Incident Response Analyst Report 2019

![]() Download full report (PDF)
Download full report (PDF)
As an incident response service provider, Kaspersky delivers a global service that results in global visibility of adversaries’ cyber-incident tactics and techniques used in the wild. In this report, we share our teams’ conclusions and analysis based on incident responses and statistics from 2019. As well as a range of highlights, this report will cover the affected industries, the most widespread attack tactics and techniques, how long it took to detect and stop adversaries after initial entry and the most exploited vulnerabilities. The report also provides some high-level recommendations on how to increase resilience to attacks.
The insights used in this report come from incident investigations by Kaspersky teams from around the world. The main digital forensic and incident response operations unit is called the Global Emergency Response Team (GERT) and includes experts in Europe, Latin America, North America, Russia and the Middle East. The work of the Computer Incidents Investigation Unit (CIIU) and the Global Research and Analysis Team (GReAT) are also included in this report.
Executive summary
In 2019, we noticed greater commitment among victims to understand the root causes of cyberattacks and improve the level of cybersecurity within their environments to reduce the probability of similar attacks taking place again in the future.
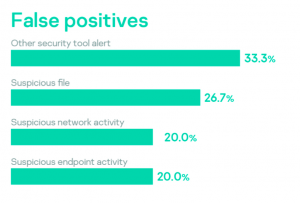
Analysis showed that less than a quarter of received requests turned out to be false positives, mostly after security tools issued alerts about suspicious files or activity. The majority of true positive incidents were triggered by the discovery of suspicious files, followed by encrypted files, suspicious activity and alerts from security tools.
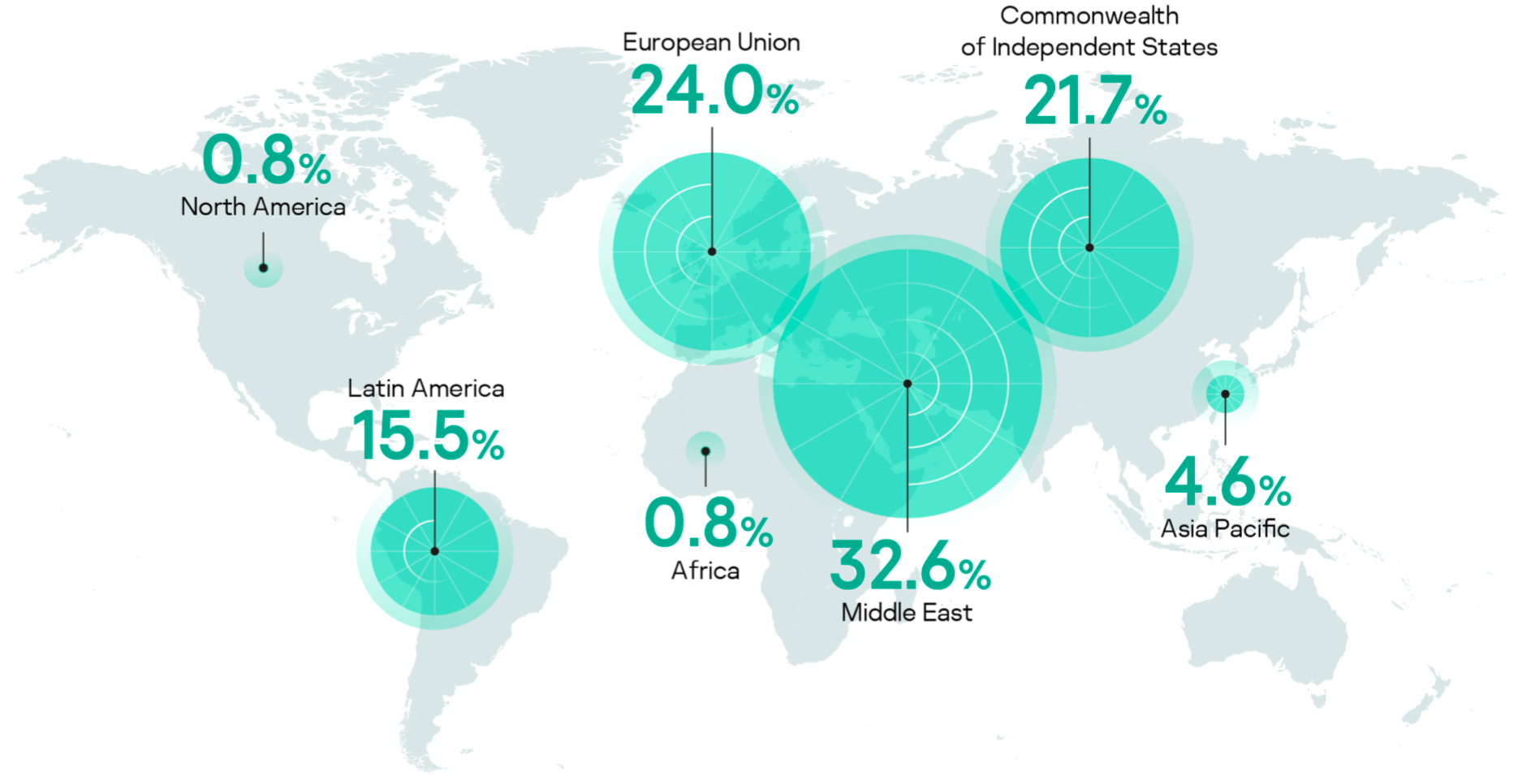
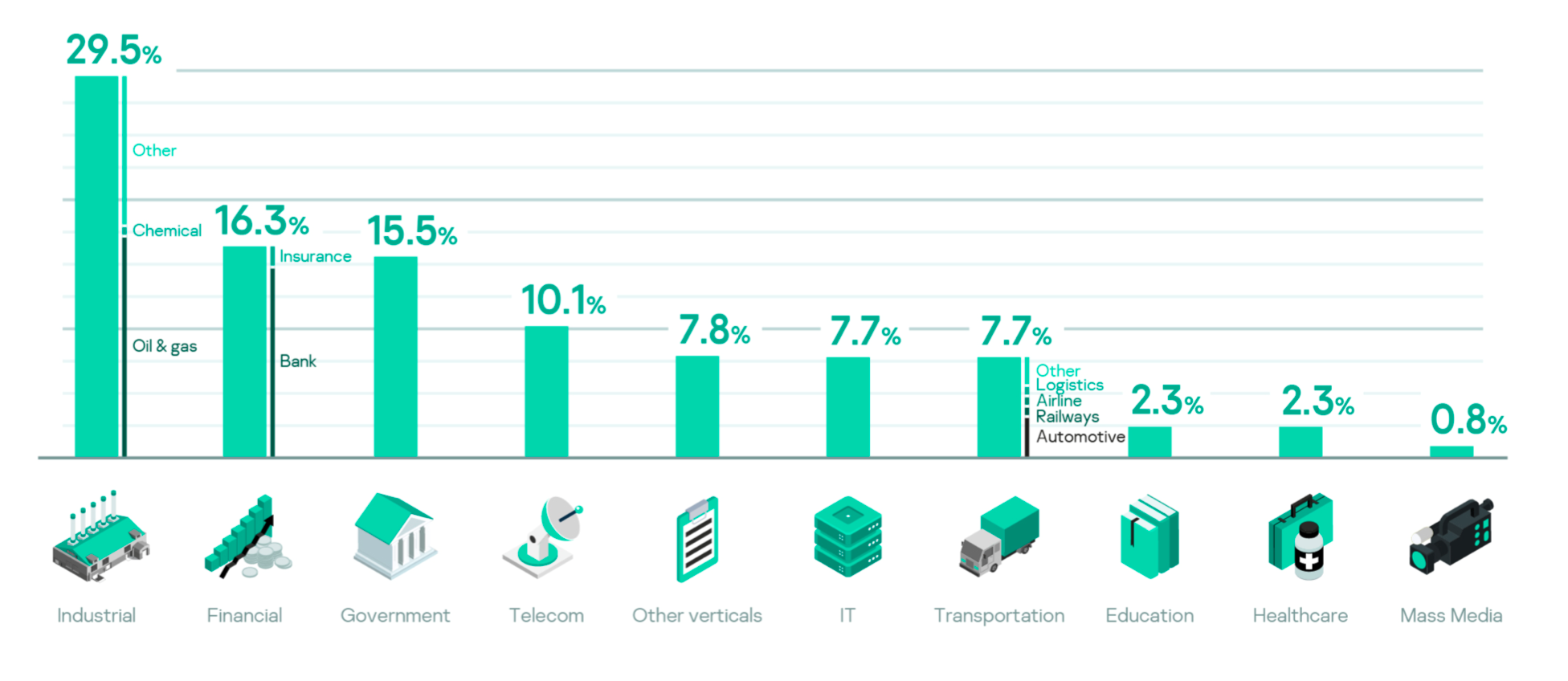
Most of the incident handling requests were received from the Middle East, Europe, the CIS and Latin America, from a wide spectrum of business sectors, including industrial, financial, government, telecoms, transportation and healthcare. Industrial businesses were the most affected by cyberattacks, with oil and gas companies leading the way. They were followed by financial institutions, dominated by banks, which bore the brunt of all money theft incidents in 2019. Ransomware’s presence continued in 2019 and was felt most by government bodies, telecoms and IT companies in various regions.
Verticals and industries
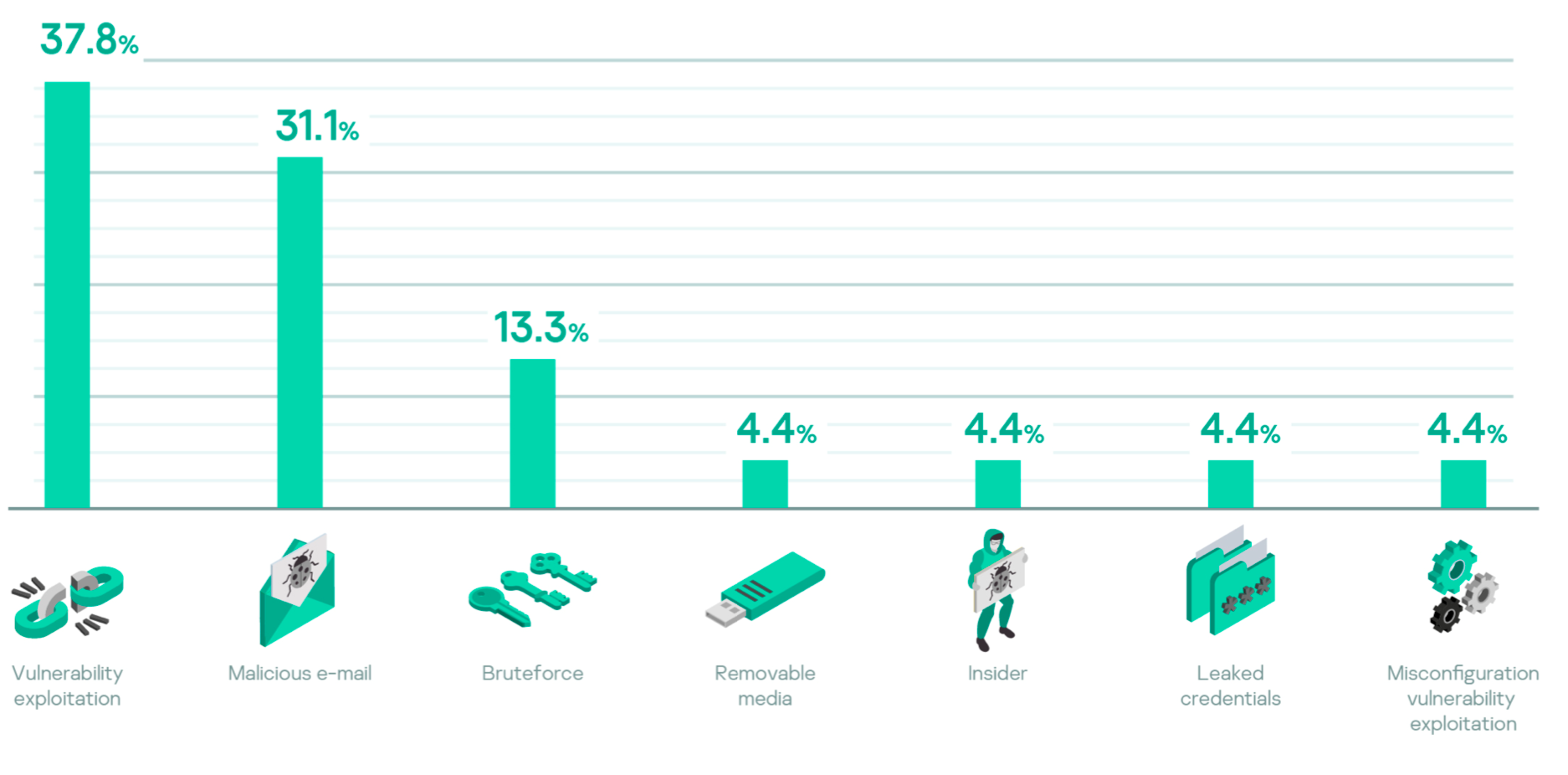
Adversaries used a variety of initial vectors to compromise victims’ environments. Initial vectors included exploitation, misconfiguration, insiders, leaked credentials and malicious removable media. But the most common were exploitation of unpatched vulnerabilities, malicious emails, followed by brute-force attacks.
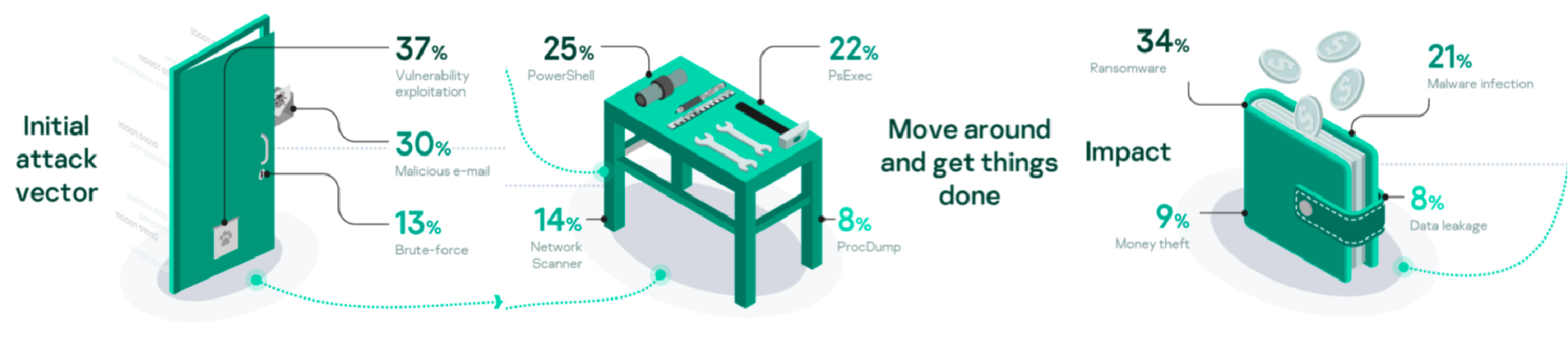
In addition to exploiting vulnerabilities, adversaries used several legitimate tools in different attack phases. This made attacks harder to discover and allowed the adversaries to keep a low profile until their goals were achieved. Most of the legitimate tools were used for credential harvesting from live systems, evading security, network discovery and unloading security solutions.
Although we started working on incidents the first day of a request in 70% of cases, analysis revealed that the time between attack success and its discovery varies between an average of one day in ransomware incidents to 10 days in cases of financial theft, up to 122 days in cyber-espionage and data-theft operations.
Recommendations
Based on 2019 incident response insights, applying the following recommendations can help protect businesses from falling victim to similar attacks:
- Apply complex password policies
- Avoid management interfaces exposed to the internet
- Only allow remote access for necessary external services with multi-factor authentication – with necessary privileges only
- Regular system audits to identify vulnerable services and misconfigurations
- Continually tune security tools to avoid false positives
- Apply powerful audit policy with log retention period of at least six months
- Monitor and investigate all alerts generated by security tools
- Patch your publicly available services immediately
- Enhance your email protection and employee awareness
- Forbid use of PsExec to simplify security operations
- Threat hunting with rich telemetry, specifically deep tracing of PowerShell to detect attacks
- Quickly engage security operations after discovering incidents to reduce potential damage and/or data loss
- Back up your data frequently and on separated infrastructure
Reasons for incident response
Significant effects on infrastructure, such as encrypted assets, money loss, data leakage or suspicious emails, led to 30% of requests for investigations. More than 50% of requests came as a result of alerts in security toolstacks: endpoint (EPP, EDR), network (NTA) and others (FW, IDS/IPS, etc.).
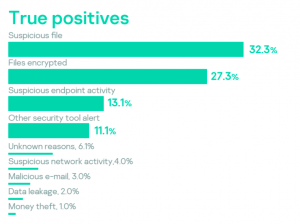
Organizations often only become aware of an incident after a noticeable impact, even when standard security toolstacks have already produced alerts identifying some aspects of the attack. Lack of security operations staff is the most common reason for missing these indicators. Suspicious files identified by security operations and suspicious endpoint activity led to the discovery of an incident in 75% of cases, while suspicious network activities in 60% of cases were false positives.
One of the most common reasons for an incident response service request is a ransomware attack: a challenge even for mature security operations. For more details on types of ransomware and how to combat it, view our story “Cities under ransomware siege“.
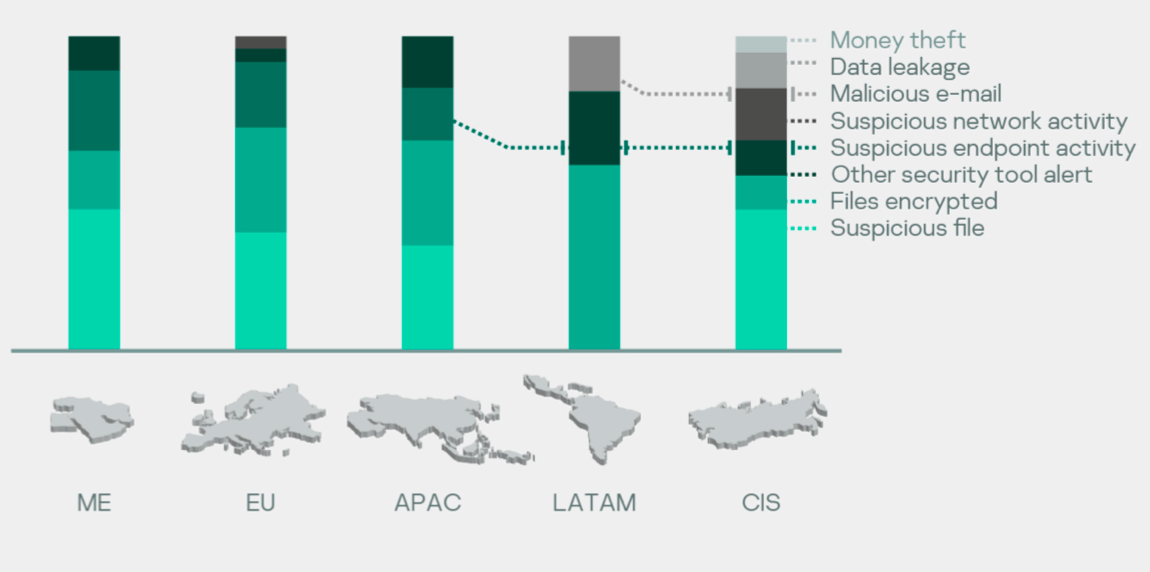
Distribution of reasons for top regions
A suspicious file is the most prevalent reason to engage incident response services. This shows that file-oriented detection is the most popular approach in many organizations. The distribution also shows that 100% of cases involving financial cybercrime and data leakage that we investigated occurred in CIS countries.
Distribution of reasons for industries
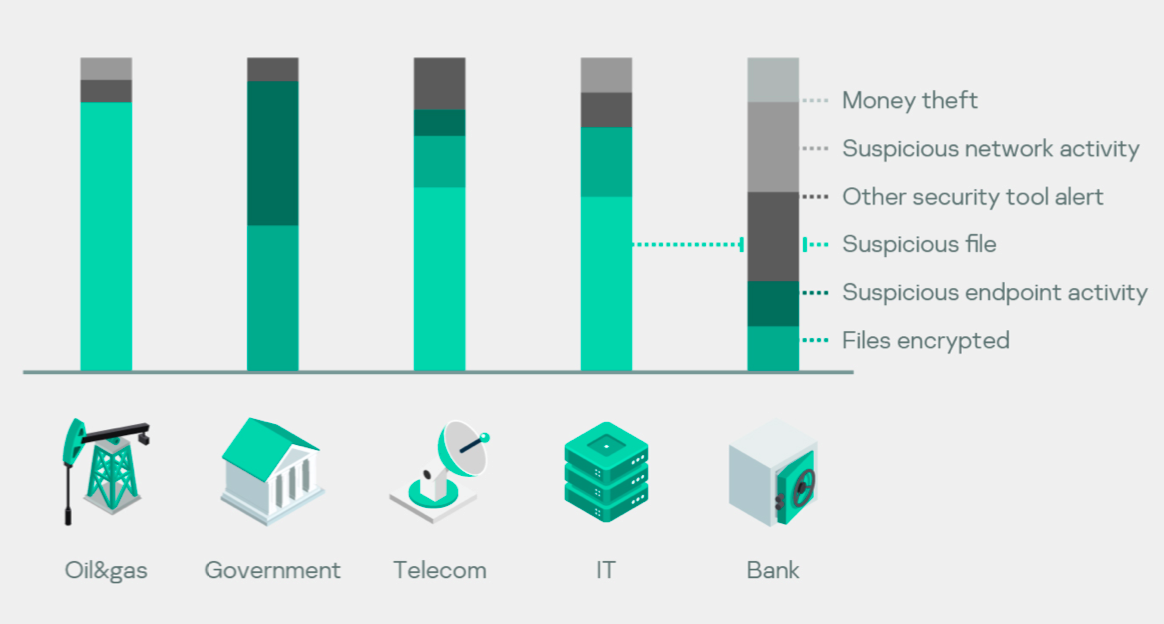
Although, different industries suffered from different incidents, 100% of money theft incidents occurred inside the financial industry (banks).
Detection of ransomware once the repercussions had been felt occurred primarily within the government, telecom and IT sectors.
Initial vectors or how adversaries get in
Common initial vectors include the exploitation of vulnerabilities (0- and 1-day), malicious emails and brute-force attacks. Patch management for 1-day vulnerabilities and applying password policies (or not using management interfaces on the internet) are well suited to address most cases. 0-day vulnerabilities and social engineering attacks via email are much harder to address and require a decent level of maturity from internal security operations.
By linking the popular initial compromise vectors with how an incident was detected, we can see detected suspicious files were detected from malicious emails. And cases detected after file encryption mostly took place after brute-force or vulnerability exploitation attacks.
Sometimes we act as complimentary experts for a primary incident response team from the victim’s organization and we have no information on all of their findings – hence the ‘Unknown reasons’ on the charts. Malicious emails are most likely to be detected by a variety of security toolstack, but that’s not showing distrubution of 0- to 1-day vulnerabilities.
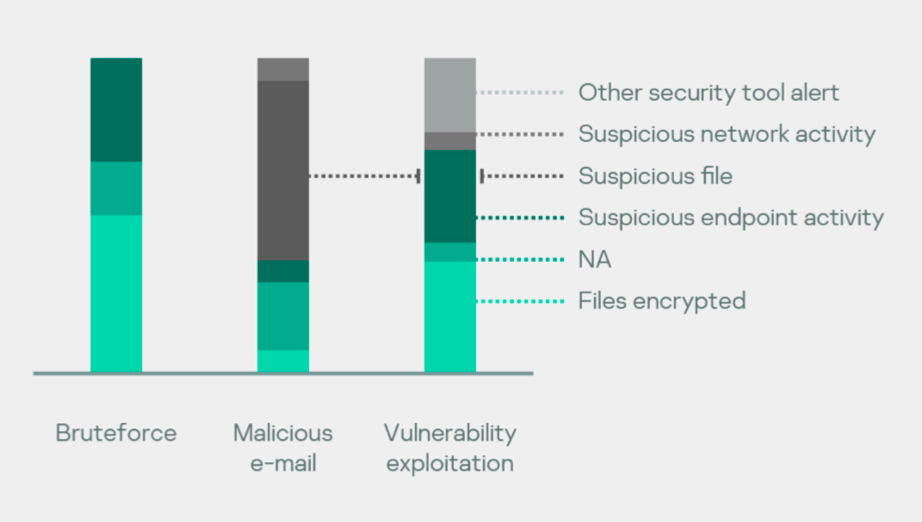
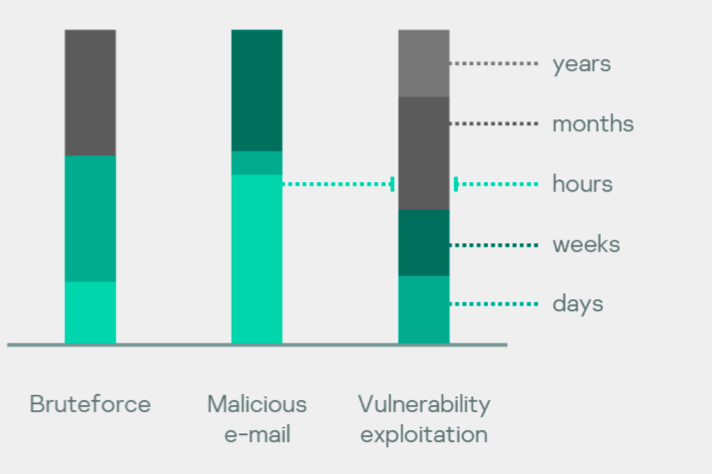
The distribution of how long an attack went unnoticed and how an organization was compromised shows that cases that begin with vulnerability exploitation on an organization’s network perimeter went unnoticed for longest. Social enginnering attacks via email were the most short-lived.
Tools and exploits
30% of all incidents were tied to legitimate tools
In cyberattacks, adversaries use legitimate tools which can’t be detected as malicious utilities as they are often used in everyday activities. Suspicious events that blend with normal activity can be identified after deep analysis of a malicious attack and connecting the use of such tools to the incident. The top used tools are PowerShell, PsExec, SoftPerfect Network Scanner and ProcDump.
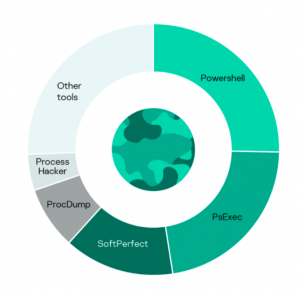
Most legitimate tools are used for harvesting credentials from memory, evading security mechanisms by unloading security solutions and for discovering services in the network. PowerShell can be used virtually for any task.
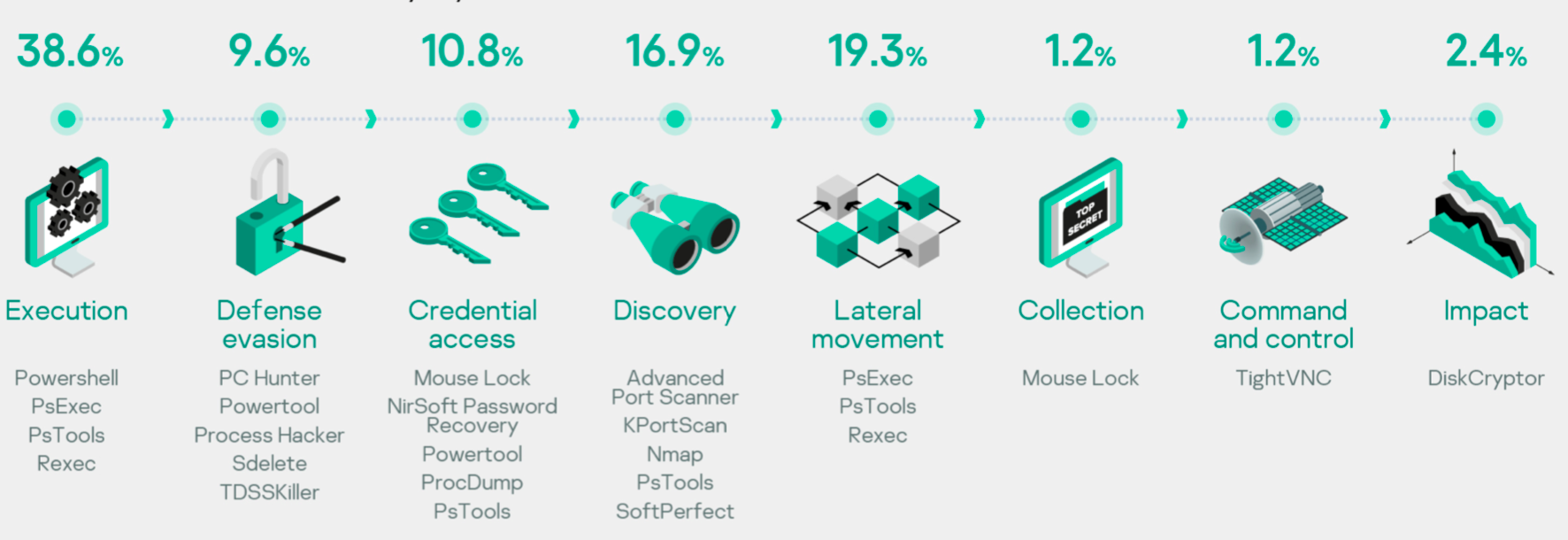
Let’s weight those tools based on occurrence in incidents – we will also see tactics (MITRE ATT&CK) where they are usually applied.
Exploits
Most of the identified exploits in incident cases appeared in 2019 along with a well-known remote code execution vulnerability in Windows SMB service (MS17-010) being actively exploited by a large number of adversaries.
| MS17-010 SMB service in Microsoft Windows Remote code execution vulnerability that was used in several large attacks such as WannaCry, NotPetya, WannaMine, etc. |
CVE-2019-0604 Microsoft Sharepoint Remote code execution vulnerability allows adversaries to execute arbitrary code without authentication in Microsoft Sharepoint. |
CVE-2019-19781 Citrix Application Delivery Controller & Citrix Gateway This vulnerability allows unauthenticated remote code execution on all hosts connected to Citrix infrastructure. |
| CVE-2019-0708 RDP service in Microsoft Windows Remote code execution vulnerability (codename: BlueKeep) for a very widespread and, unfortunately, frequently publicly available RDP service. |
CVE-2018-7600 Drupal Remote code execution vulnerability also known as Drupalgeddon2. Widely used in installation of backdoors, web miners and other malware on compromised web servers. |
CVE-2019-11510 Pulse Secure SSL VPN Unauthenticated retrieval of VPN server user credentials. Instant access to victim organization through legitimate channel. |
Attack duration
For a number of incidents, Kaspersky specialists have established the time period between the beginning of an adversary’s activity and the end of the attack. As a result of the subsequent analysis, all incidents were divided into three categories of attack duration.
| Rush hours or days | Average weeks | Long-lasting months or longer |
| This category includes attacks lasting up to a week. These are mainly incidents involving ransomware attacks. Due to the high speed of development, effective counteraction to these attacks is possible only by preventive methods. In some cases, a delay of up to a week has been observed between the initial compromise and the beginning of the adversary’s activity. |
This group includes attacks that have been developing for a week or several weeks. In most cases, this activity was aimed at the direct theft of money. Typically, the adversaries achieved their goals within a week. | Incidents that lasted more than a month were included in this group. This activity is almost always aimed at stealing sensitive data. Such attacks are characterized by interchanging active and passive phases. The total duration of active phases is on average close to the duration of attacks from the previous group. |
| Common threat: Ransomware infection |
Common threat: Financial theft |
Common threat: Cyber-espionage and theft of confidential data |
Common attack vector:
|
Common attack vector:
|
Common attack vector:
|
| Attack duration (median): 1 day |
Attack duration (median): 10 days |
Attack duration (median): 122 days |
| Incident response duration: Hours to days |
Incident response duration: Weeks |
Incident response duration: Weeks |
Operational metrics
False positives rate
False positives in incident responses are a very expensive exercise. A false positive means that triage of a security event led to the involvement of incident response experts who later ascertained that there was no incident. Usually this is a sign that an organization doesn’t have a specialist in threat hunting or they are managed by an external SOC that doesn’t have the full context for an event.
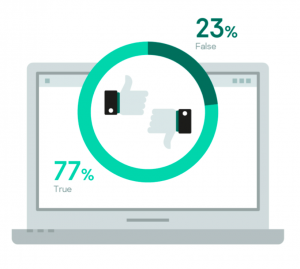
Age of attack
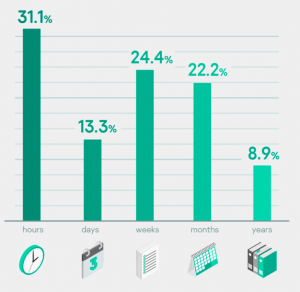
This is the time taken to detect an incident by an organization after an attack starts. Usually detecting the attack in the first few hours or even days is good; with more low-profile attacks it can take weeks, which is still OK, but taking months or years is definitely bad.
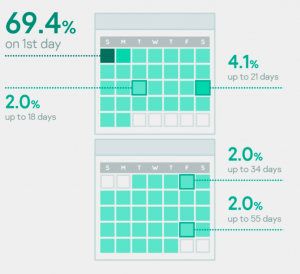
How fast we responded
How long it took us to respond after an organization contacted us. 70% of the time we start work from day one, but in some cases a variety of factors can influence the timeframe.
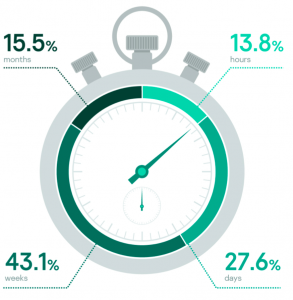
How long response took
Distribution of the time required for incident response activities can vary from a few hours to months based on how deep the adversaries were able to dig into the compromised network and how old the first compromise is.
MITRE ATT&CK tactics and techniques
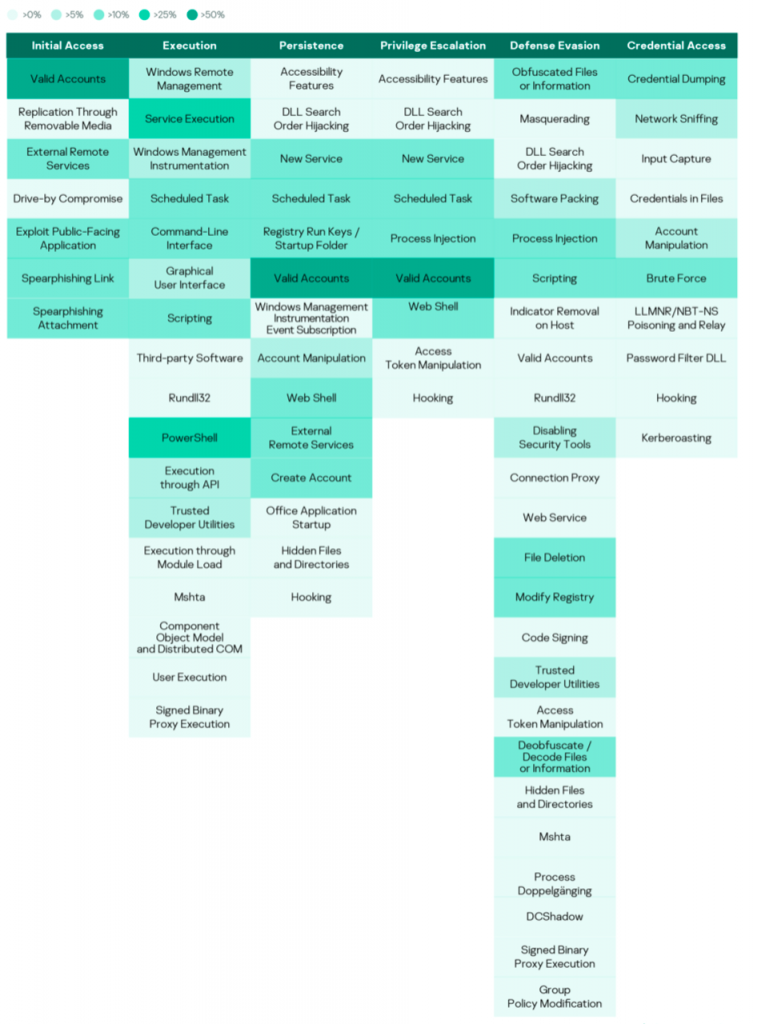
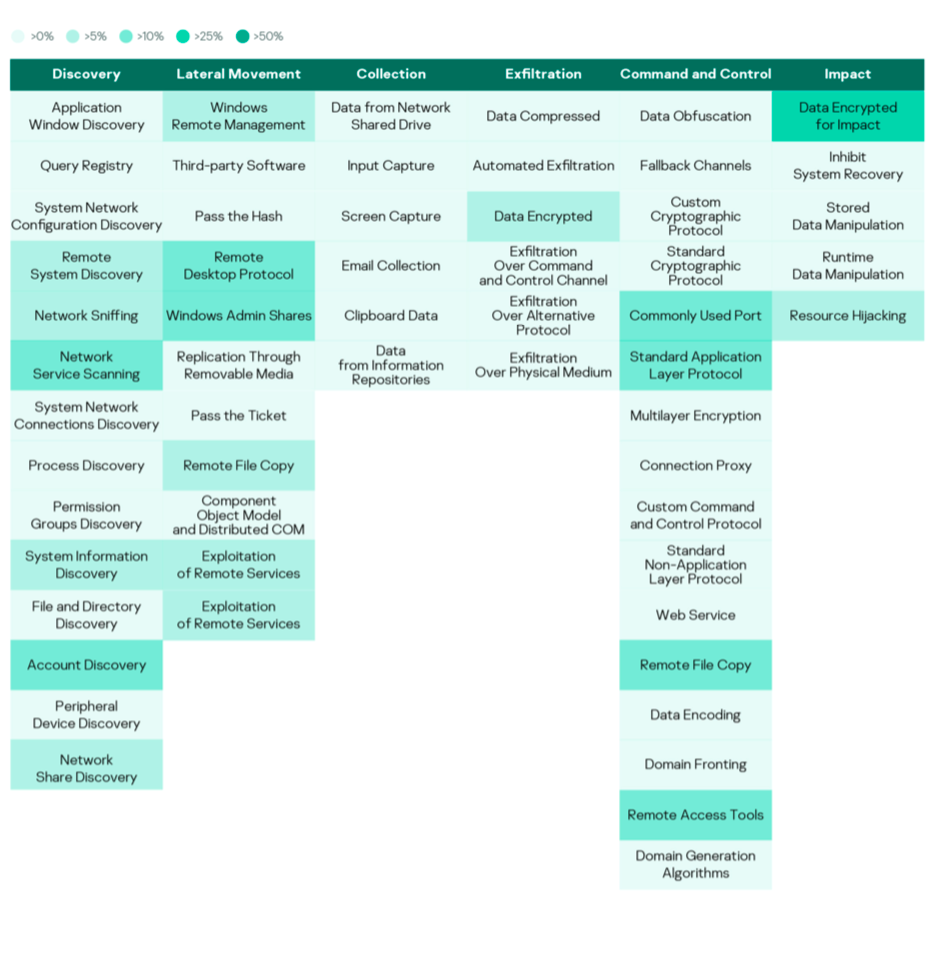
Conclusion
In 2019, the cyberattack curve was not flattened. There was an increase in the number of incidents accompanied by greater commitment among victims to understand the full attack picture. Victims from all regions suffered from a variety of attacks and all business types were targeted.
Improved security and audit planning with continuous maintenance of procedures along with rapid patch management could have minimized damages and losses in many of the analyzed incidents. In addition, having security monitoring and an investigation plan either on-premises or performed by a third party could have helped in stopping adversaries in the early phases of the attack chain, or start detections immediately after compromise.
Various tactics and techniques were used by adversaries to achieve their targets, trying multiple times till they succeeded. This indicates the importance of security being an organized process with continuous improvements instead of separate, independent actions.
Adversaries made greater use of legitimate tools in different phases of their cyberattacks, especially in the early phases. This highlights the need to monitor and justify the use of legitimate administration tools and scanning utilities within internal networks, limiting their use to administrators and necessary actions only.
Applying a powerful auditing policy with a log retention period of at least six months can help reduce analysis times during incident investigation and help limit the types of damage caused. Having insufficient logs on endpoints and network levels means it takes longer to collect and analyze evidence from different data sources in order to gain a complete picture of an attack.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


