Google Play apps with 2.5M installs load ads when screen’s off

The Google Play store was infiltrated by 43 Android applications with 2.5 million installs that secretly displayed advertisements while a phone’s screen was off, running down a device’s battery.
McAfee’s Mobile Research Team discovered the malicious Android apps and reported them to Google as they violated Google Play Store’s policies. Google subsequently removed the apps from Android’s official store.
The applications were mainly media streaming apps and news aggregators, and the target audience was predominately Korean. However, the same deceptive tactics could very easily be applied to other app categories and more diverse user demographics.
While these applications are considered adware, they still pose a risk to users as they open the door to potential user profiling risks, exhaust device battery life, consume significant internet data, and perpetrate fraud against advertisers.

Source: McAfee
Hiding in Google Play
McAfee’s report says the adware was hidden in Google Play apps that impersonated the TV/DMB Player, Music Downloader, News, and Calendar applications.
Once installed on the device, the adware apps wait several weeks before activating their ad-fraud activity to deceive the users and evade detection by Google reviewers.
McAfee says the adware’s configuration can be remotely modified and updated via Firebase Storage or Messaging, so its operators can adjust the period of dormancy and other parameters.
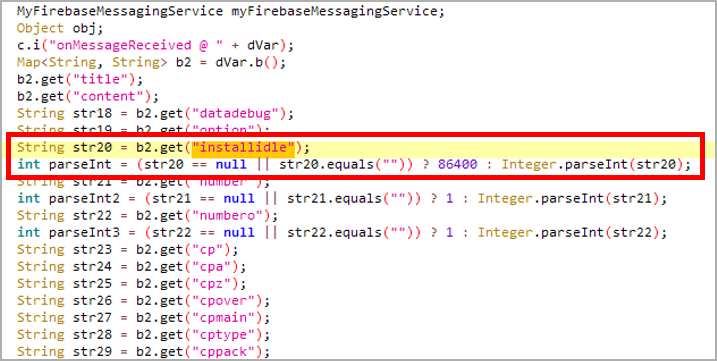
Source: McAfee
Android utilizes a power-saving feature that puts an app into standby mode when a device is not being used, preventing it from running in the background and utilizing CPU, memory, and network resources.
When the malicious adware apps are installed, users will be prompted to add them as an exclusion to Android’s power-saving system, allowing the malicious apps to run in the background.
This exclusion allows the adware apps to fetch and load advertisements even when the device’s screen is off, fraudulently generating revenue and giving the users no apparent way to realize what is happening.
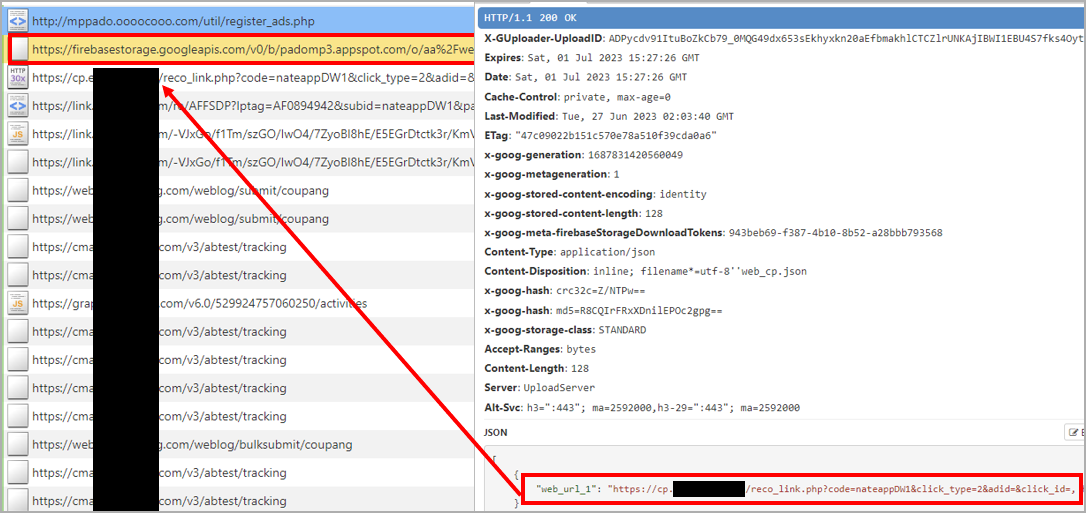
Source: McAfee
McAfee comments that it might be possible for users to briefly glimpse the loaded ads when they turn on a device’s screen before they are automatically closed.
However, the most solid indicator of compromise remains an inexplicably high battery consumption while the device is idle.
To check which apps consume the most energy on your Android device, head to “Settings → Battery → Battery Usage,” where “total” and “background” usage are indicated.
McAfee says that the adware apps also request permission to draw over other apps, typically used by banking trojans that overlay phishing pages on top of legitimate e-banking apps; however, no phishing behavior was observed in this case.
Android users are advised to always read reviews before installing apps and to scrutinize requested permissions while installing new apps before allowing them to install.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[HANDALA] - Ransomware Victim: Saturday Reckoning 5 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
![Brute Ratel C4 Detected - 52[.]68[.]211[.]55:80 6 brute_ratel_c4](https://www.redpacketsecurity.com/wp-content/uploads/2022/07/brute_ratel_c4-300x300.jpg)

