Major U.S. energy org targeted in QR code phishing attack

A phishing campaign was observed predominantly targeting a notable energy company in the US, employing QR codes to slip malicious emails into inboxes and bypass security.
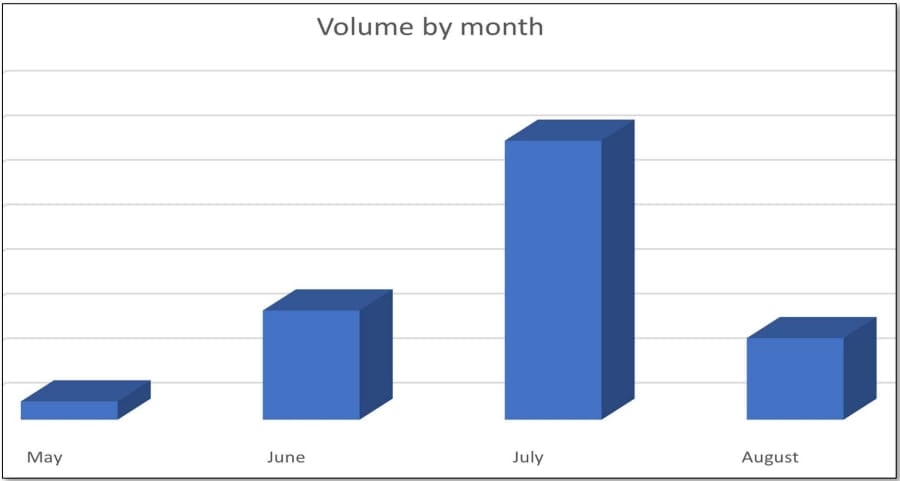
Roughly one-third (29%) of the 1,000 emails attributed to this campaign targeted a large US energy company, while the remaining attempts were made against firms in manufacturing (15%), insurance (9%), technology (7%), and financial services (6%).
According to Cofense, who spotted this campaign, this is the first time that QR codes have been used at this scale, indicating that more phishing actors may be testing their effectiveness as an attack vector.
Source: Cofense
Cofense did not name the energy company targeted in this campaign but categorized them as a “major” US-based company.
QR codes in phishing
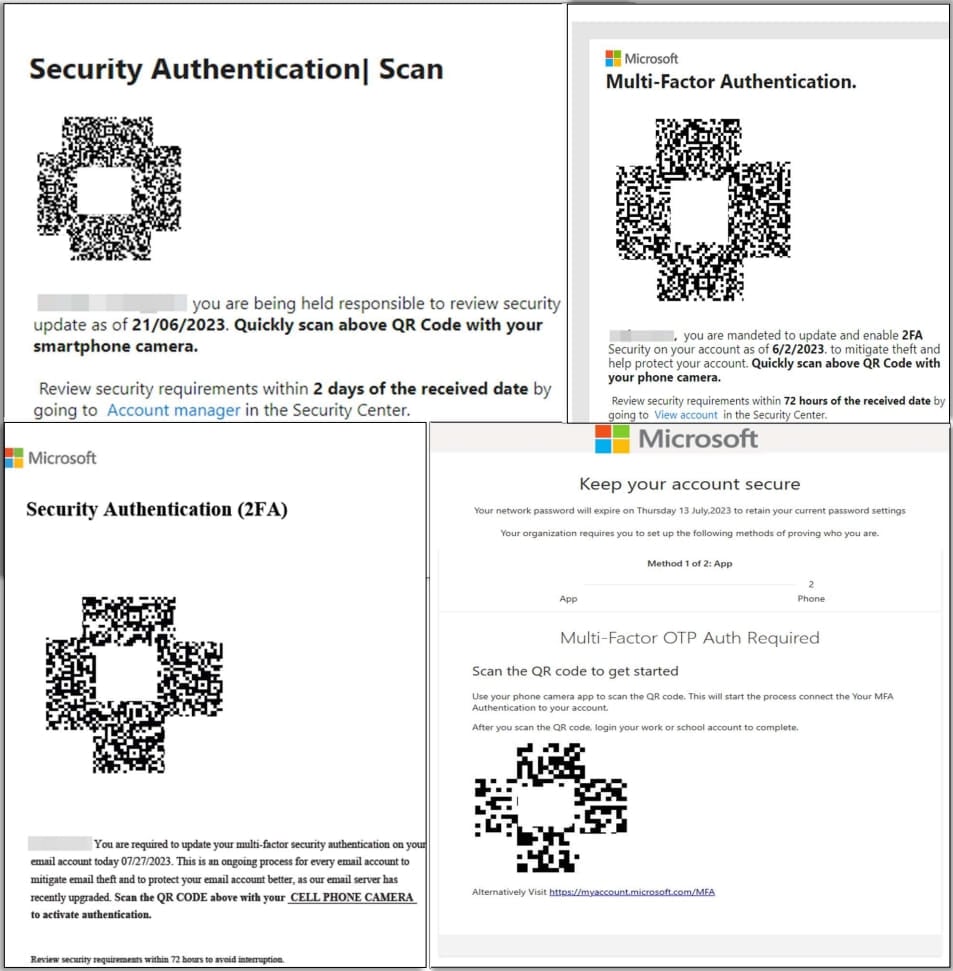
Cofense says the attack begins with a phishing email that claims the recipient must take action to update their Microsoft 365 account settings.
The emails carry PNG or PDF attachments featuring a QR code the recipient is prompted to scan to verify their account. The emails also state that the target must complete this step in 2-3 days to add a sense of urgency.
Source: Cofense
The threat actors use QR codes embedded in images to bypass email security tools that scan a message for known malicious links, allowing the phishing messages to reach the target’s inbox.
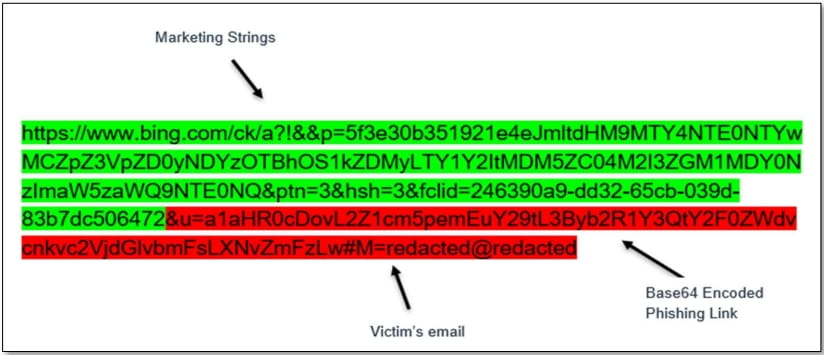
To evade security, the QR codes in this campaign also use redirects in Bing, Salesforce, and Cloudflare’s Web3 services to redirect the targets to a Microsoft 365 phishing page.
Hiding the redirection URL in the QR code, abusing legitimate services, and using base64 encoding for the phishing link all help evade detection and get through email protection filters.
QR codes in phishing
QR codes have been used in phishing campaigns, albeit on a smaller scale, in the past, including one in France and one in Germany.
Scammers have also employed QR codes to trick people into scanning them and redirect them to malicious websites that attempt to steal their money.
In January 2022, the FBI warned that cybercriminals increasingly use QR codes to steal credentials and financial information.
Despite their effectiveness in bypassing protections, QR codes still require the victim to take action to get compromised, which is a decisive mitigating factor working in favor of well-trained personnel.
Also, most QR code scanners on modern smartphones will ask the user to verify the destination URL before launching the browser as a protective step.
Apart from training, Cofense also suggests that organizations use image recognition tools as part of their phishing protection measures, although these are not guaranteed to catch all QR code threats.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

