Main phishing and scamming trends and techniques

There are two main types of online fraud aimed at stealing user data and money: phishing and scams. Phishers primarily seek to extract confidential information from victims, such as credentials or bank card details, while scammers deploy social engineering to persuade targets to transfer money on their own accord.
The history of scams and phishing
The term “phishing” was coined back in 1996, when cybercriminals attacked users of America Online (AOL), the largest internet provider at that time. Posing as AOL employees, the scammers sent messages asking users to verify their accounts or asking for payment details. This method of phishing for personal data is still in use today, because, unfortunately, it continues to yield results.
Also in the 1990s, the first online scams appeared. When banks began to roll out internet banking, scammers sent text messages to users supposedly from relatives with an urgent request to transfer money to the details given in the message.
By the early 2000s, charity had become a common scam topic: for example, after the massive Indian Ocean earthquake and tsunami of 2004, users received messages from fake charities pleading for donations. At around the same time, phishers started targeting online payment systems and internet banks. Since user accounts in those days were protected only by a password, it was enough for attackers to phish out this information to gain access to victims’ money. To do this, they sent e-mails in the name of companies such as PayPal, asking users to go to a fake site displaying the corporate logo and enter their credentials. To make their sites look more credible, cybercriminals registered multiple domains all very similar to the original, differing by just two or three letters. An inattentive user could easily mistake a fake for a genuine bank or payment system website. In addition, scammers often used personal information from victims’ own social media pages to make their attacks more targeted, and thus more successful.
As time progressed, online fraud became ever more sophisticated and persuasive. Cybercriminals learned how to successfully mimic the official websites of brands, making them almost indistinguishable from the original, and to find new ways to approach victims. There appeared services specializing in creating fake content, at which point phishing really took off. Now not only the personal data and finances of ordinary users were in the firing line, but politicians and big business as well.
This report examines the main phishing trends, methods, and techniques that are live in 2022.
Phishing and scams: current types of fraud
Phishing:
Phishers can target credentials in absolutely any online service: banks, social networks, government portals, online stores, mail services, delivery companies, etc. But it is customers of top brands that are most often at risk, because people use and trust them more than smaller brands, increasing the likelihood of a successful attack.
To extract the coveted information, cybercriminals try to persuade victims that they are logging in on the real website of the respective company or service, or that they are sharing their credentials with a company employee. Often, fake sites look no different from the original, and even an experienced user might be fooled. Phishers skillfully copy the layout and design of official sites, adding extra details to their pages, such as live chat support (usually inactive), and linking to real services to inspire confidence.
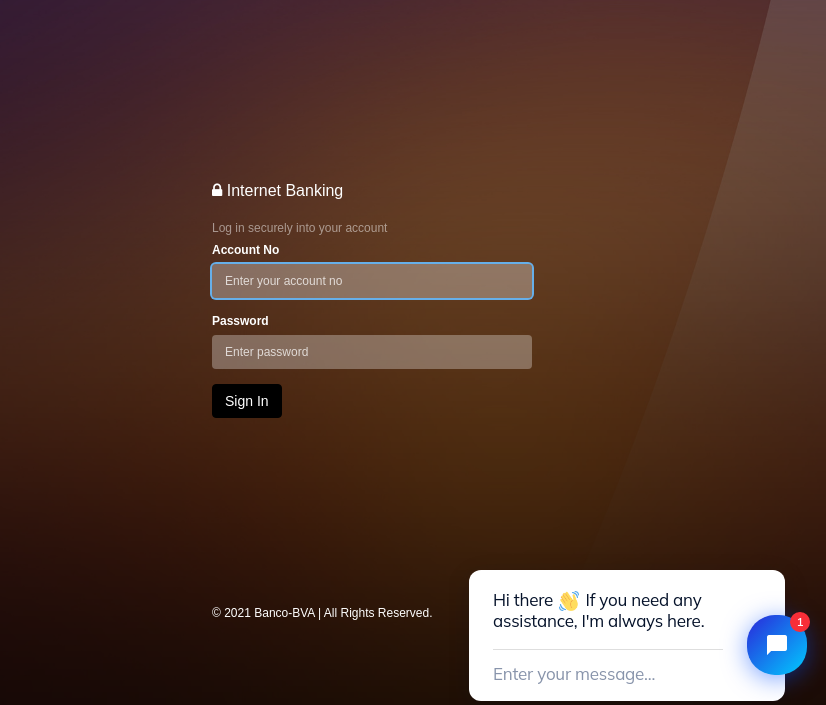
Phishing site with chat support
Recently, alongside online phishing, vishing (voice phishing) has been on the rise. Scammers either call victims directly, or employ various tricks to get them to make the call, after which they attempt to extract their personal data and money over the phone.
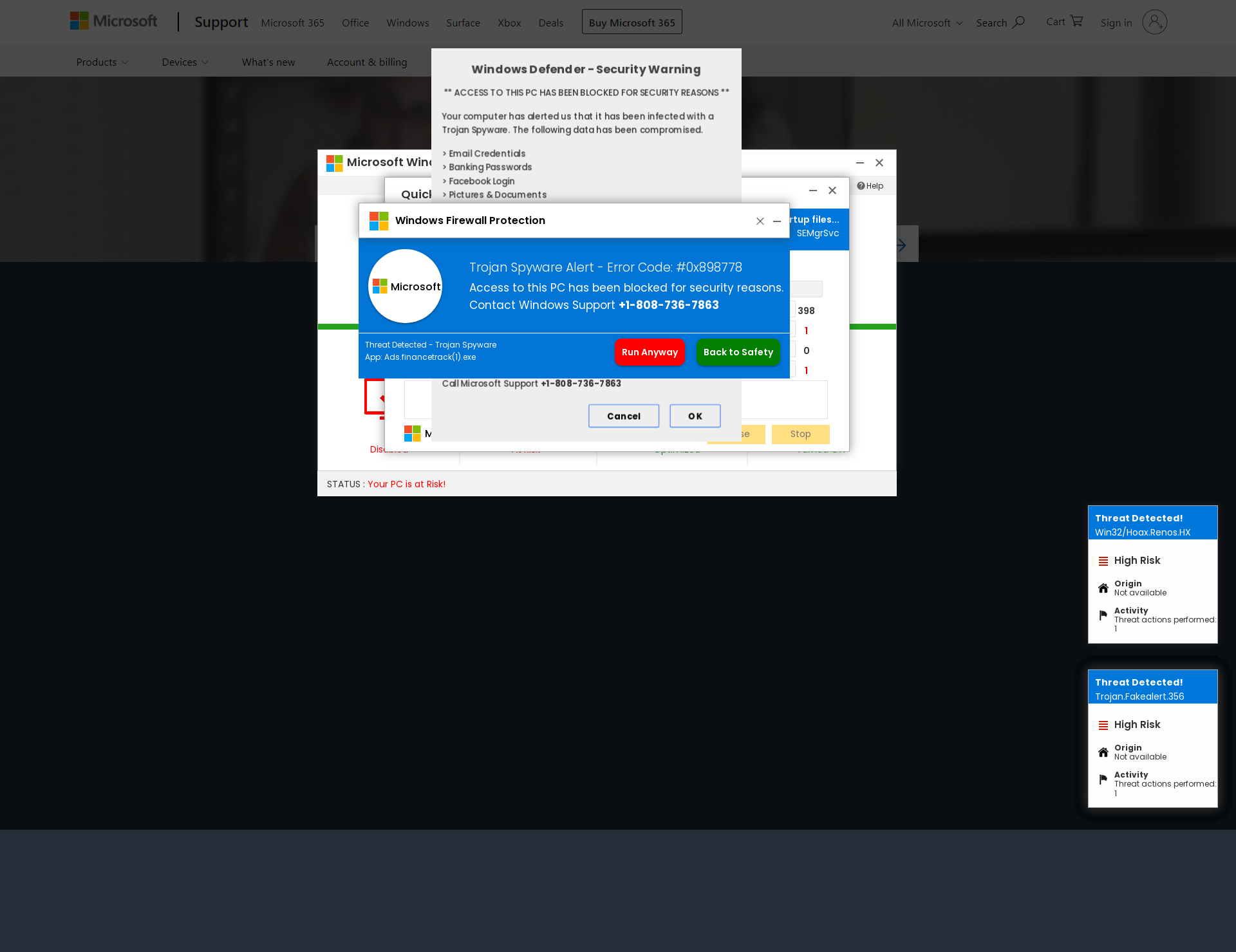
Fake message about Windows-related issues in connection with which the victim must call the scammers
Also current is targeted or spear phishing, which, as the name suggests, is aimed at a specific individual or organization. Spear-phishing e-mails and sites are far more personalized than bulk ones, making them very difficult to distinguish from genuine ones.
Scams
While phishers target both businesses and ordinary internet users, scammers prey mostly on the latter. Most scams work by offering the victim an easy way to earn a chunk of money, or the chance to win a valuable prize or get something for free or at a huge discount. The main goal of this type of threat is to raise money, but scammers can also harvest the victim’s personal data to sell later or use in other schemes.
In the screenshot below, for example, the victim is informed they have won a smartphone and asked to pay a small fee to have it delivered, as well as specify their e-mail address, date of birth, gender, phone number, and home address.
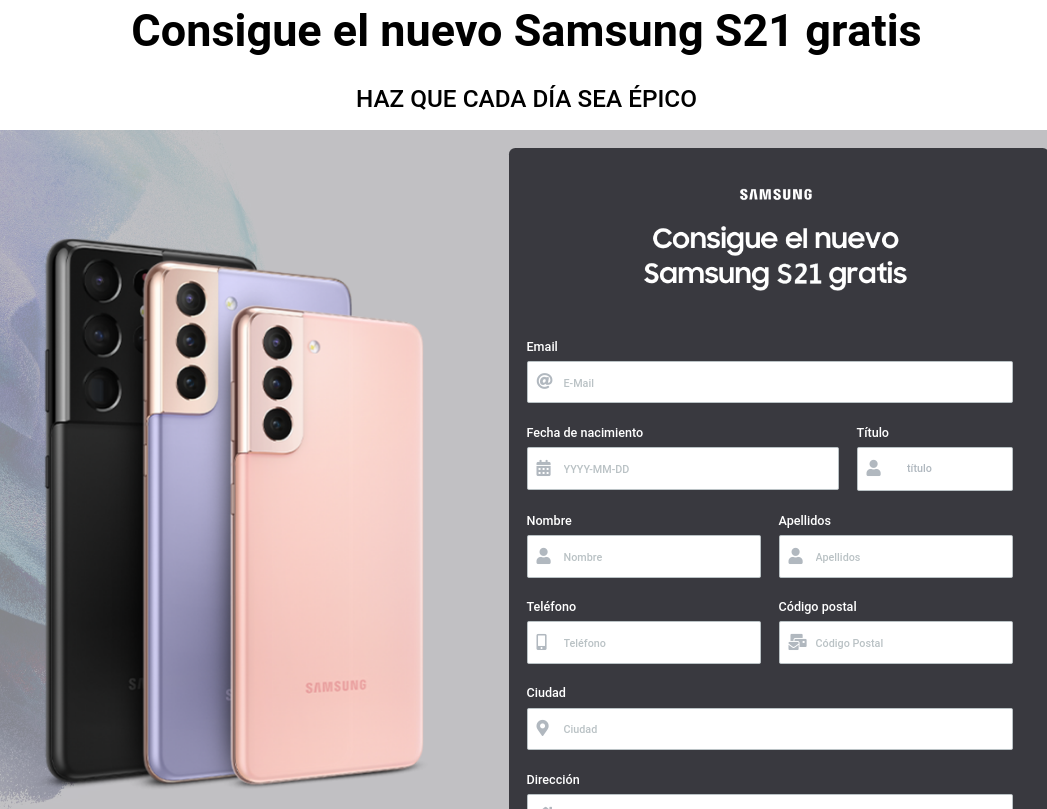
Form for collecting personal data to send the bogus prize
In most cases, scammers ask for this data to convince the victim that the prize will indeed be sent, and do not store it. However, some scammers may save all the information entered on their sites for the purpose of later sending malicious e-mails supposedly from victims, using their names and addresses.
Besides promises of easy money and valuable prizes, scammers actively lure users to non-existent dating sites. For example, they might send an invitation to chat with other users, together with a link to a scam site and attractive photos. Once on the fake site, the user is told they can get premium access to the dating platform for next to nothing, but the offer expires today. They just need to sign up and pay a small fee.
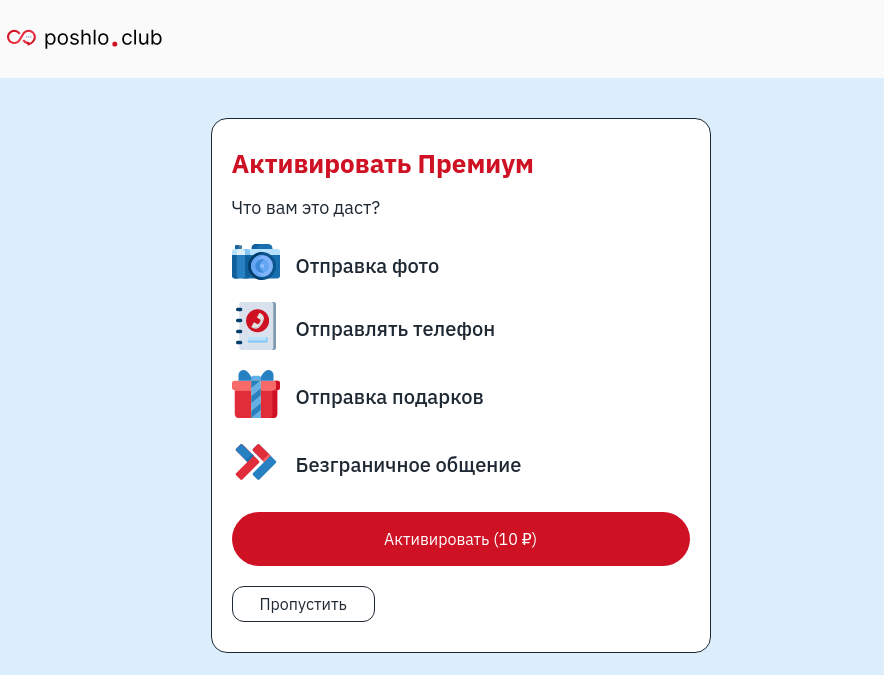
Offer to activate a premium account on a fake dating site
There are other ways to attract victims to scam sites: by “selling” sought-after or scarce goods, or trips with like-minded travelers, etc. In general, if something’s popular with users, fraudsters will use it as bait.
Distribution
Although most scams and phishing attacks begin with mass e-mails containing links to fake websites, alternative attack vectors are gaining ground today. There are so many different communication and data sharing platforms that attackers can use to distribute phishing links.
Messengers
One of the main vectors for phishing and scaming are messengers such as WhatsApp and Telegram.
WhatsApp users might receive a fraudulent message from either the cybercriminals themselves or someone in their contact list. To spread their scams, attackers send messages in the name of popular brands or government agencies, but have no qualms about involving users too. In particular, to receive a gift promised in a message, they often get the victim to forward it to all or some of their contacts.
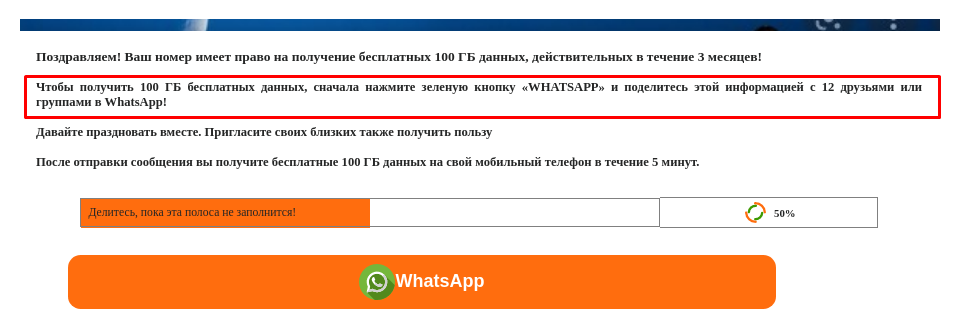
Cybercriminals get the victim to forward a link to a fake giveaway to their WhatsApp contacts
Recently, many channels have appeared on Telegram promising prizes or get-rich cryptocurrency investment schemes. The chats of popular Telegram channels are also home to scammers who, posing as ordinary users, post juicy money-making and other offers. For posting comments en masse, cybercriminals can use bots. To discover the secret of easy money, the user is invited to contact the scammers or go to their channel.
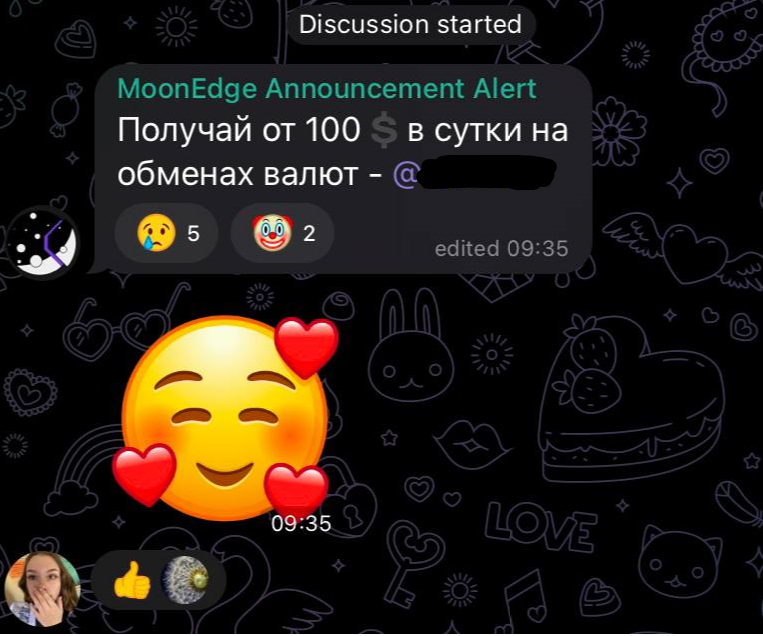
Comment in a Telegram chat promoting a currency exchange scheme
Social networks
Comments offering easy profits are also found on social networks, for example, under photos in popular accounts, where messages are more likely to be read than on a page with fewer followers. Cybercriminals invite users to follow a link in a profile header, send them a direct message, or join a secret group chat. A message can also contain a link to a phishing or scam site. Posts promising well-paid part-time work with a link to a mini app are also common on VK, the Russian equivalent of Facebook. In addition, cybercriminals can use social networks to send direct messages to users, promote their offers, or create fake accounts promising valuable gifts, in-game currency, and gift cards. These are hyped up through ads, hashtags, or mass tagging of users in posts, comments, or on photos.
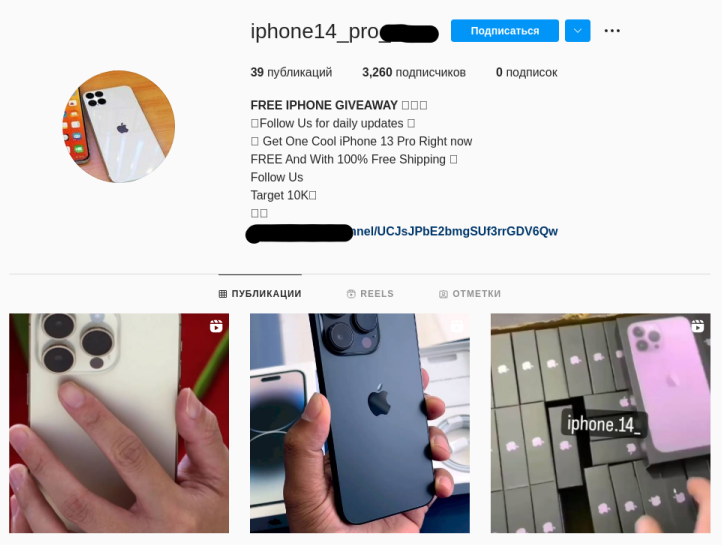
Instagram account “giving away” free smartphones
Marketplaces
Marketplaces act as an intermediary between the user and the seller, to some extent ensuring the security of the transaction for both parties. But their functionality is open to abuse by scammers as well. A widespread scheme on Russian marketplaces is when the seller appears reluctant to communicate on the site and tries to move the conversation to a third-party messenger where they can send a malicious link without fear of triggering the marketplace’s built-in defenses.
Also on marketplaces, scammers often comment on other users’ reviews of products, assuring potential buyers that an item can be purchased for far less elsewhere, and attaching a link to a scam site.
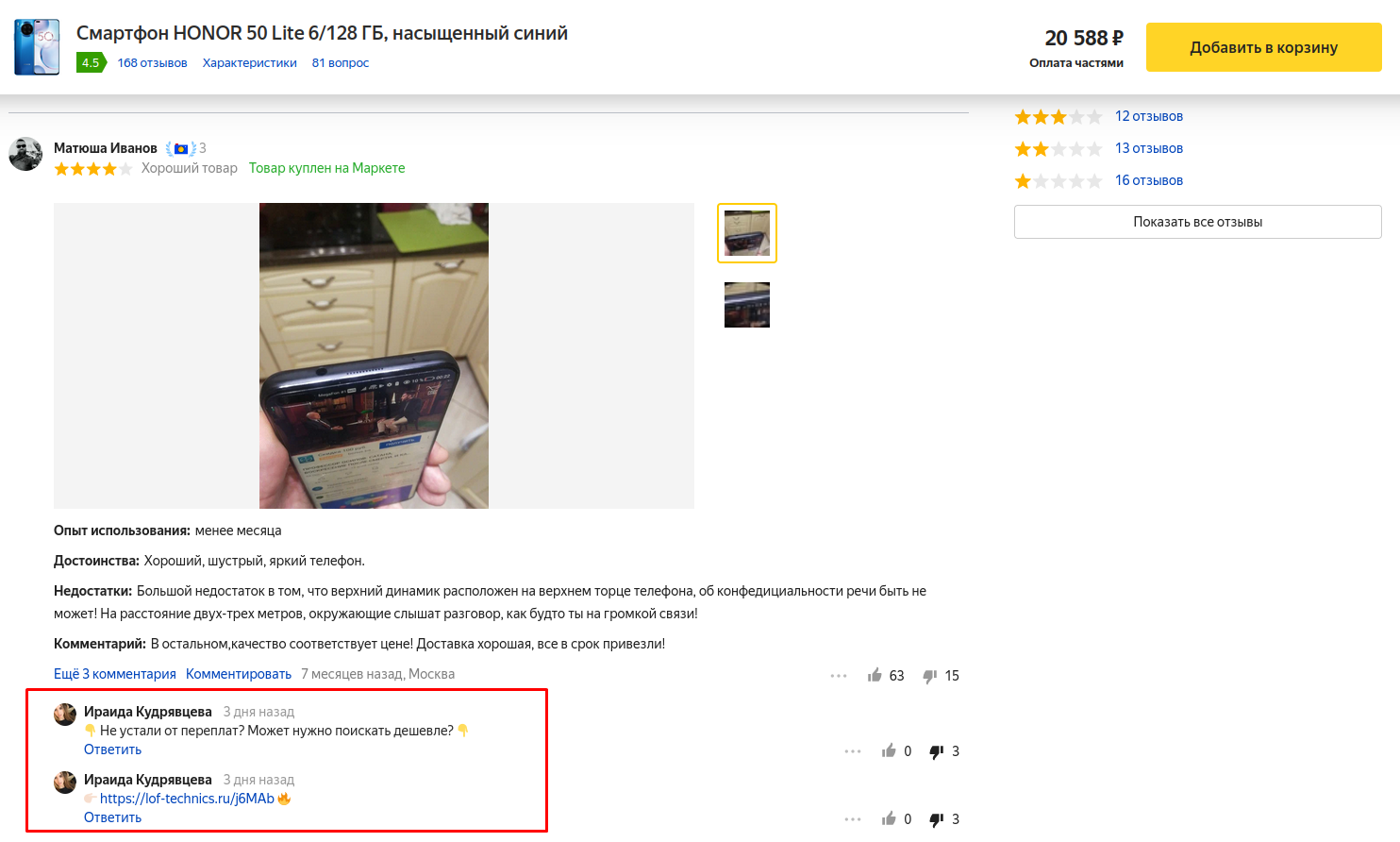
Scammers distribute links to fake sites through comments on product reviews on marketplaces
Phishing and scam attack methods
To carry out attacks, cybercriminals employ a wide range of technical and psychological tricks to dupe as many users as possible while minimizing the risk of detection.
Below are the main phishing and scam techniques used in 2022.
Spoofing
To increase the victim’s trust in a fake resource, scammers often try to make it as similar as possible to the original. This technique is known as spoofing. In the context of website spoofing, there are two main types:
- Domain spoofing, when attackers fake a website domain to fool users,
- Content spoofing, when they mimic the appearance of a legitimate site.
It’s common for attacks to deploy both of these.
Domain spoofing involves registering a domain similar to that of the target organization. Phishers are careful to choose domains that don’t look suspicious to victims. Domain spoofing can be divided into three categories:
- Typosquatting is the use of the original domain name with typos commonly made by users when inputting the URL, such as missing or extra characters, or letters in the wrong order.
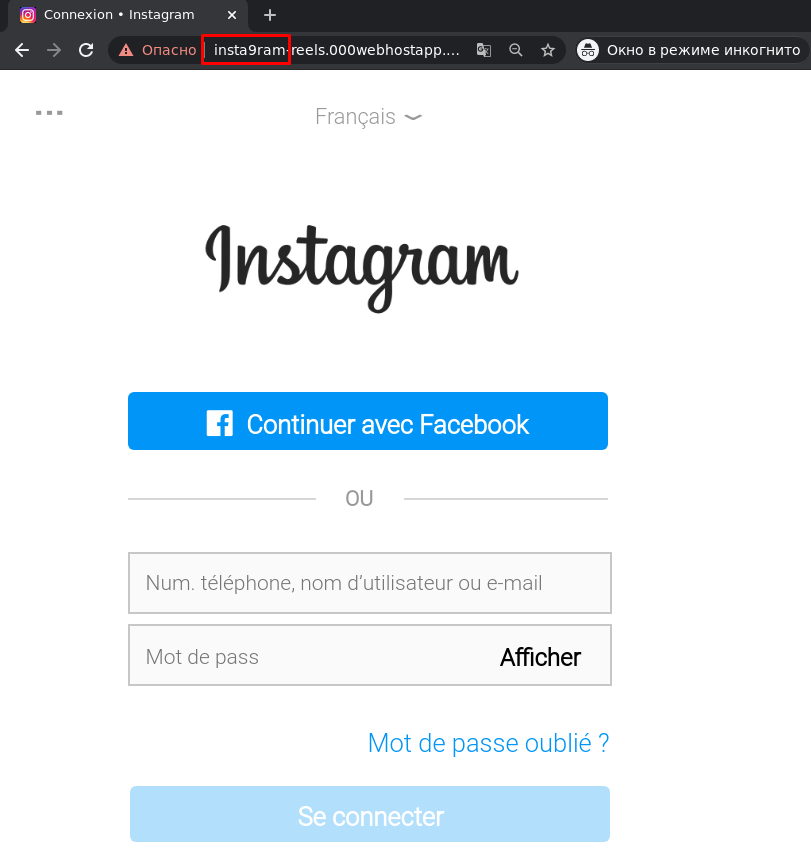
Misspelling of the domain Instagram.com, where the number 9 appears instead of the letter “g”
- Combosquatting is the use of additional words, often related to authorization or online security, in a domain name similar to that of the brand whose users are the target. For example, words like “login”, “secure”, “account”, “verify”, and so on.
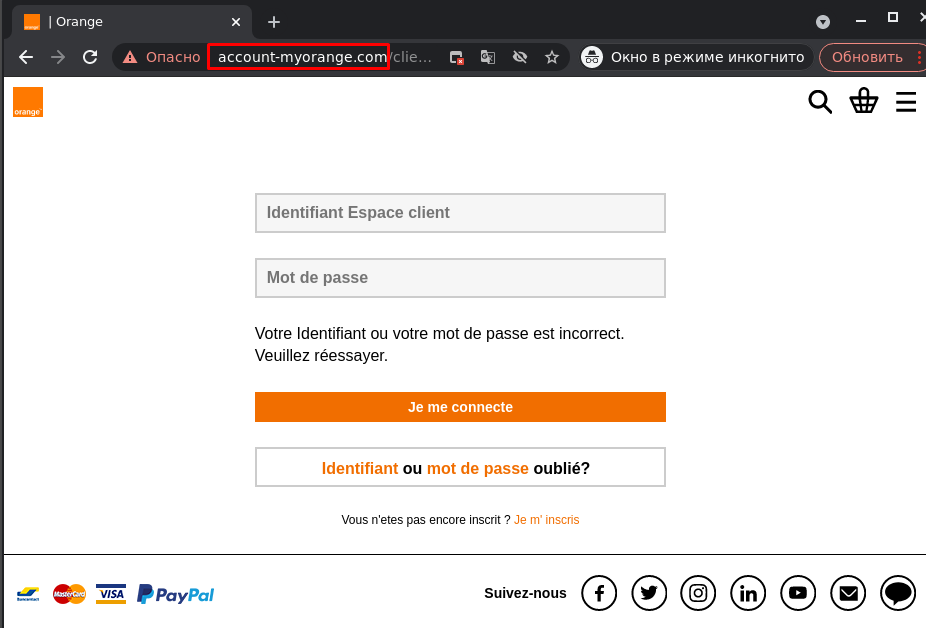
The word “account” in a domain name alongside the name of a bank
- Internationalized domain name (IDN) homograph attacks work by using Unicode characters that closely resemble letters in the Latin alphabet. For example, the most commonly used Cyrillic letters in such attacks are a, c, e, o, p, x, y, because they look identical to Latin a, c, e, o, p, x, y.
Content spoofing is used to fake the appearance of a legitimate site. Here, the following methods can be singled out:
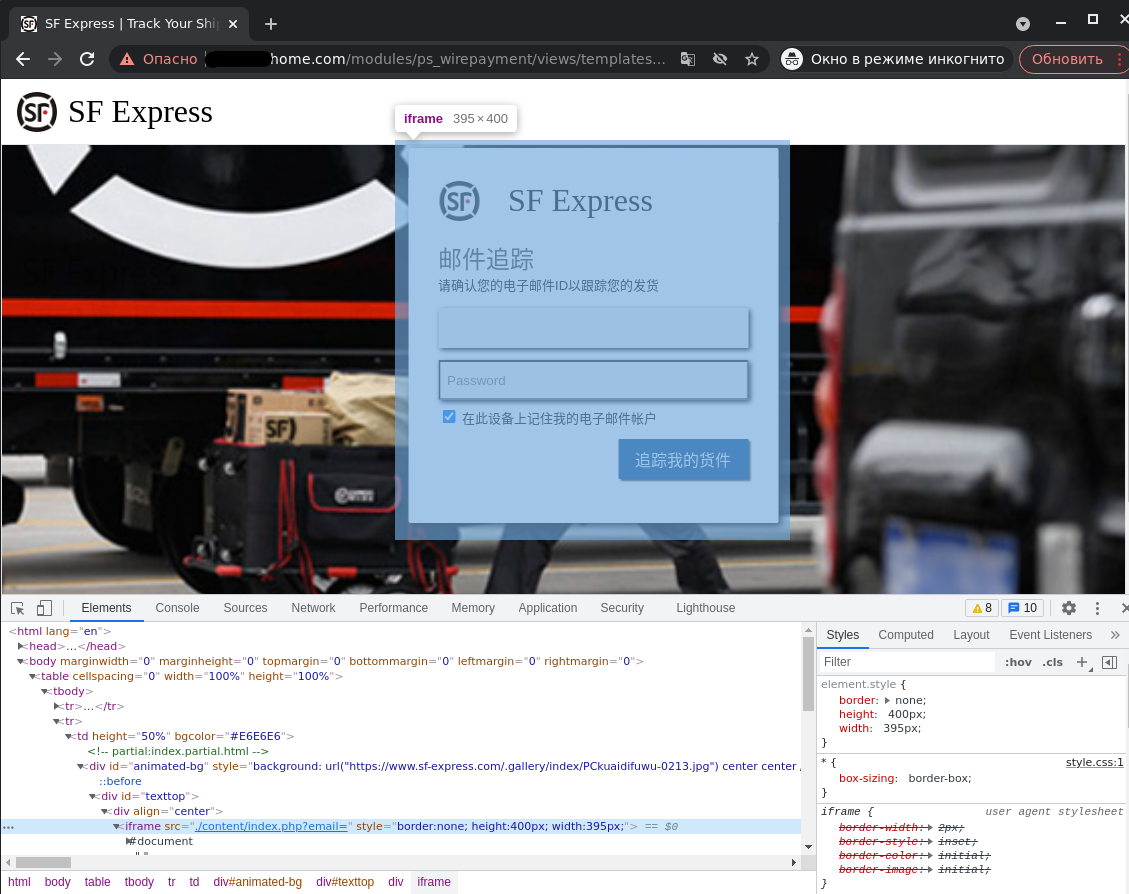
- Legal iFrame Background is when an iFrame is used to load a legitimate site onto a rogue one, on top of which a phishing form is overlaid.
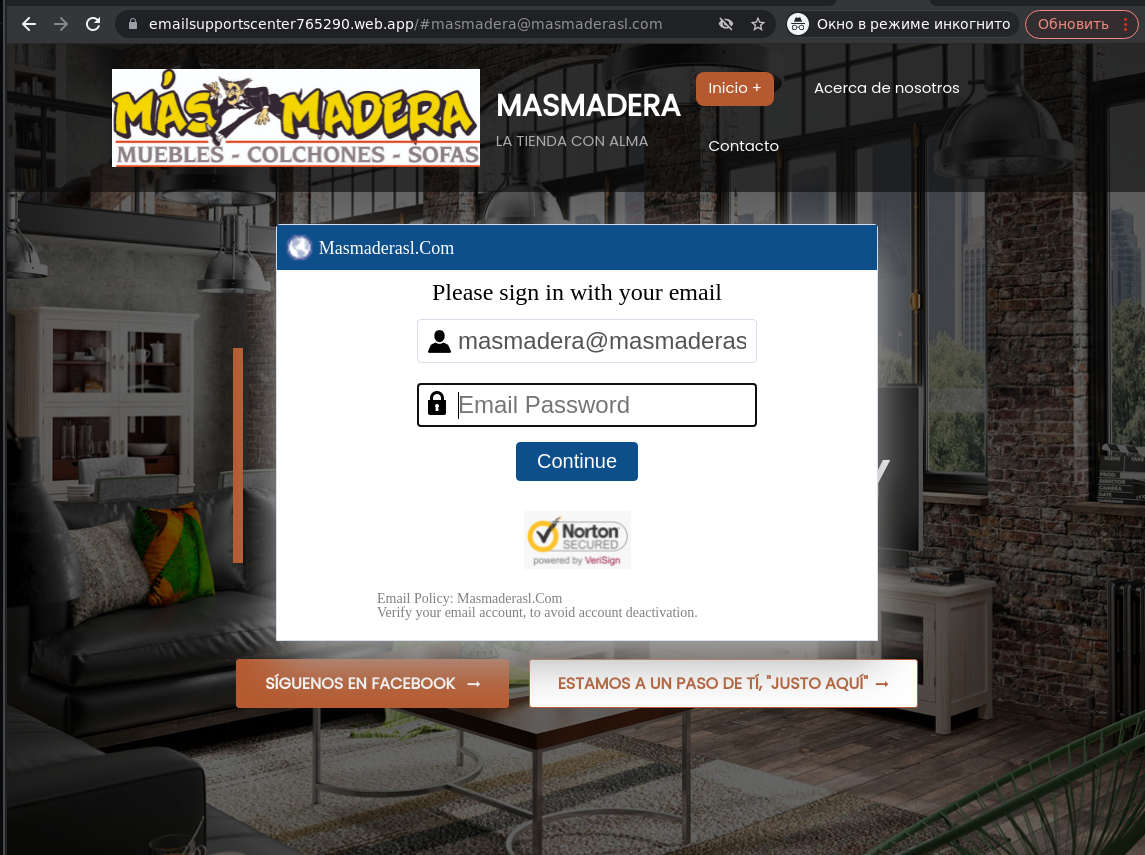
Legitimate site serving as a background for a phishing form
- HTML spoofing is the visual imitation of a legitimate site by, among other things, partially copying its style and HTML code. Scammers often use software for creating mirror sites, such as HTTrack and Website Downloader.
- iFrame Injection is when a login form or other part of a phishing page is inserted through an iFrame. Whereas the Legal iFrame Background method involves the use of an iFrame with a legitimate website as the background for a phishing form, in the case of iFrame Injection the URL of the page is legitimate, while the iFrame contains a phishing form, whose background is most often homemade content using brand logos.
- Subfolder Hijacking is the partial hacking of a site to gain access to its subdirectories to place fraudulent content there. Such attacks can either use existing directories on the legitimate site or create new ones.
- Site Swapping is the complete replacement of a legitimate site with a phishing one. The original content is usually removed.
- Use of images. If text is replaced with images of text, content engines will be unable to see and analyze the text, so users will read it.
- Browser notifications. Links to scam resources can be distributed through browser notifications. Unlike e-mails and public websites, browser notifications are processed in several stages, and not all anti-phishing engines analyze them. This allows cybercriminals to bypass at least some detection technologies.
- Pop-up windows. Scam content can open in pop-up windows on a site. Pop-up windows load later than the site’s main window, so not all anti-phishing technologies see them. In addition, pop-up windows furnish attackers with additional tools to copy the appearance of a legitimate site. In particular, cybercriminals can use the Browser-in-the-Browser method, when a pop-up window imitates a browser window with an address bar showing the URL of a legitimate site.
- URL links randomly generated using hashes. Each victim receives a unique link, which makes it difficult to block a malicious site.
- URL shorteners. Attackers can mask malicious addresses using legitimate URL shorteners, such as bit.ly.
- Fake CAPTCHA. Cybercriminals mimic CAPTCHA technology on scam sites to persuade victims to perform certain actions.
- User-Related Dynamic Content. The page content changes depending on the user and their data, such as e-mail address: to fake the domain, images are downloaded from the user’s mail and inserted into the phishing page.
- Intimidation and threats. Cybercriminals can intimidate victims to make them panic and act rashly. For example, they may threaten legal action and demand payment of a “fine” for the victim to be left in peace. Attackers can also threaten to block the victim’s account to force them to click a phishing link.
- Attackers give victims a limited time window to respond to their message in one way or another to make them act rashly.
- An appeal to pity. Cybercriminals try to arouse people’s sense of pity to get them to part with their cash.
- Lucrative offers. Scammers tempt victims with lip-smacking offers that are hard to refuse.
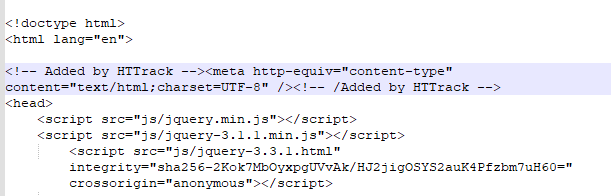
Comment in the HTML code of a phishing page indicating that HTTrack was used
Website hacking
Sometimes it’s easier for scammers to hack others’ sites to host malicious content than to create their own from scratch. Such phishing pages tend to be short-lived, because the site owners quickly detect and remove scam content, as well as regularly patch holes and vulnerabilities in their infrastructure. That said, if cybercriminals break into an abandoned site, phishing pages hosted there can survive a long time. Phishers can exploit compromised sites in several ways:
Login form created using an iFrame on a hacked site
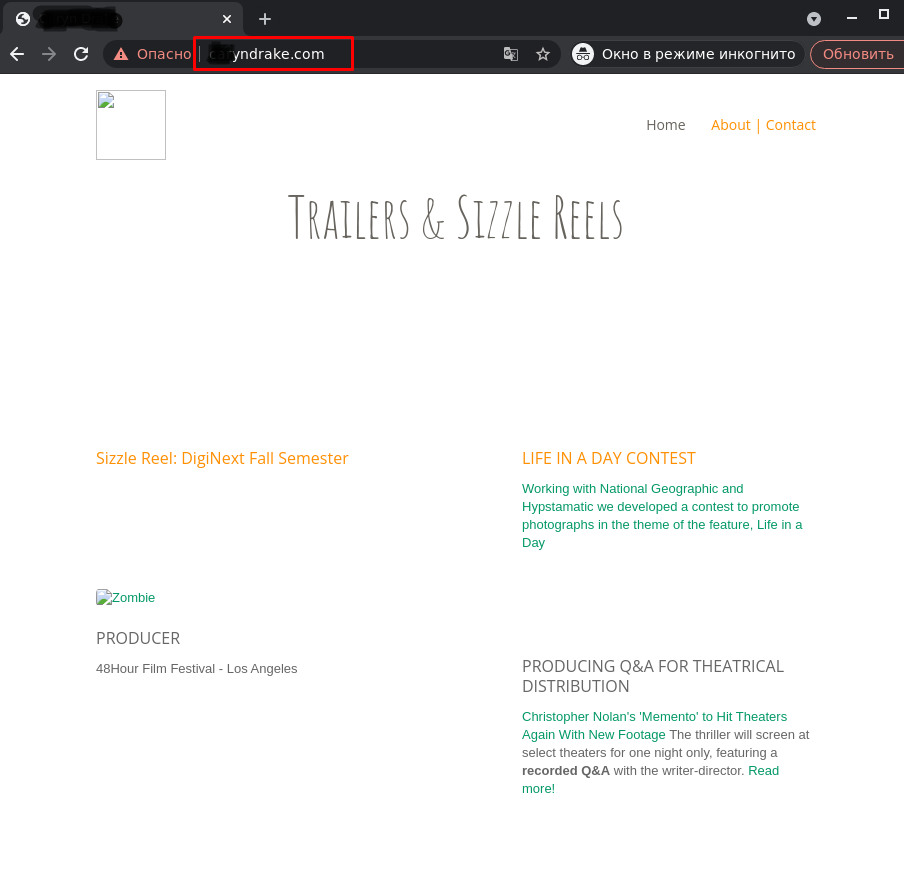
Home page of a hacked site that looks normal

Phishing page placed in a subdirectory of a hacked site
Using legitimate services
Some internet scammers, instead of bothering to create or hack sites, prefer to exploit the features of services trusted by users. As such, forms for creating online surveys and collecting data (Google Forms, MS Forms, HubSpot Form Builder, Typeform, Zoho Forms, etc.) are very often used to perform an attack.
For example, in the screenshot below, scammers under the guise of technical support for a popular cryptowallet use a Google form to coax identification data out of users, such as e-mail address and secret phrase.
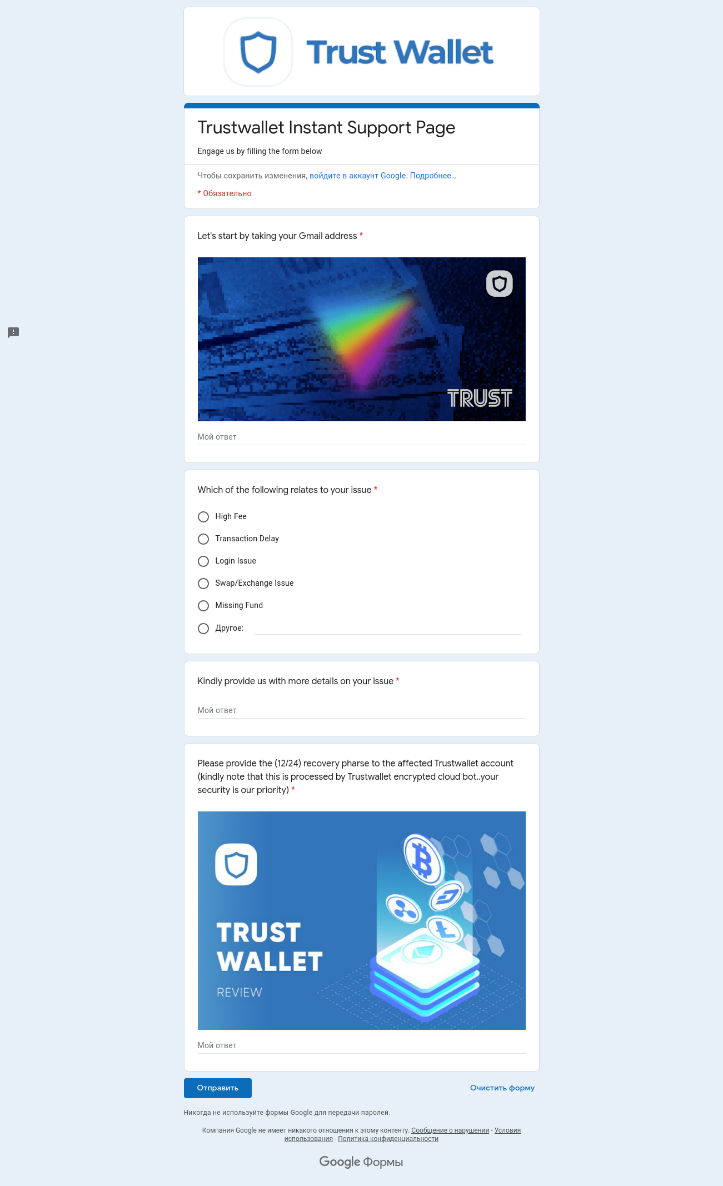
Fraudsters try to finagle confidential data through Google Forms
Although such services have started to warn users about the dangers of sharing passwords through forms, as well as to implement automatic protection (such as blocking forms containing keywords like “password”), this method remains popular with scammers due to the ability to mass-create phishing surveys. To bypass built-in security, they often use text spoofing, that is, they replace characters in keywords with visually similar ones: for example, they write pa$$w0rd instead of password, making such words unrecognizable to automated systems.
Besides forms, cybercriminals make active use of cloud documents. Not least, they can send e-mails with a link to a document in a legitimate service that contains a phishing link.
Avoiding detection
Scammers use various techniques to hide from detection. Some are quite effective but not so common, because they require more advanced technical know-how than many scammers possess.
One method to avoid detection is obfuscation, where the user-invisible source code of a scam page is scrambled to make the attack hard to detect by automated means. We talked in detail about obfuscation methods in our post about the phishing-kit market.
Another way to protect a scam site from detection is to use methods to hide page content from automated analysis. Here are some of them:
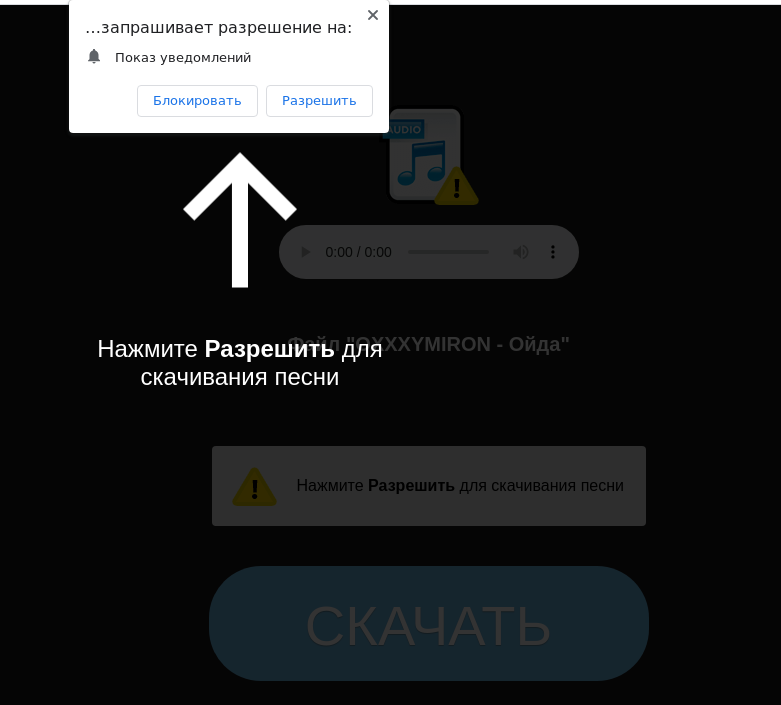
To download a song on a scam site, the user is asked to allow browser notifications from that site
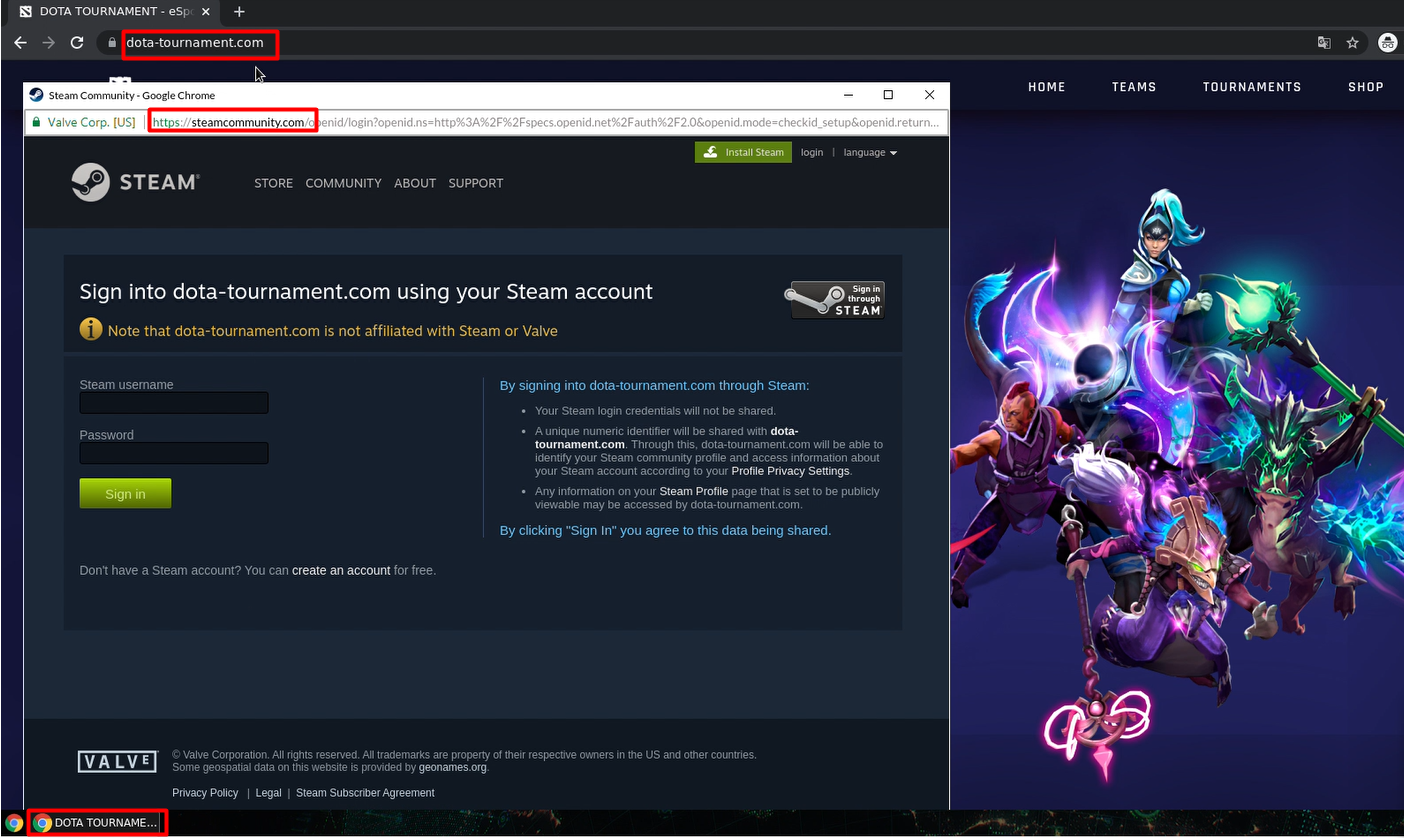
Browser-in-the-Browser attack: a pop-up window mimics a browser window with an address bar
Along with content, scammers try to hide the URLs of malicious sites from detection technologies. For this purpose, they can use:
Social engineering elements
Cybercriminals’ tricks often target the user and not the security system’s vulnerabilities. Scammers employ their knowledge of the human psyche to deceive victims. These can be combined with technical means to achieve a devastating effect.
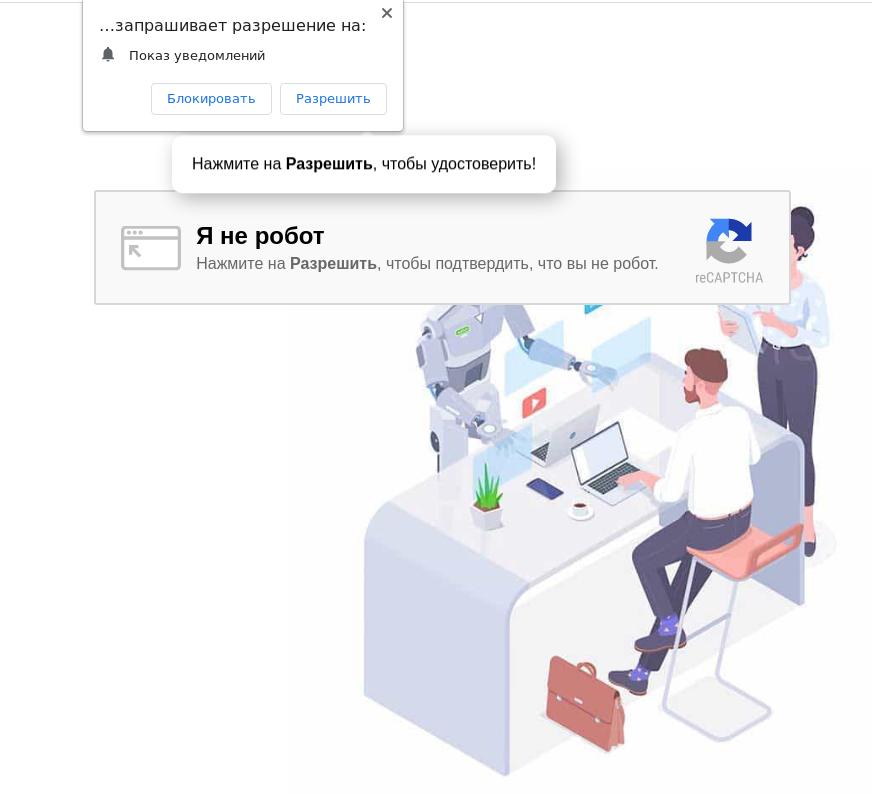
Fake CAPTCHA on a phishing page asking for permission to show browser notifications, supposedly to prove you’re not a robot
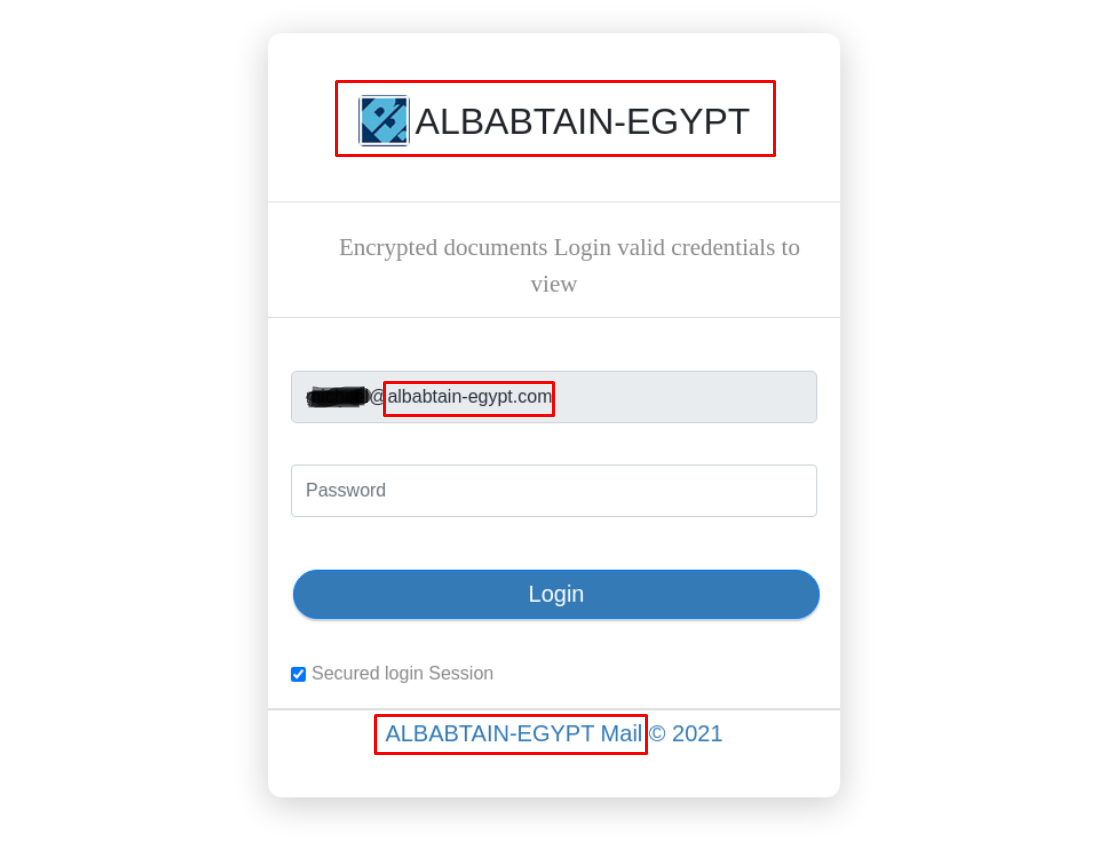
Attackers use the victim’s mail domain to create content on a scam site
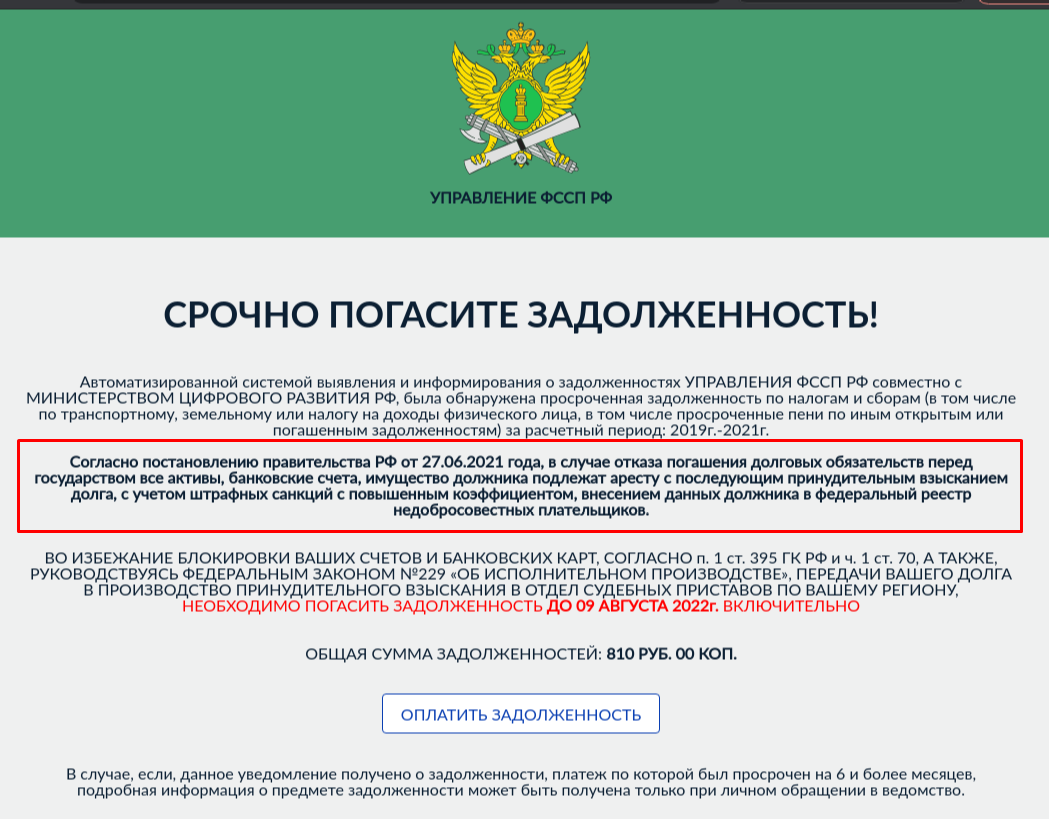
Scammers threaten to seize all the user’s property and accounts if they fail to pay off a bogus debt
Scam site demands urgent payment of “COVID-19-related expenses” for delivery of a parcel

Cybercriminals lure the user with the chance to win an Amazon gift card
Conclusion
Most users today are more or less aware of the current web threats. Many have either experienced internet scams themselves, or know about them from the news or other sources, making it harder for attackers to dupe victims and so requiring the use of ever more sophisticated methods. Instead of slapdash phishing and scam sites, high-quality fakes are becoming increasingly common. This includes mimicking a browser window with a legitimate URL in a pop-up window, as well as phishing pages with a legitimate site in the background, loaded via an iFrame. We’ve also seen elements of targeted attacks in phishing and scams, such as downloading content related to the target’s mail domain or using data got from large-scale leaks to make contact with potential victims.
At the same time, vishing is on the rise, because it’s easier to apply pressure over the phone, giving the victim no time to mull things over. In addition, cybercriminals use other available communication channels: e-mail, popular messengers, social networks, marketplaces.
To implement attacks, they employ a variety of techniques, such as spoofing, social engineering, site hacking, and code and content hiding. Alongside this, detection avoidance methods also continue to evolve. Attackers are increasingly using one-time generated links with hashes to prevent web threat detection technologies from blocking them.
Note, too, that scammers continue to base their malicious campaigns on the hottest topics in the news. If there’s a major event going on somewhere, a problem on a country or global scale, or some service or technology is becoming all the rage, be sure that cybercriminals will seek to exploit it. For instance, the lockdown period was beset by large-scale “financial aid” scams, while last year’s upturn in cryptocurrency prices went hand in hand with numerous fraudulent investment schemes. So it pays to be vigilant online, especially when it comes to money: no matter how much you want to believe that good fortune has fallen from the sky, if something sounds too good to be true, it probably is.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


