Is your web browser vulnerable to data theft? XS-Leak explained
In recent news, IT security researchers from Ruhr-Universität Bochum (RUB) and the Niederrhein University of Applied Sciences have disclosed 14 new cross-site leak (also known as XSLeak or XS-Leak) attacks that can affects modern browsers, such as Google Chrome, Microsoft Edge, Mozilla Firefox, and Apple’s Safari. Although the news and press release regarding this haven’t mentioned other browsers that are Chromium-based and Firefox-based, we can make a cautious assumption that these, too, could be vulnerable to the new XS-Leak attacks.
But what is XS-Leak? Why should internet users be worried about them? And how can they protect themselves from such web threats?
XS-Leak, explained
An XS-Leak is a type of attack that targets inherent side-channels of a web platform, allowing actors to bypass the ‘same-origin’ policy (SOP) in web browsers so they can steal user information in the background from trusted and legitimate websites. A side-channel can operate as an information leakage channel, as it “allows an attacker to infer information about a secret by observing nonfunctional characteristics of a program, such as execution time or memory consumed.” [1]
The “same-origin policy” is a critical security mechanism. Its purpose is to prevent information from being stolen from websites that users trust. It does this by restricting how documents and scripts from one origin (the URL location) can interact with resources on another origin. Without this policy, an attacker who successfully compromises a script could see everything in a user’s browser.
Browsers support various interactions between websites and web applications. XS-Leaks take advantage of a minute amount of data that is exposed every time this interaction happens between websites.
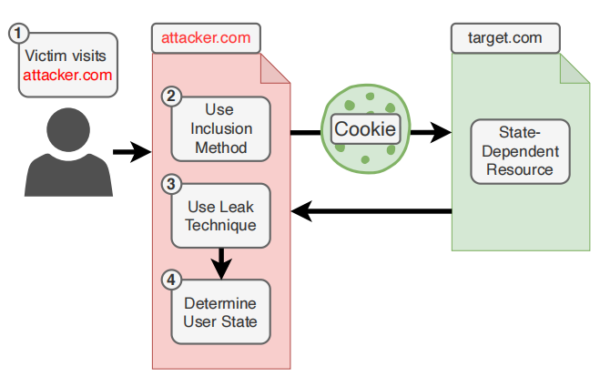
XS-Leaks Wiki further explains: “The principle of an XS-Leak is to use such side-channels available on the web to reveal sensitive information about users, such as their data in other web applications, details about their local environment, or internal networks they are connected to.”
XS-Leaks has been around since at least the year 2000, and 34 of them have been identified and classified. XS-Leaks can be caused by different things, such as browser APIs, browser implementation details and bugs, and hardware bugs (like vulnerabilities in modern processors that Meltdown and Spectre exploit).
What is the XSinator?
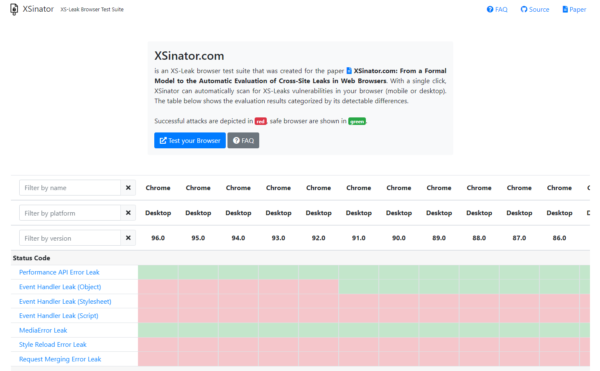
The XSinator is a “browser test suite” or online tool that anyone can use to automatically scan for XS-Leaks vulnerabilities in the user’s mobile and desktop browser. XSinator.com has been created as accompanying material for the researchers’ paper entitled, “XSinator.com: From a formal Model to the Automatic Evaluation of Cross-Site Leaks in Web Browsers” [PDF].
How can I protect myself from XS-Leaks?
Mitigating the risks presented by XS-Leaks falls on the hands of web browser developers. And protecting against this, they continue to do so as some browsers have already implemented a number of new defense mechanisms against it.
IT security researchers from both universities have informed the web browser development teams of their findings and are currently fixing the issues. They also made available detailed technical defenses that browser developers can implement against XS-Leaks in their paper.
The post Is your web browser vulnerable to data theft? XS-Leak explained appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[SAFEPAY] - Ransomware Victim: frapack[.]de 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)