Macs turn on apps signed by Symantec, treat them as malware
On August 23, following an update to Apple’s XProtect system—one of the security features built into macOS—some Mac users began to see security alerts about some of their apps, claiming that they “will damage your computer,” and offering users the option to “report malware to Apple.” This has led to much confusion online, and to an influx of requests in our support system asking about this malware. The most common so far has been from an app named ReceiverHelper.
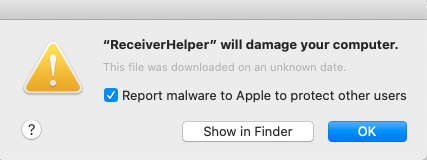
Is ReceiverHelper malware?
If you’re one of the affected folks, the good news is that this isn’t malicious at all. It is a component of Citrix, which is legitimate software made by the company of the same name. Not all Citrix software is being flagged as malicious, fortunately. Only some older versions of the software are causing problems.
Of course, if you thought that this was malware, we’d have to forgive you. Not only is macOS apparently saying that it is, but the name is highly suspicious. There has been a fair bit of Mac adware going around lately with odd two-word names, like StandardBoost or ActivityInput. All of these adware names are pretty generic, revealing nothing about what they’re actually supposed to be doing. Unfortunately, the name “ReceiverHelper” fits right in.
ReceiverHelper is not alone. There are a few other apps acting up. Among them are two other Citrix apps, ServiceRecords and AuthManager_Mac. (It’s almost like Citrix is trying to make its apps sound shady!) Other companies are also seeing an impact to older apps, such as AnyConnect’s vpnagentd.
What’s causing the warnings?
As was the case with a similar issue affecting HP printers last year, it’s all about code signing. What is code signing, you ask? In short, it’s a cryptographic way to validate that an app has not been tampered with. If an app is signed by the company that created it then you can be sure you’re using an unadulterated version of the software. Code signing is a really important security feature, and all apps really ought to be signed. If they’re not, they can’t be considered 100% safe. (For a primer in code signatures and certificates, see our previous coverage of the HP incident.)
In simple terms, code signing relies on a chain of trust: Signing is performed using a secret key. An organization proves its ownership of that secret key using a digital certificate, and that certificate’s authenticity is vouched for by a certificate authority (CA).
In the HP incident, HP revoked the certificate it used to sign a lot of its printer software. The HP software on people’s Macs didn’t change but the chain of trust that vouched for it was broken, so it began to trigger alerts as if it was malware.
This time around the chain of trust has been broken again, but the problem isn’t the certificates, it’s the CA that vouches for the certificates.
A CA is an trusted organization that issues certificates. In the case of Mac apps, you’re really supposed to get your certificates directly from Apple. However, not everyone does, and some companies will use certificates obtained from third parties to sign their apps.
Citrix did exactly this, and the decision has come back to haunt them. It turns out, they made a really poor choose of CA to obtain their certificate from: Symantec.
What’s wrong with Symantec?
A few years ago, Symantec offered CA services. However, Symantec CA played a bit fast and loose with the rules, which is never good for a CA. An important part of being a certification authority is trust, and Symantec made some big mistakes as a CA. Those mistakes led to an investigation, and what was found was highly concerning.
As a result, it was widely agreed that trust for Symantec certificates should be gradually phased out. The slow process of distrusting Symantec certificates began in 2018.
On August 23, 2021, Apple pushed out an update for XProtect that, among other things, rejects any code signed with certificates issued by Symantec. The Gatekeeper process in macOS will reject any apps signed with such a certificate, showing the infamous “will damage your computer” message.
For those technically inclined and in possession of one of the affected apps, you can verify this yourself with the codesign and spctl commands in the Terminal:
% codesign --verify --verbose /usr/local/libexec/ReceiverHelper.app
/usr/local/libexec/ReceiverHelper.app: valid on disk
/usr/local/libexec/ReceiverHelper.app: satisfies its Designated Requirement
% spctl -a /usr/local/libexec/ReceiverHelper.app
/usr/local/libexec/ReceiverHelper.app: rejectedThe codesign command shows that the code signature is still valid—meaning that the app hasn’t been tampered with and the certificate hasn’t been revoked. However, the spctl command, which checks the file with Gatekeeper, shows that it is rejected, and thus will not be allowed to run.
How do I fix these issues?
The best fix is to simply remove or update the affected software. Unfortunately, we can’t help you with that. We’re good at removing malware here at Malwarebytes, but that’s not what this is. You’ll need to find out from the vendor of the affected software how to remove or replace it. For Citrix software, we recommend contacting Citrix support. (Unfortunately, we’ve gotten some reports that Citrix support is turning folks away if they don’t have active accounts, so you may need to be persistent.)
We do know that the affected Citrix apps (that we know about) are located at the following path:
/usr/local/libexec/
Why there? Excellent question… I have no idea. It’s not the right place for these things on macOS. Deleting ReceiverHelper, ServiceRecords, and AuthManager_Mac from this location may solve your problem. It also may cause other problems, as that wouldn’t be a complete uninstallation. You do this at your own risk and we suggest that you treat it as a method of last resort.
Avoid scams!
Unfortunately, if you type something like “remove ReceiverHelper” into Google right now, you’re going to get a bunch of scam sites in the results. These sites purport to help you remove the software, but in reality the instructions are automatically generated. The goal of these sites is to rank high on search results, call whatever the user was searching for malware (ReceiverHelper, et al, in this case), then promote some junk software to folks who visit and find they’re having trouble with the (nonsensical) instructions.
When you’re having a problem like this, Google and other search engines can be your worst enemy. Instead, consider asking on the Malwarebytes forums, Apple’s forums, or similar places, to get better advice.
The post Macs turn on apps signed by Symantec, treat them as malware appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[QILIN] - Ransomware Victim: alissco[.]com 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
