FAQ: Mitigating Microsoft Office’s ‘Follina’ zero-day
On Monday May 30, 2022, Microsoft issued CVE-2022-30190, a new vulnerability ‘Follina’ already being exploited in the wild (zero-day) via malicious Word documents.
Q: What exactly is Follina?
A: Follina is the nickname given to a new vulnerability discovered as a zero-day and identified as CVE-2022-30190. In technical terms it is a Remote Code Execution Vulnerability in the Microsoft Windows Support Diagnostic Tool (MSDT).
Q: But what does it mean, and is this a serious vulnerability?
A: An attacker can send you a malicious Office document containing this vulnerability and compromise your machine with malware. It is serious since it is already actively being exploited in the wild.
Q: How can I protect my devices from Follina?
A: While waiting for an official patch from Microsoft, the best mitigation consists of disabling the MSDT URL Protocol.
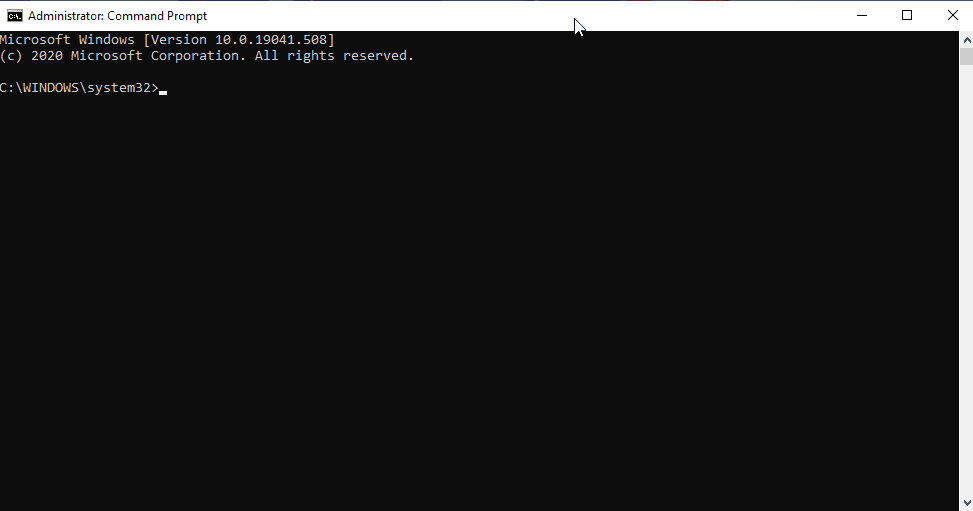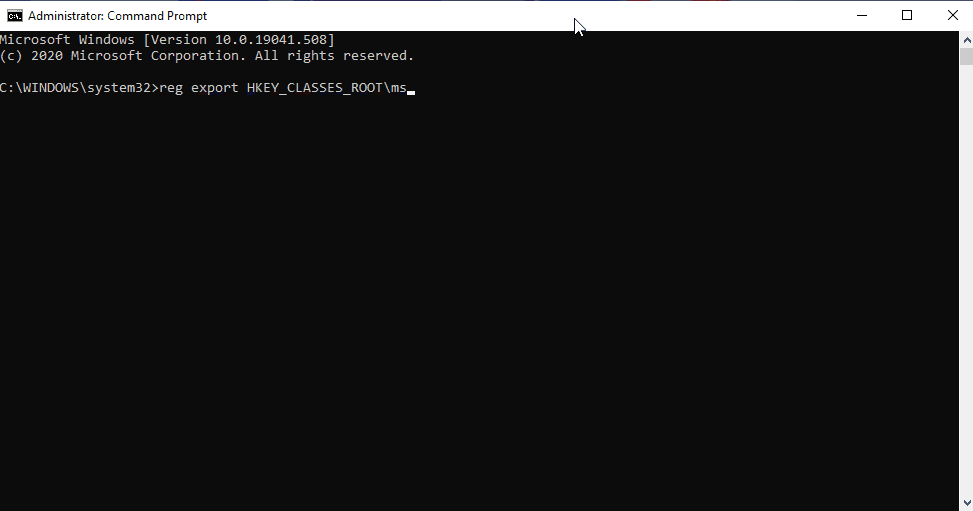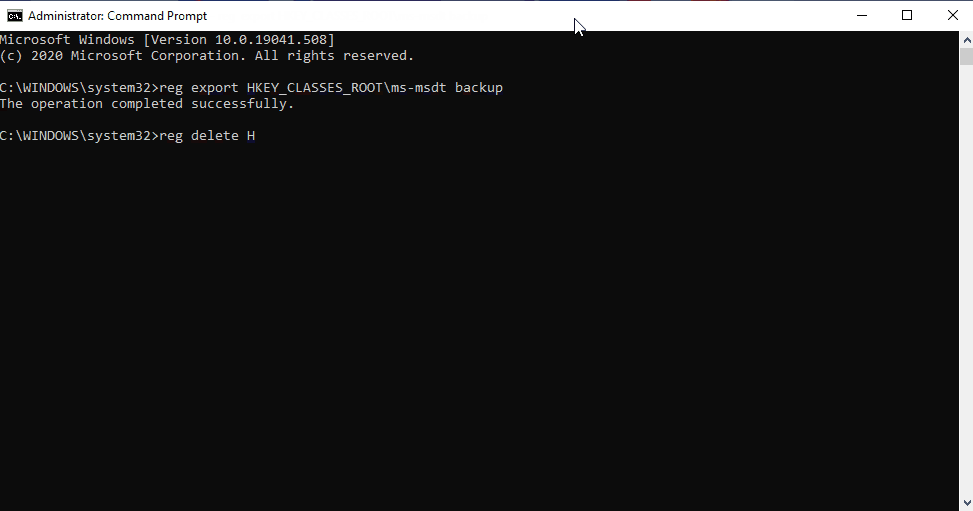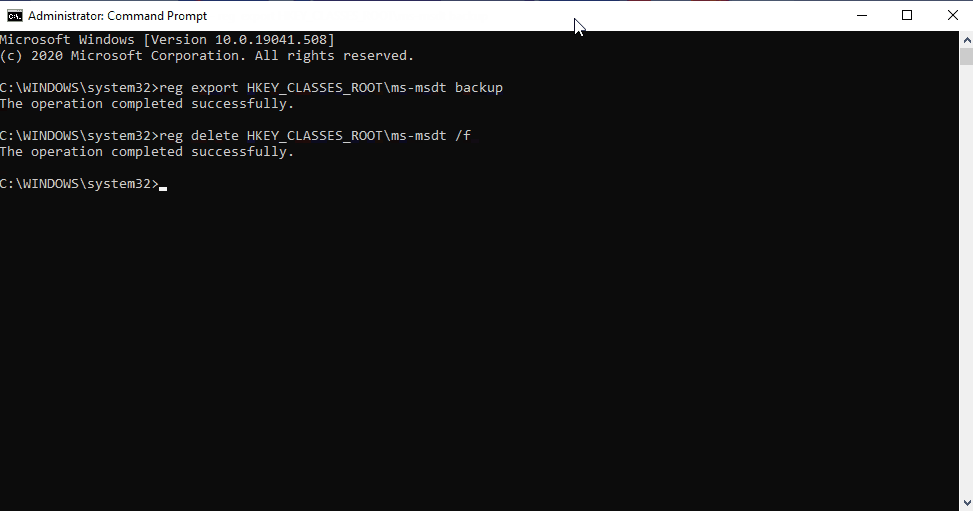
- Run the Command Prompt as Administrator.
- To back up the registry key, execute the command “reg export HKEY_CLASSES_ROOTms-msdt filename“
- Execute the command “reg delete HKEY_CLASSES_ROOTms-msdt /f”.
Q: Does Malwarebytes protect from Follina?
A: Yes, it does. Please see additional steps below based on your product to ensure you are protected.
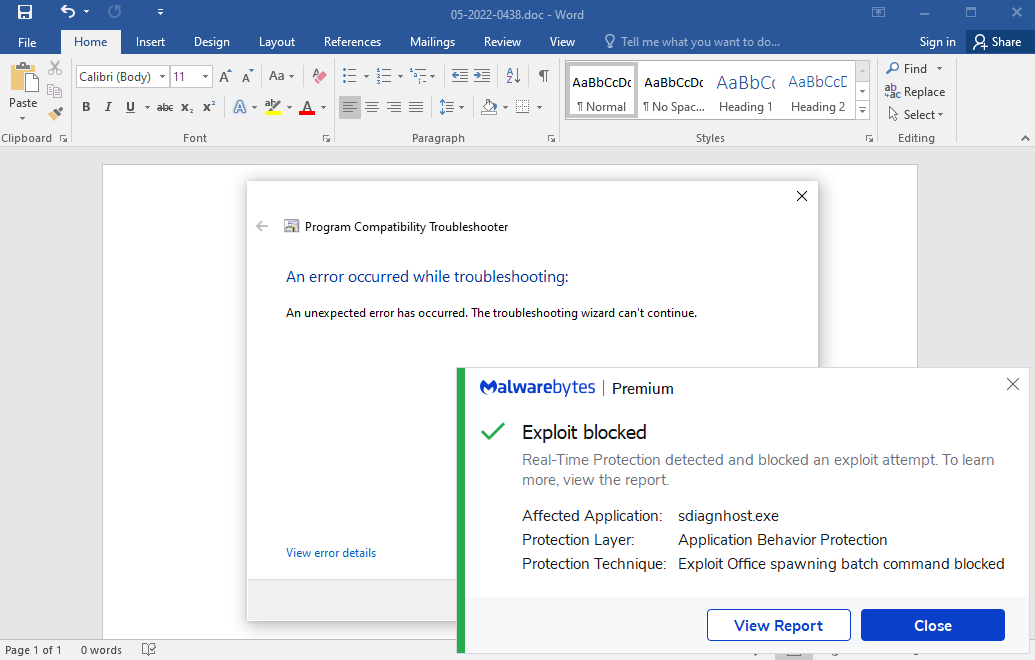
How to add protection for Malwarebytes Premium (Consumer)
Follow the instructions below to add sdiagnhost.exe as a new protected application.
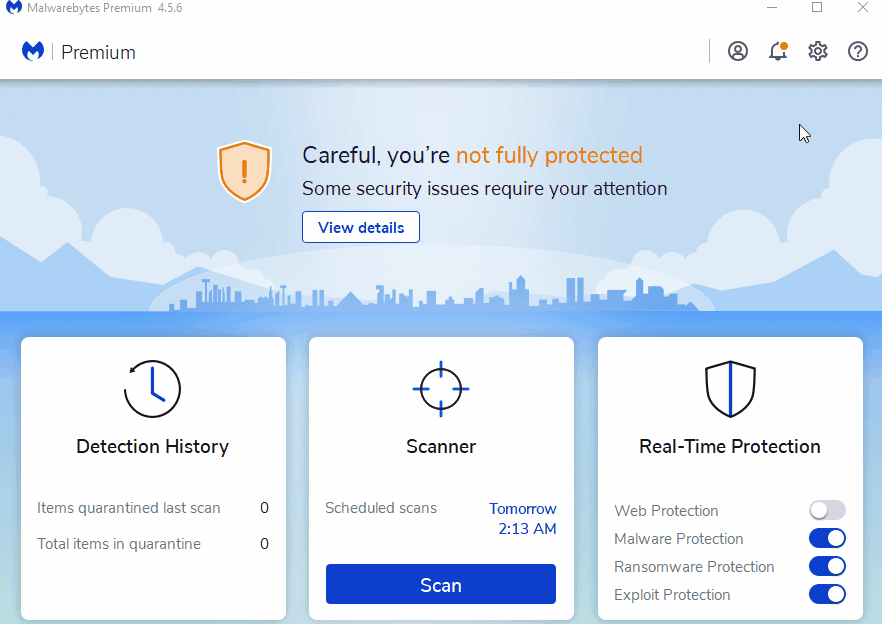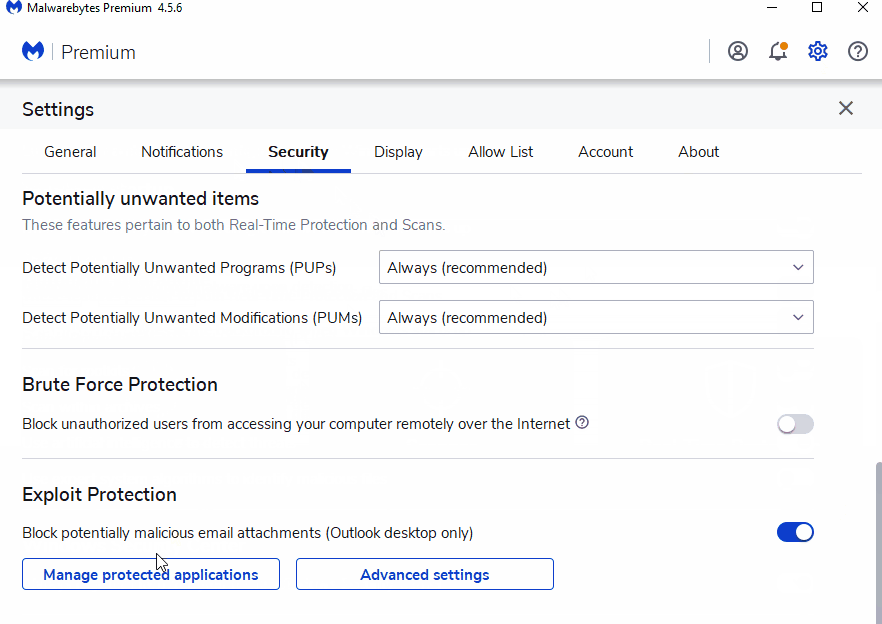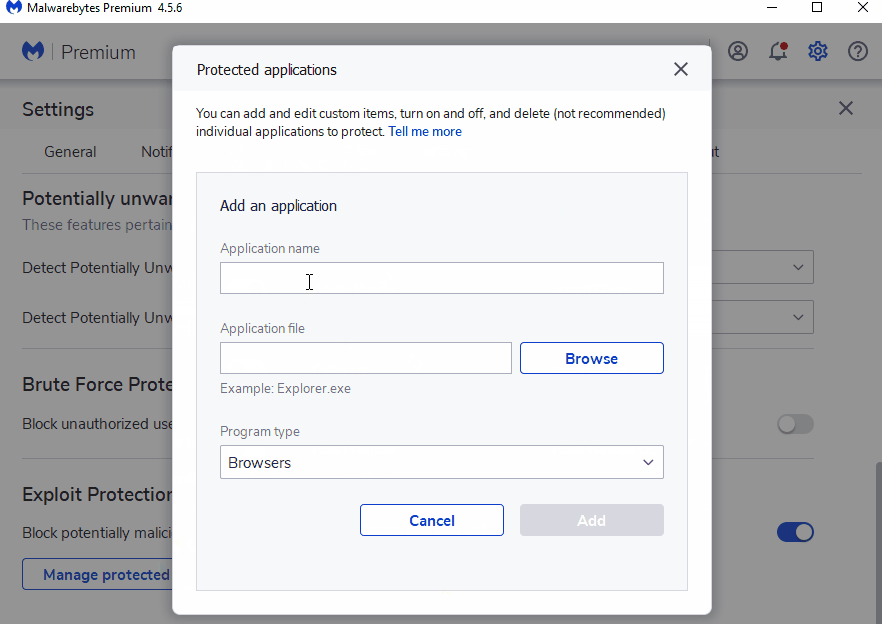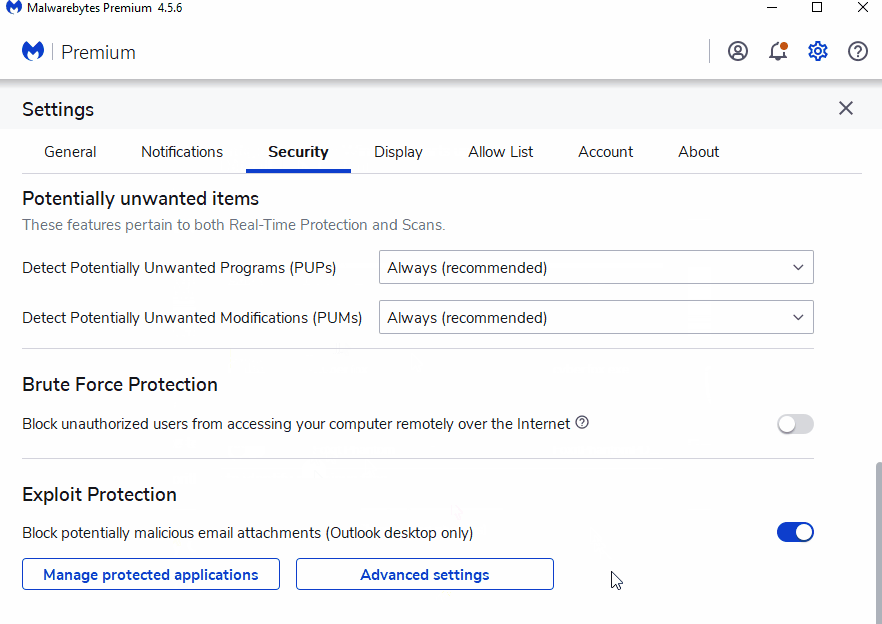
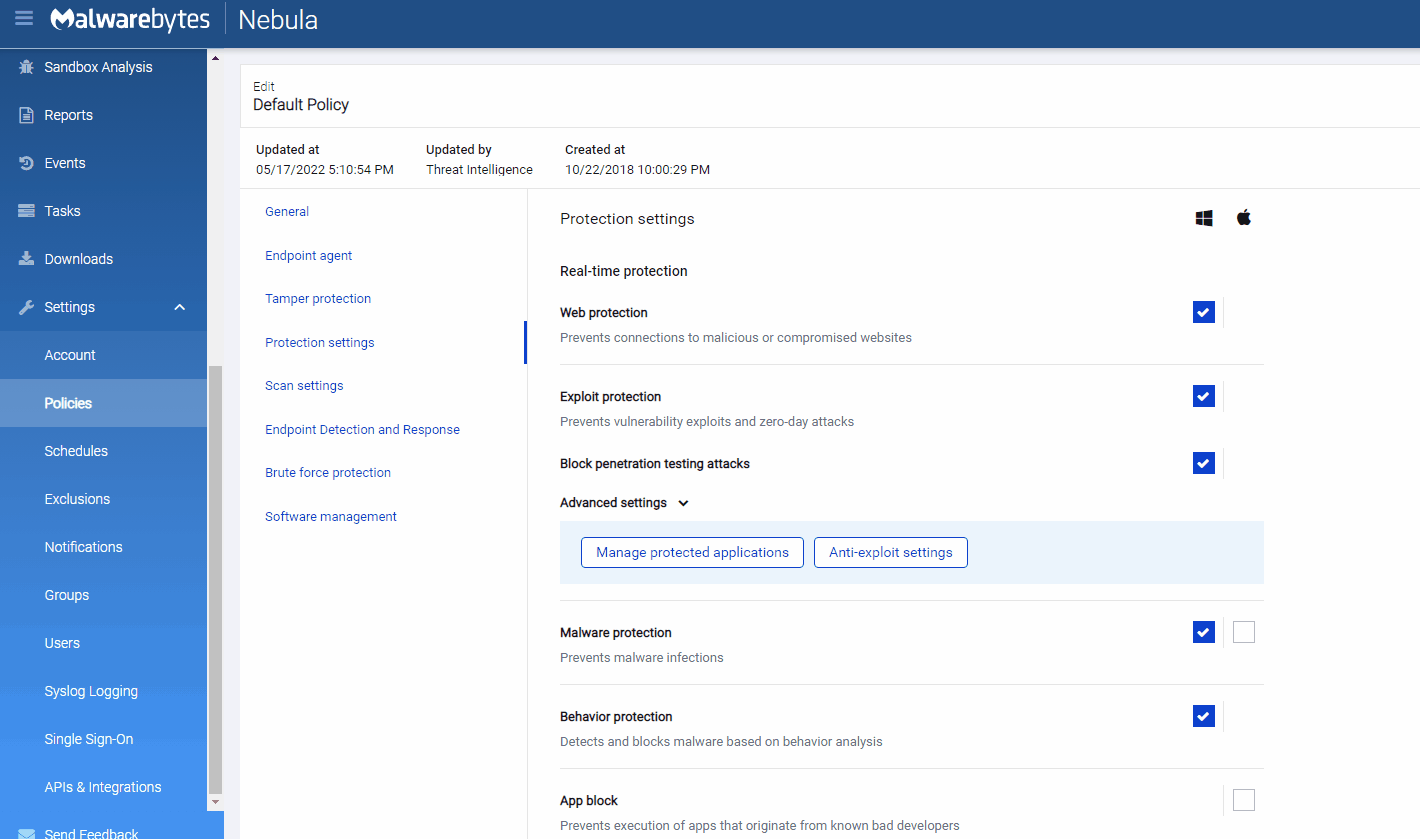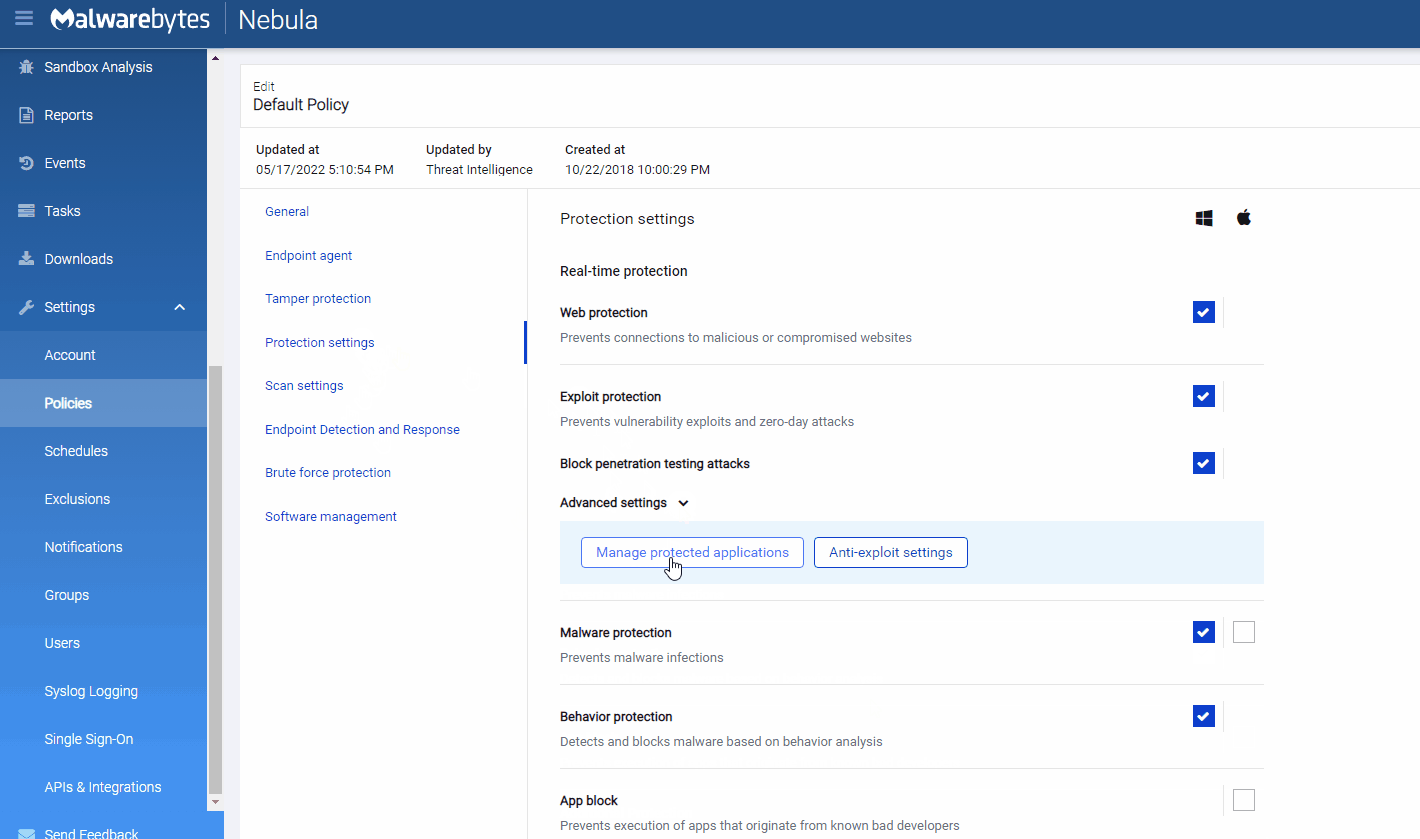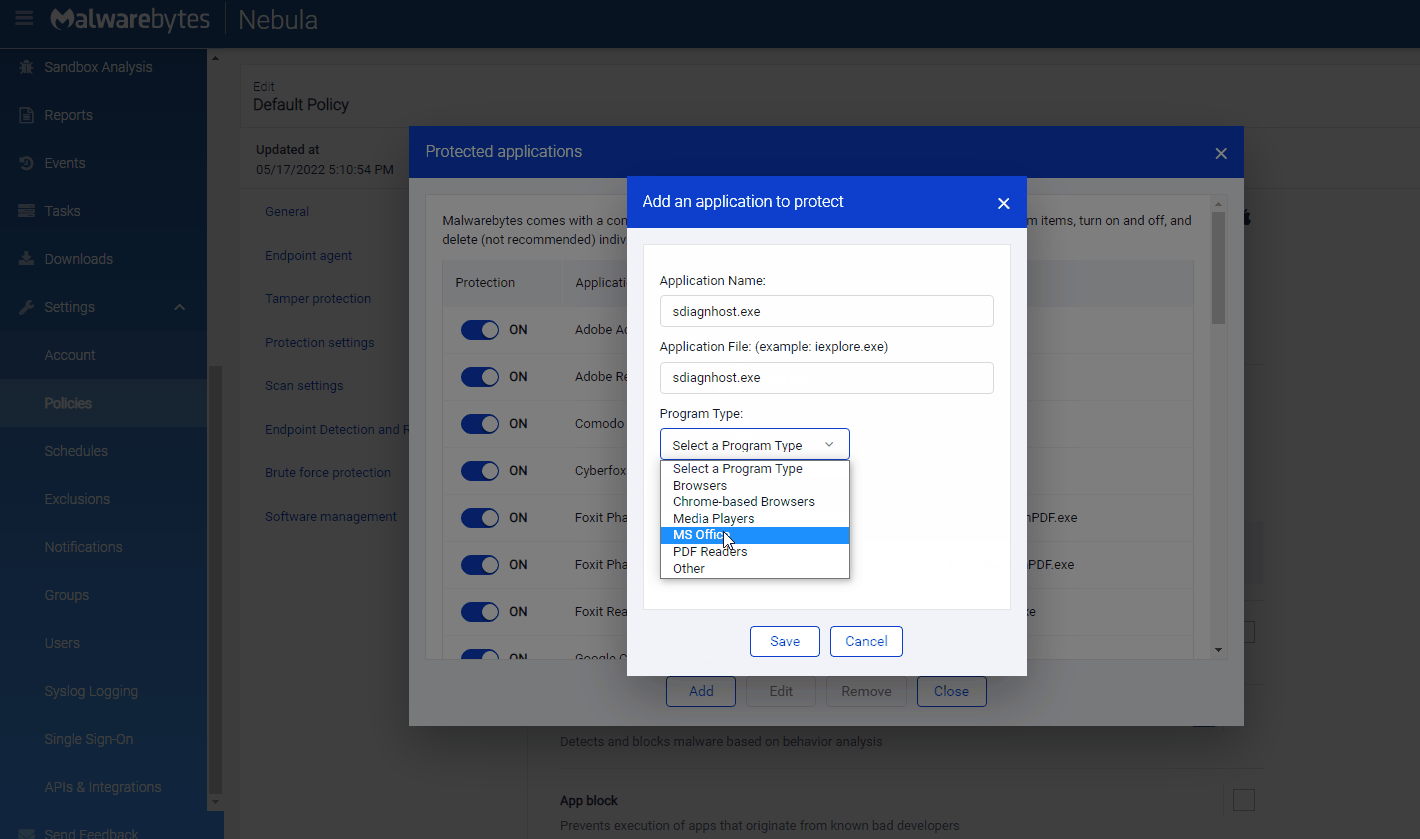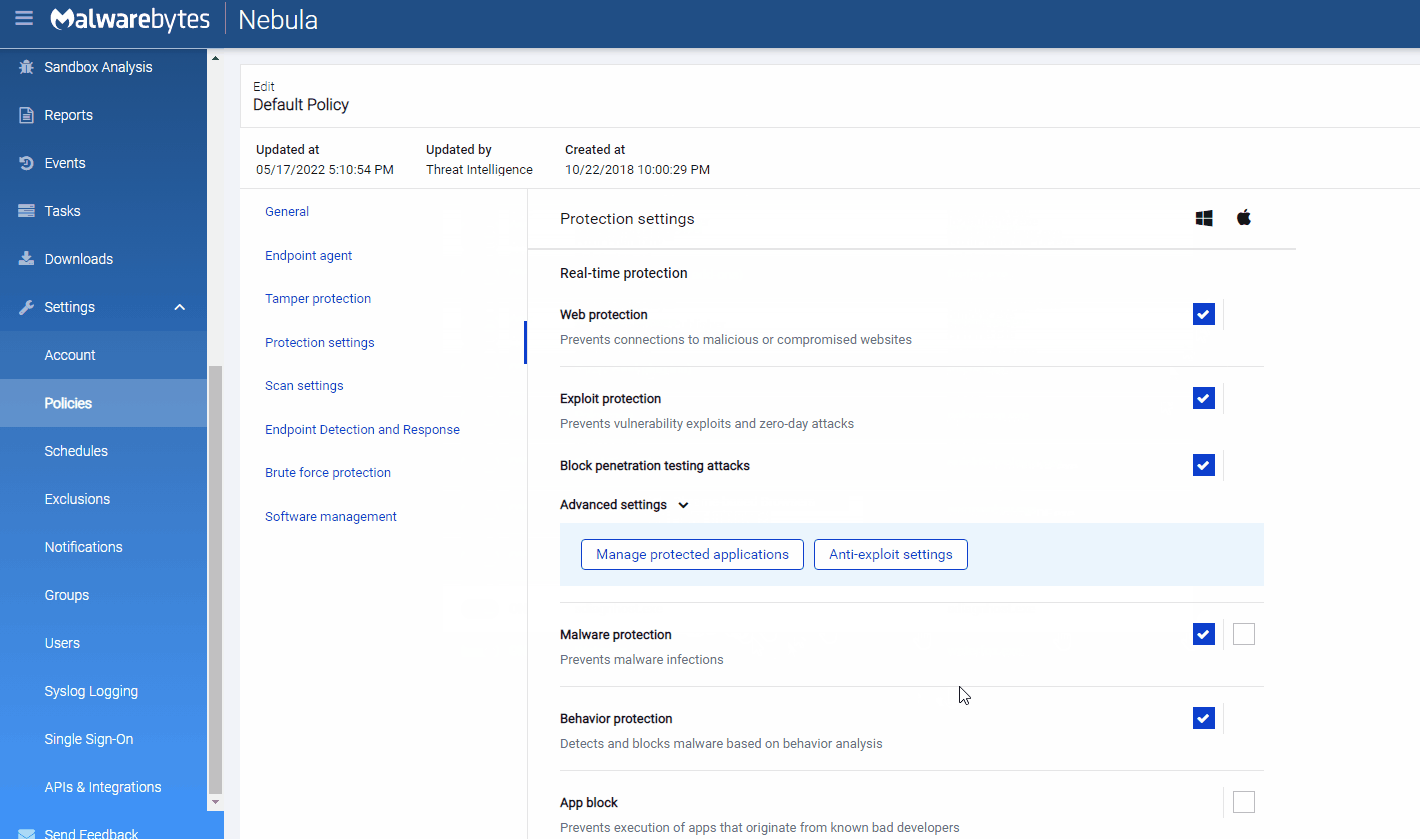
How to add protection on Malwarebytes Nebula (Enterprise)
Follow the instructions below to add sdiagnhost.exe as a new protected application.
The post FAQ: Mitigating Microsoft Office’s ‘Follina’ zero-day appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![[EVEREST] - Ransomware Victim: MUSE-INSECURE: Inside Collins Aerospaces Security Failure 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
![Cobalt Strike Beacon Detected - 47[.]109[.]90[.]134:88 9 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
