It’s baaaack: Public cyber enemy Emotet has returned
It was never a question of “if” but “when”. After five months of absence, the dreaded Emotet has returned. Following several false alarms over the last few weeks, a spam campaign was first spotted on July 13 showing signs of a likely comeback.
The Emotet botnets started pushing malspam actively on Friday, July 17, using the same techniques as it employed previously. Malicious emails contain either a URL or an attachment. One familiar technique is for the document to be sent as a reply within existing email threads.
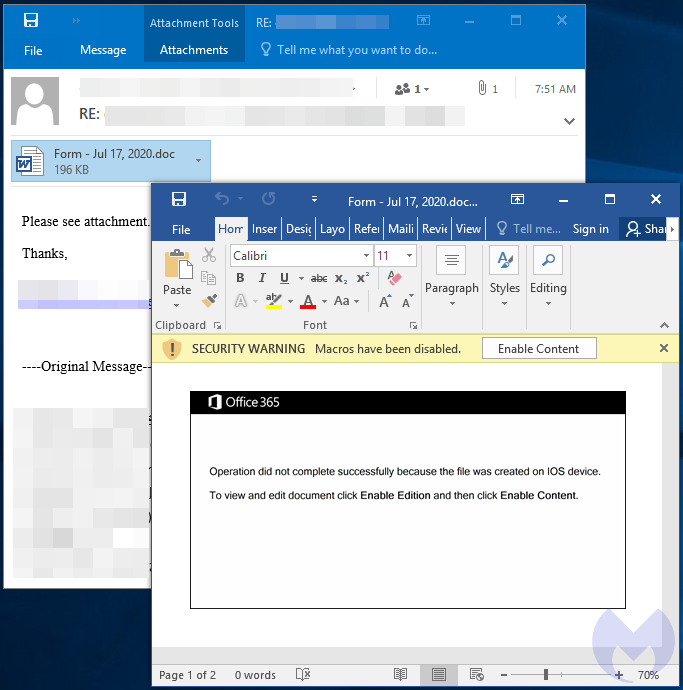
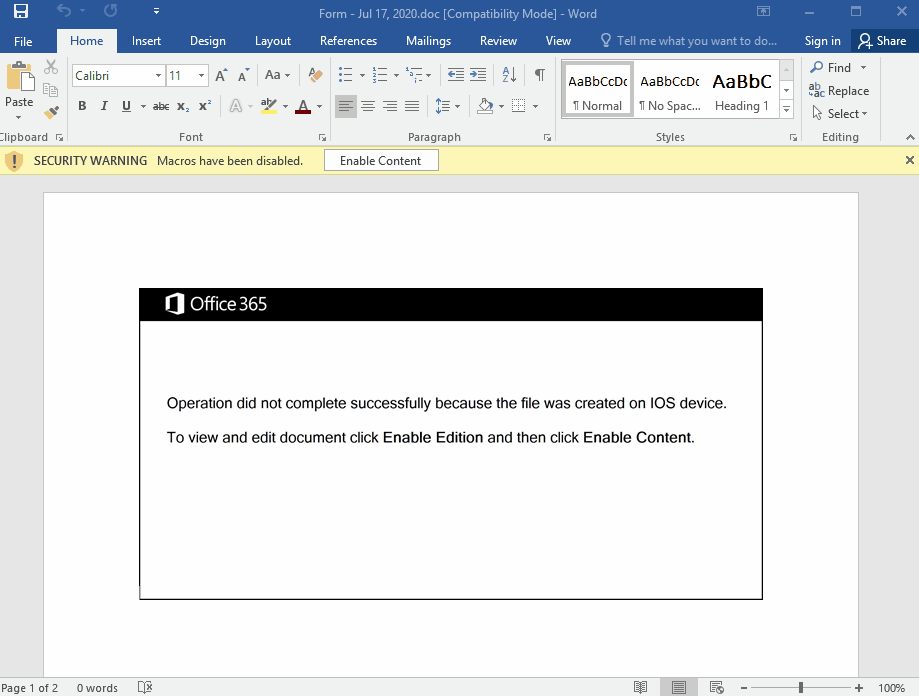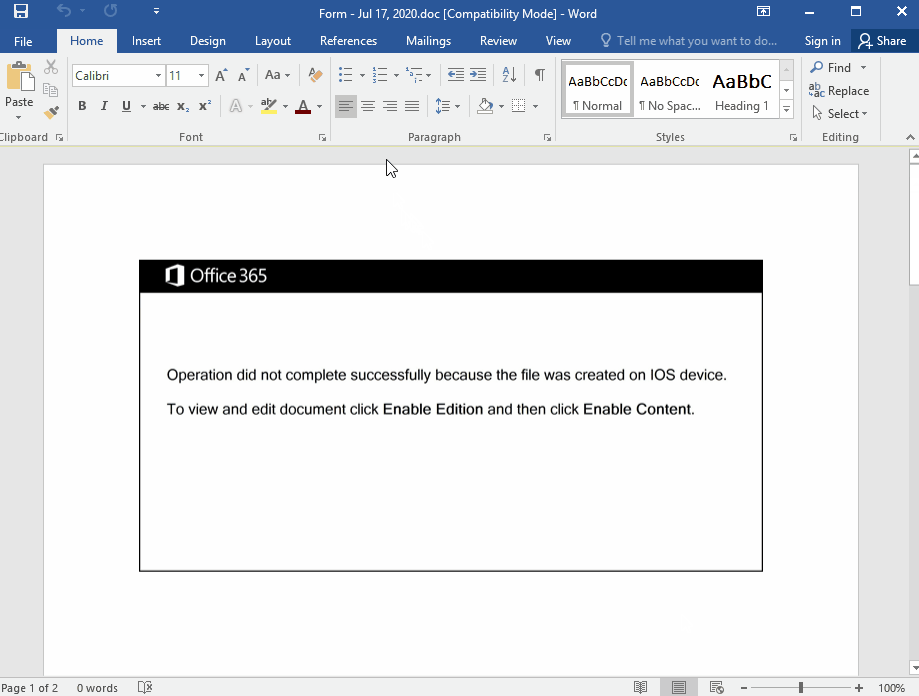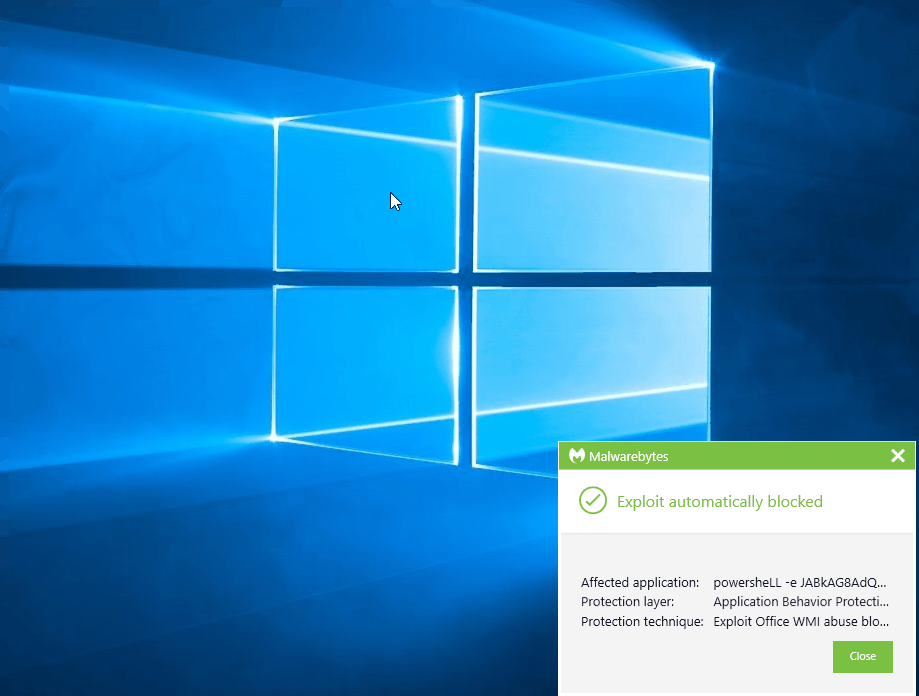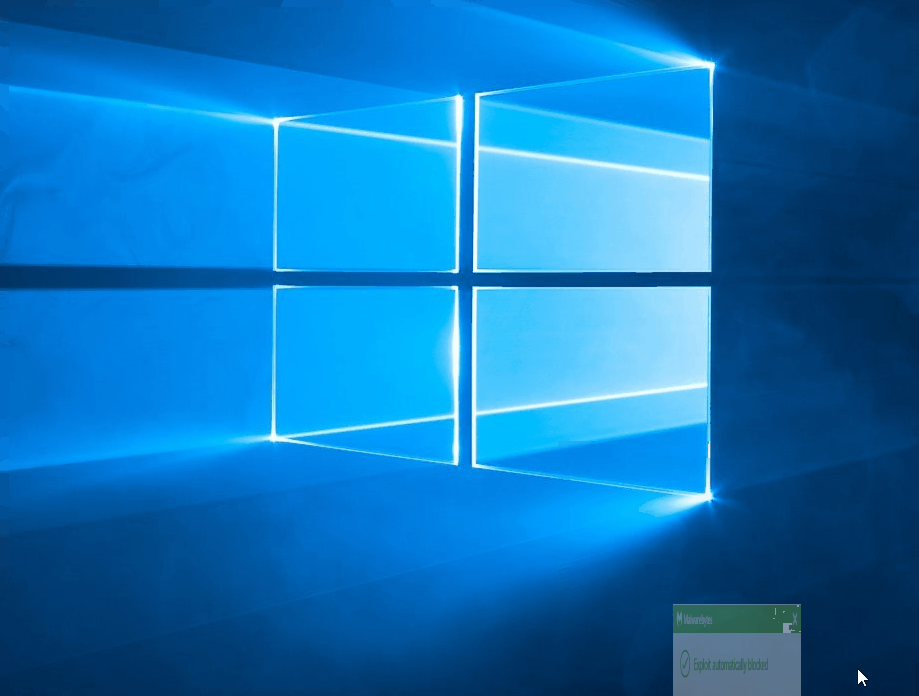
The document contains a heavily obfuscated macro:
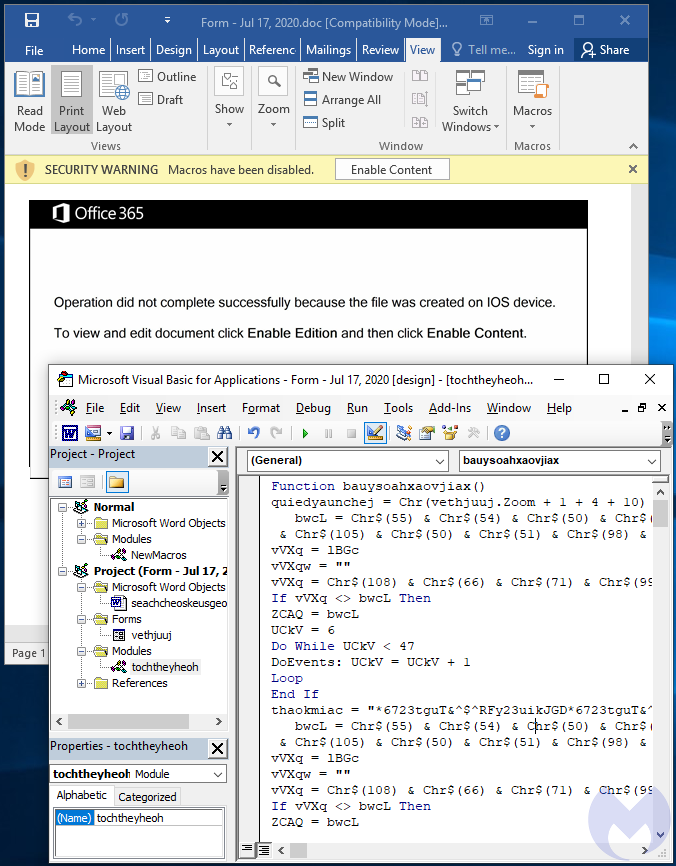
Once the macro is enabled, WMI launches PowerShell to retrieve the Emotet binary from one of the remote compromised websites. It will iterate through a list until it identifies one that is responding.
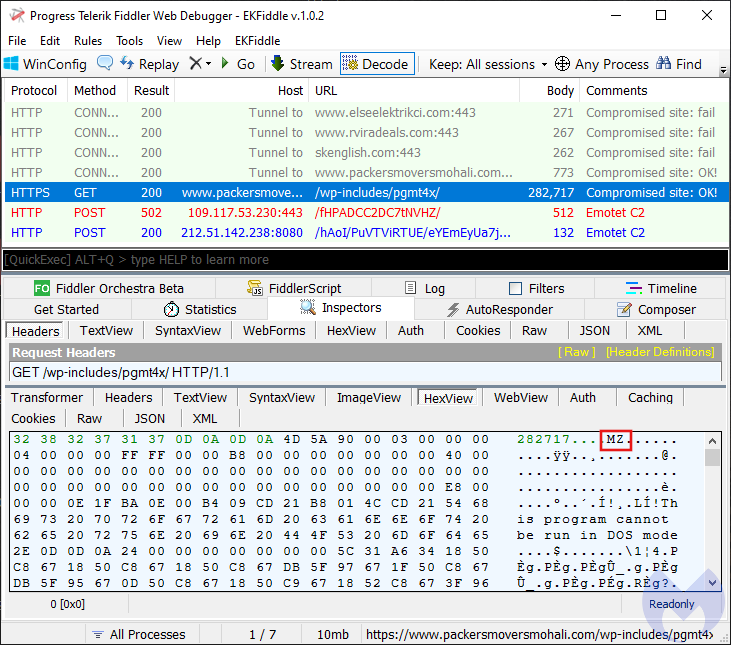
Once the payload is executed, it will send a confirmation back to one of Emotet’s command and control server.
Emotet has returned to its old tricks
The Emotet Trojan was by far the most visible and active threat on our radars in 2018 and 2019—right up until it went into an extended break.
Emotet is used by cybercriminals as the initial entry point, followed by a dwell time that can last days or weeks. In the meantime, other threats such as TrickBot can be delivered as a secondary payload.
The real damage that an Emotet compromise causes happens when it forms alliances with other malware gangs and in particular threat actors interested in dropping ransomware.
Malwarebytes users were already protected against Emotet thanks to our signature-less anti-exploit technology.
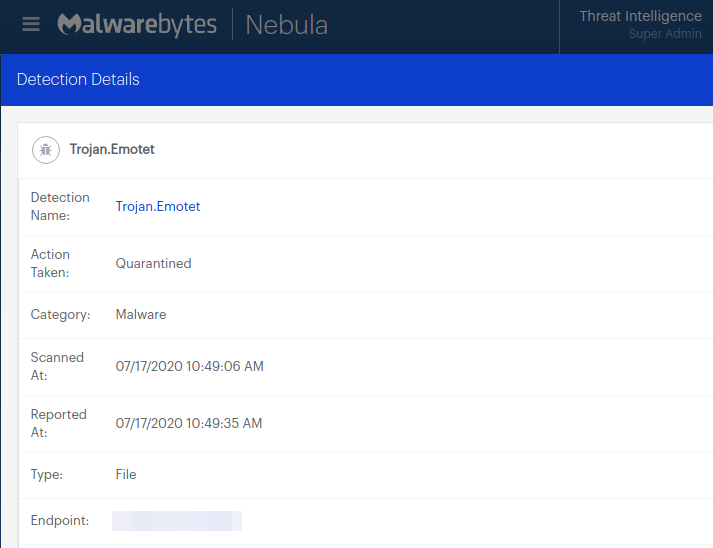
We also detect the Emotet binary as a standalone file:
Indicators of Compromise
Malicious documents
5d2c6110f2ea87a6b7fe9256affbac0eebdeee18081d59e05df4b4a17417492b
4fdff0ebd50d37a32eb5c3a1b2009cb9764e679d8ee95ca7551815b7e8406206
bb5602ea74258ccad36d28f6a5315d07fbeb442a02d0c91b39ca6ba0a0fe71a2
6d86e68c160b25d25765a4f1a2f8f1f032b2d5cb0d1f39d1d504eeaa69492de0
18fab1420a6a968e88909793b3d87af2e8e1e968bf7279d981276a2aa8aa678e
d5213404d4cc40494af138f8051b01ec3f1856b72de3e24f75aca8c024783e89
Compromised sites
elseelektrikci[.]com
rviradeals[.]com
skenglish[.]com
packersmoversmohali[.]com
tri-comma[.]com
ramukakaonline[.]com
shubhinfoways[.]com
test2.cxyw[.]net
sustainableandorganicgarments[.]com
staging.icuskin[.]com
fivestarcleanerstx[.]com
bhandaraexpress[.]com
crm.shaayanpharma[.]com
zazabajouk[.]com
e2e-solution[.]com
topgameus[.]com
cpads[.]net
tyres2c[.]com
thesuperservice[.]com
ssuse[.]com
Emotet binaries
454d3f0170a0aa750253d4bf697f9fa21b8d93c8ca6625c935b30e4b18835374
d51073eef56acf21e741c827b161c3925d9b45f701a9598ced41893c723ace23
1368a26328c15b6d204aef2b7d493738c83fced23f6b49fd8575944b94bcfbf4
7814f49b3d58b0633ea0a2cb44def98673aad07bd99744ec415534606a9ef314
f04388ca778ec86e83bf41aa6bfa1b163f42e916d0fbab7e50eaadc8b47caa50
C2s
178.210.171[.]15
109.117.53[.]230
212.51.142[.]238
190.160.53[.]126
The post It’s baaaack: Public cyber enemy Emotet has returned appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


