Iron Tiger hackers create Linux version of their custom malware

The APT27 hacking group, aka “Iron Tiger,” has prepared a new Linux version of its SysUpdate custom remote access malware, allowing the Chinese cyberespionage group to target more services used in the enterprise.
According to a new report by Trend Micro, the hackers first tested the Linux version in July 2022. However, only in October 2022 did multiple payloads begin circulating in the wild.
The new malware variant is written in C++ using the Asio library, and its functionality is very similar to Iron Tiger’s Windows version of SysUpdate.
The threat actor’s interest in expanding the targeting scope to systems beyond Windows became evident last summer when SEKOIA and Trend Micro reported seeing APT27 targeting Linux and macOS systems using a new backdoor named “rshell.”
APT27’s latest campaign
The observed SysUpdate campaign analyzed by Trend Micro deployed both Windows and Linux samples against valid targets.
One of the victims of this campaign was a gambling company in the Philippines, whose attack utilized a command and control server registered with a domain similar to the victim’s brand.
The infection vector is unknown, but Trend Micro’s analysts hypothesize that chat apps were used as lures to trick employees into downloading initial infection payloads.
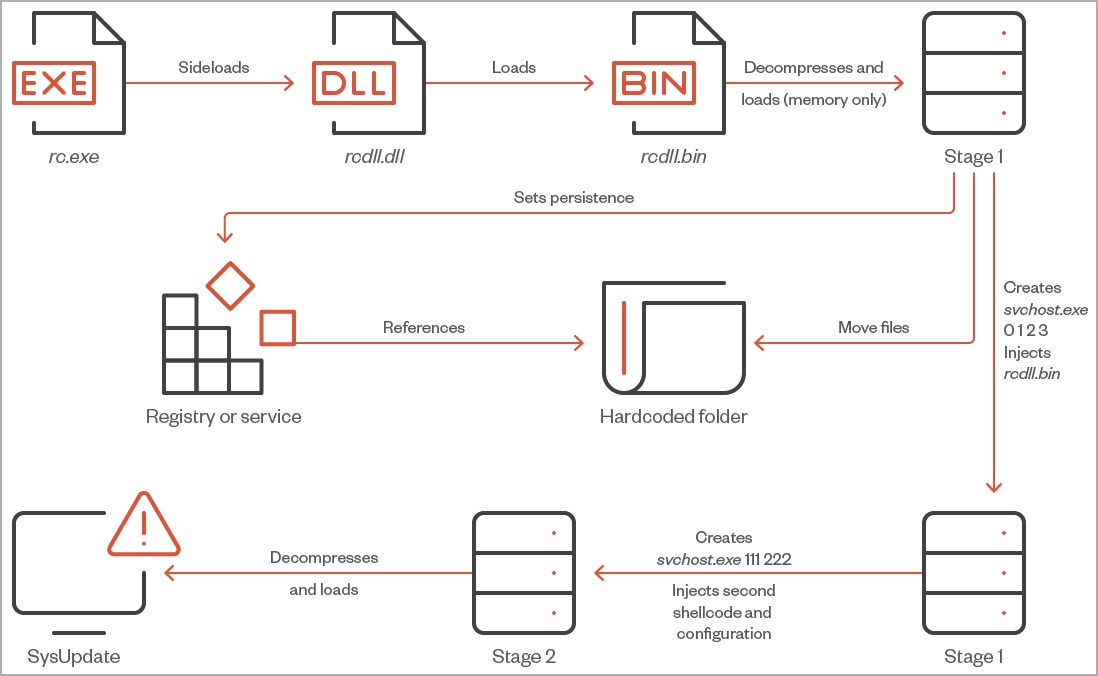
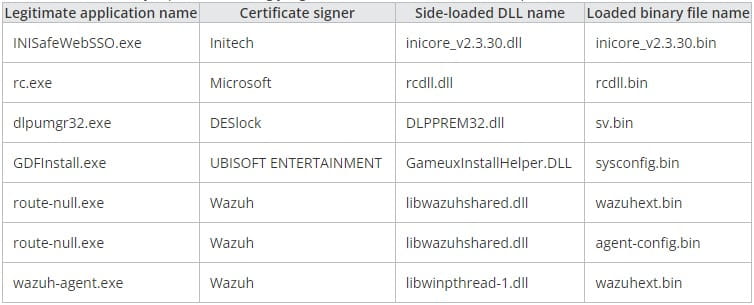
One item that has evolved compared to past campaigns relying on SysUpdate is the loading process, which now uses a legitimate and digitally-signed “Microsoft Resource Compiler” executable (rc.exe) to perform DLL side-loading with rc.dll to load shellcode.
The shellcode loads the first stage of SysUpdate in memory, so it’s difficult for AVs to detect. Then, it moves the required files to a hardcoded folder and establishes persistence with Registry modifications or by creating a service, depending on the process permissions.
The second stage will launch after the next system reboot to decompress and load the primary SysUpdate payload.
SysUpdate is a feature-rich remote access tool allowing a threat actor to perform a variety of malicious behavior as listed below:
- Service manager (lists, starts, stops, and deletes services)
- Screenshot grab
- Process manager (browses and terminates processes)
- Drive information retrieval
- File manager (finds, deletes, renames, uploads, downloads a file, and browses a directory)
- Command execution
Trend Micro comments that Iron Tiger used a Wazuh-signed executable in later sideloading stages to blend with the victim’s environment, as the target organization used the legitimate Wazuh platform.
New Linux version of SysUpdate
The Linux variant of SysUpdate is an ELF executable and shares common network encryption keys and file-handling functions with its Windows counterpart.
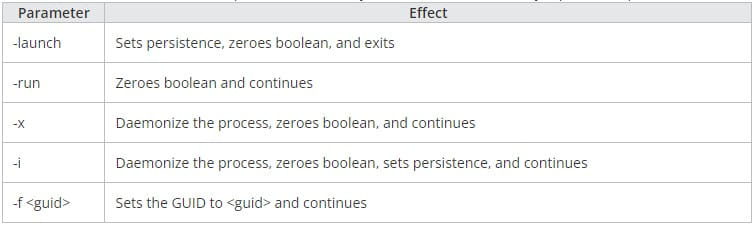
The binary supports five parameters that determine what the malware should do next: setting persistence, daemonizing the process, setting a GUID (Globally Unique Identifier) for the infected system, etc.
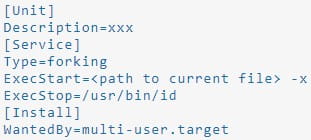
The malware establishes persistence by copying a script to the “/usr/lib/systemd/system/” directory, an action that requires root user privileges.
Upon its launch, it sends the following information to the C2 server:
- GUID (picked at random if its parameter wasn’t used previously)
- Host name
- Username
- Local IP address and port used to send the request
- Current PID
- Kernel version and machine architecture
- Current file path
- Boolean (0 if it was launched with exactly one parameter, 1 otherwise)
One new feature in the Linux SysUpdate variant is DNS tunneling, seen only on one Windows sample of the malware.
SysUpdate obtains DNS information from “/etc/resolv.conf” file to retrieve the default system DNS IP address which can be used for sending and receiving DNS queries. If that fails, it uses Google’s DNS server at 8.8.8.8.
The idea of this system is to bypass firewalls or network security tools that might be configured to block all traffic beyond a specific IP address allowlist.
Trend Micro says the choice of the Asio library for developing the Linux version of SysUpdate might be due to its multi-platform portability and predicts that a macOS version of the malware might appear in the wild soon.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.





