LockBit ransomware claims attack on Port of Lisbon in Portugal

An cyberattack hitting the Port of Lisbon Administration (APL), the third-largest port in Portugal, on Christmas day has been claimed by the LockBit ransomware gang.
The Port of Lisbon is part of the critical infrastructure in Portugal’s capital city, being one of the most accessed ports in Europe, due to its strategic location, and serving container ships, cruise ships, and pleasure crafts.
According to a company statement shared with local media outlets on Monday, the cyberattack did not impact the port’s operations.
“All safety protocols and response measures provided for this type of occurrence were quickly activated, the situation being monitored by the National Cybersecurity Center and the Judicial Police,” says the announcement shared with Portuguese national newspaper Publico.
“The Port of Lisbon Administration (APL) is working permanently and closely with all competent entities in order to guarantee the security of the systems and respective data,” reads the statement for the publication.
At the time of writing, the port’s official website at “portodelisboa.pt” remains offline.
LockBit threatens data leak
APL didn’t disclose the nature of the cyberattack in the announcement, but the LockBit ransomware group added the organization to its extortion site yesterday, thus claiming the attack.
The ransomware gang claims to have stolen financial reports, audits, budgets, contracts, cargo information, ship logs, crew details, customer PII (personally identifiable information), port documentation, email correspondence, and more.
The group has already published samples of the stolen data but BleepingComputer could not verify their legitimacy.
LockBit threatens to publish all files they stole during the computer intrusion on January 18, 2022, if their payment demands aren’t met.
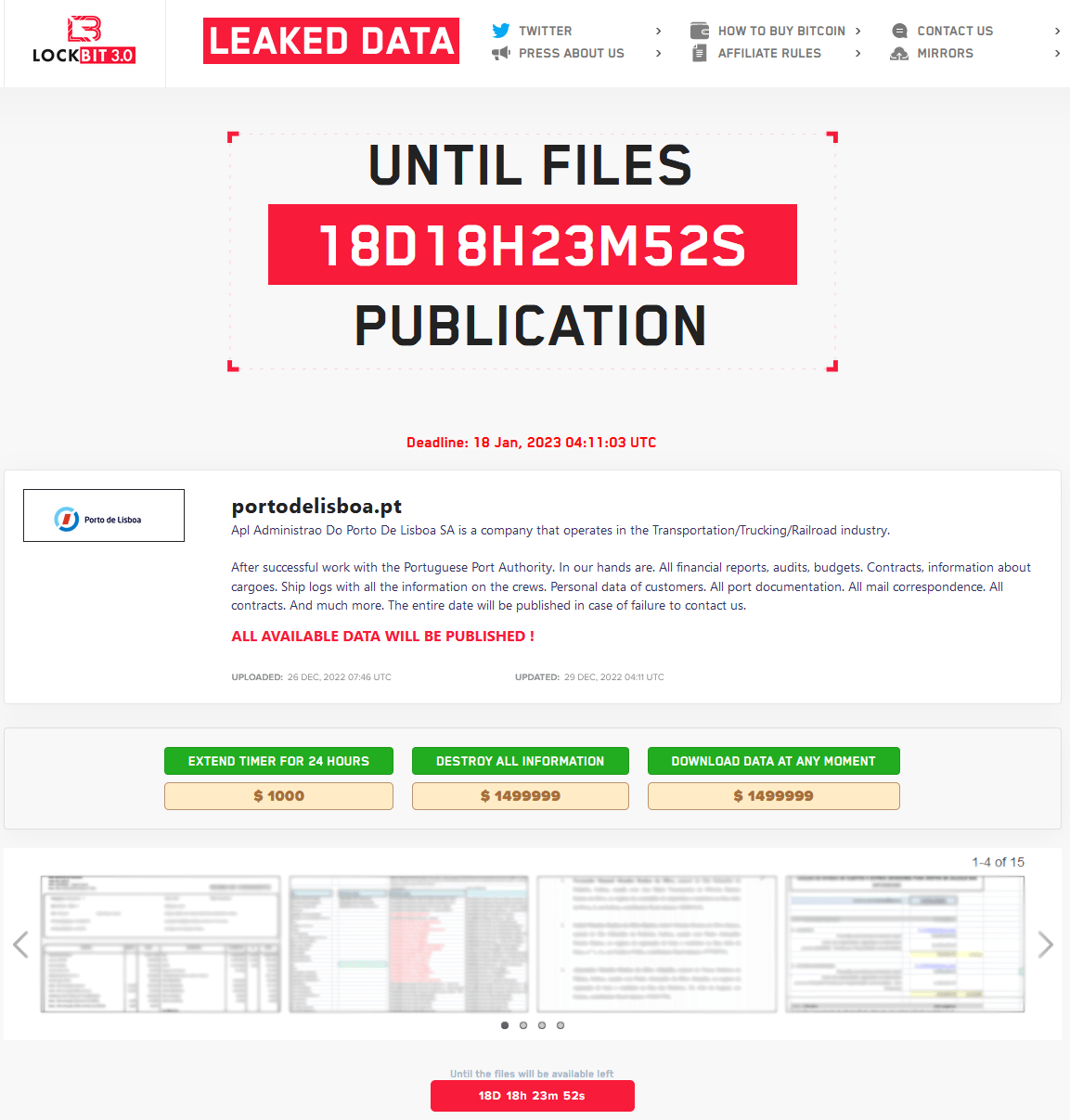
As seen in the image above, the threat actor set the ransom to $1,500,000 and also gives the possibility to delay the publication of the data by 24 hours by paying $1,000.
Interestingly, LockBit offers to sell the data for the same amount to anyone wishing to access them immediately and exclusively.
The LockBit gang is currently at the third version of their encryptor that powers the notorious RaaS (ransomware as a service) project, and one of the most prolific gangs this year.
Another notable recent attack from LockBit targeted Continental, the multinational automotive giant, which got listed on the ransomware gang’s Tor site in November 2022.
This week, Japanese media circulated rumors that the cybercrime department of Japan’s police helped at least three domestic firms restore their systems for free following LockBit 3.0 attacks.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.





