MetaMask warns of new ‘Address Poisoning’ cryptocurrency scam

Cryptocurrency wallet provider MetaMask is warning users of a new scam called ‘Address Poisoning’ used to trick users into sending funds to a scammer rather than an intended recipient.
When MetaMask users send or receive cryptocurrency, it appears in the wallet transaction list. Clicking the transaction displays more details, including the token, the amount sent or received, and a short form of the third party’s address.
For example, below are examples of two shortened addresses that could be shown in MetaMask cryptocurrency transactions.
From: 0x242...54b7
To: 0x242...54b7While both wallet addresses look identical in their short form, they could be completely different, easily confusing MetaMask users.
Scammers poison your MetaMask transactions
In a new post by MetaMask, the developers warn of a new scam called ‘Address Poisoning’ that relies on poisoning the wallet’s transaction history with scammer’s addresses that are very similar to addresses that a user recently had transactions.
The threat actor monitors the blockchain for new transactions to conduct the scam.
After selecting a target, they use a vanity address creator to create an address very similar, if not almost exactly the same, as the one involved in the recent transaction.
It should be noted that creating an address that matches a target address’ prefix or suffix can take under a minute. However, targeting both will take far longer (possibly too long to be worthwhile) to generate.
The threat actor then sends the targeted sender’s address a small amount of cryptocurrency, or even a $0 token transaction, from this new address so that the transaction appears in their wallet’s history.
As the threat actor’s address is very similar to a user’s previous transaction, and as MetaMask shortens the addresses in the transaction history, it looks like it’s from the same person.
This method effectively poisons the transaction history with multiple entries that look like they are between the same address but are using different ones — one address for the actual, legitimate transaction and the newer one from the attacker using a copycat wallet address.
The attacker then hopes that when a user needs to send cryptocurrency to someone they previously sent to, they will find the most recent transaction, which in this case is from the attacker, and sends the crypto to the scammer’s address instead.
To perform a transaction, even for negligible amounts, the attacker still has to cover additional costs known as “gas,” as the transaction is registered on the blockchain.
However, the threat actors are willing to invest in the scam in the hopes of a much larger payout.
Since there’s no way to stop these malicious transactions from occurring on the blockchain, MetaMask is warning users to be diligent when copying addresses from transactions.
Furthermore, as clicking on the short-form address in MetaMask transactions copies it automatically to the keyboard without showing the full address, as shown in the mockup below, it is crucial to be very careful.
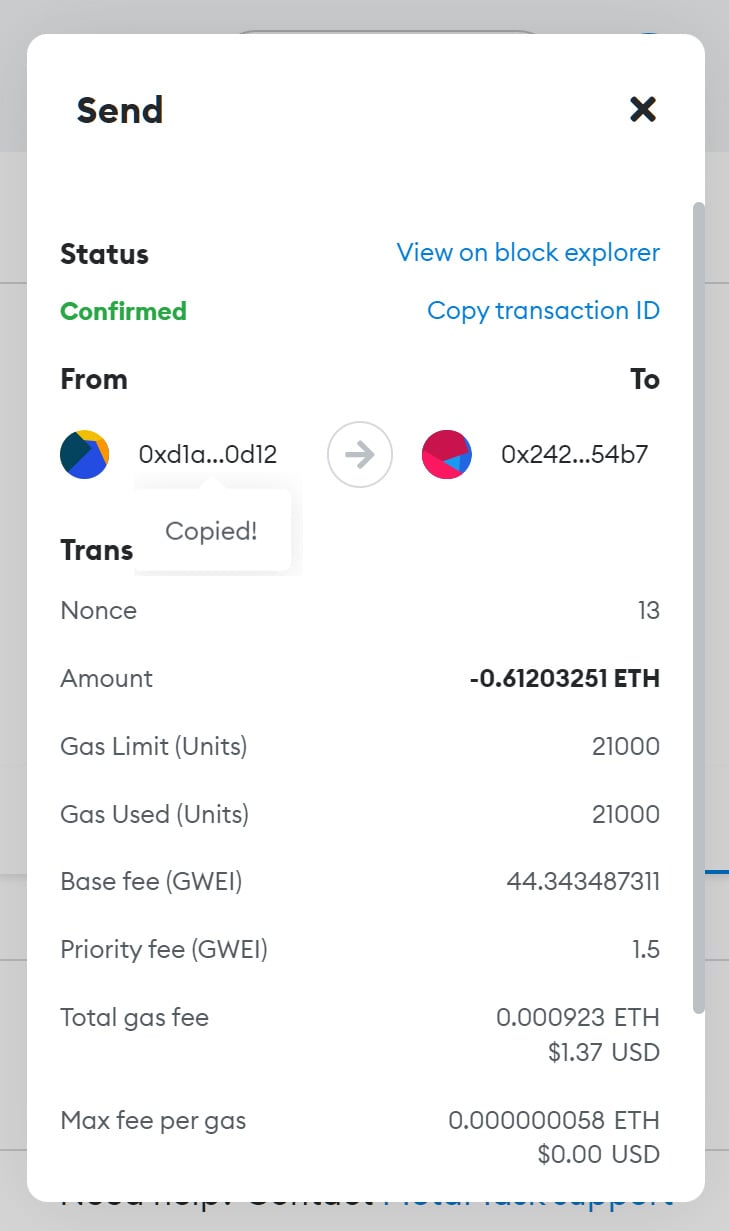
Source: BleepingComputer
Instead, search your transaction list for a known valid transaction and grab the full address from a blockchain explorer like EtherScan.
MetaMask also recommends you use their built-in Address Book feature at ‘Settings → Contacts’ to save known, valid cryptocurrency addresses for people or services you commonly send transactions.
One possible way that MetaMask could prevent these types of attacks is to create a new option that forces the displaying of complete Send and From addresses in transaction histories.
However, as Ethereum addresses are very long (66 characters), this would introduce user interface design issues.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.









