How to spot a DocuSign phish and what to do about it
Phishing scammers love well known brand names, because people trust them, and their email designs are easy to rip off. And the brands phishers like most are the ones you’re expecting to hear from, or wouldn’t be surprised to hear from, like Amazon or DHL. Now you can add DocuSign to that list.
DocuSign is a service that allows people to sign documents in the Cloud. Signing documents electronically saves a lot of paper and time. It also cuts back on human contact, which is particularly useful for remote working, or when everyone is locked down in a pandemic. Google searches for DocuSign almost doubled during March 2020, and stayed there, as so many people around the world started working from home.
Earlier this year, DocuSign specifically warned about phishing campaigns using its brand.
Bad signs to look for
DocuSign phishing emails have many of the tell-tale signs of other phishing attacks: Fake links, fake senders, misspellings, and the like. Recipients can check links by hovering their mouse pointer over the document link in the email. If it is an actual DocuSign document it will be hosted at docusign.net. In the spam campaigns we have seen, documents were hosted at docs.google.com, feedproxy.google.com, and some documents came as attachments, which DocuSign does not do.
Also, the sender address should belong to docusign.net, but that alone is not enough: We have seen spoofed messages coming from that address, so check for other indicators. You can read an exhaustive list of things to look out for, as well as addresses to report suspicious activity on DocuSign’s incident reporting page (although we recommend you simply opt for the safe document access option, described below).
Remember, if you’re in doubt, it is not stupid or rude to contact a sender by direct mail or another method, and verify the email’s authenticity (just don’t hit “reply”).
We’ve included some examples of DocuSign phishing campaigns below.
Fake DocuSign invoice emails
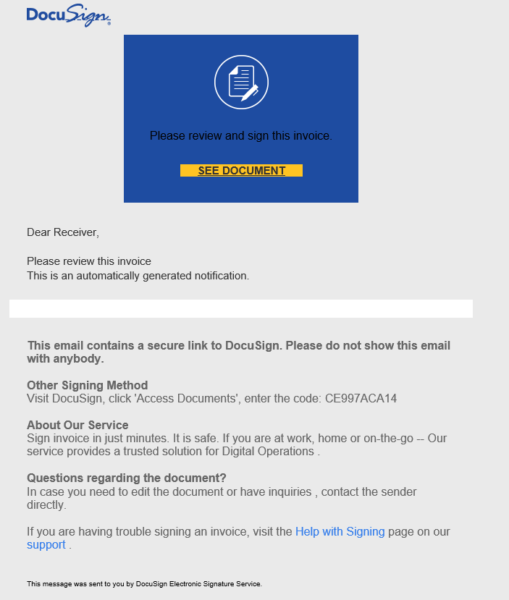
Signs:
- “Dear Receiver”? If the sender does not use your actual name, that is a red flag.
- The security code is way too short.
- DocuSign links will read “REVIEW DOCUMENT” if it is a document that needs to be signed.
- An extra space in “inquiries , contact” and other sloppy spelling.
- Document was hosted at
feedproxy.google.com, notdocusign.net.
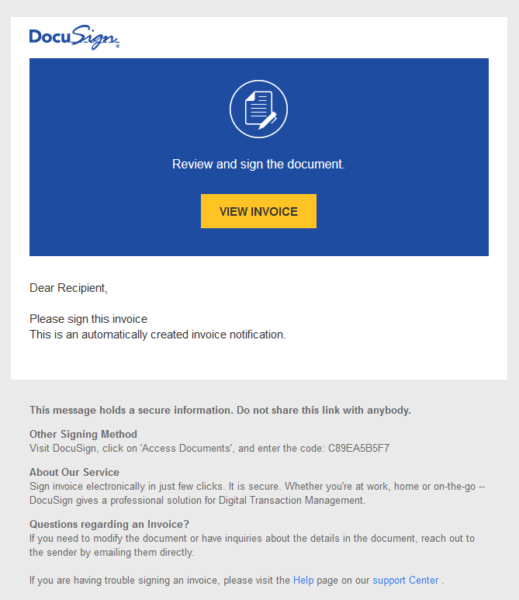
Signs:
- “Dear Recipient”? Again, if the sender does not use your actual name, that is a red flag.
- The security code is way too short.
- Sentences are slightly off, like you would expect from a non-native speaker.
- Document was hosted at
docs.google.com.
Fake DocuSign attachments
Another sample from our spam honeypot came with an attachment pretending to be from DocuSign.
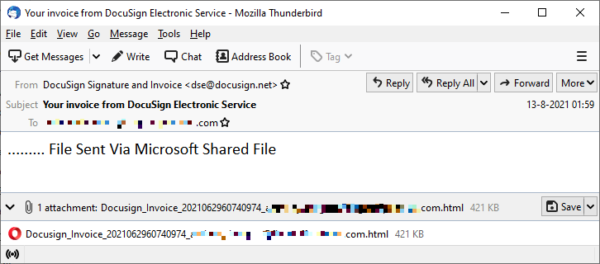
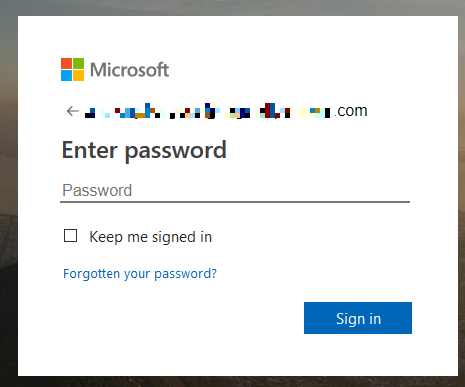
The sender address was spoofed. Opening the attachment presents the user with a fake Microsoft login screen, hoping to harvest the target’s password. The information would have been sent to a command and control server through the use of a compromised WordPress website.
Safe document access
Rather than trying to identify whether or not an email is bad, it’s often safer (and no less convenient) to assume it’s bad and ignore its links completely.
We recommend that you use the “Alternate Signing Method” mentioned in legitimate DocuSign mails. If you get a DocuSign email, visit docusign.com, click ‘Access Documents’, and enter the security code provided in the email. It will have a format similar to this one: EA66FBAC95CF4117A479D27AFB9A85F01. (Don’t bother, it’s invalid.) If a scammer sends you a fake code it simply won’t work. There is no need to trust the sender, or the links in their email.
However, to complicate matters, phishers have now been discovered sending legitimate DocuSign emails from legitimate DocuSign accounts.
Real DocuSign emails used for phishing
Security vendor Avanan recently spotted a new DocuSign campaign that bypasses most of the advice provided above, by using real DocuSign accounts.
In this new attack, scammers upload a file to a real DocuSign account (either a free one or one stolen from somebody else) and share it with the target’s email address.
As result, the recipient will receive a legitimate DocuSign mail with an existing and functional security code that leads to the malicious file. Sharing malicious documents is hard to do because DocuSign does have protection against weaponized attachments: Uploaded document files are converted into static .pdf files, which removes malicious content like embedded macros. It remains to be seen if attackers will find ways around DocuSign’s protections. It probably won’t be necessary though.
Hyperlinks are carried across to the shared document, after it’s converted to a PDF, and remain clickable for the recipient. So all an attacker has to do is make the victim click a link to a phishing site in the DocuSign-hosted document. And scammers are very good at getting people to click on links.
The protection methods against attacks using existing DocuSign accounts are:
- You can determine if the email is legitimate by contacting the alleged sender using something other than email.
- If you fall for the scam, anti-malware software will warn you if you try to go to a known phishing site; it should recognize and block malicious files that get downloaded; and its exploit protection will stop malicious documents from deploying their payload.
- If the phishing site is unknown, a password manager can help. A password manager will not provide credentials for a site that it does not recognize, and while a phishing site might fool the human eye, it won’t fool a password manager. This helps users from getting their passwords harvested.
Keep your passwords safe!
The post How to spot a DocuSign phish and what to do about it appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


