Encryption Flaws Allow Hackers to Steal Vehicles without Leaving a Trace

New vulnerabilities were revealed earlier this week in the encryption frameworks utilized by immobilizers, the radio-enabled gadgets within cars that usually communicate at short range with a ‘key fob’ to easily unlock the car’s ignition and permit it to start as discovered by researchers from KU Leuven in Belgium and the University of Birmingham in the UK.
Issues were particularly identified in Toyota, Hyundai, and Kia who utilize and further implement a Texas Instruments encryption system called DST80. Aside from these, a couple of other influenced vehicles incorporate Camry, Corolla, and RAV4; Kia Optima, Soul, and Rio; the full rundown of vehicles that the researchers have found to have the cryptographic defects in their immobilizers is below:
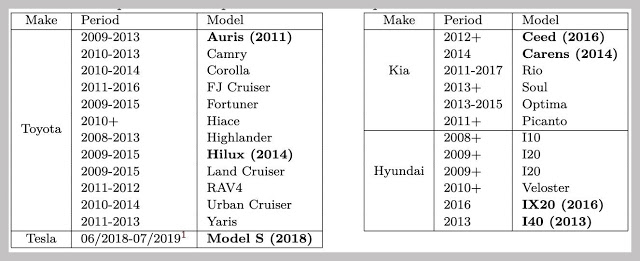
In spite of the fact that the list likewise incorporates the Tesla S, the researchers announced the DST80 vulnerability to Tesla a year ago, and the company pushed out a firmware update that blocked the assault. Toyota has affirmed that the cryptographic vulnerabilities the researchers discovered are genuine.
Be that as it may, their technique likely isn’t as simple to pull off as the “relay” attacks that thieves have utilized over and overused to steal luxury cars and SUVs. Those, by and large, require just a couple of radio devices to expand the range of a key fob to open and start a victim’s vehicle. One can pull them off from a reasonable distance, even though the walls of a structure.
The researchers built up their key cloning technique by purchasing an assortment of immobilizers’ electronic control units from eBay and reverse engineering the firmware to break down how they communicated with key fobs. They regularly saw it far as too simple to even consider cracking the secret value that Texas Instruments DST80 encryption utilized for authentication.
Anyway, the issue lies not in DST80 itself however in how the carmakers implemented it: The Toyota fobs’ cryptographic key depended on their serial number, for instance, and furthermore openly transmitted that serial number when checked with an RFID reader. What’s more, Kia and Hyundai’s key fobs utilized 24 bits of randomness instead of the 80 bits that the DST80 offers, making their secret values simple to figure. At the point when the affected carmakers and Texas Instruments were reached out for comments, Kia and Texas Instruments didn’t respond.
Be that as it may, Hyundai noted in a statement that none of its affected models are sold in the US. Toyota reacted in an explanation that “the described vulnerability applies to older models, as current models have a different configuration.”
In any case, the researchers have chosen to distribute their findings to uncover the genuine condition of immobilizer security and permit car owners to choose for themselves if it’s sufficient. Protective car owners with hackable immobilizers may choose, like whether or not to utilize a steering wheel lock or not.

