCRANSOM] - Ransomware Victim: State Bar of Texas (www[.]texasbar[.]com) 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)