Hackers use VPN provider’s code certificate to sign malware

The China-aligned APT (advanced persistent threat) group known as ‘Bronze Starlight’ was seen targeting the Southeast Asian gambling industry with malware signed using a valid certificate used by the Ivacy VPN provider.
The main benefit of using a valid certificate is to bypass security measures, avoid raising suspicions with system alerts, and blend in with legitimate software and traffic.
According to SentinelLabs, which analyzed the campaign, the certificate belongs to PMG PTE LTD, a Singaporean vendor of the VPN product ‘Ivacy VPN.’
The cyberattacks observed in March 2023 are likely a later phase of the ‘Operation ChattyGoblin’ that ESET identified in a Q4 2022 – Q1 2023 report.
However, SentinelLabs says it’s challenging to associate with specific clusters due to the extensive sharing of tools between Chinese threat actors.
DLL side-loading
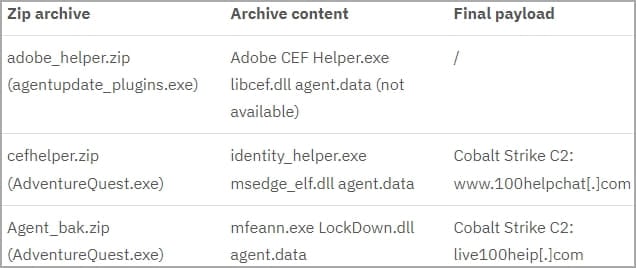
The attacks begin with dropping .NET executables (agentupdate_plugins.exe and AdventureQuest.exe) on the target system, likely via trojanized chat apps, that fetch password-protected ZIP archives from Alibaba buckets.
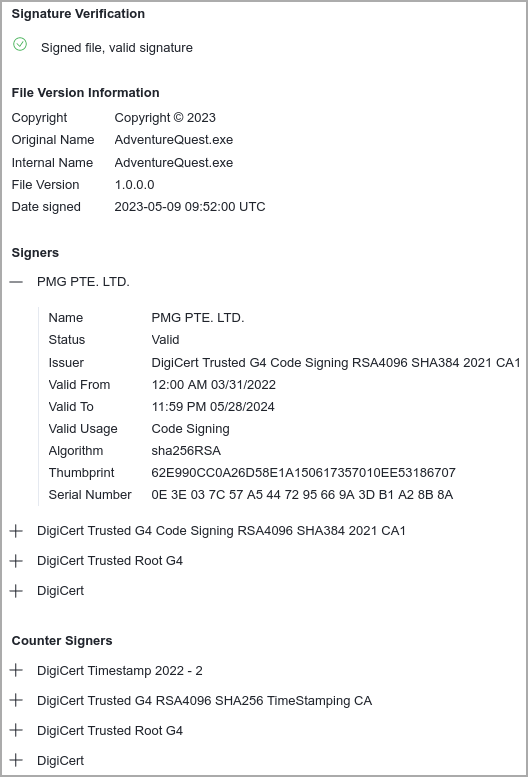
The AdventureQuest.exe malware sample was first found by security researcher MalwareHunterteam in May when they noted that the code-signing certificate was the same as one used for official Ivacy VPN installers.
These archives contain vulnerable software versions like Adobe Creative Cloud, Microsoft Edge, and McAfee VirusScan, which are susceptible to DLL hijacking. The Bronze Starlight hackers use these vulnerable applications to deploy Cobalt Strike beacons on targeted systems.
The malicious DLLs (libcef.dll, msedge_elf.dll, and LockDown.dll) are packed inside the archives alongside the legitimate program executables, and Windows prioritizes their execution against safer versions of the same DLL stored in C:\Windows\System32, hence allowing malicious code to run.
SentinelLabs notes that the .NET executables feature a geofencing restriction that prevents the malware from running in the United States, Germany, France, Russia, India, Canada, or the United Kingdom.
These countries are outside this campaign’s target scope and are excluded to evade detection and analysis. However, due to an error in the geofencing implementation, it does not work.
Abusing a valid certificate
An intriguing aspect of the observed attacks is using a code-singing certificate that belongs to PMG PTE LTD, the firm behind Ivacy VPN.
In fact, the same certificate is used to sign the official Ivacy VPN installer linked to from the VPN provider’s website.
(@malwrhunterteam)
“It is likely that at some point the PMG PTE LTD signing key has been stolen – a familiar technique of known Chinese threat actors to enable malware signing,” hypothesizes SentinelLabs.
“VPN providers are critical targets since they enable threat actors to potentially gain access to sensitive user data and communications.”
If the certificate was stolen, security researchers are concerned about what else the threat actors had access to at the VPN provider.
PMG PTE LTD has not responded to this disclosure with a public statement, so the exact means by which the hackers gained access to the certificate remain unclear.
In the meantime, DigiCert revoked and invalidated the certificate in early June 2023 for breach of the “Baseline Requirements” guidelines.
BleepingComputer contacted Ivacy about their abused code-signing certificate but did not receive a response.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

