Iptable_Evil – An Evil Bit Backdoor For Iptables
When connecting to the backdoored VM from a VM that does not set the evil bit, the SSH connection will eventually time out.
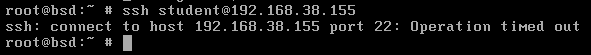
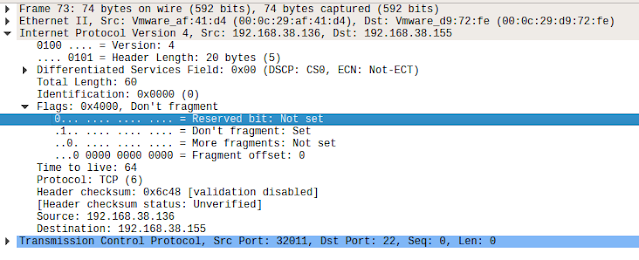
Packet captures of backdoor and non-backdoor SSH connections are in the docs/ folder in this repo for your perusal.
Kernel Version
- 5.8.0-48-generic (Ubuntu 20.04)
Further Information and Resources
- RFC 3514 inventing the evil bit: https://tools.ietf.org/html/rfc3514
- Ben Cox’s introduction to the evil bit: https://blog.benjojo.co.uk/post/evil-bit-RFC3514-real-world-usage
- Ben Cox’s
iptables_uwu(mostly just for giving the names of things to research): https://github.com/benjojo/iptables-uwu - A somewhat outdated but very detailed explanation of how
iptablesworks and how to add targets and modules to it: https://inai.de/documents/Netfilter_Modules.pdf - https://upload.wikimedia.org/wikipedia/commons/3/37/Netfilter-packet-flow.svg
- Bootlin’s Elixir search is significantly easier to use to find identifiers in the kernel than grep: https://elixir.bootlin.com/linux/v5.8/source/net/ipv4/netfilter/ip_tables.c#L225
- Ubuntu’s docs explain how to build the kernel: https://wiki.ubuntu.com/Kernel/BuildYourOwnKernel
Download Iptable_Evil
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



