Malvertisers up their game against researchers
Threat actors constantly take notice of the work and takedown efforts initiated by security researchers. In this constant game of cat and mouse chasing, tactics and techniques keep evolving from simple to more complex, and more covert.
This is a trend we have observed time and time again, no matter the playing field, from exploit kits to credit card skimmers. As defenders, we may have mixed reactions: on the one hand, as technical people we naturally appreciate a well-written exploit or piece of code and the challenge it creates. There is something about it that sparks our interest and curiosity. On the other hand, we know that the people behind it have bad intentions and intend on doing harm.
In today’s blog post, we look at a recent malvertising chain that started using a more advanced cloaking technique to remain under the radar. Based on our tracking, it is a new trend for these malvertising campaigns dropping infostealers and other malware used by initial access brokers in ransomware operations.
Malicious ad and cloaking
Threat actors continue to target certain IT programs such as remote access programs and scanners by creating ads that are displayed on popular search engines such as Google. The ad below is for the Advanced IP scanner tool and was found when performing a Google search from a US IP address.
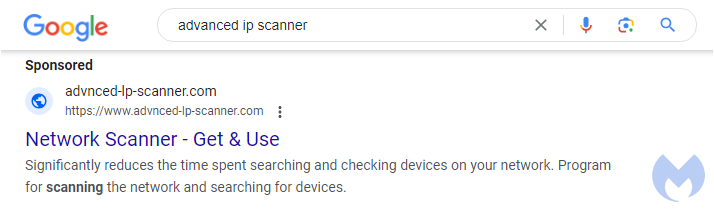 Figure 1: Malicious ad on Google for Advanced IP Scanner
Figure 1: Malicious ad on Google for Advanced IP Scanner
The domain name advnced-lp-scanner[.]com may look legitimate but it is not. It was registered on Jul 30 2023 and is hosted on a server in Russia at 185.11.61[.]65.
If you were to investigate this ad, you would likely open it up in a virtual machine and see what it leads to. One of the most common checks that is done by threat actors is a simple server-side IP check to determine whether you are running a VPN or proxy or have visited the site before. That means that as researchers we need to constantly find new IP addresses that look legitimate and then revisit the page again.
Interestingly, even with a fresh IP address the landing page looked innocent. This can happen for different reasons, for example if the threat actor is in the process of setting up the site and hasn’t finished swapping it to the malicious version. Or it could also be that the time of day is not in line with when the attacker is making the switch.
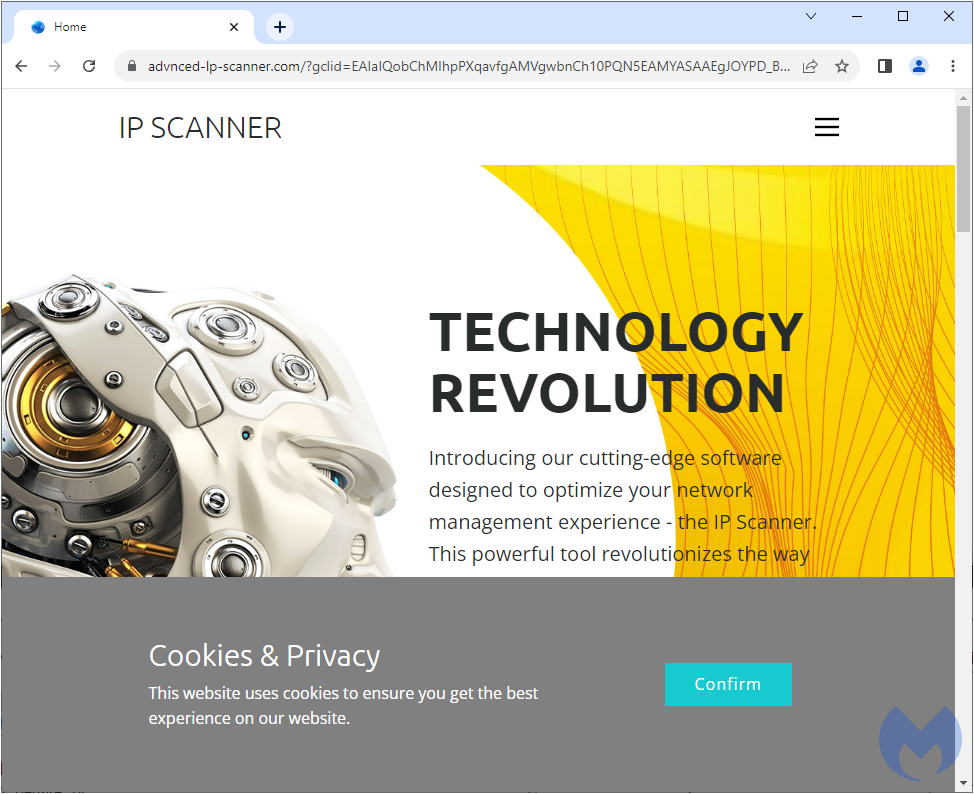 Figure 2: Decoy page without any malware to download
Figure 2: Decoy page without any malware to download
Advanced fingerprinting
Looking closer at the network requests from the ad to the web server we saw new code that looked suspicious. This is Base64 encoded JavaScript that is loaded before anything else on the page.
In fact, this client-side request was performed after a server-side IP check to determine if your IP address was clean. In other words, this is another layer that needs to be processed before we get to see what we are looking for.
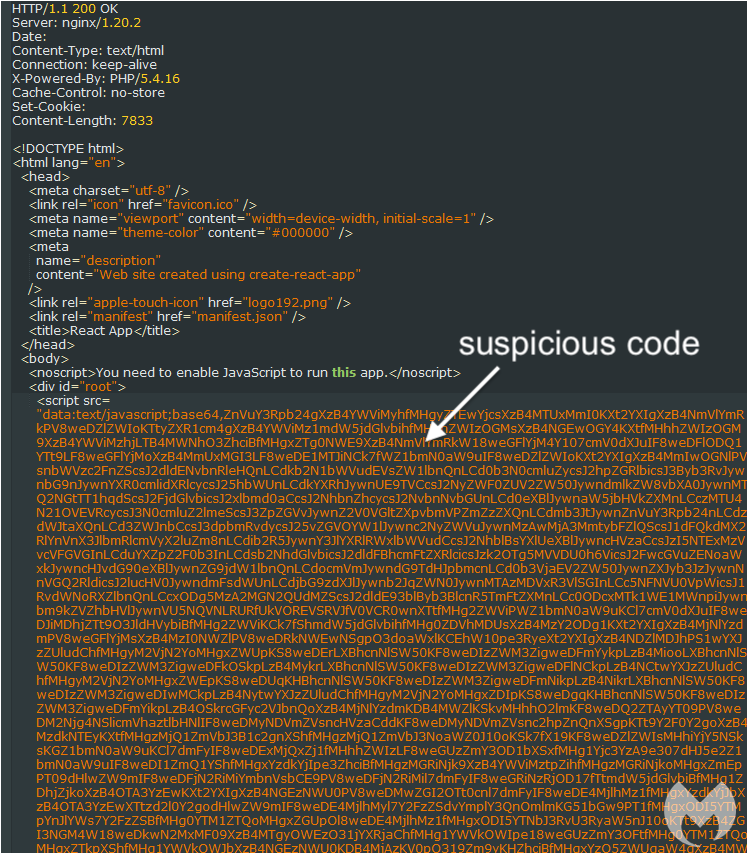 Figure 3: Suspicious Base64-encoded code
Figure 3: Suspicious Base64-encoded code
We can deobfuscate this code using CyberChef and further beautify it to see what it does. Here are some of those checks:
- browser properties such as window and screen size
- time zone (difference between UTC and local time)
- browser rendering capabilities related to video card driver
- MIME type for MP4 file format
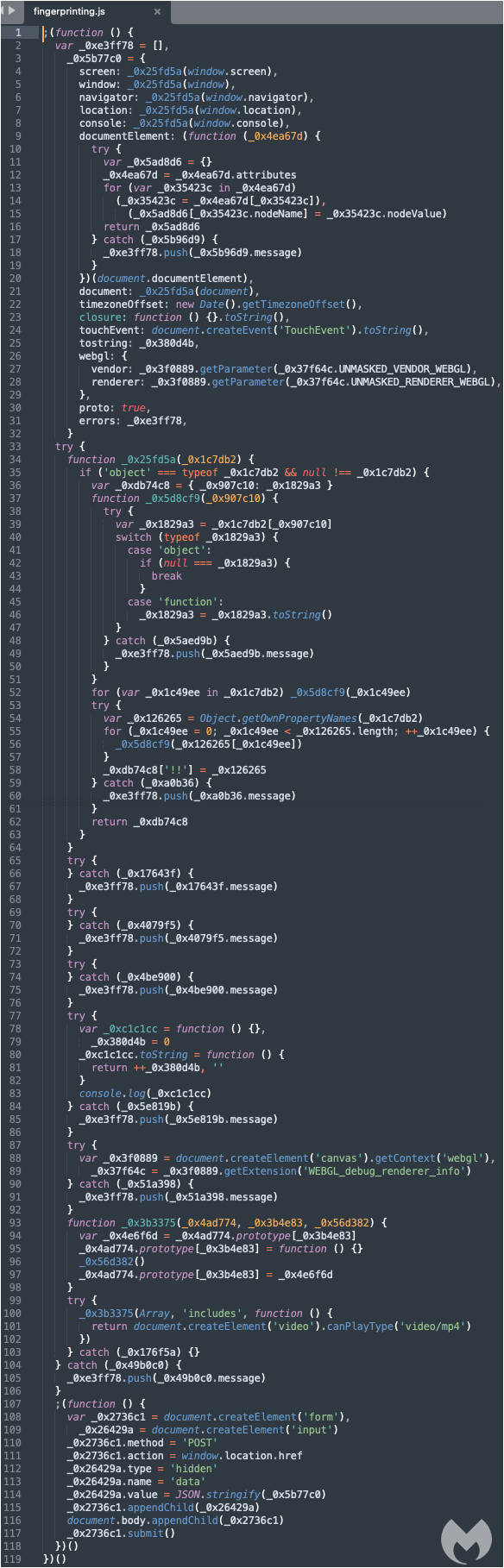 Figure 4: Decoded fingerprinting script
Figure 4: Decoded fingerprinting script
Many tools used by researchers are scripted in Python and will fail the test. Same goes for virtual machines, the WEBGL_debug_renderer_info API can help to detect if you are using virtualization such as VMware or VirtualBox.
The data that is collected from visitors is then sent back to the attacker’s website via a POST request for further parsing and to determine what action to take next.
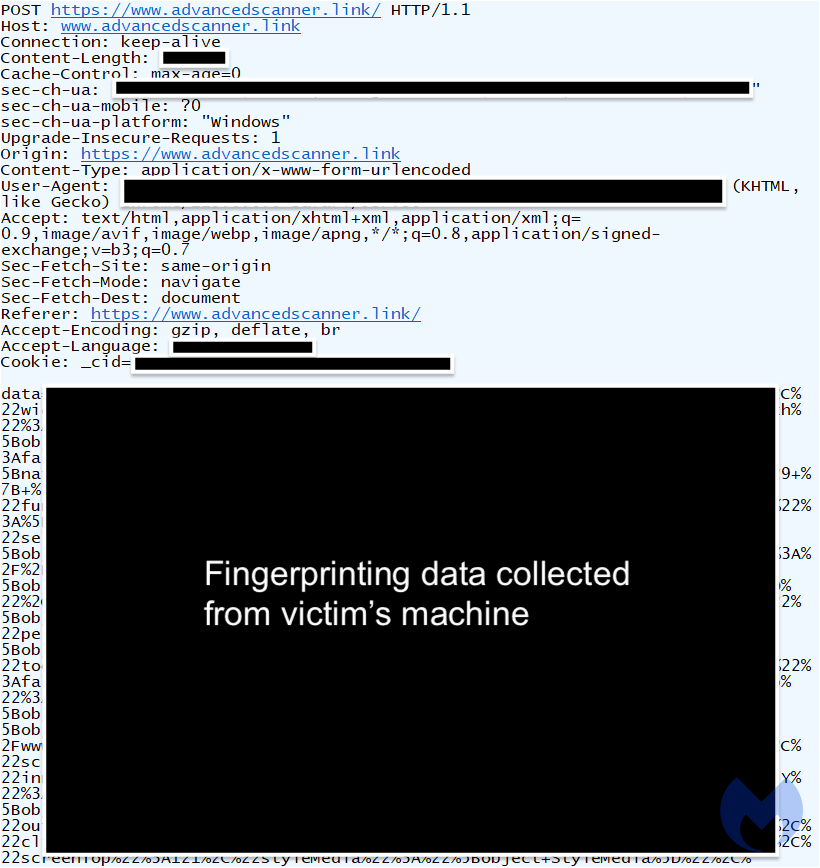
Figure 5: POST request sending victim’s details to attacker
Below is the web traffic view of a successful redirection to the malicious page where the victim can download the malware payload.
 Figure 6: Web traffic from malicious ad to payload page
Figure 6: Web traffic from malicious ad to payload page
And this is the malware landing page:
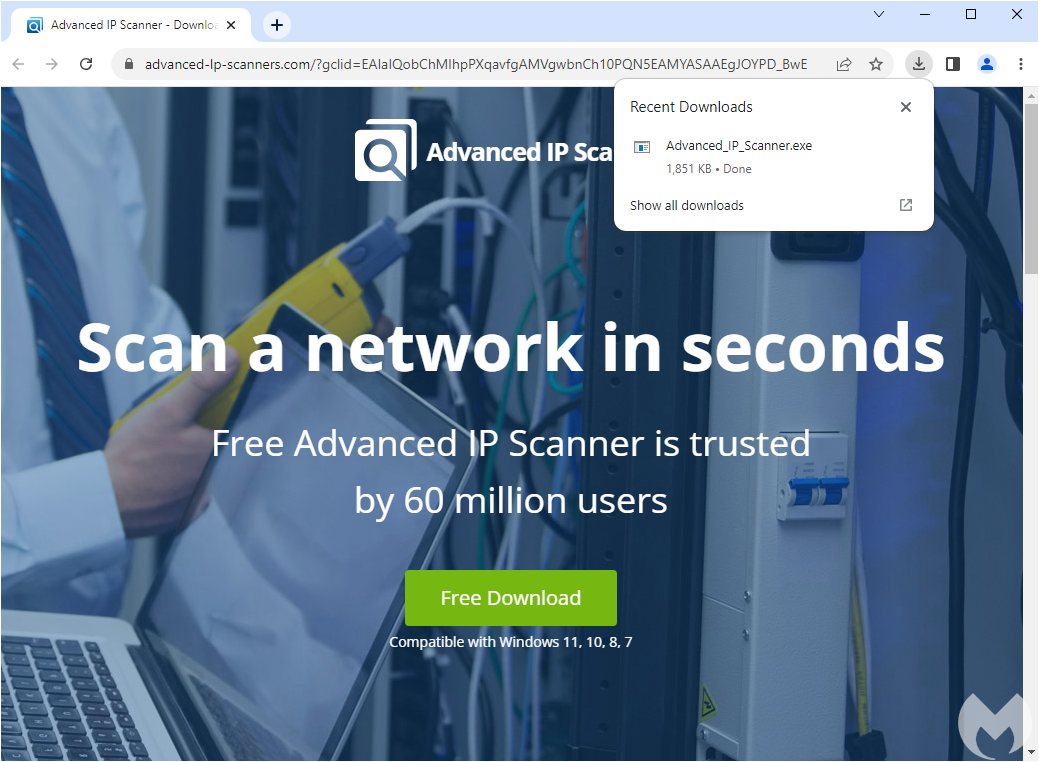 Figure 7: Malware landing page after successfully passing the fingerprinting checks
Figure 7: Malware landing page after successfully passing the fingerprinting checks
We can now collect the payload and make sure that it is detected.
Conclusion
By using better filtering before redirecting potential victims to malware, threat actors ensure that their malicious ads and infrastructure remain online longer. Not only does it make it more difficult for defenders to identify and report such events, it also likely has an impact on takedown actions. In the majority of cases where we have reported malvertising incidents, the abused platform needs to validate the information before taking action against the advertiser.
This makes sense as reports could be erroneous and lead to advertising accounts being suspended unjustly. However, it also means that while an incident is being investigated and reproduced (which could take hours), people will click on those ads and download malware.
As we continue to report malvertising campaigns, we improve our understanding of the threat actors’ TTPs and adjust our toolsets accordingly. Any intelligence gathered is shared within our products and ultimately delivered to Malwarebytes customers via web and malware protection updates to ensure they remain protected.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[BABUK2] - Ransomware Victim: wapda[.]gov[.]pk By Babuk Locker 2[.]0 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
