Fake Linux vulnerability exploit drops data-stealing malware

Cybersecurity researchers and threat actors are targeted by a fake proof of concept (PoC) CVE-2023-35829 exploit that installs a Linux password-stealing malware.
Uptycs analysts discovered the malicious PoC during their routine scans when detection systems flagged irregularities such as unexpected network connections, unauthorized system access attempts, and atypical data transfers.
Three repositories were found hosting the malicious fake PoC exploit, with two removed from GitHub and the remaining one still live.

Uptycs reports that the bad PoC has been widely shared among members of the security research community, so infections might exist on a significant number of computers.
Malicious PoC details
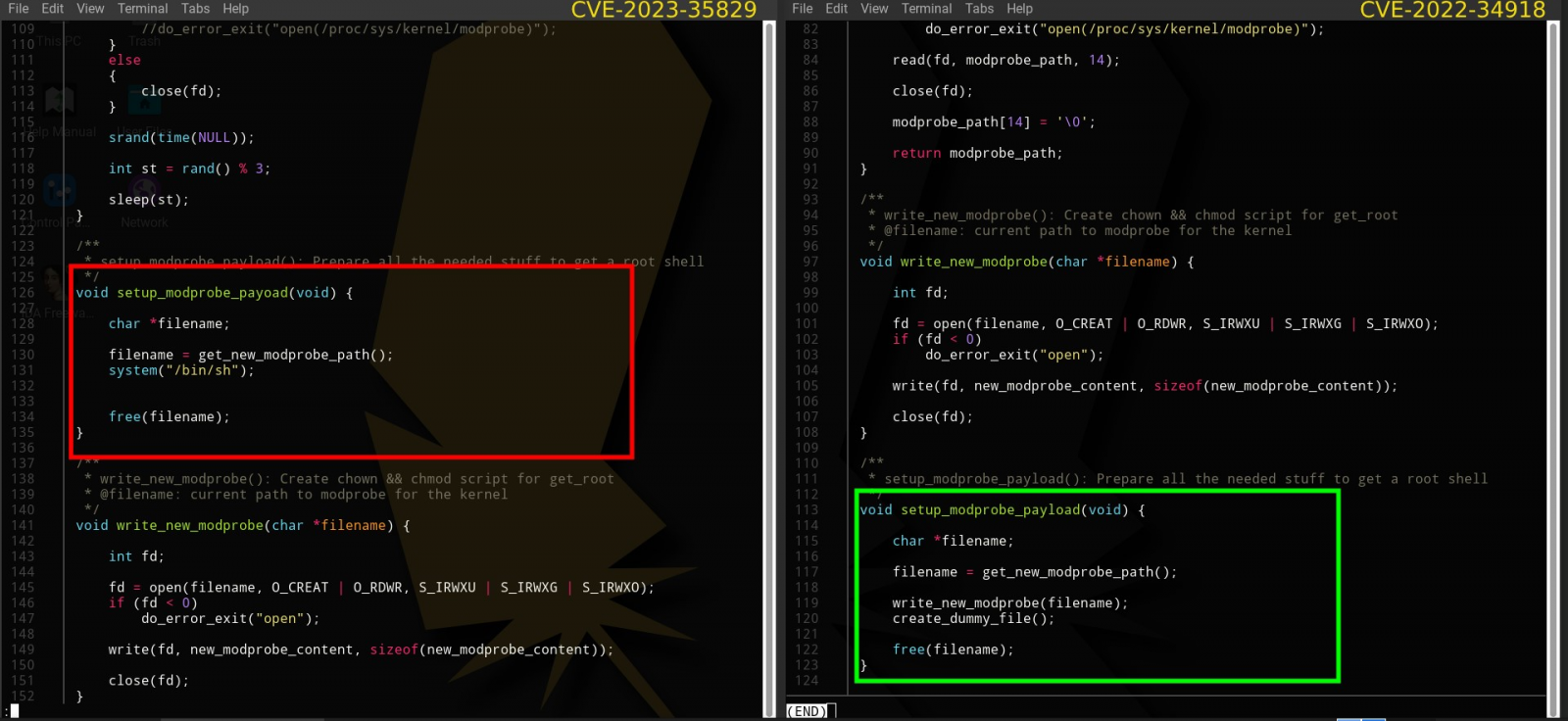
The fake PoC claims to be an exploit for CVE-2023-35829, a high-severity use-after-free flaw impacting the Linux kernel before 6.3.2.
In reality, though, the PoC is a copy of an old, legitimate exploit for another Linux kernel vulnerability, CVE-2022-34918.
The code takes advantage of namespaces, a Linux feature that partitions kernel resources, to give the impression that it’s a root shell, even though its privileges are still limited within the user namespace.
This is done to reinforce the illusion that the exploit is genuine and working as expected, giving the attackers more time to roam freely on the compromised system.
Upon launch, the PoC also creates a ‘kworker’ file and adds its path to the ‘/etc/bashrc’ file for persistence.
Next, it contacts the attacker’s C2 server to download and execute a Linux bash script from an external URL.
The downloaded script accesses the ‘/etc/passwd’ file to steal valuable data from the system, modifies the ‘~/.ssh/authorized_keys’ to grant the attacker unauthorized remote access to the server, and eventually uses curl to exfiltrate data via ‘transfer.sh’.
The script steals data that includes the username, hostname, and the contents of the victim’s home directory. However, as the threat now has remote access to the server, they can steal whatever they want manually.
The bash script disguises its operations as kernel-level processes to evade detection, as system administrators tend to trust them and generally don’t scrutinize those entries.
Don’t trust exploit code
Uptycs suggests that researchers who downloaded and used the fake PoC perform the following steps:
- Remove any unauthorized ssh keys
- Delete the kworker file
- Remove the kworker path from the bashrc file
- Check /tmp/.iCE-unix.pid for potential threats
PoCs downloaded from the internet should be tested on sandboxed/isolated environments like virtual machines and, if possible, have their code inspected before execution.
Submitting binaries to VirusTotal is also a quick and easy way to identify a malicious file.
Using fake PoCs to target researchers and threat actors with malware is not new.
Last month, VulnCheck analysts discovered a campaign where threat actors impersonated real researchers from trusted cybersecurity companies to push malware masquerading as zero-day exploits for Chrome, MS Exchange, and Discord.
In October 2022, university researchers published a technical paper explaining that up to 10.3% of all PoCs hosted on GitHub might be malware.
The North Korean Lazarus hackers are also believed responsible for a 2021 campaign using social media to target vulnerability researchers with fake PoCs that installed backdoors.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


