Fonix ransomware gives up life of crime, apologizes
Ransomware gangs deciding to pack their bags and leave their life of crime is not new, but it is a rare thing to see indeed.
And the Fonix ransomware (also known as FonixCrypter and Xinof), one of those ransomware-as-a-service (RaaS) offerings, is the latest to join the club.
Fonix was first observed in mid-2020, but it only started turning heads around September-October of that year. Believed to be of Iranian origin, it is known to use four methods of encryption—AES, Salsa20, ChaCha, and RSA—but because it encrypts all non-critical system files, it’s slower compared to other RaaS offerings.
Encrypted files usually bear the .FONIX and .XINOF (Fonix spelled backwards) file extensions; however, the .repter extension was also used. The Desktop wallpaper of affected system is changed to the Fonix logo.
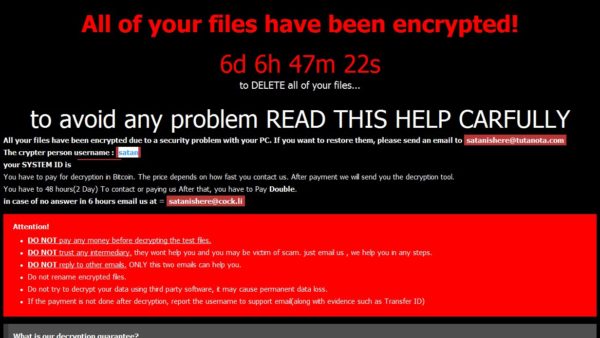
The same account that announced the end of Fonix later tweeted an apology:
And a promise to “make up for our mistakes”:
That promise came in the form of the master decryption keys needed to decrypt .FONIX and .XINOF files, and an administration tool, which can only decrypt one file at a time. Cautious readers may want to wait for more useful decryption tools, written by more legitimate organisations, before trusting code released by known cybercriminals.
This isn’t the first time a ransomware group has displayed a conscience—that is assuming we take their word they will continue to “use our abilities in positive ways”. In 2018, developers of the GandCrab ransomware, another RaaS that also made a public announcement of shutting down its operations in mid-2019, made a U-turn and released decryption keys for all its victims in Syria after a Syrian father took to Twitter to plead with them. GandCrab had infected his system and encrypted photos of his two sons who had been taken by the war.
In 2016, when TeslaCrypt made an exit from the RaaS scene, a security researcher reached out to its developers and asked if they would release the encryption keys. They did release the master key that helps decrypt affected systems for free.
It remains to be seen if the Fonix gang will keep their word. If some or all of them change their minds and go back to a life of crime, they wouldn’t be the first ransomware gang to do so. Any ransomware group packing up and leaving is good news. However, while Fonix appears to have left the building, it was only one small player in a vast criminal ecosystem. The threat of ransomware remains.
The post Fonix ransomware gives up life of crime, apologizes appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


