Microsoft Office 365 Users Targeted By a New Phishing Campaign Using Fake Zoom Notifications
As people across the world struggle to survive the onslaught of the corona pandemic by switching to the work-from-home criteria, the usage and demand of cloud-based communication platform providing users with audio and videoconferencing services have seen a sudden upsurge.
Zoom is one such platform that has from the beginning of 2020 has seen an extremely high increase of new monthly active users after a huge number of employees have adopted remote working.
However recently Microsoft Office 365 users are being targeted by a brand new phishing campaign that utilizes fake Zoom notifications to caution the users who work in corporate environments that their Zoom accounts have been suspended, with the ultimate goal of stealing Office 365 logins.
Reports are as such that those targeted by this campaign are all the more ready to believe in such emails during this time since the number of remote workers participating in daily online meetings through video conferencing platforms, as Zoom has definitely increased because of stay-at-home orders or lockdowns brought about by the pandemic.
As of now the phishing campaign mimicking automated Zoom account suspension alerts has received by more than 50,000 mailboxes based on details given by researchers as email security company Abnormal Security who recognized these continuous attacks.
The phishing messages spoof an official Zoom email address and are intended to imitate a real automated Zoom notification.
Utilizing a spoofed email address and an email body practically free from any grammar blunders or typos (other than a self-evident ‘zoom’ rather than ‘Zoom account’) makes these phishing messages all the more persuading and conceivably more viable.
The utilization of a lively “Happy Zooming!” toward the end of the email could raise a few cautions however, as it doesn’t exactly fit with the rest of the message’s tone.
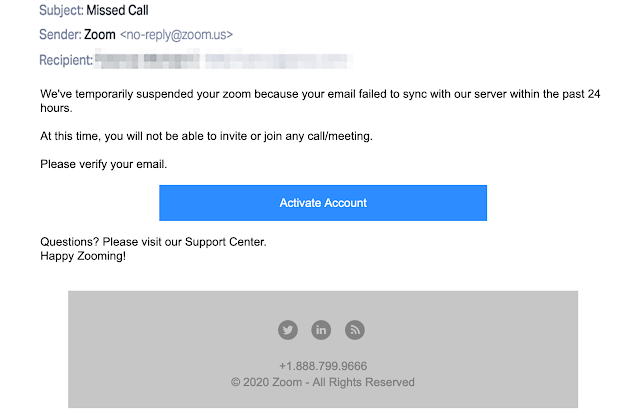
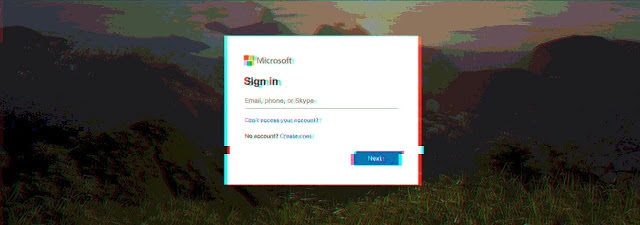
As soon as the users click the “Activate Account” button, they are redirected to a fake Microsoft login page through ‘an intermediary hijacked site’.
On the phishing landing page, they are asked to include their Outlook credentials in a form intended to exfiltrate their account subtleties to attacked controlled servers.
On the off chance that they succumb to the attackers’ tricks, the victims’ Microsoft credentials will be utilized to assume full control for their accounts and all their data will be ready for the picking, later to be utilized as a part of identity theft and fraud schemes like the Business Email Compromise (BEC) attacks.
Despite the fact that the US Federal Bureau of Investigation (FBI) had warned of BEC abusing popular cloud email services, like Microsoft Office 365 and Google G Suite through Private Industry Notifications issued in March and in April.
Even after this, Office 365 users are continuously targeted by phishing campaigns with the ultimate objective of reaping their credentials.
Regardless Microsoft has warned of phishers’ ongoing movement to new types of phishing strategies, like consent phishing, other than conventional email phishing and credential theft attacks.
Microsoft Partner Group PM Manager Agnieszka Girling says, “While application use has accelerated and enabled employees to be productive remotely, attackers are looking at leveraging application-based attacks to gain unwarranted access to valuable data in cloud services,”
The company additionally has made a legal move to destroy some portion of the attack infrastructure used to host malignant 365 OAuth apps utilized in consent phishing to seize victims’ Office 365 accounts.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


