LokiBot Impersonates Popular Game Launcher and Drops Compiled C# Code File

(By Augusto Remillano II, Mohammed Malubay, and Arvin Roi Macaraeg, Threat Analysts)
LokiBot, which has the ability to harvest sensitive data such as passwords as well as cryptocurrency information, proves that the actors behind it is invested in evolving the threat. In the past, we have seen a campaign that exploits a remote code execution vulnerability to deliver LokiBot using the Windows Installer service, a Lokibot variant that uses ISO images, and a variant with an improved persistence mechanism using steganography. Recently, we discovered LokiBot (detected by Trend Micro as Trojan.Win32.LOKI) impersonating a popular game launcher to trick users into executing it on their machines. Further analysis revealed that a sample of this variant employs a quirky, installation routine that involves dropping a compiled C# code file.
This unusual LokiBot variant, which uses a “compile after delivery” detection evasion technique, was proactively detected and blocked by machine learning detection capabilities built into Trend Micro solutions as Troj.Win32.TRX.XXPE50FFF034.
Technical Analysis
The infection starts with a file that is supposedly the installer of the Epic Games store. This fake installer was built using the NSIS (Nullsoft Scriptable Install System) installer authoring tool. In this campaign, the malicious NSIS Windows installer used the logo of Epic Games — the development company behind popular games such as Fortnite — to trick users into thinking that it’s a legitimate installer.

Figure 1. File icon of the LokiBot malware installer under the guise of a game installer
Upon execution, the malware installer drops two files: a C# source code file and a .NET executable in the “%AppData% directory” of the affected machine.
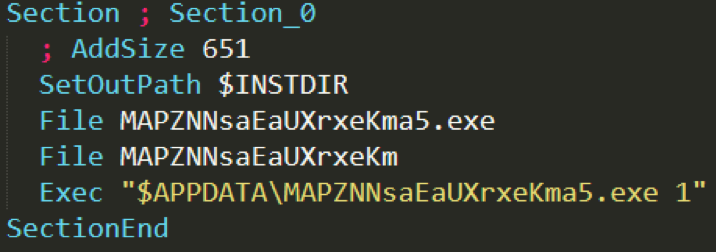
Figure 2. Screenshot of installer script
Further analysis of the .NET executable showed a heavily obfuscated file that contains plenty of junk codes that make reverse-engineering more difficult.
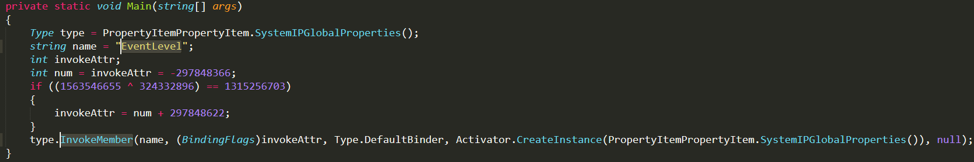
Figure 3. Screenshot showing the main function of the dropped .NET executable
The .NET executable would then read and compile the dropped C# code file, which is named “MAPZNNsaEaUXrxeKm,” within the infected device.
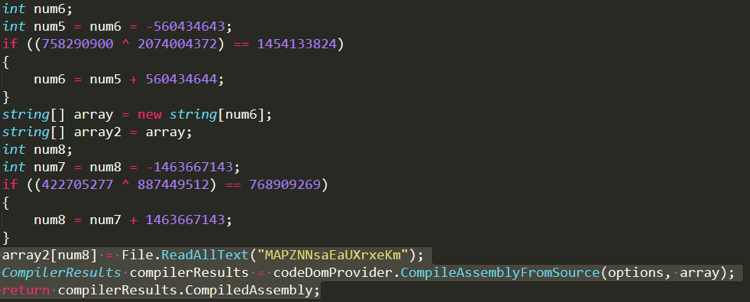
Figure 4. Screenshot of code snippet that shows a portion of the junk code that can be found in the binary (top part), as well as code that shows how the dropped C# code file is read and compiled (bottom part)
After compiling the C# code file, the binary would call the EventLevel function present in the C# code file using the InvokeMember function. The called function would decrypt and load the encrypted assembly code embedded inside it.
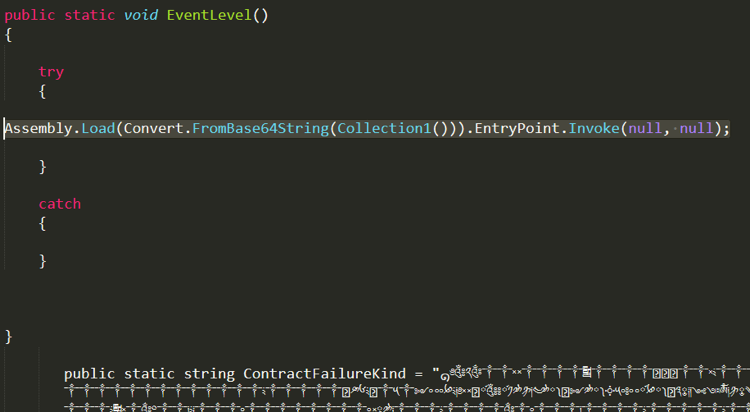
Figure 5. Screenshot of code showing the binary calling the EventLevel() function
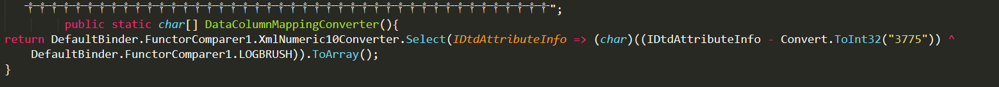
Figure 6. Code snippet that shows how the assembly code would be decrypted
This LokiBot sample’s installation routine combines two techniques to evade detection: First, it makes use of a C# source code to evade defense mechanisms that solely target executable binaries. In addition, it also uses obfuscated files in the form of the encrypted assembly code embedded in the C# code file.
The final phase of the infection would be the execution of the LokiBot payload. Consistently among the most active infostealers in the wild, these tweaks to its installation and obfuscation mechanisms indicate that LokiBot is not about to slow down in the near future.
Trend Micro Solutions
Trend Micro Deep Discovery
Deep Discovery provides detection, in-depth analysis, and proactive response to attacks using exploits and similar threats through specialized engines, custom sandboxing, and seamless correlation across the entire attack life cycle, allowing it to detect these kinds of attacks even without engine or pattern updates. These solutions are powered by XGen
provides detection, in-depth analysis, and proactive response to attacks using exploits and similar threats through specialized engines, custom sandboxing, and seamless correlation across the entire attack life cycle, allowing it to detect these kinds of attacks even without engine or pattern updates. These solutions are powered by XGen security, which provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. Smart, optimized, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
security, which provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. Smart, optimized, and connected, XGen powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Indicators of Compromise
| SHA-256 | File Type | Detection Name |
| c93abb57b2b669f8e9a8b4695fe865aea3f0c0e74deafa99e805900b110552e1
|
LokiBot Payload | Trojan.Win32.LOKI
|
| 385bbd6916c88636a1a4f6a659cf3ce647777212ebc82f0c9a82dc4aea6b7c06 | Encrypted Assembly Code | |
| 17d54bca1bd7c11beecfc77b25e966b745b9cf281f2c1c88c99a83f807aec335 | Decoder |
The post LokiBot Impersonates Popular Game Launcher and Drops Compiled C# Code File appeared first on .

![[INCRANSOM] - Ransomware Victim: evergreenpnw[.]com 11 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
