Microsoft Disrupts Cybercrime Gang Behind 750 Million Fraudulent Accounts

Microsoft’s Digital Crimes Unit seized multiple domains used by a Vietnam-based cybercrime group (Storm-1152) that registered over 750 million fraudulent accounts and raked in millions of dollars by selling them online to other cybercriminals.
Storm-1152 is a major cybercrime-as-a-service provider and the number one seller of fraudulent Outlook accounts, as well as other illegal “products,” including an automatic CAPTCHA-solving service to bypass Microsoft’s CAPTCHA challenges and register more fraudulent Microsoft email accounts.
“Storm-1152 runs illicit websites and social media pages, selling fraudulent Microsoft accounts and tools to bypass identity verification software across well-known technology platforms. These services reduce the time and effort needed for criminals to conduct a host of criminal and abusive behaviors online,” according to Amy Hogan-Burney, the General Manager of Microsoft’s Digital Crimes Unit.
“Since at least 2021, the Defendants have been engaged in a scheme to obtain millions of Microsoft Outlook email accounts in the names of fictitious users based on a series of false representations, and then sell these fraudulent accounts to malicious actors for use in various types of cybercrime,” according to the complaint.
According to Microsoft Threat Intelligence, numerous cybergroups involved in ransomware, data theft, and extortion have bought and used accounts provided by Storm-1152 in their attacks.
For instance, financially-motivated Storm-0252, Storm-0455, and Octo Tempest (aka Scattered Spider) cybercrime gangs used Storm-1152 fraudulent accounts to infiltrate organizations worldwide and deploy ransomware on their networks.
The resulting service disruptions resulted in damages estimated by Microsoft to be in the hundreds of millions of dollars.
“Upon information and belief, evidence gathered thus far by Microsoft’s investigation in this case shows that Microsoft email accounts—which were fraudulently obtained by Defendants and sold to cybercriminals—have been used by organized cybercrime groups known to Microsoft as Storm-0252, Storm-0455, and Octo Tempest to engage in cybercrime activity, including email phishing scams, which are frequently used as a vehicle for spreading ransomware and other malware,” the complaint adds.
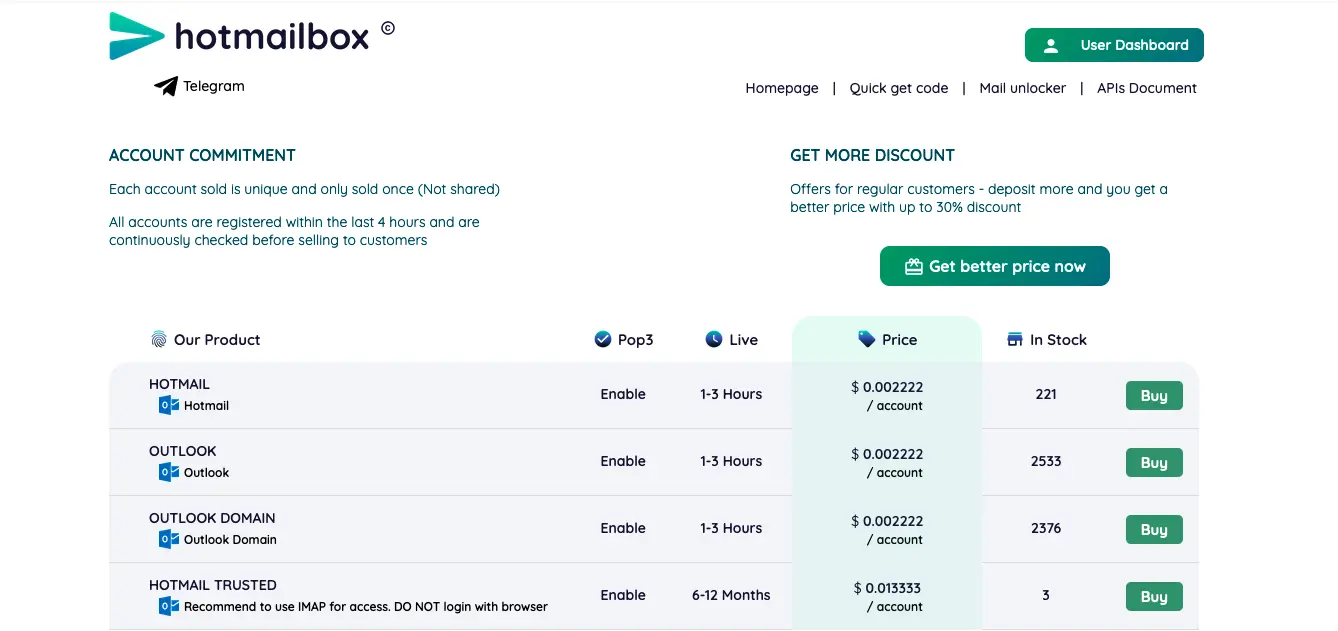
On December 7, Microsoft seized Storm-1152’s U.S.-based infrastructure and took down the following websites after obtaining a court order from the Southern District of New York:
- Hotmailbox.me, a website selling fraudulent Microsoft Outlook accounts
- 1stCAPTCHA, AnyCAPTCHA, and NoneCAPTCHA, websites that facilitate the tooling, infrastructure, and selling of the CAPTCHA solving service to bypass the confirmation of use and account setup by a real person. These sites sold identity verification bypass tools for other technology platforms
- The social media sites actively used to market these services
The company also sued Duong Dinh Tu, Linh Van Nguyen (a/k/a Nguyen Van Linh), and Tai Van Nguyen for their purported involvement in hosting the cybercriminal operation on the seized domains.
As further alleged in the complaint, the defendants managed and developed the code for the seized websites. They were also involved in publishing video guides on how to use the fraudulent Outlook accounts and offered chat support to ‘customers’ using their fraudulent services.
“Today’s action is a continuation of Microsoft’s strategy of taking aim at the broader cybercriminal ecosystem and targeting the tools cybercriminals use to launch their attacks. It builds on our expansion of a legal method used successfully to disrupt malware and nation-state operations,” Hogan-Burney said.
