Fake ransomware warnings hit WordPress sites: How to stay safe
A ransomware warning has appeared out of nowhere and started taking over WordPress sites.
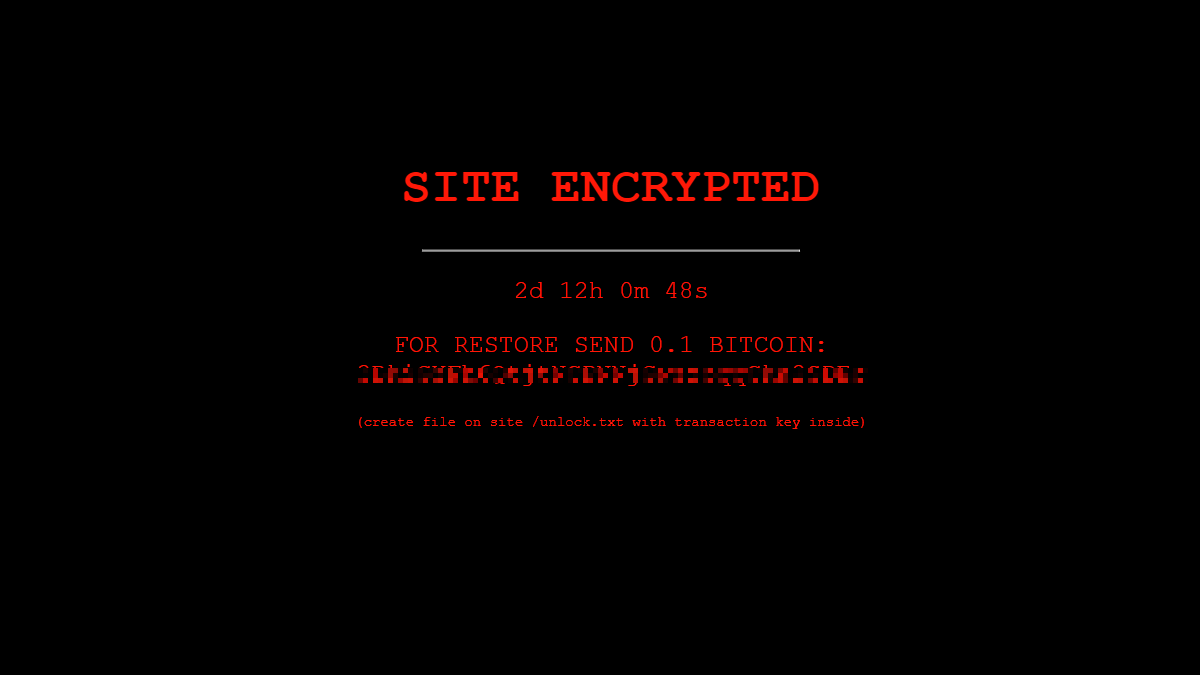
The warning, with its black background and red writing, says:
“SITE ENCRYPTED
{ Countdown }
FOR RESTORE SEND 0.1 BITCOIN:
[address redacted]
(create file on site /unlock.txt with transaction key inside)”
But there’s just one thing… the warning is a fake. There is no ransomware.
The ransomware that isn’t what it claims to be
The warning is clearly intended to scare the site owner into paying the 0.1 Bitcoin ransom amount, which amounts to roughly $6,000 at the time of writing. The countdown clock adds to the intimidation.
Researchers at Sucuri found and analyzed the fake ransomware. When they performed an on-site scan for a file that contained the bitcoin address, they found that the ransomware alert was merely an HTML page that displays the notice and a PHP script that accounts for the timer.
WordPress
WordPress is one of the, if not the most popular content management system (CMS). Of course, this also makes it a primary target for anyone looking to compromise websites. WordPress is an open-source CMS, meaning its source code is public so that anyone can inspect, modify, and enhance. This has resulted in a great many available plugins to add to sites that perform all kinds of tasks, from stopping spammers to incorporating special smileys. You name it, there is a plugin for it.
Unfortunately, not all these plugins have the same level of security, and some even have an ulterior, malicious motive. In this case, it looks as if files were added into the directory of an already present plugin.
Removing the infection
Once the infection was found, it turned out to be easy to remove. All victims had to do is find the file with the bitcoin address in it and delete it. In this case it was the file /wp-content/plugins/directorist/directorist-base.php. Directorist is the name of a legitimate plugin intended to create lists of directories based on location, category, and other interests.
By backtracking changes and looking at the access logs, the researchers found that it is very likely the legitimate plugin was already installed on the website and later tampered with by the attackers. While it was clear that the attacker must have had administrator level access, it is unclear whether they had brute forced the admin password or had acquired the already-compromised login from the black market.
Restoring the website
Deleting the file removed the ransom notice but it also left the researchers with a lot of 404 Not Found responses to internal links on the website. As it turned out, our fake ransomware included a basic SQL command which finds any posts and pages with the “publish” status and changes them to “null“. All the content was still in the database, just unable to be viewed!
Website administrators can undo this effect by using another simple SQL command.
UPDATE `wp_posts` SET `post_status` = 'publish' WHERE `post_status` = 'null';Please note that this command will also bring back some content that you may have removed yourself, but at least it will bring back all the content that the plugin made invisible.
Under development?
The researchers found indications for the presence of a file called azz_encrypt.php in the directorist directory, but were unable to find the file actually present on any of the infected websites they looked at. So this CMS hijack may be a work in progress that aims to do some actual encryption at one point.
How to protect your WordPress site
If you are running a website, you do not need scares like this one. Besides a possible loss of revenue, it brings in extra work. So what can you do to keep your WordPress site safe?
- When using a CMS, and especially a popular one, you need to keep an eye out for updates—for both the CMS itself and any plugins you have installed. Speed is important, so patch as soon as you are able. Attackers are always aware of the latest vulnerabilities and will scan the Internet for unpatched sites to hijack, sometimes within hours of a patch being made available.
- Create backups regularly (there are plugins for that). If you find out an intruder made changes to your website, it makes things a lot easier for you if you have a recent backup that you can restore without losing too much work, and without having to comb through every piece of code to check if anything else has been tampered with.
- Choose your plug-ins wisely.
- Think about access management. Consider who you allow to make changes to your site, and to what level.
- Use secure passwords (and preferably 2FA) .
- Be wary of SQL injection.
- If you allow uploads, limit the type of files to non-executables and monitor them closely.
- For websites that require even more security, there are specialized vulnerability scanners and application firewalls that you may want to look into. This is especially true if you are a popular target for people that would love to deface or abuse your website.
- If the CMS is hosted on your own servers, be aware of the dangers that this setup brings. Remember that you are relying on open-source code. Running it on your own servers should be met with special precautions to keep it separated from other work servers.
Stay safe, everyone!
The post Fake ransomware warnings hit WordPress sites: How to stay safe appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![[NIGHTSPIRE] - Ransomware Victim: Wilmington Personal Injury Lawyer - DPLAW 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
