Microsoft Discovers Critical Rce Flaw In Perforce Helix Core Server

Four vulnerabilities, one of which is rated critical, have been discovered in the Perforce Helix Core Server, a source code management platform widely used by the gaming, government, military, and technology sectors.
Microsoft analysts discovered the flaws during a security review of the product, which the company’s game development studios use, and responsibly reported them to Perforce in late August 2023.
Although Microsoft says it has not observed any exploitation attempts of the discovered vulnerabilities in the wild, users of the product are recommended to upgrade to version 2023.1/2513900, released on November 7, 2023, to mitigate the risk.
The Perforce Helix Core vulnerabilities
The four flaws discovered by Microsoft mainly involve denial of service (DoS) issues, with the most severe allowing arbitrary remote code execution as LocalSystem by unauthenticated attackers.
The vulnerabilities are summarized as follows:
- CVE-2023-5759 (CVSS score 7.5): Unauthenticated (DoS) via RPC header abuse.
- CVE-2023-45849 (CVSS score 9.8): Unauthenticated remote code execution as LocalSystem.
- CVE-2023-35767 (CVSS score 7.5): Unauthenticated DoS via remote command.
- CVE-2023-45319 (CVSS score 7.5): Unauthenticated DoS via remote command.
The most dangerous flaw of the set, CVE-2023-45849, allows unauthenticated attackers to execute code from ‘LocalSystem,’ a high-privileged Windows OS account reserved for system functions. This account level can access local resources and system files, modify registry settings, and more.
The vulnerability arises from the server’s mishandling of the user-bgtask RPC command. In its default configuration, Perforce Server permits unauthenticated attackers to remotely execute arbitrary commands, including PowerShell scripts, as LocalSystem.
By leveraging CVE-2023-45849, attackers may install backdoors, access sensitive information, create or modify system settings, and potentially take complete control of the system running a vulnerable version of Perforce Server.
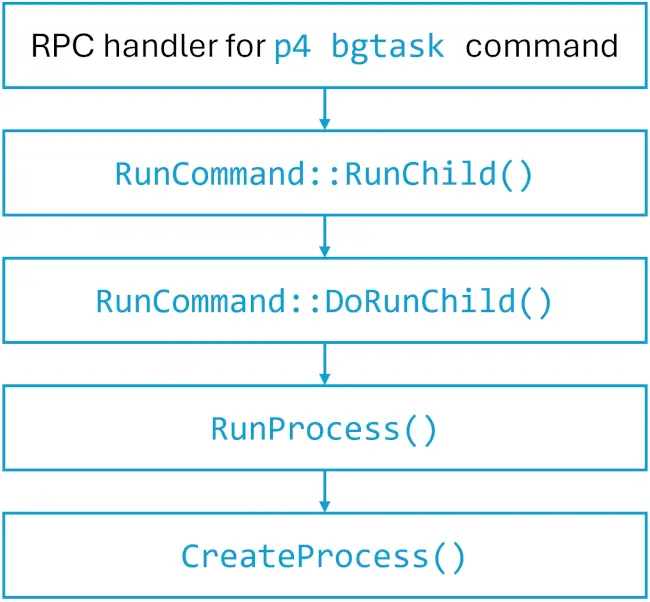
The remaining three vulnerabilities are less severe, allowing denial of service attacks, but can still cause operational disruption that could translate to significant financial losses in large-scale deployments.
Protection recommendations
Apart from downloading the latest version of Helix Core from the vendor’s download portal, Microsoft proposes taking the following steps:
- Regularly update third-party software.
- Restrict access using VPN or IP allow-list.
- Use TLS certificates with a proxy for user validation.
- Log all access to the Perforce Server.
- Set up crash alerts for IT and security teams.
- Use network segmentation to contain breaches.
It is also recommended to follow the tips provided in this official security guide.
