Introducing EDR for Linux: Remediating and isolating threats on Linux servers
We’re excited to announce our new EDR for Linux offering, which extends our advanced protection and response capabilities to Linux devices via Nebula and OneView.
In this post, we show you what remediating and isolating threats on Linux servers looks like with Malwarebytes EDR for Linux.
Let’s get started!
Table of Contents
- Part 1: Downloading the test tool
- Part 2: Remediating endpoints
- Part 3: Endpoint isolation
- Part 4: Removing endpoint isolation
Part 1: Downloading the test tool
Malwarebytes EDR for Linux provides a test tool to trigger suspicious activity.
Executing a shell script named trigger.sh, we downloaded Ncat from a Github repository and stored it in a temporary folder. We then ran Ncat from the temporary folder, trying to manipulate SSH authorized keys.
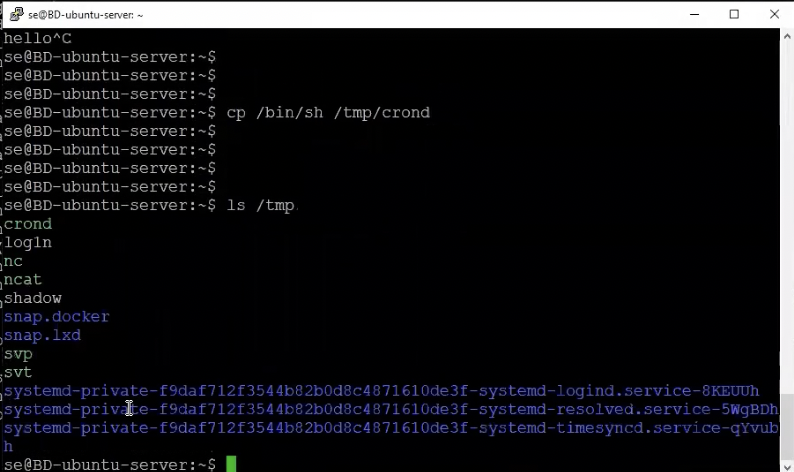
We can see that Ncat is now in our temporary folder.
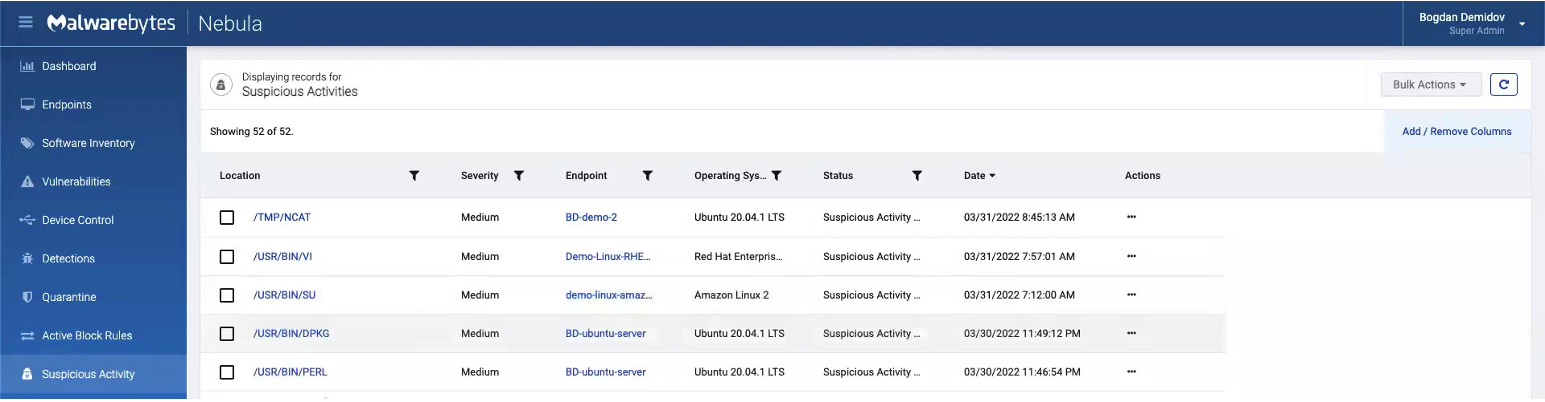
Let’s head back to Nebula and check the “Suspicious activities” tab. At the top, we’ll see that on our DB-demo-2 endpoint, Ncat in our temporary folder is being flagged as suspicious.
You might be wondering though: why exactly is running Ncat from a temporary folder considered suspicious? To find the reason, we can click on the /TMP/NCAT alert and see what detection rule was triggered.
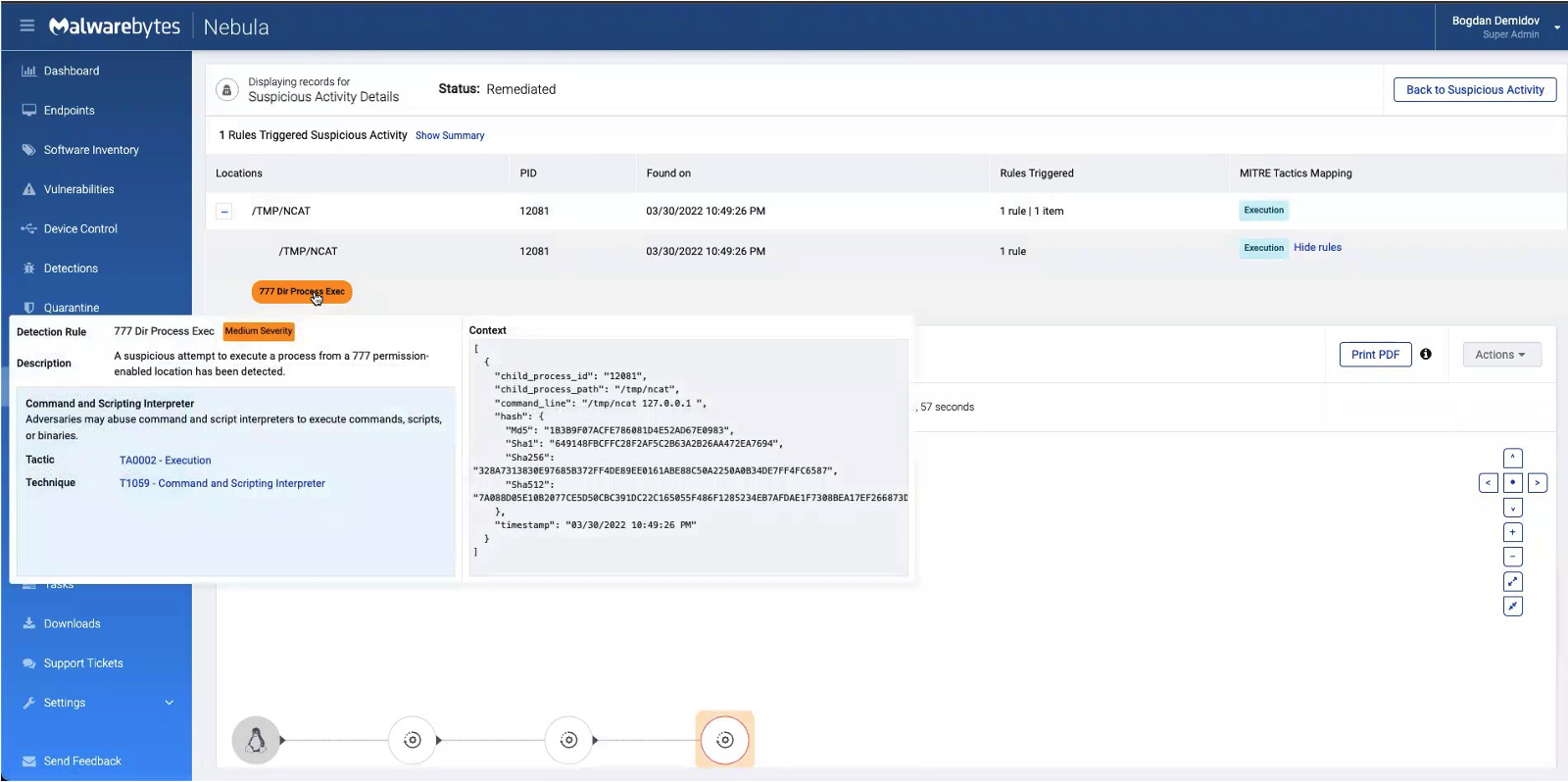
As you can see above, we find that the technique triggered is Command and Scripting Interpreter. The attempt to execute a process from the temp folder – which gives full privileges – has been detected.
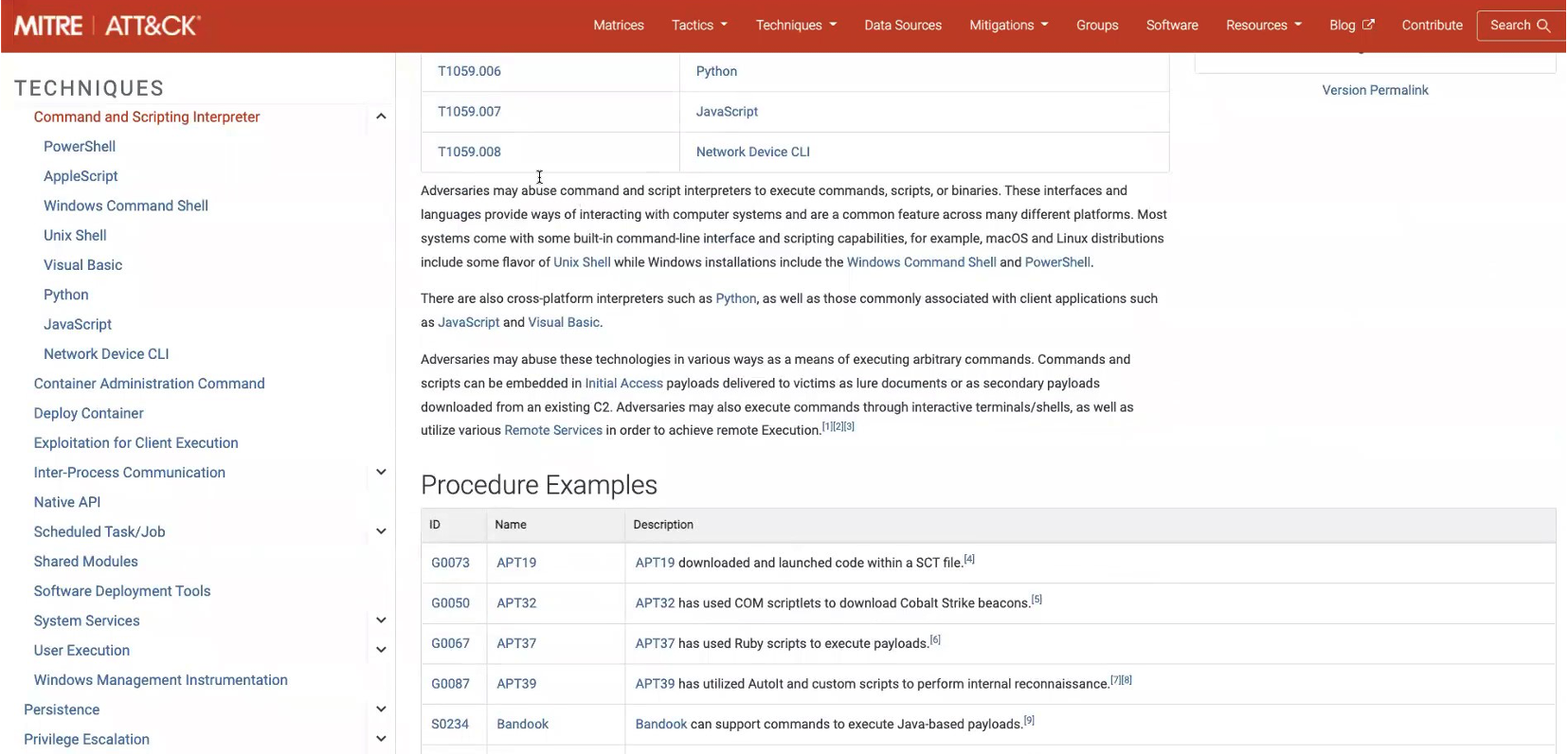
We can learn more about this particular adversary behavior, as well as which groups leverage these sorts of attacks, by clicking on the “T1059 – Command Scripting and Interpreter” link. This takes us to a MITRE ATT&CK page on the topic.
Part 2: Remediating endpoints
Now, it’s time to remediate the threat!
Going back to the “Suspicious Activity” tab, we can bulk select the threats we want to remediate. Under the “Bulk Actions” tab on the upper-right, a drop-down menu appears with a “Remediate” option.
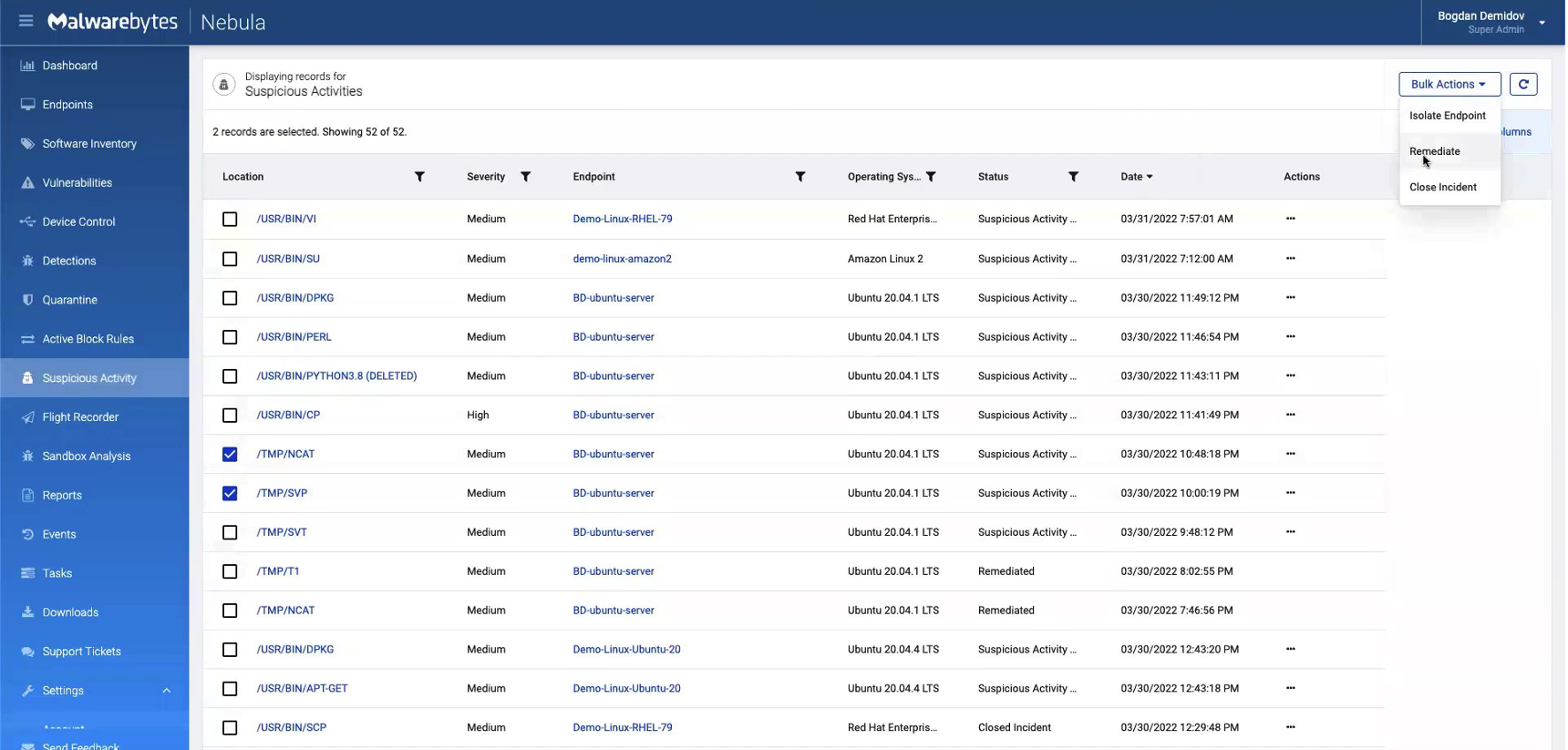
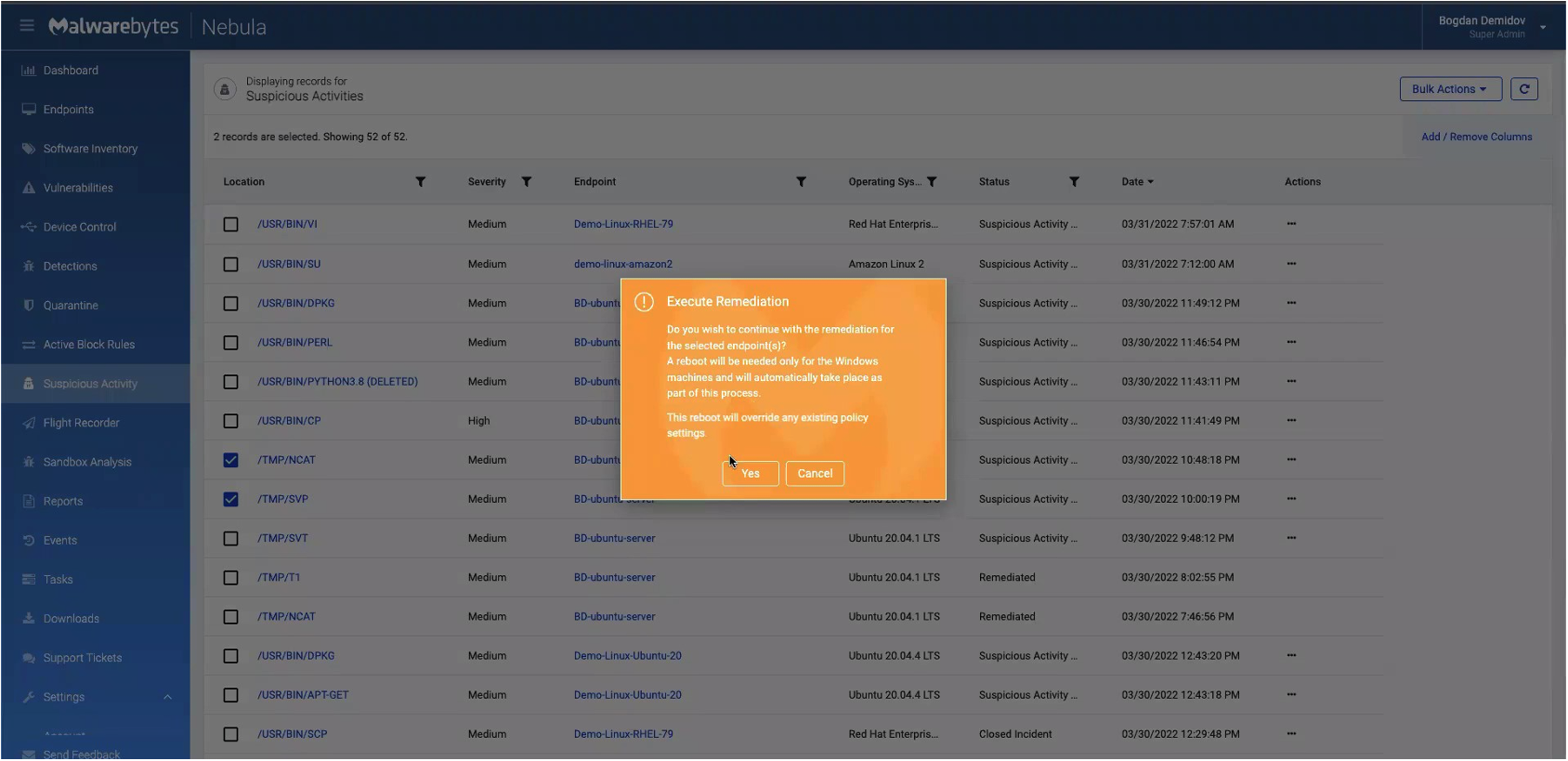
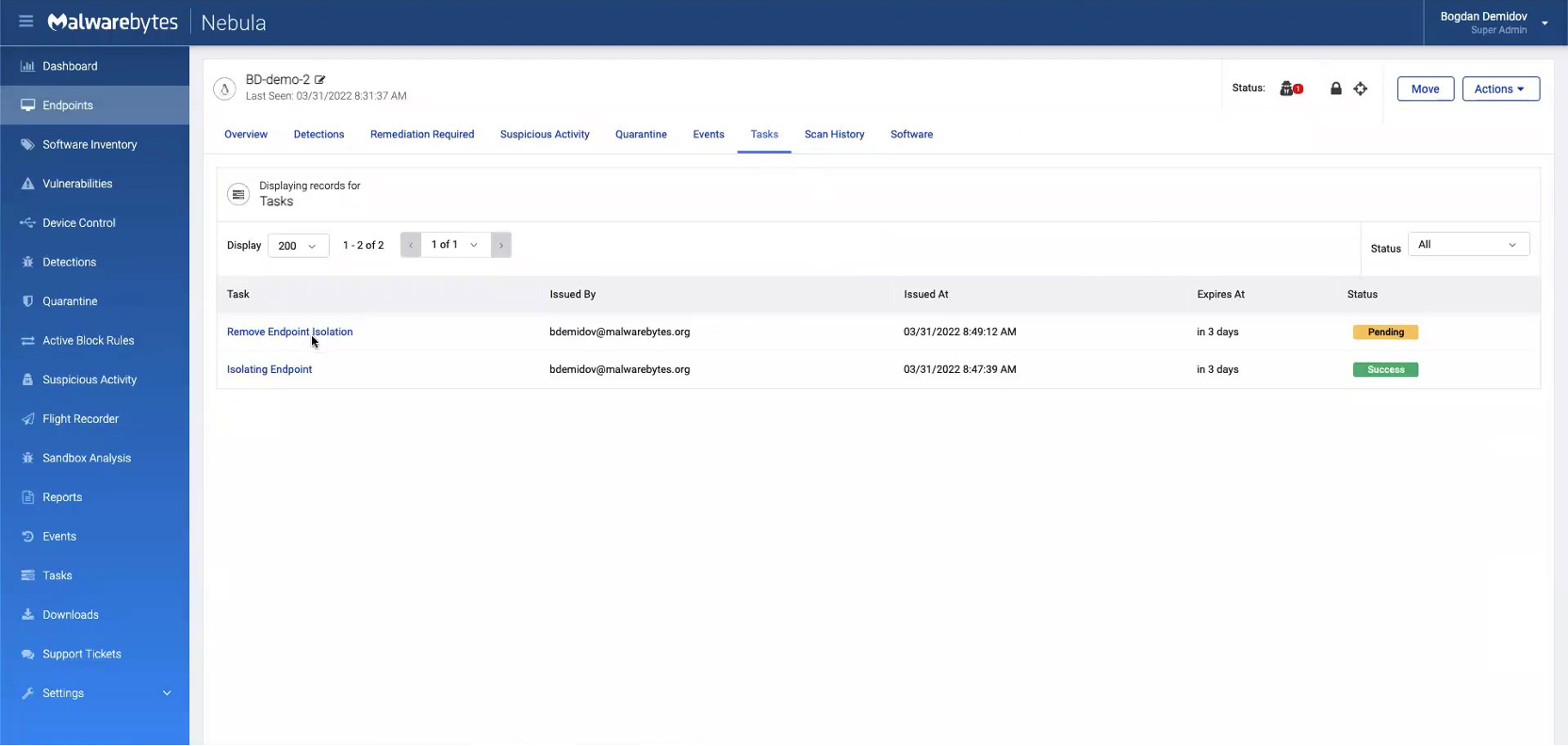
The remediation process takes about one to two minutes to complete. We can check on the status of our remediation by going to the “Tasks” tab and clicking on the threat, as shown below.
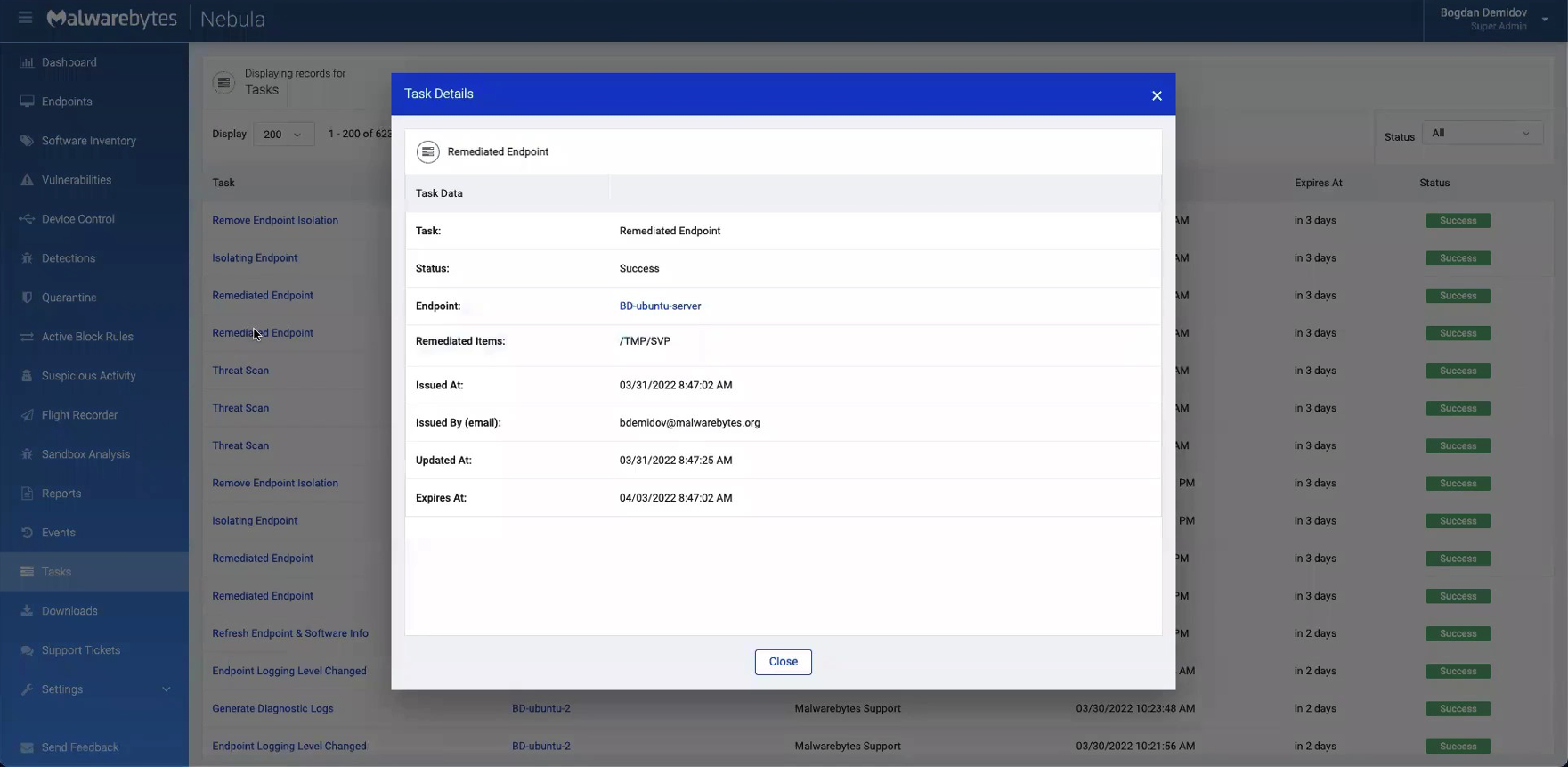
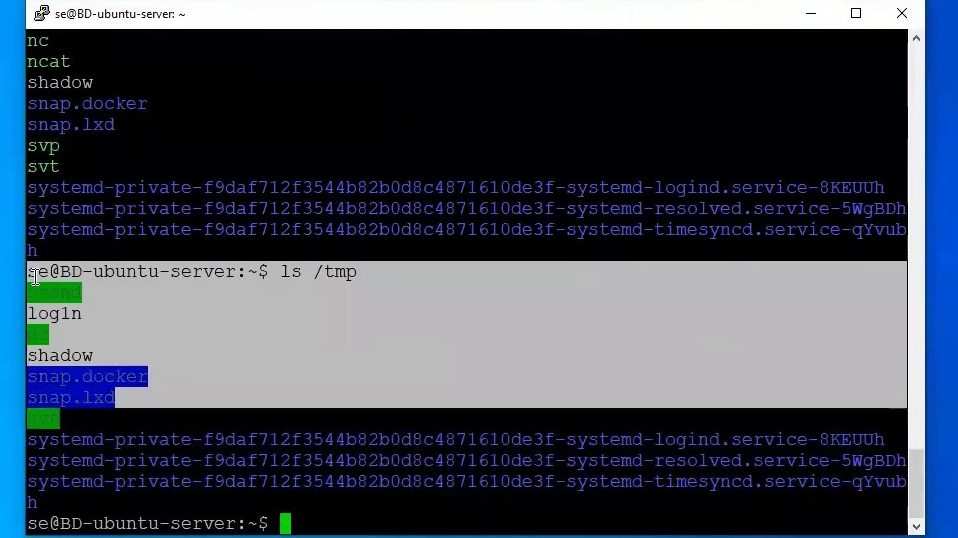
Let’s confirm by checking back on our temp folder. As you can see, Ncat has been removed by our remediation engine.
Part 3: Endpoint isolation
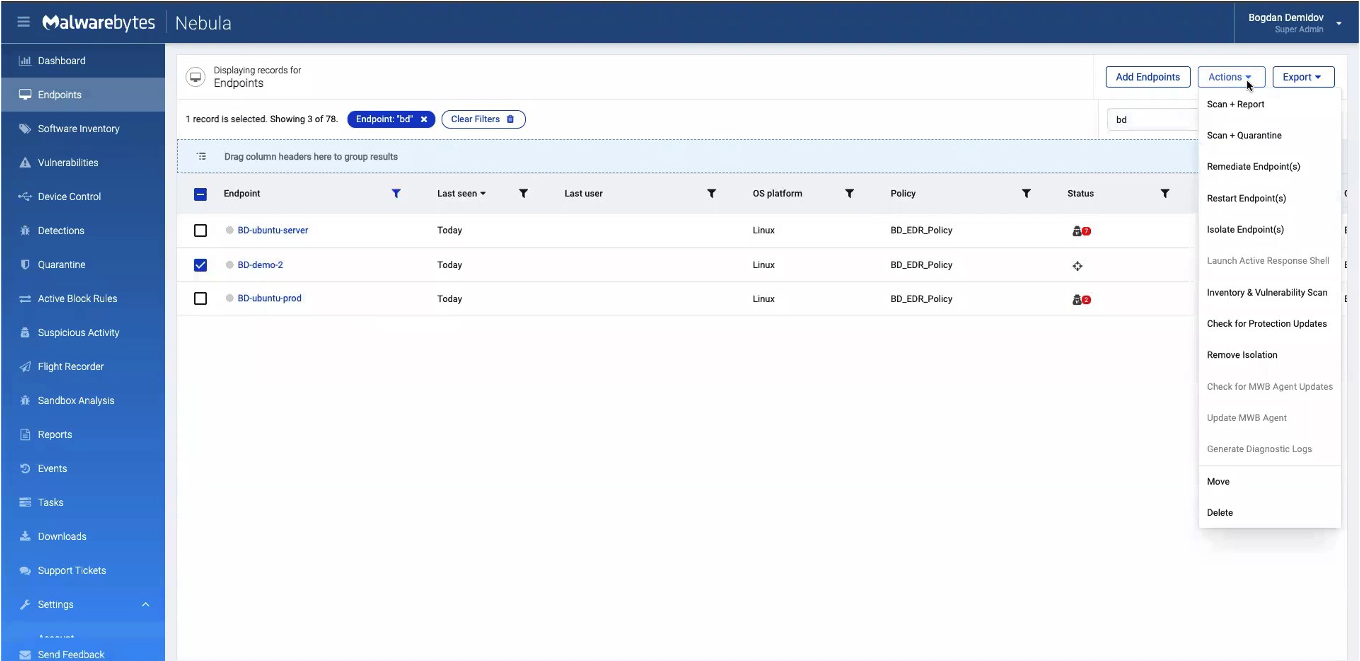
We can isolate an endpoint by going over to the “Endpoints” tab. After selecting the machine we wish to isolate, we go under the “Actions” tab in the upper-right, a drop-down menu appears with a “Isolate Endpoint(s)” option.
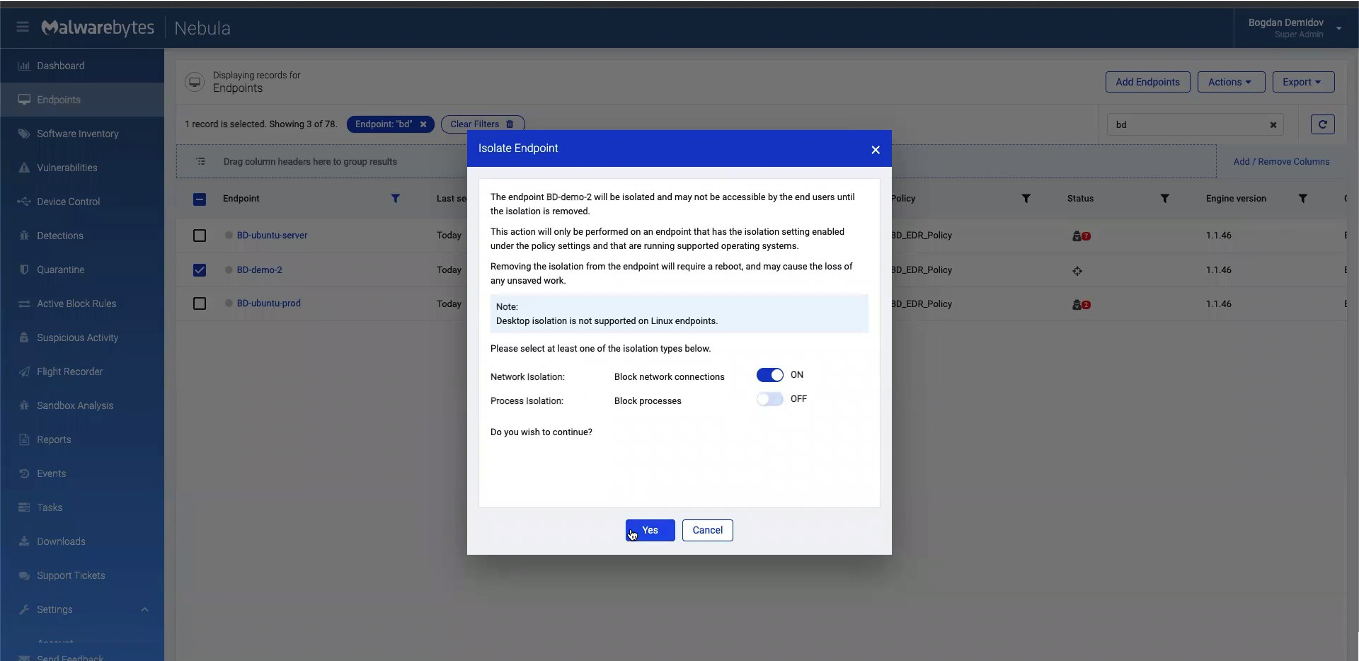
We’re given the option to toggle either “Block network connections” or “Block Processes’‘ for this device. For this example, we only want to do network isolation.
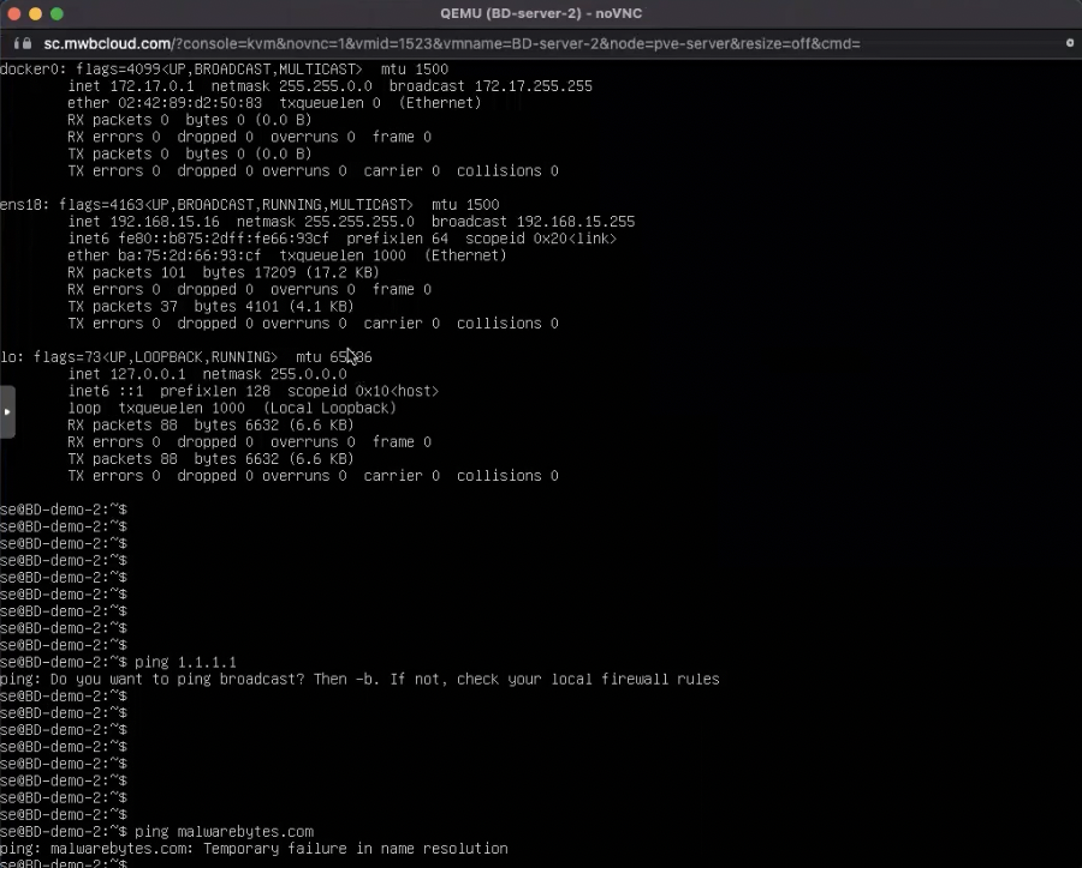
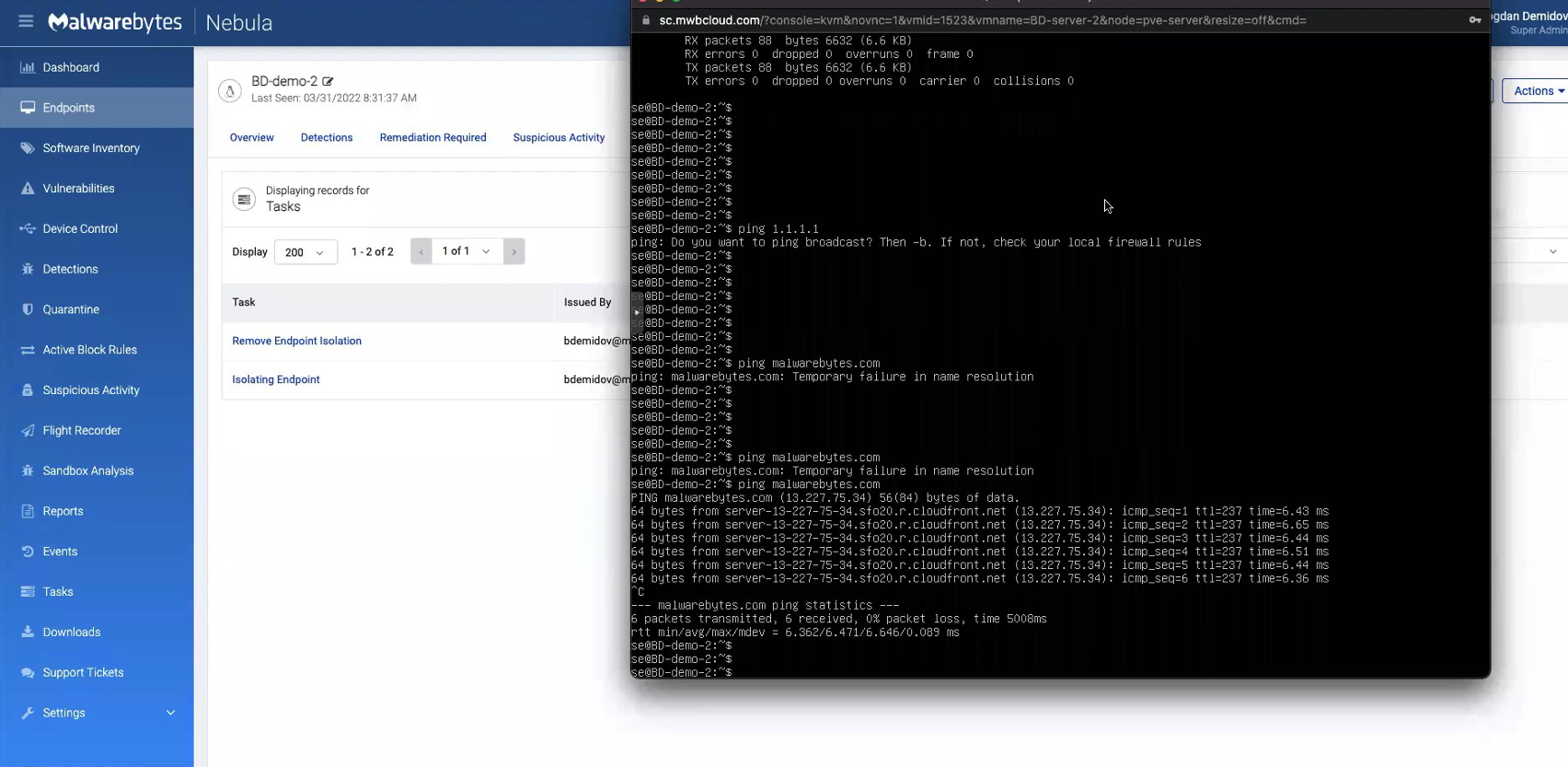
This blocks the endpoint from all outbound and inbound communication – except trusted communication, such as with Nebula servers or OpenVPN. And, as you see below, we are disconnected from the endpoint and no longer able to ping it.
Part 4: Removing endpoint isolation
While we are no longer able to connect to the machine, we are still able to manage it. Going back to the “Endpoints” tab, we’re able to see the status of our device by clicking on it and going to “Tasks”.
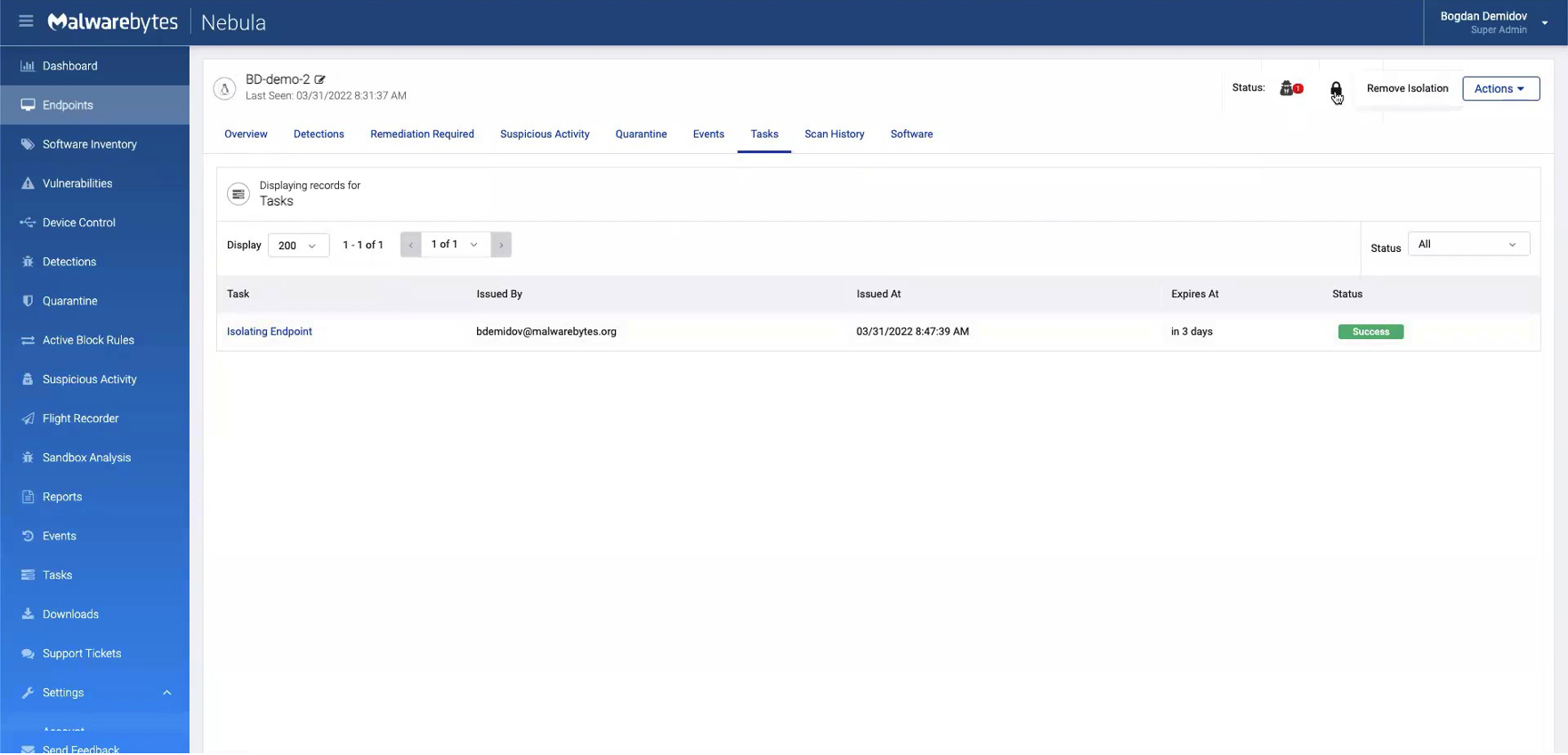
We see that the “Isolating Endpoint” task is successful. To remove the isolation, we start by clicking the lock icon in the upper-right corner, which will prompt a “Remove Isolation” button.
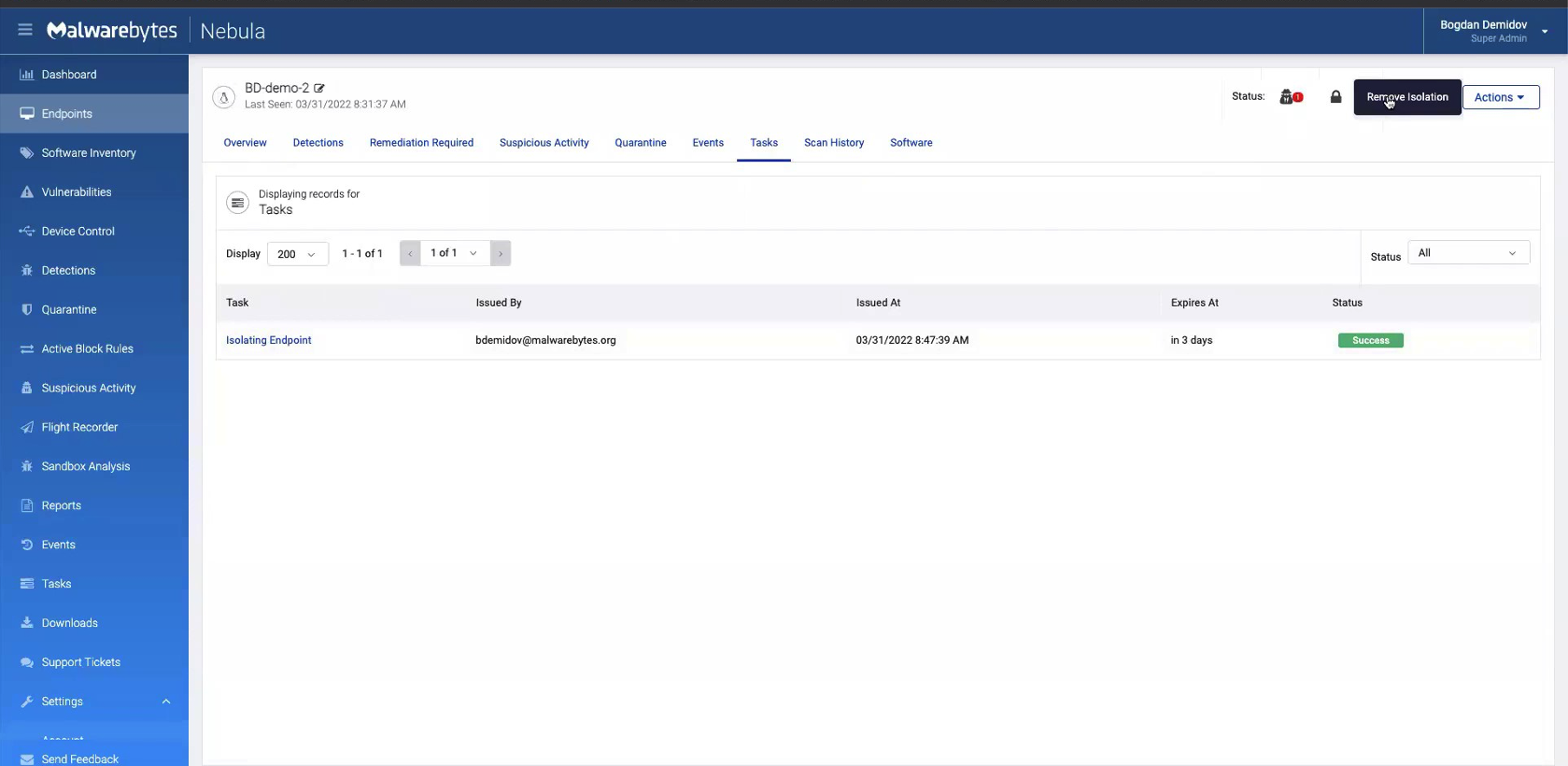
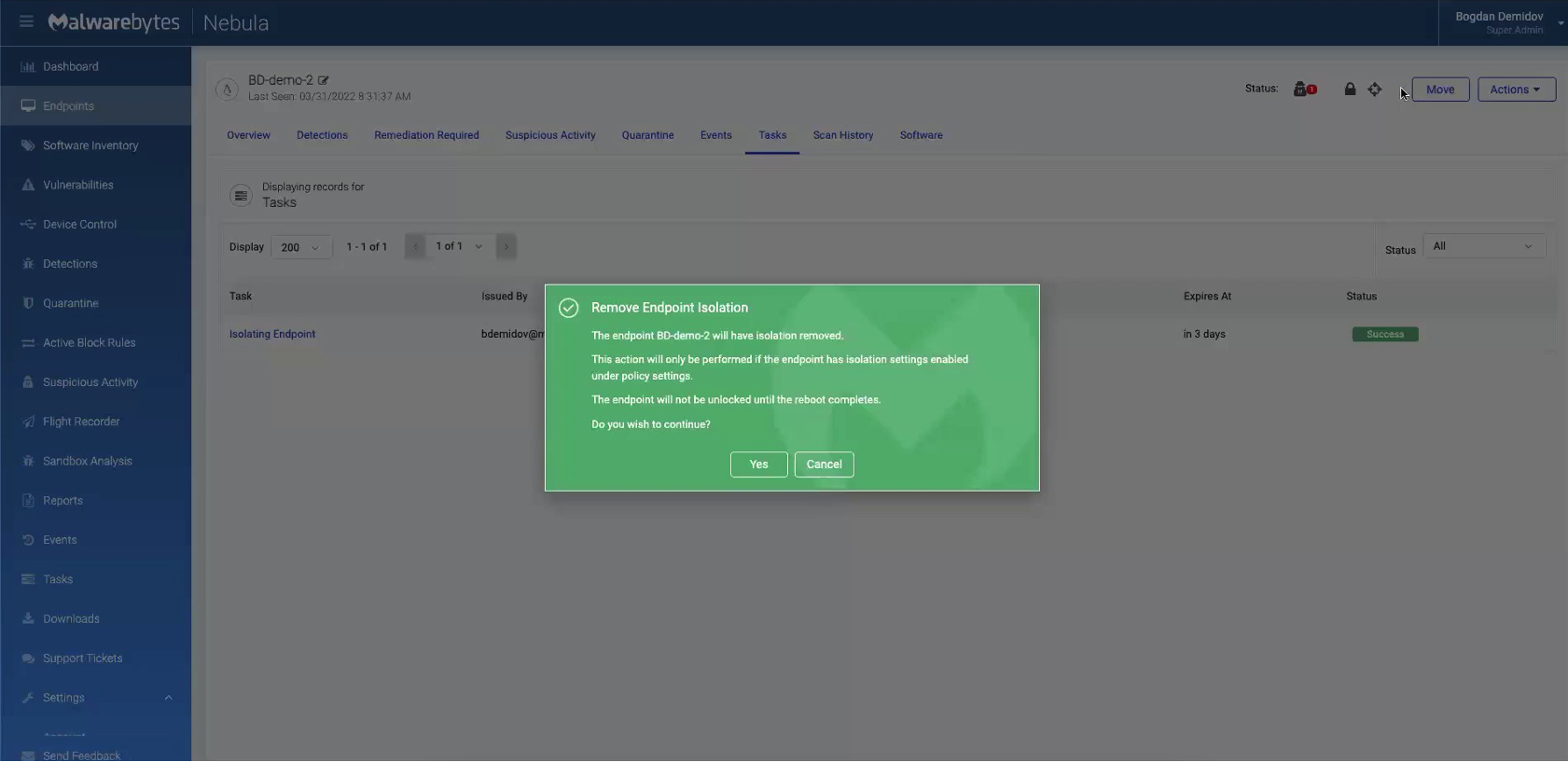
When we refresh the page, our “Remove Endpoint Isolation” task appears with a pending status. Again, give this another minute to resolve to complete.
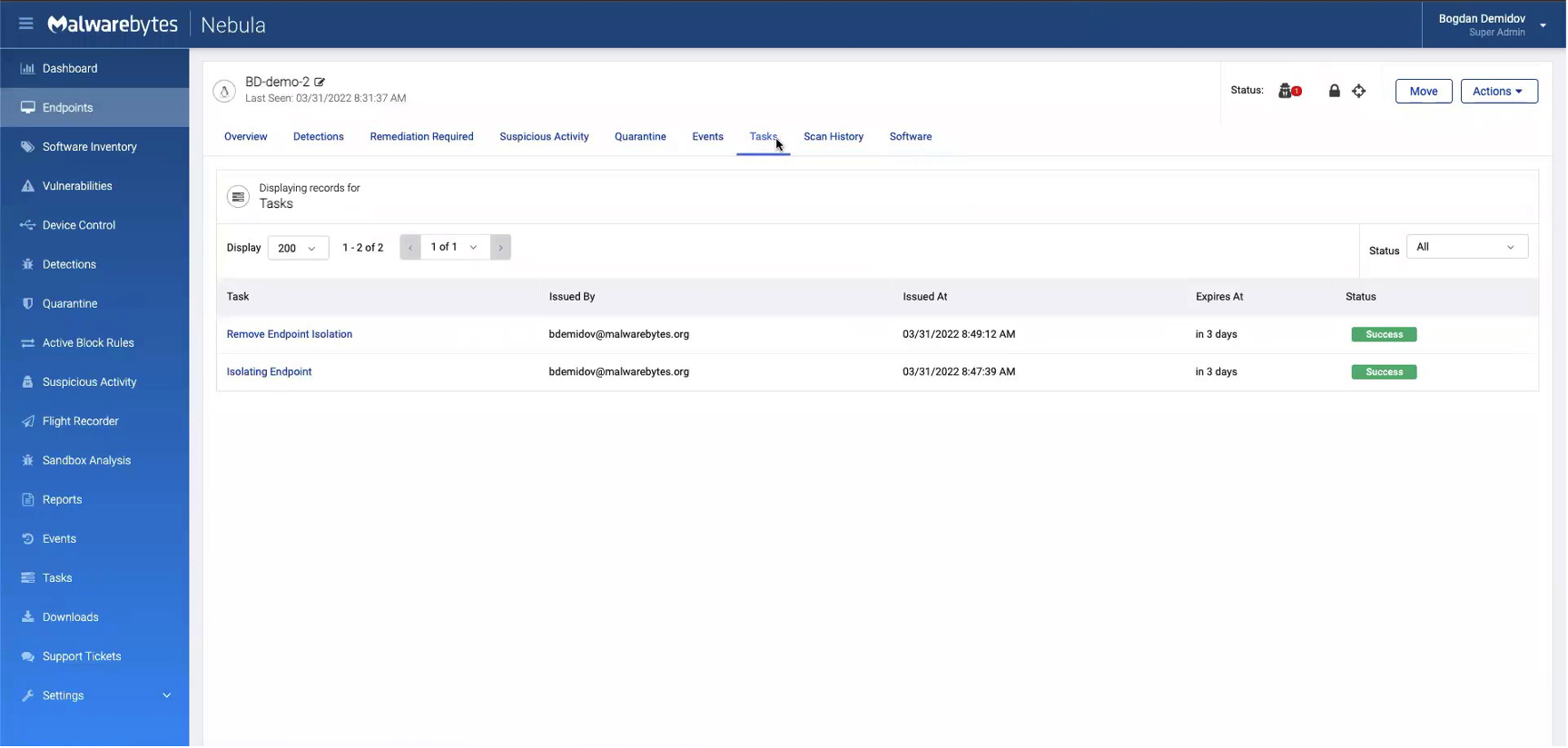
Now, we have reestablished a connection with the endpoint and can ping it.
Learn more about Malwarebytes EDR for Linux.
The post Introducing EDR for Linux: Remediating and isolating threats on Linux servers appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


