Forbidden – Bypass 4Xx HTTP Response Status Codes
Bypass 4xx HTTP response status codes. Based on PycURL.
Script uses multithreading, and is based on brute forcing so might have some false positives. Script uses colored output.
Results will be sorted by HTTP response status code ascending, content length descending, and ID ascending.
To filter out false positives, check each content length manually with the provided cURL command. If it does not results in bypass, just ignore all other results with the same content length.
| Test | Scope |
|---|---|
| Various HTTP methods | method |
| Various HTTP methods with ‘Content-Length: 0’ header | method |
| Cross-site tracing (XST) with HTTP TRACE and TRACK methods | method |
| File upload with HTTP PUT method | method |
| Various HTTP method overrides | method-override |
| Various HTTP headers | header |
| Various URL overrides | header |
| URL override with two ‘Host’ headers | header |
| Various URL path bypasses | path |
| Basic authentication/authorization including null session | auth |
| Broken URL parser check | parser |
Extend this script to your liking.
Tested on Kali Linux v2021.4 (64-bit).
Made for educational purposes. I hope it will help!
Future plans:
- add option to test only allowed HTTP methods,
- do not ignore URL parameters and fragments.
Table of Contents
- How to Run
- Automation
- HTTP Methods
- HTTP Headers
- URL Paths
- Results Format
- Images
How to Run
Open your preferred console from /src/ and run the commands shown below.
Install required tools:
apt-get install -y curl Install required packages:
pip3 install -r requirements.txt Run the script:
python3 forbidden.py Be aware of rate limiting. Give it some time before you run the script again for the same domain in order to get better results.
Some websites require a user agent header. Download a user agent list from here.
Automation
Bypass 403 Forbidden HTTP response status code:
apt-get install -y curl
Bypass 401 Unauthorized HTTP response status code:
pip3 install -r requirements.txt
Broken URL parser check:
python3 forbidden.py
HTTP Methods
ACL ARBITRARY BASELINE-CONTROL BIND CHECKIN CHECKOUT CONNECT COPY DELETE GET HEAD INDEX LABEL LINK LOCK MERGE MKACTIVITY MKCALENDAR MKCOL MKREDIRECTREF MKWORKSPACE MOVE OPTIONS ORDERPATCH PATCH POST PRI PROPFIND PROPPATCH PUT REBIND REPORT SEARCH SHOWMETHOD SPACEJUMP TEXTSEARCH TRACE TRACK UNBIND UNCHECKOUT UNLINK UNLOCK UPDATE UPDATEREDIRECTREF VERSION-CONTROL HTTP Headers
Client-IP Cluster-Client-IP Connection Contact Forwarded Forwarded-For Forwarded-For-Ip From Host Origin Referer Stuff True-Client-IP X-Client-IP X-Custom-IP-Authorization X-Forward X-Forwarded X-Forwarded-By X-Forwarded-For X-Forwarded-For-Original X-Forwarded-Host X-Forwarded-Server X-Forward-For X-Forwared-Host X-Host X-HTTP-Host-Override X-Original-URL X-Originating-IP X-Override-URL X-ProxyUser-IP X-Real-IP X-Remote-Addr X-Remote-IP X-Rewrite-URL X-Wap-Profile X-Server-IP X-Target URL Paths
Inject to front, back, and both front and back of URL path; with and without prepending and appending slashes.
count=0; for subdomain in $(cat subdomains_403.txt); do count=$((count+1)); echo "#${count} | ${subdomain}"; python3 forbidden.py -u "${subdomain}" -t method,method-override,header,path -f GET -o "forbidden_403_results_${count}.json"; doneResults Format
count=0; for subdomain in $(cat subdomains_401.txt); do count=$((count+1)); echo "#${count} | ${subdomain}"; python3 forbidden.py -u "${subdomain}" -t auth -f GET -o "forbidden_401_results_${count}.json"; doneImages
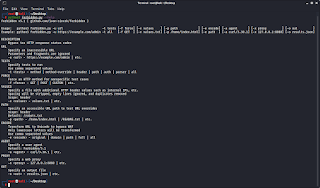
Figure 1 – Help
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[QILIN] - Ransomware Victim: South Alabama Regional Planning Commission 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)


