[MEDUSA] – Ransomware Victim: Metropolitan Borough of Gateshead
![[MEDUSA] - Ransomware Victim: Metropolitan Borough of Gateshead 1 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image.png)
Ransomware Group: MEDUSA
VICTIM NAME: Metropolitan Borough of Gateshead
NOTE: No files or stolen information are [exfiltrated/downloaded/taken/hosted/seen/reposted/disclosed] by RedPacket Security. Any legal issues relating to the content of the files should be directed at the attackers directly, not RedPacket Security. This blog is simply posting an editorial news post informing that a company has fallen victim to a ransomware attack. RedPacket Security is in no way affiliated or aligned with any ransomware threat actors or groups and will not host infringing content. The information on this page is fully automated and redacted whilst being scraped directly from the MEDUSA Onion Dark Web Tor Blog page.
AI Generated Summary of the Ransomware Leak Page
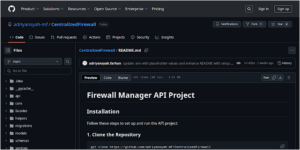
The ransomware leak page concerning the Metropolitan Borough of Gateshead, a public sector entity in the United Kingdom, reveals significant data breaches. Discovered on February 22, 2025, the attack reportedly transpired on January 14, 2025, conducted by the hacking group known as Medusa. The borough, located in Tyne and Wear and part of the Tyneside conurbation, serves a population of approximately 196,154 residents, according to the latest census conducted in 2021. The Gateshead Council, which employs around 684 individuals, is involved in this leaking incident, further highlighting the cybersecurity challenges faced within public sector offices.
The details extracted from the leak suggest extensive impacts on various stakeholders, involving three employee-level exposures, three third-party entities, and a notable presence of 62 user accounts compromised. The leak page indicates that multiple aspects of the borough’s operations might be affected, with domains related to third parties also being implicated. As of the last update on January 20, 2025, notable download links and additional materials were mentioned, though specific URLs were redacted for safety. Moreover, the page features a screenshot depicting the context of the breach, which underscores the vulnerabilities in the borough’s digital infrastructure.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![Cobalt Strike Beacon Detected - 185[.]9[.]146[.]38:80 4 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)