IT threat evolution Q3 2022

- IT threat evolution in Q3 2022
- IT threat evolution in Q3 2022. Non-mobile statistics
- IT threat evolution in Q3 2022. Mobile statistics
Targeted attacks
CosmicStrand: discovery of a sophisticated UEFI rootkit
In July, we reported a rootkit that we found in modified Unified Extensible Firmware Interface (UEFI) firmware, the code that loads and initiates the boot process when the computer is turned on. Rootkits are malware implants that are installed deep in the operating system. Difficult to detect, they ensure that a computer remains infected even if someone reinstalls the operating system or replaces the hard drive. However, they aren’t easy to create: the slightest programming error could crash the machine. Nevertheless, in our APT predictions for 2022, we noted that more attackers would reach the sophistication level required to develop such tools.
The main purpose of CosmicStrand is to download a malicious program at startup, which then performs the tasks set by the attackers. Having successfully passed through all stages of the boot process, the rootkit eventually runs a shell code and contacts the attackers’ C2 (Command-and-Control) server, from which it receives a malicious payload.
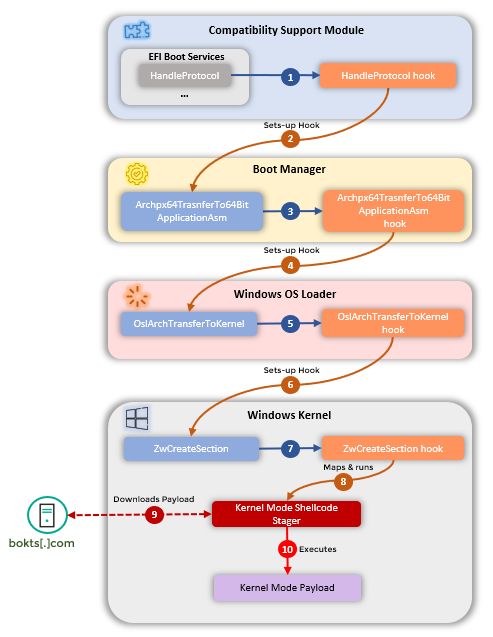
We were unable to intercept the file received by the rootkit from the C2 server. However, on one of the infected machines, we found malware that we think is probably related to CosmicStrand. This malware creates a user named “aaaabbbb” in the operating system with local administrator rights.
We identified targets of CosmicStrand, which we attribute to an unknown Chinese-speaking threat actor, in China, Vietnam, Iran and Russia. All of them were ordinary people using our free antivirus solution, seemingly unconnected with any organization of interest to a sophisticated attacker of this kind. It also turned out that the motherboards infected in all known cases came from just two manufacturers. Therefore, it’s likely that the attackers found some common vulnerability in these motherboards that made UEFI infection possible.
It’s also unclear how the attackers managed to deliver the malware. It’s possible that the attackers are able to infect UEFI remotely. Or that those infected had purchased a modified motherboard from a reseller.
Andariel deploys DTrack and Maui ransomware
On 6 July, the US CISA (Cybersecurity and Infrastructure Security Agency) published an alert in which they accused North Korean state-sponsored threat actors of using the Maui ransomware to target the US healthcare sector. While CISA offered nothing to substantiate its attribution, we determined that approximately 10 hours prior to deploying Maui to the initial target system, the group deployed a variant of the well-known DTrack malware to the same target, preceded by deployment of the 3proxy tool months earlier. We believe that this helps to solidify the attribution to the Korean-speaking APT Andariel (aka Silent Chollima and Stonefly), with low-to-medium confidence.
Andariel’s primary tool is DTrack, used to collect information about the target, send it to a remote host and, in the case of the variant used in these attacks, store it on a remote host in the target network. When the attackers find noteworthy data, the Maui ransomware is deployed – it is typically detected on targeted hosts 10 hours after the activation of DTrack.
The attackers also use another tool, called 3Proxy, to maintain remote access to the compromised computer.
To infect target systems, the attackers exploit unpatched versions of public online services. In one such case, the malware was downloaded from an HFS (HTTP file server): the attackers used an unknown exploit that enabled them to run a PowerShell script from a remote server. In another, they were able to compromise a WebLogic server through an exploit for the CVE-2017-10271 vulnerability, which ultimately allowed them to run a script.
Our research revealed that, rather than just focusing on a particular industry, Andariel is ready to attack any company. We detected at least one attack on a housing company in Japan, as well as several targets in India, Vietnam and Russia.
VileRAT: DeathStalker’s continuous strike at foreign and crypto-currency exchanges
In late August 2020, we published an overview of DeathStalker and its activities, including the Janicab, Evilnum and PowerSing campaigns. Later that year, we documented the PowerPepper campaign. We believe DeathStalker to be a group of mercenaries, offering hack-for-hire services, or acting as an information broker to support competitive and financial intelligence efforts. Meanwhile, in August 2020, we also released a private report on VileRAT for our threat intelligence customers. VileRAT is a Python implant, part of an evasive and highly intricate attack campaign against foreign exchange and cryptocurrency trading companies. We discovered it in Q2 2020 as part of an update of Evilnum, and attributed it to DeathStalker.
Since we first identified it, DeathStalker has continuously updated and used its VileRAT tool-chain against the same type of targets.
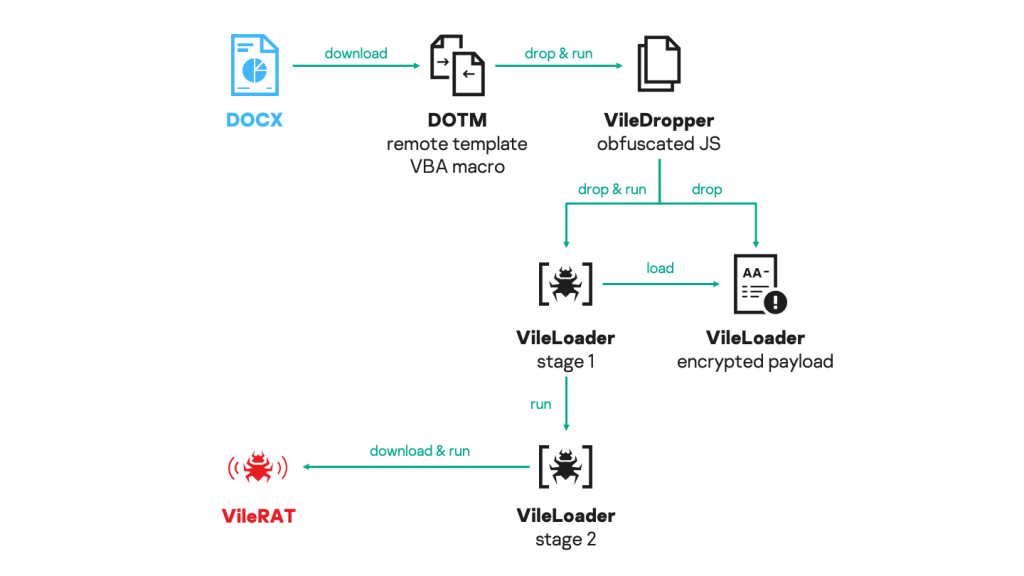
The threat actor has also sought to escape detection. However, the VileRAT campaign took this to another level: it is undoubtedly the most intricate, obfuscated and tentatively evasive campaign we have ever identified from DeathStalker. From state-of-the-art obfuscation with VBA and JavaScript, to multi-layered and low-level packing with Python, a robust multi-stage in-memory PE loader and security vendor-specific heuristic bypasses – the threat actor has left nothing to chance. On top of this, DeathStalker has developed a vast and quickly changing infrastructure as well.
On the other side, there are some glitches and inconsistencies. VileRAT, the final payload in the tool-chain is more than 10MB in size. The group uses simple infection vectors, many suspicious communication patterns, noisy and easy-to-identify process executions or file deployments, as well as sketchy development practices leaving bugs that require frequent implant updates. For these reasons, an effective endpoint solution will still be able to detect and block most VileRAT-related malicious activities.
Using only data that we could verify with our own telemetry, we identified 10 organizations compromised or targeted by DeathStalker since 2020 – in Bulgaria, Cyprus, Germany, the Grenadines, Kuwait, Malta, the UAE and the Russian Federation.
We do not know what DeathStalker’s principal intention is in targeting these organizations: this could range from due diligence, asset recovery, information gathering in the context of litigation or arbitration cases, aiding customers to bypass sanctions and/or spying on targets’ customers. However, it does not appear to be direct financial gain.
Kimsuky’s GoldDragon cluster and C2 operations
Kimsuky is a prolific and active threat actor primarily targeting North Korea-related entities. Like other sophisticated adversaries, this group updates its tools frequently. We recently had the chance to investigate how the threat actor configures its GoldDragon cluster and what kind of tricks it uses to confirm and further validate its victims. The Kimsuky group has configured multi-stage C2 servers with various commercial hosting services located around the world.
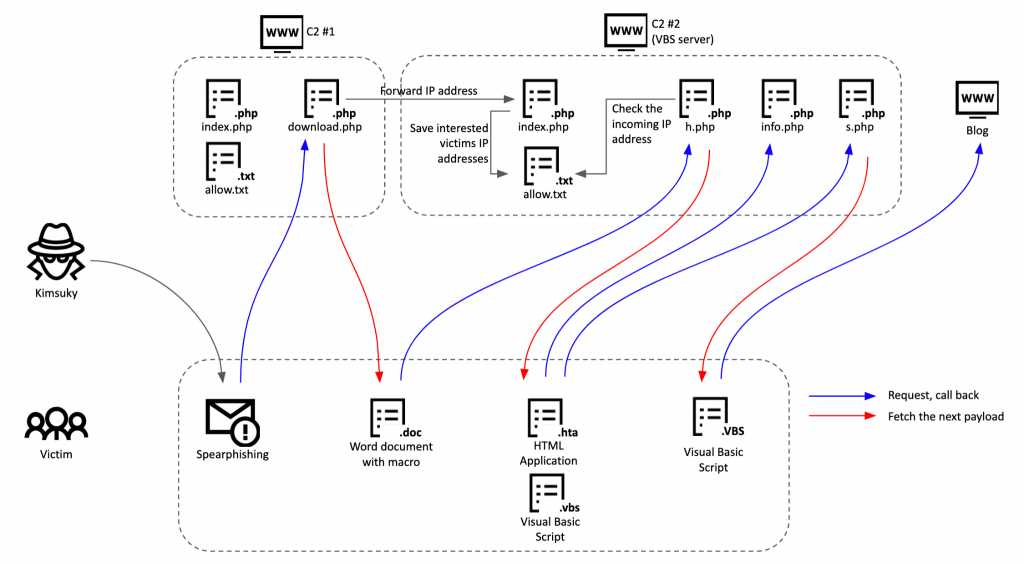
The attacks occur in several stages. First, the threat actor sends a spear-phishing email to the potential victim with a lure to download additional documents. If the victim clicks the link, it results in a connection to the first-stage C2 server, with an email address as a parameter. The first-stage C2 server verifies that the incoming email address parameter is expected and delivers the malicious document if it’s in the target list. The first-stage script also forwards the victim’s IP address to the next-stage server. When the fetched document is opened, it connects to the second C2 server. The corresponding script on the second C2 server checks the IP address forwarded from the first-stage server to verify that it’s an expected request from the same victim. Using this IP validation scheme, the actor verifies whether the incoming request is from the victim or not. On top of that, the operator relies on several other processes to carefully deliver the next payload. Another C2 script on the second C2 server checks the operating system type and predefined user-agent strings to filter out requests from security researchers or auto-analysis systems.
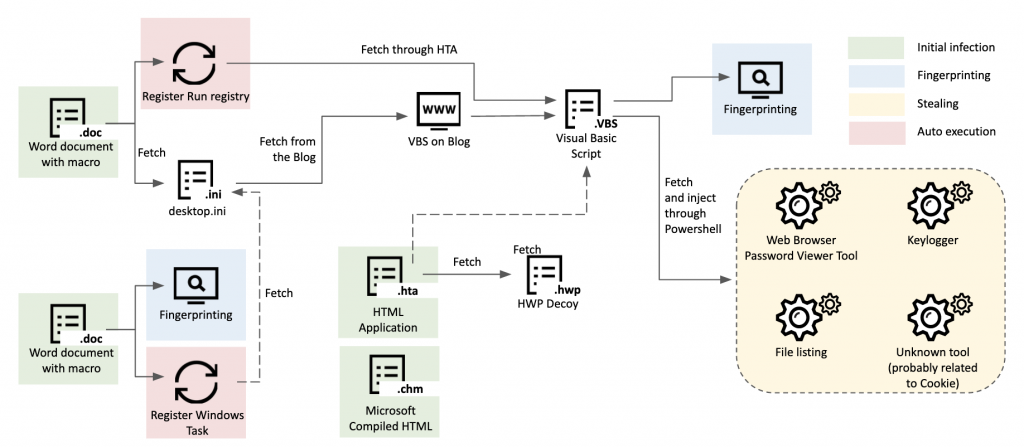
Based on the contents of the decoy document, we hypothesize that the targets of this operation are people or entities related to political or diplomatic activities. We know that historically politicians, diplomats, journalists, professors and North Korean defectors have been prime targets of the Kimsuky group. The email address names from the C2 scripts help to confirm this hypothesis.
Our research underlines how Kimsuky pays close attention to validating its victims and delivering the next-stage payloads to them, while taking steps to make analysis difficult.
Targeted attacks on industrial enterprises
In August, Kaspersky ICS CERT experts reported a wave of targeted attacks on military industrial complex enterprises and public institutions in Belarus, Russia, Ukraine and Afghanistan. The attacks, which took place earlier this year, affected industrial plants, design bureaus and research institutes, government agencies, ministries and departments. We identified more than a dozen targets, and observed significant overlaps in TTPs (Tactics, Techniques and Procedures) with the threat actor TA428.
The attackers gained access to the enterprise network using carefully crafted phishing emails. Some of the information they contained is not publicly available, indicating that the attackers conducted reconnaissance ahead of the attack, possibly using information obtained in earlier attacks on the target organization or others associated with the target. Microsoft Word documents attached to the phishing emails contained malicious code that exploits the CVE-2017-11882 vulnerability, which enables an attacker to execute arbitrary code – in this case, the main module of the PortDoor backdoor – without any additional user action.
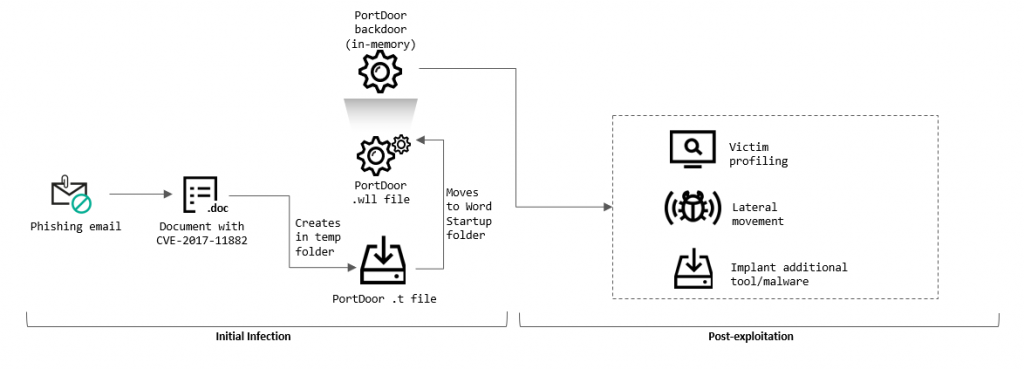
The attackers used five different backdoors at the same time – probably for redundancy. They provide extensive functionality for controlling infected systems and collecting confidential data. Once they have gained initial access, the attackers attempt to spread to other computers on the network. Once they have obtained domain administrator privileges, they search for, and exfiltrate, sensitive data to their servers hosted in different countries – these servers are also used as first-stage C2 servers. The attackers compress stolen files into encrypted and password-protected ZIP archives. After receiving the data, the first-stage C2 servers forward the archives to a second-stage server located in China.
Other malware
Prilex: the pricey prickle credit card complex
Prilex, active since 2014, is a well-known threat actor targeting ATMs and Point of Sale (PoS) terminals. In 2016, the group began to focus all its activities on PoS systems. Since then the group has greatly improved its malware: it develops complex threats and poses a major threat to the payment chain. Prilex is now conducting so-called “GHOST” attacks – fraudulent transactions using cryptograms, which are pre-generated by the victim’s card during the store payment process.
The group delivers its malware using social engineering. The cybercriminals call their chosen target and tell them their PoS software needs to be updated by a technician. Later, the fake technician goes to the targeted company in person and infects the machines. Alternatively, they persuade the target to install AnyDesk and use this to install the malware remotely.
Prior to striking victims, the cybercriminals perform an initial screening of the machine, in order to check the number of transactions that have already taken place and whether this target is worth attacking. If so, the malware captures any running transaction and modifies its content in order to be able to capture the card information. All the captured card details are then saved to an encrypted file, which is later sent to the attackers’ server, allowing them to make transactions through a fraudulent PoS device registered in the name of a fake company.
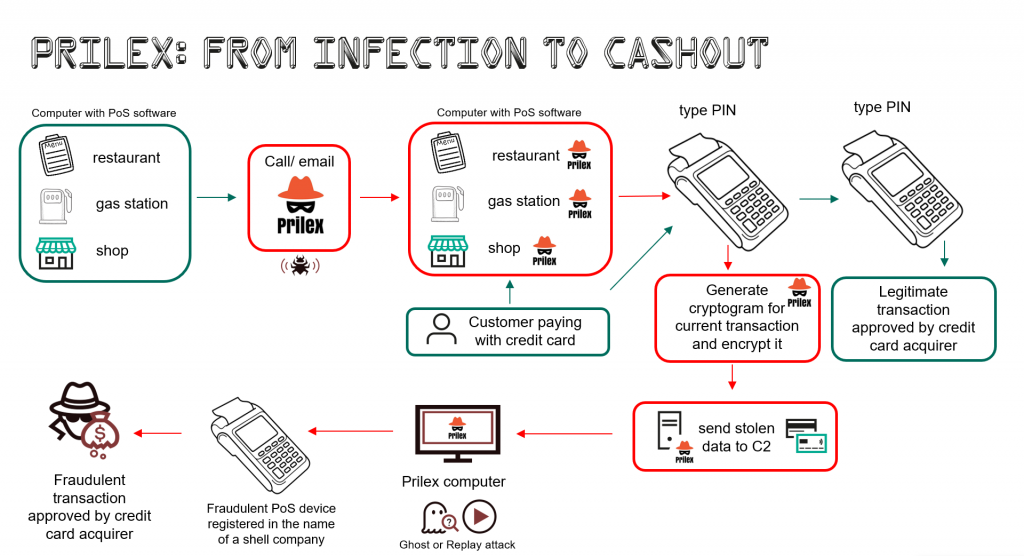
Having attacked one PoS system, the cybercriminals obtain data from dozens, or even hundreds, of cards daily. It is especially dangerous if the infected machines are located in popular shopping malls in densely populated cities, where the daily flow of customers can reach thousands of people.
In our recent investigation, we discovered that the Prilex group is controlling the development lifecycle of its malware using Subversion – used by professional development teams. Moreover, there is also a supposed official Prilex website selling its malware kits to other cybercriminals as Malware-as-a-Service (MaaS). Prilex has previously sold various versions of its malware on the dark web, for example, in 2019 a German bank lost more than €1.5 million in a similar attack by the Prilex malware. The development of its MasS operation means that highly sophisticated and dangerous PoS malware could spread to many countries, increasing the risk of multimillion-dollar losses for businesses all around the world.
We also discovered web sites and Telegram chats where cybercriminals sell Prilex malware. Posing as the Prilex group itself, they offer the latest versions of PoS malware, costing from $3,500 to $13,000. We are not sure about the real ownership of these web sites, as they could be copycats.
Luna and Black Basta: new ransomware for Windows, Linux and ESXi
Ransomware groups have increasingly targeted not only Windows computers, but also Linux devices and ESXi virtual machines. We highlighted one example earlier this year – the BlackCat gang, which distributes malware written in the cross-platform language Rust. We recently analyzed two other malware families that provide similar functionality: Black Basta and Luna.
Black Basta, first discovered in February, exists in versions for Windows and for Linux – the latter primarily targeting ESXi virtual machine images. One of the key features of the Windows version is that it boots the system in Safe Mode before encrypting data: this allows the malware to evade detection by security solutions, many of which don’t work in Safe Mode.
At the time we published our report, Black Basta operators had released information on 40 victims, among them manufacturing and electronics firms, contractors, and others, located in the US, Australia, Europe, Asia and Latin America.
Luna, discovered in June and also written in Rust, is able to encrypt both Windows and Linux devices, as well as ESXi virtual machine images. In an advert on the dark web, the cybercriminals claim to co-operate only with Russian-speaking partners. This means that the targets of interest to the attackers are most likely located outside the former Soviet Union. This is also borne out by the fact that the ransom note embedded into the code of the ransomware is written in English, albeit with mistakes.
Malicious packages in online code repositories
In July, we reported a malicious campaign that we named LofyLife. Using our internal automated system for monitoring open-source repositories, our researchers identified four malicious packages spreading Volt Stealer and Lofy Stealer malware in the npm repository.
The identified malicious packages appeared to be used for ordinary tasks such as formatting headlines or certain gaming functions. The “formatting headlines” package was in Brazilian Portuguese with a “#brazil” hashtag, suggesting that the attackers were seeking to target people based in Brazil. Other packages were presented in English, so they could be targeting users from other countries.
The packages contained highly obfuscated malicious JavaScript and Python code. This made them harder to analyze when being uploaded to the repository. The malicious payload consisted of malware written in Python dubbed Volt Stealer – an open-source malicious script – and JavaScript malware dubbed Lofy Stealer. Volt Stealer was used to steal Discord tokens from infected machines, along with the victim’s IP address, and upload them via HTTP. Lofy Stealer infects Discord client files and monitors the victim’s actions, detecting when a person logs in, changes the registered email or password, enables or disables multi-factor authentication and adds new payment methods (in which case the malware steals full credit card details). It uploads collected information to a remote endpoint.
The npm repository is an open-source home for JavaScript developers to share and reuse code for building various web applications. As such, it represents a significant supply chain that, if exploited by attackers, can be used to deliver malware to many people. This is not the first time we’ve seen an npm package poisoned in this way.
npm is not the only such code repository to have been targeted recently. In August, Check Point published a report on 10 malicious Python packages in the Python Package Index (PyPI), the most popular Python repository among software developers. The malicious packages were intended to steal developers’ personal data and credentials. Following this research, we discovered two other malicious Python packages in the PyPI, masquerading as one of the most popular open-source packages named “requests“.
The attacker used a description of the legitimate “requests” package in order to trick victims into installing a malicious one. In addition, the description contained fake statistics and the project description referenced the web pages of the original “requests” package, as well as the author’s email. All mentions of the legitimate package’s name were replaced with the name of the malicious one.
Cyberthreats facing gamers
The gaming industry is huge and growing. The industry attracts an audience of more than 3 billion people worldwide – a huge pool of potential victims for cybercriminals who target this sector. Cybercriminals make extensive use of social engineering tricks to entice potential victims into installing malware: the promise of an Android version of a game that’s not on Google Play; the chance to play games for free; access to game cheats; etc.
We recently published our report on gaming-related threats in 2021–22. Here are some of the key headlines:
- In the year up to June 2022, Kaspersky blocked gaming-related malware and unwanted software on the computers of 384,224 people, with 91,984 files distributed under the guise of 28 games.
- The top five PC games used as bait in these attacks were Minecraft, Roblox, Need for Speed, Grand Theft Auto and Call of Duty.
- The top five mobile games used as a lure to target gamers were Minecraft, Roblox, Grand Theft Auto, PUBG and FIFA.
- Malware and unwanted software distributed as cheat programs stand out as a particular threat to gamers’ security. In the year to June 2022, we detected 3,154 unique files of this type, affecting 13,689 people.
- Miners pose an increasing threat, with Far Cry, Roblox, Minecraft, Valorant and FIFA heading the list of games and game series that cybercriminals used as a lure for such threats.
Among the top threats is RedLine, which we deemed worthy of a separate report. The attackers distribute this password-stealing Trojan under the guise of game cheats in an attempt to steal accounts, card numbers, crypto-wallets and more. They post videos on YouTube purportedly about how to use cheats in popular online games such as Rust, FIFA 22, DayZ and others. The videos prompt the victim to follow a link in the description to download and run a self-extracting archive.
The Trojan, once installed, steals account passwords, credit card details, session cookies and more. RedLine is also able to execute commands on the computer, as well as download and install other programs onto the infected machine.
RedLine also comes with a cryptocurrency miner. Gaming computers are a logical target for cybercriminals, since they typically have powerful GPUs – useful for cryptocurrency mining.
In addition to losing sensitive data, the player’s reputation is at stake. RedLine downloads videos from the C2 server and posts them on the victim’s YouTube channel – the same video that led the gamer to become infected. In this way, they become the means by which other gamers become infected.
NullMixer: oodles of Trojans in a single dropper
Trying to save money by using unlicensed software can be costly: a single file downloaded from an unreliable source can result in system compromise. In September, we published our analysis of NullMixer, a Trojan dropper designed to drop a wide variety of malware families.
NullMixer spreads via malicious web sites that can be accessed using standard search engines. Often, the web sites host “cracks”, “keygens” and activators for downloading software illegally: they pretend to be legitimate, but actually contain a malware dropper. They stay at the top of search engine results using SEO.
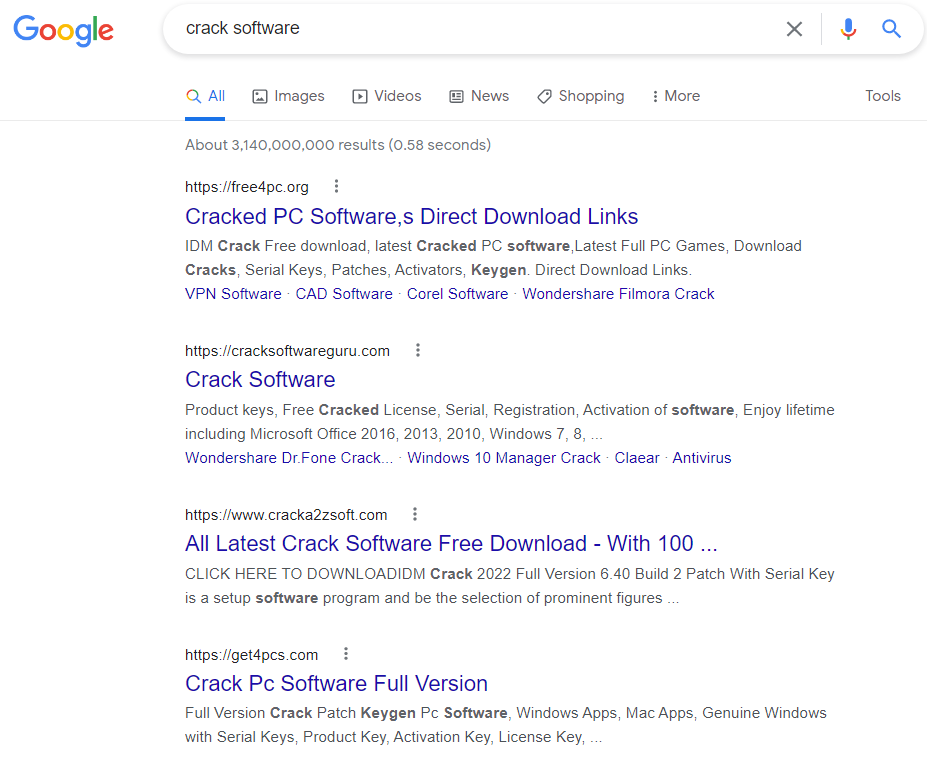
When someone attempts to download software from one of these sites, they are redirected multiple times, ending up on a page containing download instructions and archived password-protected malware masquerading as the desired piece of software. When they extract and execute the file, the malware drops a number of malicious files to the compromised machine. The malware families dropped onto the computer include SmokeLoader/Smoke, LgoogLoader, Disbuk, RedLine (described above), Fabookie and ColdStealer, consisting of backdoors, spyware, bankers, credential stealers, droppers and more.
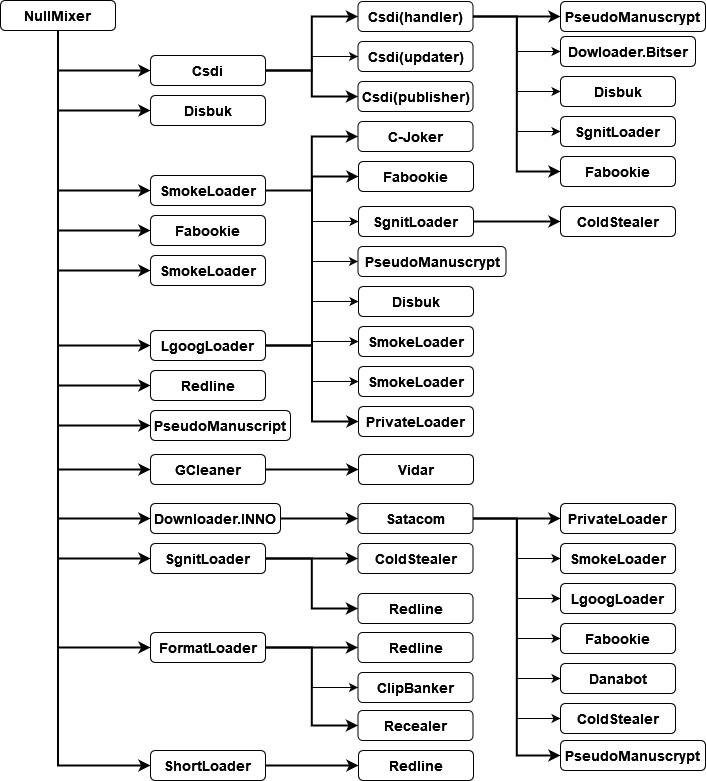
Once all the dropped files have been launched, the NullMixer starter beacons to the C2 to confirm the successful installation. The dropped files are then left to their own devices.
Since the beginning of the year, we have blocked attempts to infect more than 47,778 people worldwide. Some of the most targeted countries are Brazil, India, Russia, Italy, Germany, France, Egypt, Turkey and the US.
Many of the malware families dropped by NullMixer are downloaders, which suggests that infections will not be limited to the malware families described in our report. Many of the other malware families mentioned here are stealers, and compromised credentials can be used for further attacks inside a local network.
Potential threat in the browser
Browser extensions are very useful for blocking ads, keeping a to-do list, spellchecking, translating text and much more. They are also popular: Chrome, Safari, Mozilla and other browsers have their own online stores distributing thousands of extensions – and the most popular plug-ins there reach over 10 million people. However, extensions are not always secure; and even seemingly innocent add-ons can present a real risk.
Malicious and unwanted add-ons promote themselves as useful, and often do have legitimate functions implemented along with malicious ones. Some impersonate popular legitimate extensions. Often, such add-ons are distributed through official marketplaces. In 2020, Google removed 106 browser extensions from its Chrome Web Store – all siphoned off sensitive user data, such as cookies and passwords, and even took screenshots. These extensions had been downloaded 32 million times.
It’s always good to check the permissions an extension requests during installation. And if it’s asking for permission to do things that don’t seem appropriate, don’t install it. For example, a browser calculator that asks for access to geolocation or browsing history. However, it’s not always so clear. Often the wording is so vague that it is impossible to tell exactly how secure an extension is. Basic extensions often require permission to “read and change all your data on the websites you visit”. They may really need it in order to function properly, but this permission gives the extension wide powers.
Even if not malicious, they can still be dangerous. Many collect massive amounts of data from web pages people visit. To earn more money, some developers may pass it on to third parties or sell it to advertisers. If that data is not anonymized properly, information about web sites that people visit and what they do there could be exposed to third parties.
Extension developers are also able to push updates without requiring any action by the person who installed it. Even a legitimate extension could be later hijacked to install malware.
We recently published an overview of the types of threat that mimic useful web-browser extensions and statistics on attacks, using data from the Kaspersky Security Network (KSN), for the period between January 2020 and June 2022.
In the first half of this year, 1,311,557 people tried to download malicious or unwanted extensions at least once, which is more than 70 percent affected by the same threat in the whole of last year.
From January 2020 to June 2022, adware hiding in browser extensions affected more than 4.3 million people, which is approximately 70 percent of all people affected by malicious and unwanted add-ons.
The most common threat in the first half of 2022 was the WebSearch family of adware extensions, able to collect and analyze search queries and redirect people to affiliate links.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![Cobalt Strike Beacon Detected - 8[.]219[.]161[.]236:48899 11 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
