Have you been infected with Hacking Teams Malware?
Worried that you might have been targeted with Hacking Team spyware, but don’t know how to find out for sure? IT security firm Rook Security has released Milano, a free automated tool meant to detect the Hacking Team malware on a computer system.
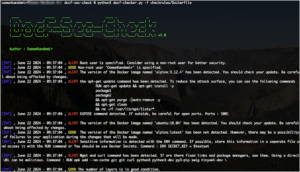
 It does so by looking for files associated with the recent Hacking Team breach. The tool is still in beta, and currently searches the system for 40 Windows executable and library files. The list is expected to expand as the company’s researchers continue to review the leaked Hacking Team data.
It does so by looking for files associated with the recent Hacking Team breach. The tool is still in beta, and currently searches the system for 40 Windows executable and library files. The list is expected to expand as the company’s researchers continue to review the leaked Hacking Team data.
Milano offers two scanning options: quick scan and deep scan. The former searches for files by file name, and if it finds one that matches the list, it checks whether the file’s computed hash matches the hash from the Hacking-Team-associated file.
The latter checks all files’ computed hashes against all md5’s from Hacking-Team-associated files (and this can take an hour or more, depending on the system).
“This breach has been very unique in nature and challenging for security technology vendors to obtain code samples to create signatures and patches, thereby leaving scores of systems potentially vulnerable to nefarious actors seeking to weaponize Hacking Team’s once proprietary tools,” said J.J. Thompson, CEO of Rook Security.
“After our Intelligence Team quickly deduced how the leaked code could be weaponized and used for harm, we immediately put a team in place to identify, analyse, and detect malicious files located in this data.”
Facebook has also offered a way to discover if your Mac(s) have been compromised by Hacking Team malware: they have provided a specific query pack for its open source OS analysis tool osquery, which will identify known variants of Mac OS X backdoors – whether leveraged by APTs or not.
“This pack is high signal and should result in close to zero false positives,” Facebook security engineer Javier Marcos de Prado promises, and adds that several queries in the pack are meant to identify the Hacking Team OS X backdoor in an organization’s infrastructure.
The leaked Hacking Team data has given us insight into the company’s capabilities and that of their spying tools, but this is just the beginning. The data trove is huge, and more unpleasant revelations are sure to follow.
source: net-security.com


![Brute Ratel C4 Detected - 18[.]177[.]187[.]233:80 4 brute_ratel_c4](https://www.redpacketsecurity.com/wp-content/uploads/2022/07/brute_ratel_c4-300x300.jpg)
![Cobalt Strike Beacon Detected - 118[.]89[.]73[.]78:4433 5 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)