Exploits released for Linux flaw giving root on major distros

Proof-of-concept exploits have already surfaced online for a high-severity flaw in GNU C Library’s dynamic loader, allowing local attackers to gain root privileges on major Linux distributions.
Dubbed ‘Looney Tunables’ and tracked as CVE-2023-4911, this security vulnerability is due to a buffer overflow weakness, and it affects default installations of Debian 12 and 13, Ubuntu 22.04 and 23.04, and Fedora 37 and 38.
Attackers can trigger it using a maliciously crafted GLIBC_TUNABLES environment variable processed by the ld.so dynamic loader to gain arbitrary code execution with root privileges when launching binaries with SUID permission.
Since Qualys’ Threat Research Unit disclosed it on Tuesday, several security researchers have already published proof-of-concept (PoC) exploit code that works for some system configurations.
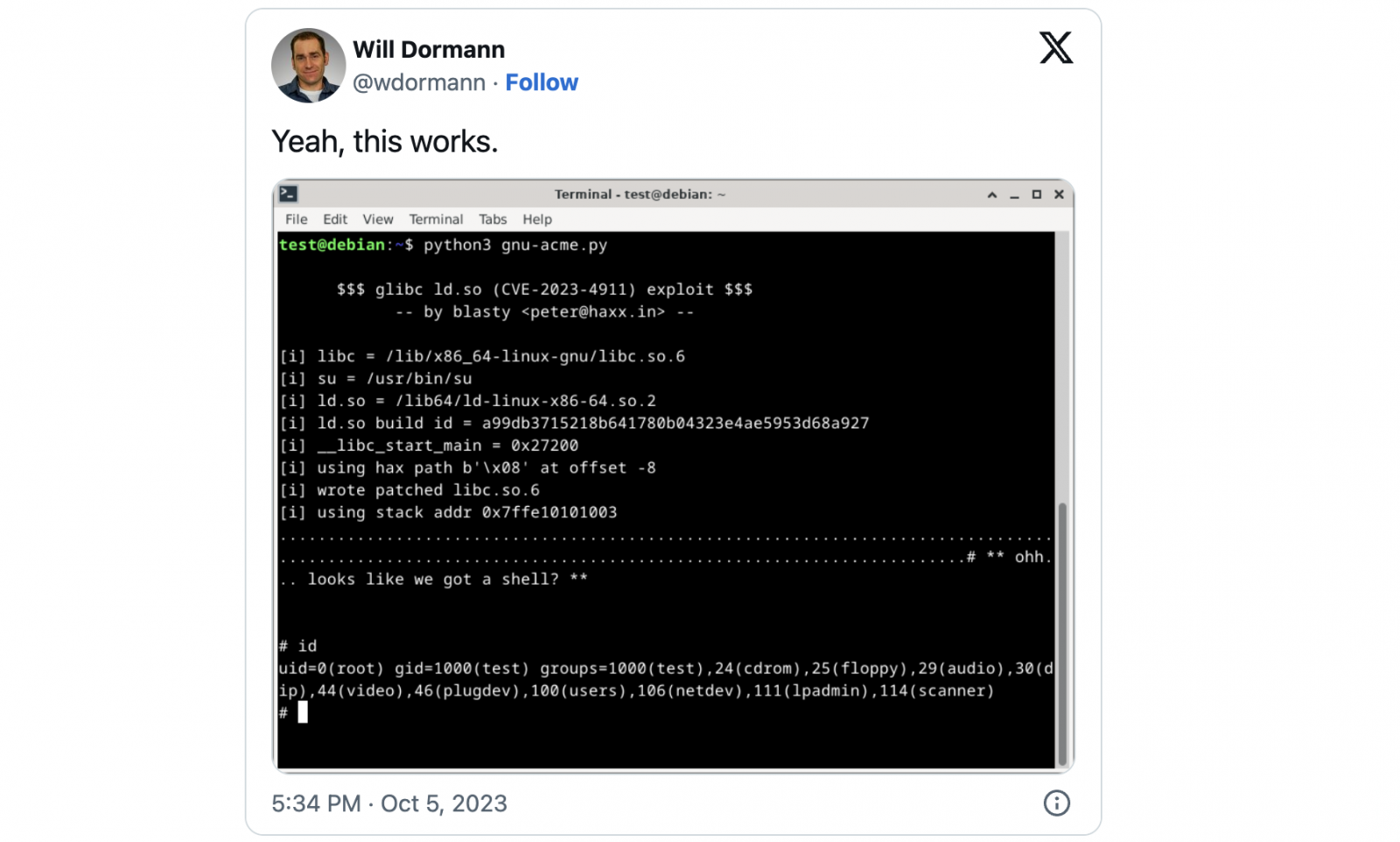
One of these PoC exploits, confirmed as working by vulnerability and exploit expert Will Dormann, was released by independent security researcher Peter Geissler (blasty) earlier today.
While his exploit can be used against a limited number of targets, the PoC also includes instructions on adding additional ones by identifying workable offset for each system’s ld.so dynamic loader.
Other researchers are also developing and rapidly releasing their own CVE-2023-4911 exploits on GitHub and elsewhere, although BleepingComputer has yet to confirm they’re working.
Administrators must act promptly due to the significant threat posed by this security flaw, which grants complete root access to systems running the latest releases of widely used Linux platforms, including Fedora, Ubuntu, and Debian.
While Alpine Linux admins, a distro unaffected by this vulnerability, don’t have to worry about patching their systems, those on other affected systems must prioritize patching to safeguard their systems’ integrity and security.
“Our successful exploitation, leading to full root privileges on major distributions like Fedora, Ubuntu, and Debian, highlights this vulnerability’s severity and widespread nature,” said Saeed Abbasi, Product Manager at Qualys’ Threat Research Unit, on Tuesday.
“Although we are withholding our exploit code for now, the ease with which the buffer overflow can be transformed into a data-only attack implies that other research teams could soon produce and release exploits. This could put countless systems at risk, especially given the extensive use of glibc across Linux distributions.”
Qualys researchers have found and disclosed other severe Linux security bugs in recent years, including a flaw in Polkit’s pkexec component (dubbed PwnKit), one in the Kernel’s filesystem layer (dubbed Sequoia), and another in the Sudo Unix program (aka Baron Samedit).
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.