KITT-Lite – Python-Based Pentesting CLI Tool
The KITT Penetration Testing Framework was developed as an open source solution for pentesters and programmers alike to compile the tools they use with what they know into an open source project. With KITT, users are able to easily access a list of commonly used tools to their profession which are all open to configuration in the source code.
UPDATE: Now Supporting Kali 2020.2!
If you want to check out the full GUI version of KITT its repo can be found here
Features
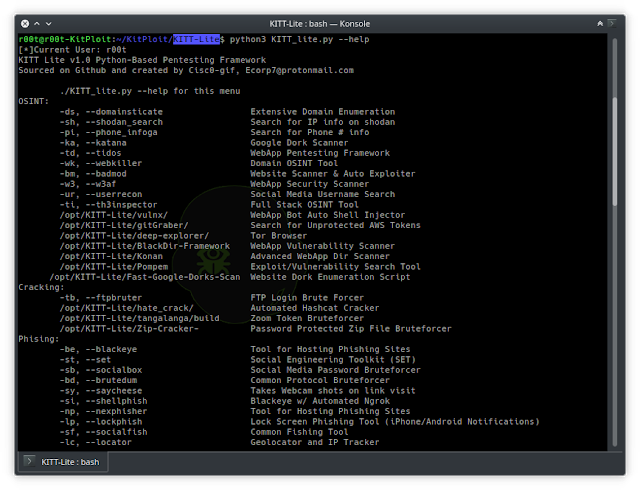
OSINT
- Domainsticate – Custom domain enumeration tool
- Shodan Search – Quick Shodan search tool
- PhoneInfoga – OSINT tool for phone numbers
- gitGraber – Unprotected Token search tool for GitHub
- gitHound – Sensitive Data Fuzzer for GitHub
- GitRob – Sensitive File Fuzzer for GitHub
- Katana – Google Dork Scanner
- TIDoS-Framework – WebApp Recon and Vulnerability Analysis Framework
- Domained – Subdomain Enumeration Tool
- Vulnx – WebApp Bot Auto Shell Injector
- Webkiller – Domain OSINT Tool
- BadMod – Website Scanner & Auto Exploiter
- Deep-Explorer – .Onion link browser
- W3af – Website Security Scanner
- UserRecon – Social Media Username Search Tool
- Th3inspector – Full Stack OSINT Tool
- BlackDir-Framework – WebApp Vulnerability Scanner
- Skiptracer – OSINT Scraping Framework COMING SOON
- Konan – Advanced WebApp Dir Scanner
- Fast-Google-Dork-Scan – Website Dork Enumeration Script
- Pompem – Exploit/Vulnerability Search Tool
Cracking
- Hate_Crack – Automated Hashcat Cracker
- FTPBruter – FTP Login Brute Forcer
- Tangalanga – Zoom Token Brute Forcer
- Zip-Crakcer – Password Protected Zip File Bruteforcer
Phishing
- Blackeye – Webpage Phishing Tool
- SET – Social Engineers Toolkit
- SocialBox – Social Media Password Bruteforcer
- Seeker – Social Engineering IP GeoLocator (Give/Take 30m)
- BruteDum – Common Protocol Bruteforcer
- SayCheese – Takes Webcam pic on site visit
- Shellphish – Blackeye w/ Automated Ngrok
- Nexphisher – Webpage Phishing Tool
- Lockphish – Lock Screen Phishing Tool
- SocialFish – Common Phishing Tool
- Locator – Geolocator and IP Tracker
- EvilApp – MiTM Phishing Attack Using APK
- Droidfiles – Downloads Files from Android Dirs from .apk payload
- Cuteit – IP Obfuscator
- TrevorC2 – Cmd Injection Masked Phishing Site
Payloads
- Evil-Droid – Android APK Payloading & Embedding Framework
- Catchyou – Undetectable Win32 Payload Generator
- Winspy – Windows Reverse Shell Generator w/ IP Poisoning
- Evilreg – Windows .reg Reverse Shell Generator
- Badlnk – Shortcut (.lnk) Reverse Shell Generator
- Enigma – Multiplatform Payload Dropper
- Avet_Fabric – Windows AV Evasive Payloads
- Eviloffice – Injects Macro & DDE Code into Excel & Word Documents
- Evilpdf – Embeds .exe Files into PDF Files
- EvilDLL – DLL Reverse Shell Generator
- DroidTracker – Android .APK Locaton Tracker
- hmmcookies – Grabs Firefox, Chrome, and Opera Cookies
Keyloggers
- HeraKeylogger – Chrome Keylogger Extension
- KatroLogger – Keylogger for Unix/Linux Systems
Privilege Escalation/Exploitation
- BIOS_UBTU_Rooter.sh – Custom Ubuntu usb boot exploit
- LinEnum – Linux shell enumeration tool
- Linux – Linux Exploits and Enumeration Scripts
- Mimikatz_trunk – Windows post exploitation tool
- mysql – MSQL exploits and enumeration scripts
- passwd_backdoor.sh – Custom passwd/ backdoor exploit for post-exploitation
- pspy – Process scanner for linux
- windows-privesc-check – Windows PrivEsc Scripts
- Windows-Privlege-Escalation – Windows PrivEsc Scripts
- Chromepass – AV-Undetectable Chrome Login Extraction Tool (Local exec)
- htbenum – Offline Local Enum Server (Mainly for HTB)
- PeekABoo – Enables RDP Service (Only on WinRM Machines – Enabled by default on WinServer machines but not client machines)
- firefox_decrypt – Mozilla Browser Saved Login Extractor
- Powershell-reverse-tcp – Reverse TCP Powershell Payload w/ Obfuscation
- Invoker – Post Windows Non-GUI Shell Utility
- HiveJack – Windows SAM Dump Tool
- Impacket – Python Network Protocol Tools
- Win-Brute-Logon – Post Tool For Cracking User Passwords (XP -> 10)
- Covermyass – Covers Your Tracks on UNIX Systems
- Leviathan – System Audit Toolkit
- ispy – EternalBlue/Bluekeep Scanner/Exploiter
- NekoBotV1 – Auto Exploiter Tool
- Gtfo – Unix Binary Search Tool
- Grok-backdoor – Python-Based Backdoor with Ngrok Tunneling
- Mimikatz – Windows password, hash, PIN, and kerberos ticket extraction tool
Ransomeware
- Hidden-cry – Windows AES 256 Bit Encrypter/Decrypter
- CryDroid – Android Encrypter/Decrypter
Bots
- Idisagree – Trojan Discord Bot
- UFOnet – DDoS Third Party Vector Tool
Network Cracking
- Airsuite-ng – Software suite w/ detector, packet sniffer, WEP and WPA/WPA2-PSK Cracker and analysis tool
- Wash & Reaver – WPS Cracking tools
- Wifite2 – Network Auditing Tool
- Ettercap – MiTM Attack Suite
- Airgeddon – Network Auditing Tool
- WiFipumpkin3 – Network Cracking Framework
- Wifijammer – Stationary or Mobile WiFi Jammer
- PwnSTAR – Fake AP Tool Framework
- HT-WPS – WPS Pin Extractor
- Linset – WPA/WPA2 MiTM Attack Tool
- PentBox – HoneyPot Setup Tool
- Espionage – Packet Sniffer/ARP Spoofer
- EvilNet – ARP Attacks, VLAN Attacks, MAC Flooding, etc.
IoT Exploitation
- HomePwn – IoT Exploitation Framework
- Spooftooph – BT Spoofing
- BtVerifier – Rfcomm Channel Verifier
- BlueScan – BT Port/MAC Scanner
Hardware Hacking
- MouseJack – BT Keyboard and Mouse Hijacker
- GPIO_CTL – Custom GPIO Controller for RPi
- Brutal – RubberDucky Payload Generator
System Security
- SysIntegrity – File MD5sum Integrity Analyzer
- snort – Network Intrusion Detection System
- ssh_port_randomizer – SSHD Port Randomizer
- ssh rsa_key generator – RSA Key generator
- proxy router – Traffic Proxy Router
- ssh_encryption – Buffing SSHD Security Protocols
- Fail2ban Configurations – Fail2ban Protocol Auditer
- PTF – PenTesting Tool Installation Framework
- ClamAV – CLI Virus/Malware Scanner
- Wotop – Tunnels Internet Traffic Over HTTP
- TorghostNG – Directs All Internet Traffic Through Tor Proxy
Getting Started
WARNING: KITT was developed and tested on Kali Linux for RPi, I have not added support for any other distro yet but plan to in the near future.
WARNING: Installation Takes About 20 Minutes To Finish!
To begin, run sudo ./setup.sh to install all necessary libraries and configure PATH usage. Simply follow all instructions in the installer.
If you want to only install the tools, run sudo ./catchup.sh
Usage
To begin the framework, type KITTlite and execute in terminal.
Legal Disclaimer
Usage of KITT-Lite and/or the tools installed with KITT-Lite for attacking targets without prior mutual consent is illegal. It’s the end user’s responsibility to obey all applicable local, state, and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
Built With
- RPi 3B+ – Micro-Computer Developed by the Raspberry Pi Foundation
- Kali Linux – Pentesting OS Developed by Offensive Security
- GitHub – This Website!
Authors
- Cisc0-gif – Main Contributor/Author
- Email: [email protected]
- Discord: Fergo310#5226
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


