Keep Zoombombing cybercriminals from dropping a load on your meetings
While shelter in place has left many companies struggling to stay in business during the COVID-19 epidemic, one company in particular has seen its fortunes rise dramatically. Zoom, the US-based maker of teleconferencing software, has become the web conference tool of choice for employees working from home (WFH), friends coming together for virtual happy hour, and families trying to stay connected. Since March 15, Zoom has occupied the top spot on Apple’s App Store. Only one week prior, Zoom was the 103rd-most popular app.
Even late-night talk show hosts have jumped on the Zoom bandwagon, with Samantha Bee, Stephen Colbert, Jimmy Fallon, and Jimmy Kimmel using a combination of Zoom and cellphone video to produce their respective shows from home.
In an incredibly zeitgeisty moment, everyone and their parents are Zooming. Unfortunately, opportunistic cybercriminals, hackers, and Internet trolls are Zooming, too.
What is Zoombombing?
Since the call for widespread sheltering in place, a number of security exploits have been discovered within the Zoom technology. Most notably, a technique called Zoombombing has risen in popularity, whether for pure mischief or more criminal purpose.
Zoombombing, also known as Zoom squatting, occurs when an unauthorized user joins a Zoom conference, either by guessing the Zoom meeting ID number, reusing a Zoom meeting ID from a previous meeting, or using a Zoom ID received from someone else. In the latter case, the Zoom meeting ID may have been shared with the Zoombomber by someone who was actually invited to the meeting or circulated among Zoombombers online.
The relative ease by which Zoombombing can happen has led to a number of embarrassing and offensive episodes.
In one incident, a pornographic video appeared during a Zoom meeting hosted by a Kentucky college. During online instruction at a high school in San Diego, a racist word was typed into the classroom chat window while another bomber held up a sign that said the teacher “Hates Black People.” And in another incident, a Zoombomber drew male genitalia on screen while a doctoral candidate defended his dissertation.
Serious Zoombombing shenanigans
The Zoombombing problem has gotten so bad that the US Federal Bureau of Investigations has issued a warning.
That said, it’s the Zoombombs that no one notices that are most worrying, especially for Zoom’s business customers. Zoombombers can discreetly enter a Zoom conference and capture screenshots of confidential screenshares and record video and audio from the meeting. While it’s not likely for a Zoom participant to put up a slide with their username and password, the information gleaned from a Zoom meeting can be used in a phishing or spear phishing attack.
As of right now, there hasn’t been a publicly disclosed data breach as a result of a Zoombomb, but the notion isn’t far-fetched.
Numerous organizations and educational institutions have announced they will no longer be using Zoom. Of note, Google has banned the use of Zoom on company-owned devices in favor of their own Google Hangouts. The New York City Department of Education announced they’d no longer be using Zoom for remote learning. And Elon Musk’s SpaceX has banned Zoom, noting “significant privacy and security concerns” in a company-wide memo.
“Most Zoombombing incidents can be prevented with a little due diligence on the part of the user,” Malwarebytes Head of Security John Donovan said. “Anyone using Zoom, or any web conference software for that matter, is strongly encouraged to review their conference settings and minimize the permissions allowed for their conference attendees.”
“You can’t walk into a high school history class and start heckling the teacher. Unfortunately, the software lets people do that if you’re not careful,” he added.
For their part, Zoom has published multiple blog posts acknowledging the security issues with their software, changes the company has made to shore up security, and tips for keeping conferences private.
Keep your Zoom meetings secure
Here are our tips for keeping your Zoom meetings secure and free from Zoombombers. Keep in mind that many of these tips apply to other teleconferencing tools as well.
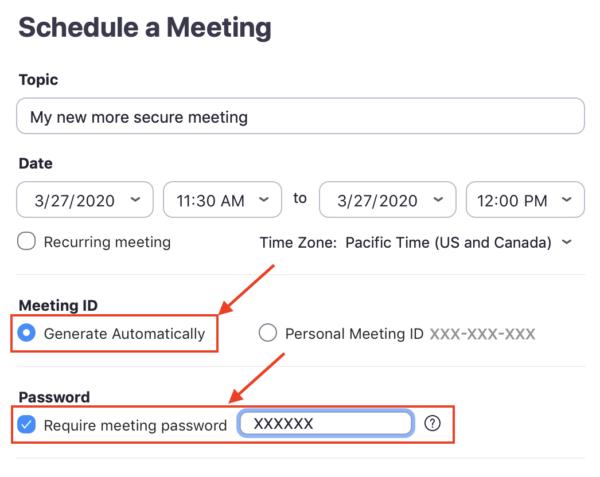
- Generate a unique meeting ID. Using your personal ID for meetings is like having an open-door policy—anyone can pop in at any time. Granted, it’s convenient and easy to remember. However, if a Zoombomber successfully guesses your personal ID, they can drop in on your meetings whenever they want or even share your meeting ID with others.
- Set a password for each meeting. Even if you have a unique meeting ID, an invited participant can still share your meeting ID with someone outside your organization. Adding a password to your meeting is one more layer of security you can add to keep interlopers out.
- Allow signed-in users only. With this option, it won’t matter if Zoombombers have the meeting ID—even the password. This setting requires everyone to be signed in to Zoom using the email they were invited through.
- Use the waiting room. With the waiting room, the meeting doesn’t start until the host arrives and adds everyone to the meeting. Attendees in the waiting room can’t communicate with each other while they’re in the waiting room. This gives you one additional layer of manual verification, before anyone can join your meeting.
- Enable the chime when users join or leave the meeting. Besides giving you a reason to embarrass late arrivals, the chime ensures no one can join your meeting undetected. The chime is usually on by default, so you may want to check to make sure you haven’t turned it off in your settings.
- Lock the room once the meeting has begun. Once all expected attendees have joined, lock the meeting. It seems simple, but it’s another easy way to keep Zoombombing at bay.
- Limit screen sharing. Before the meeting starts, you can restrict who can share their screen to just the host. And during the meeting, you can change this setting on the fly, in case a participant ends up needing to show something.
A special note for IT administrators: As a matter of company policy, many of these Zoom settings can be set to default. You can even further lock down settings for a particular group of users with access to sensitive information (or those with a higher learning curve on cybersecurity hygiene). For more detailed information, see the Zoom Help Center.
Remember, Zoombombing isn’t just embarrassing—it’s a big security risk. Sure, the Zoombombing incidents making headlines at the moment seem to be about trolling people more than anything else, but the potential for more serious abuse exists.
No matter which web conferencing software you use, take a moment to learn its settings and make smart choices about the data you share in your meetings. Do this, and you’ll have a safe and happy socially-distanced gathering each time you sign on.
The post Keep Zoombombing cybercriminals from dropping a load on your meetings appeared first on Malwarebytes Labs.

