LOLEKHosted admin arrested for aiding Netwalker ransomware gang

Update 8/11/23: Updated with information from DOJ about alleged Netwalker Ransomware involvement.
Police have taken down the Lolek bulletproof hosting provider, arresting five individuals and seizing servers for allegedly facilitating Netwalker ransomware attacks and other malicious activities.
A bulletproof hosting provider is a hosting company that turns a blind eye to reports of criminal activity or the hosting of copyrighted material on their servers.
Cybercriminals prefer these types of hosting providers over traditional companies, as they can launch cybercrime campaigns without fear that they will be shut down after malicious activity is reported.
On Tuesday, BleepingComputer learned that the platform’s site at lolekhosted[.]net had been seized, now displaying a message stating that an international law enforcement operation between Poland and the US seized the site.
“This domain has been seized by the Federal Bureau of Investigation and Internal Revenue Service – Criminal Investigation as part of a coordinated law enforcement action taken against LOLEK HOSTED,” reads the Lolek seizure message.
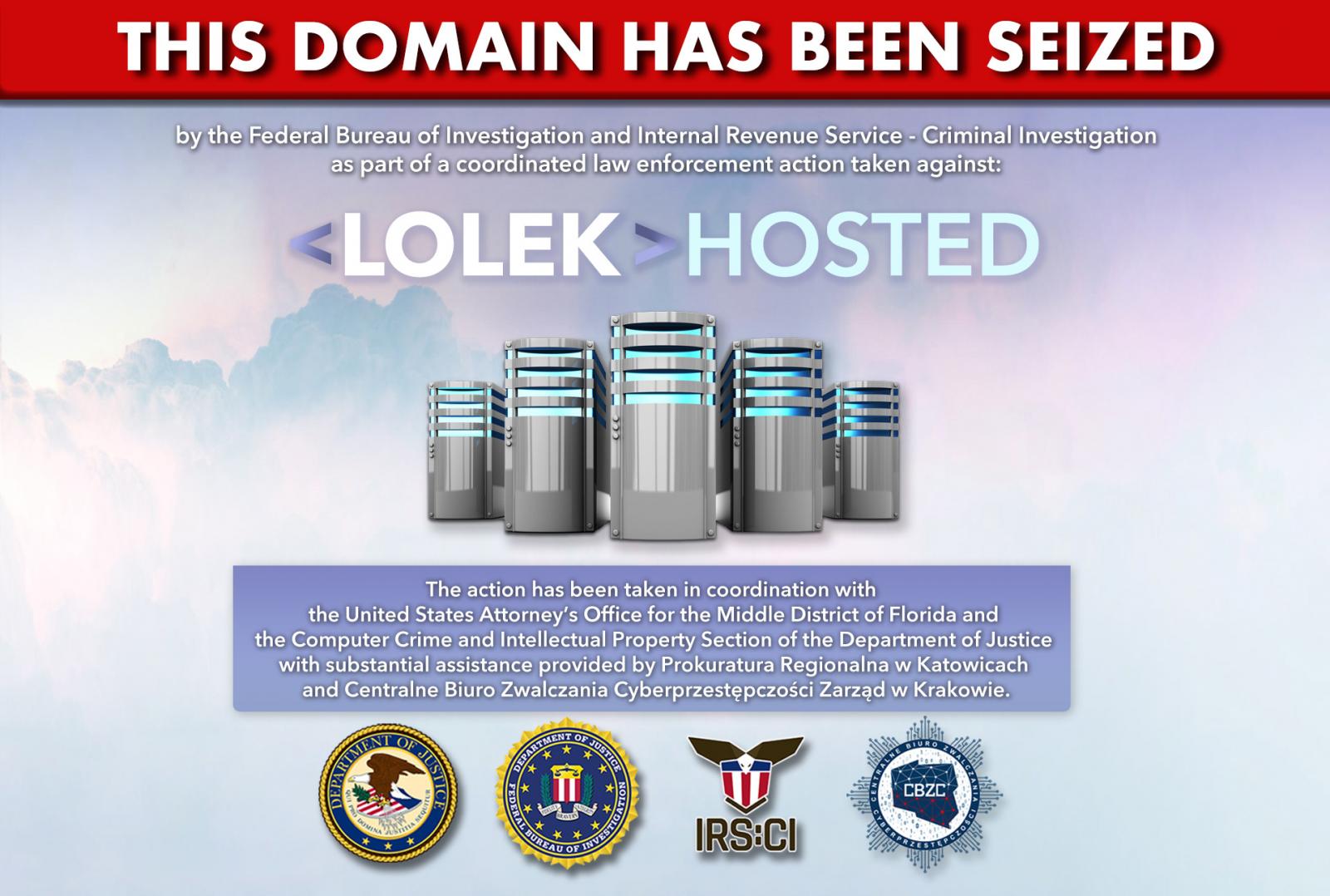
Source: BleepingComputer
Lolek promoted itself as a “100% privacy hosting” service with a no-log policy, meaning they do not log any activity on its servers or routers that could be used to incriminate customers.

Source: BleepingComputer
Customer reviews of the service seen by BleepingComputer said that almost any activity was allowed at the hosting provider, and the platform accepted PayPal and cryptocurrency for payments.
Used by Netwalker Ransomware gang
While the FBI and IRS declined to comment earlier this week on the investigation, Europol and the DOJ announced today the seizure of Lolek and the arrest of five administrators in Poland.
“This week, the Polish Central Cybercrime Bureau (Centralne Biuro Zwalczania Cyberprzestępczości) under the supervision of the Regional Prosecutor’s Office in Katowice (Prokuratura Regionalna w Katowicach) took action against LolekHosted.net, a bulletproof hosting service used by criminals to launch cyber-attacks across the world,” reads Europol’s announcement.
“Five of its administrators were arrested, and all of its servers seized, rendering LolekHosted.net no longer available.”
Europol says that Lolek was seized as cybercriminals used its servers to launch DDoS attacks, distribute information-stealing malware, host command and control servers, host fake online shops, and conduct spam campaigns.
However, an announcement by the US Department of Justice sheds more light on the police operation, stating that a Polish national named Artur Karol Grabowski was charged yesterday for the operation of LolekHosted.
While it is unclear if Grabowski was one of the administrators arrested in Poland, the DOJ says he facilitated cybercrime by allowing customers to register under fake names, frequently changing IP address of servers, and notifying customers of legal inquiries.
The DOJ also states that Grabowski allegedly aided the now-disrupted ransomware operation known as Netwalker by renting servers used in over 50 attacks to breach networks and store stolen data and hacking tools.
“LolekHosted clients used its services to execute approximately 50 NetWalker ransomware attacks on victims located all over the world, including in the Middle District of Florida,” reads the DOJ announcement.
“Specifically, clients used the servers of LolekHosted as intermediaries when gaining unauthorized access to victim networks, and to store hacking tools and data stolen from victims.”
Law enforcement seized the bulletproof hosting provider’s servers on August 8th in an operation led by the FBI and IRS, with Europol providing support linking available data to various criminal cases within and outside the EU, as well as tracing cryptocurrency transactions.
Grabowski now faces charges of computer fraud conspiracy, wire fraud conspiracy, and international money laundering, and if convicted of all, could receive 45 years of jail time.
As bulletproof hosting providers have become a significant component in malware distribution and cybercrime, law enforcement has been actively targeting these platforms.
In 2018, the Dutch police seized MaxiDed for hosting DDoS botnets, cyber-espionage, malvertising, spam, and malware operations. Since then, numerous arrests [1, 2] have been made for involvement in BPH services.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

