Grepmarx – A Source Code Static Analysis Platform For AppSec Enthusiasts
Grepmarx is a web application providing a single platform to quickly understand, analyze and identify vulnerabilities in possibly large and unknown code bases.
Features
SAST (Static Analysis Security Testing) capabilities:
- Multiple languages support: C/C++, C#, Go, HTML, Java, Kotlin, JavaScript, TypeScript, OCaml, PHP, Python, Ruby, Bash, Rust, Scala, Solidity, Terraform, Swift
- Multiple frameworks support: Spring, Laravel, Symfony, Django, Flask, Node.js, jQuery, Express, Angular…
- 1600+ existing analysis rules
- Easily extend analysis rules using Semgrep syntax: https://semgrep.dev/editor
- Manage rules in rule packs to tailor code scanning
SCA (Software Composition Analysis) capabilities:
- Multiple package-dependency formats support: NPM, Maven, Gradle, Composer, pip, Gopkg, Gem, Cargo, NuPkg, CSProj, PubSpec, Cabal, Mix, Conan, Clojure, Docker, GitHub Actions, Jenkins HPI, Kubernetes
- SBOM (Software Bill-of-Materials) generation (CycloneDX compliant)
Extra
- Analysis workbench designed to efficiently browse scan results
- Scan code that doesn’t compile
- Comprehensive LOC (Lines of Code) counter
- Inspector: automatic application features discovery
- … and a Dark Mode
Screenshots
| Scan customization | Analysis workbench | Rule pack edition |
|---|---|---|
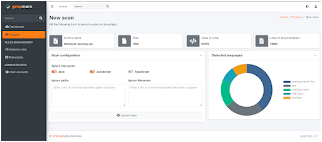 | 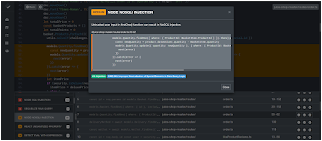 | 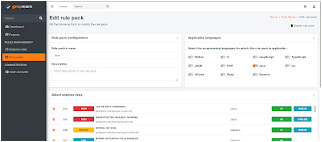 |
Execution
Grepmarx is provided with a configuration to be executed in Docker and Gunicorn.
Docker execution
Make sure you have docker-composer installed on the system, and the docker daemon is running. The application can then be easily executed in a docker container. The steps:
Get the code
$ git clone https://github.com/Orange-Cyberdefense/grepmarx.git
$ cd grepmarxStart the app in Docker
$ sudo docker-compose pull && sudo docker-compose build && sudo docker-compose up -dVisit http://localhost:5000 in your browser. The app should be up & running.
Note: a default user account is created on first launch (user=admin / password=admin). Change the default password immediately.
Gunicorn
Gunicorn ‘Green Unicorn’ is a Python WSGI HTTP Server for UNIX. A supervisor configuration file is provided to start it along with the required Celery worker (used for security scans queuing).
Install using pip
$ pip install gunicorn supervisorStart the app using gunicorn binary
$ supervisord -c supervisord.confVisit http://localhost:8001 in your browser. The app should be up & running.
Note: a default user account is created on first launch (user=admin / password=admin). Change the default password immediately.
Build from sources
Get the code
$ git clone https://github.com/Orange-Cyberdefense/grepmarx.git
$ cd grepmarxInstall virtualenv modules
$ virtualenv env
$ source env/bin/activateInstall Python modules
$ # SQLite Database (Development)
$ pip3 install -r requirements.txt
$ # OR with PostgreSQL connector (Production)
$ # pip install -r requirements-pgsql.txtInstall additionnal requirements
# Dependency scan (cdxgen / depscan) requirements
$ sudo apt install npm openjdk-17-jdk maven gradle golang composer
$ sudo npm install -g @cyclonedx/cdxgen
$ pip install appthreat-depscanA Redis server is required to queue security scans. Install the
redispackage with your favorite distro package manager, then:
$ redis-serverSet the FLASK_APP environment variable
$ export FLASK_APP=run.py
$ # Set up the DEBUG environment
$ # export FLASK_ENV=developmentStart the celery worker process
$ celery -A app.celery_worker.celery worker --pool=prefork --loglevel=info --detachStart the application (development mode)
$ # --host=0.0.0.0 - expose the app on all network interfaces (default 127.0.0.1)
$ # --port=5000 - specify the app port (default 5000)
$ flask run --host=0.0.0.0 --port=5000Access grepmarx in browser: http://127.0.0.1:5000/
Note: a default user account is created on first launch (user=admin / password=admin). Change the default password immediately.
Credits & Links
- The web application dashboard is based on AdminLTE Flask
- SAST code scanning is powered by the semgrep engine
- SBOM generation is done with the great CycloneDX cdxgen, and SCA is performed using the awesome AppThreat dep-scan
- LOC counting is handled by scc
- Features discovery is done using Application Inspector
Grepmarx – Provided by Orange Cyberdefense.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.






![[Palo Alto Networks Security Advisories] CVE-2025-4614 PAN-OS: Session Token Disclosure Vulnerability 11 Palo_Alto_Networks_Logo](https://www.redpacketsecurity.com/wp-content/uploads/2025/02/Palo_Alto_Networks_Logo-300x55.png)

